Practice Free N10-009 Exam Online Questions
Which of the following is an XML-based security concept that works by passing sensitive information about users, such as login information and attributes, to providers?
- A . IAM
- B . MFA
- C . RADIUS
- D . SAML
D
Explanation:
The correct answer is SAML (Security Assertion Markup Language). SAML is an XML-based standard used for single sign-on (SSO) and identity federation. It allows identity providers (IdPs) to share authentication and authorization data with service providers (SPs), passing secure tokens containing user attributes and credentials.
A Chief Executive Officer (CEO) of a company purchases a new phone that will be used while traveling to different countries. The CEO needs to be able to place outgoing calls and receive incoming calls on the phone using a SIM card.
Which of the following cellular technologies does the CEO’s phone need?
- A . WDMA
- B . CDMA
- C . GSM
- D . SLA
C
Explanation:
GSM (Global System for Mobile communications) is the international standard that uses SIM cards to authenticate and connect phones to the cellular network. GSM allows users to place and receive calls while traveling globally, provided they have a SIM card. CDMA, on the other hand, does not use SIM cards in the same way and is primarily used in the United States. (Reference: CompTIA Network+ Study Guide, Chapter on Network Fundamentals)
A Chief Executive Officer (CEO) of a company purchases a new phone that will be used while traveling to different countries. The CEO needs to be able to place outgoing calls and receive incoming calls on the phone using a SIM card.
Which of the following cellular technologies does the CEO’s phone need?
- A . WDMA
- B . CDMA
- C . GSM
- D . SLA
C
Explanation:
GSM (Global System for Mobile communications) is the international standard that uses SIM cards to authenticate and connect phones to the cellular network. GSM allows users to place and receive calls while traveling globally, provided they have a SIM card. CDMA, on the other hand, does not use SIM cards in the same way and is primarily used in the United States. (Reference: CompTIA Network+ Study Guide, Chapter on Network Fundamentals)
Which of the following technologies is most appropriate for a business that requires high-speed access to frequently used web content, such as images and videos?
- A . CDN
- B . SAN
- C . Firewall
- D . Switch
A
Explanation:
The correct solution is a Content Delivery Network (CDN). A CDN caches web content (like images, videos, scripts) on distributed servers close to end users. This reduces latency, improves load times, and decreases the load on origin servers. For a business requiring high-speed access to media-rich content, a CDN is the most effective option.
B. SAN (Storage Area Network) is used for storage in a data center, not for distributing web content.
C. Firewall secures traffic but doesn’t accelerate content delivery.
D. Switches forward packets within a LAN, not globally distribute content.
By leveraging CDNs, businesses can handle large traffic volumes efficiently while improving user experience.
Reference (CompTIA Network+ N10-009):
Domain: Network Infrastructure ― CDNs, caching, performance optimization.
Which of the following protocols provides remote access utilizing port 22?
- A . SSH
- B . Telnet
- C . TLS
- D . RDP
A
Explanation:
SSH (Secure Shell) is a protocol used to securely connect to a remote server/system over a network.
It operates on port 22 and provides encrypted communication, unlike Telnet which operates on port 23 and is not secure. TLS is used for securing HTTP connections (HTTPS) and operates on ports like 443, while RDP (Remote Desktop Protocol) is used for remote desktop connections and operates on port 3389.
Reference: The CompTIA Network+ materials and tutorials cover SSH as the standard protocol for secure remote access, highlighting its operation on port 22.
A network technician is troubleshooting network latency and has determined the issue to be occuring two network switches (Switch10 and Switch11). Symptoms reported included poor video performance and slow file copying.
Given the following information:
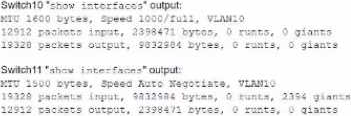
Which of the following should the technician most likely do to resolve the issue?
- A . Disable automatic negotiation on Switch11.
- B . Modify Switch10 MTU value to 1500.
- C . Configure STP on both switches.
- D . Change the native VLAN on the ports.
A new backup system takes too long to copy files to the new SAN each night. A network administrator makes a simple change to the network and the devices to decrease backup times.
Which of the following does the network administrator change?
- A . QoS
- B . SDN
- C . MTU
- D . VXLAN
- E . TTL
C
Explanation:
Increasing the MTU (Maximum Transmission Unit) size allows larger frames to be transmitted, reducing overhead and improving throughput ― especially for large file transfers like backups.
A junior network administrator is auditing the company network and notices incrementing input errors on a long-range microwave interface.
Which of the following is the most likely reason for the errors?
- A . The parabolic signal is misaligned.
- B . The omnidirectional signal is being jammed.
- C . The omnidirectional signal is not strong enough to receive properly.
- D . The parabolic signal uses improper routing protocols.
A
Explanation:
A misaligned parabolic antenna can cause a significant increase in input errors because the signal is not properly focused or directed towards the receiving antenna, resulting in poor reception and data corruption.
The document confirms:
“Misalignment of parabolic microwave antennas can lead to weak or incorrect signal reception, causing an increase in input errors and connectivity issues on the link.”
A network administrator wants users to be able to authenticate to the corporate network using a port-based authentication framework when accessing both wired and wireless devices.
Which of the following is the best security feature to accomplish this task?
- A . 802.1X
- B . Access control list
- C . Port security
- D . MAC filtering
A
Explanation:
An administrator is configuring a switch that will be placed in an area of the office that is accessible to customers.
Which of the following is the best way for the administrator to mitigate unknown devices from connecting to the network?
- A . SSE
- B . ACL
- C . Perimeter network
- D . 802.1x
D
Explanation:
