Practice Free MD-102 Exam Online Questions
HOTSPOT
You have a Microsoft 365 subscription that contains the devices shown in the following table.
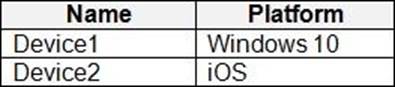
You plan to enroll the devices in Microsoft Intune.
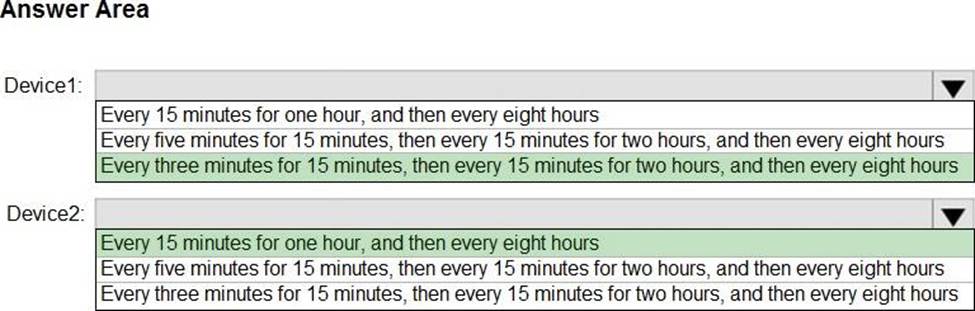
How often will the compliance policy check-ins run after each device is enrolled in Intune? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

Explanation:
Box 1: Every three minutes for 15 minutes, then every 15 minutes for two hours, and then around every eight hours
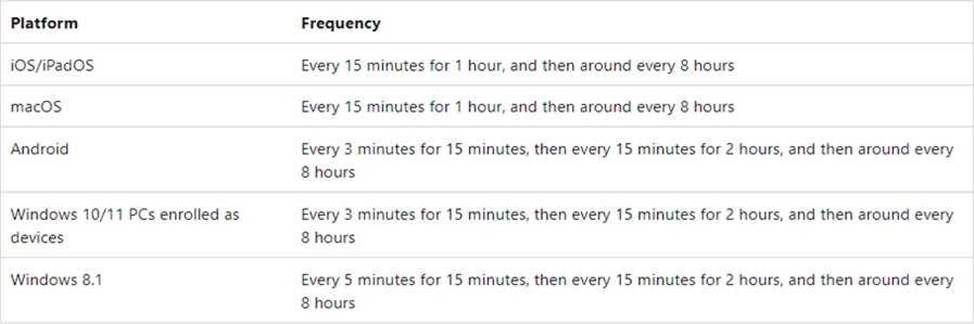
If devices recently enroll, then the compliance, non-compliance, and configuration check-in runs more frequently. The check-ins are estimated at:
Windows 10: Every 3 minutes for 15 minutes, then every 15 minutes for 2 hours, and then around every 8 hours
Box 2: Every 15 minutes for one hour, and then every eight hours
iOS/iPadOS: Every 15 minutes for 1 hour, and then around every 8 hours
Reference: https://docs.microsoft.com/en-us/mem/intune/configuration/device-profile-troubleshoot
HOTSPOT
You have a Microsoft 365 subscription that contains the devices shown in the following table.

You plan to enroll the devices in Microsoft Intune.
How often will the compliance policy check-ins run after each device is enrolled in Intune? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.


Explanation:
Box 1: Every three minutes for 15 minutes, then every 15 minutes for two hours, and then around every eight hours
If devices recently enroll, then the compliance, non-compliance, and configuration check-in runs more frequently. The check-ins are estimated at:
Windows 10: Every 3 minutes for 15 minutes, then every 15 minutes for 2 hours, and then around every 8 hours

Box 2: Every 15 minutes for one hour, and then every eight hours
iOS/iPadOS: Every 15 minutes for 1 hour, and then around every 8 hours
Reference: https://docs.microsoft.com/en-us/mem/intune/configuration/device-profile-troubleshoot
HOTSPOT
Your network contains an Active Directory domain named adatum.com. The domain contains two computers named Computer1 and Computer2 that run Windows 10. Remote Desktop is enabled on Computer2.
The domain contains the user accounts shown in the following table.
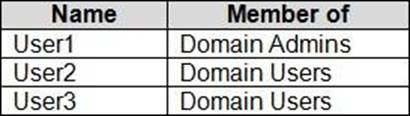
Computer2 contains the local groups shown in the following table.
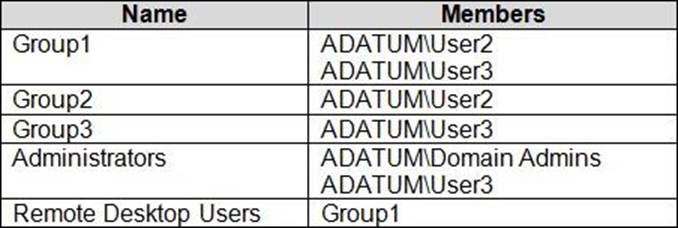
The relevant user rights assignments for Computed are shown in the following table.
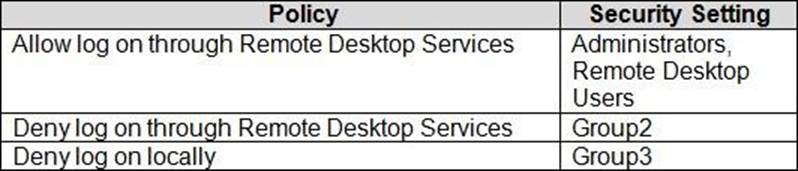
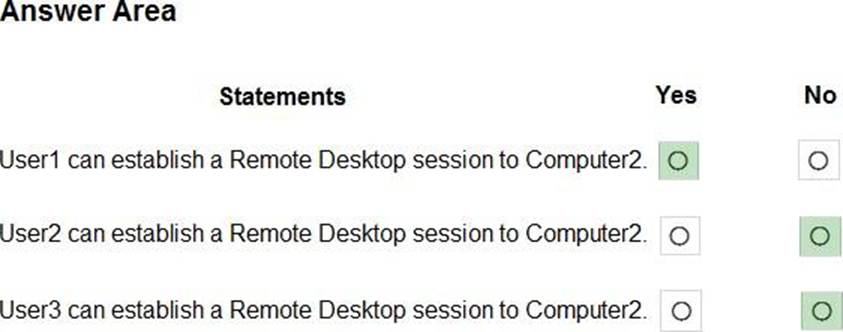
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You need to meet the technical requirements for the iOS devices.
Which object should you create in Intune?
- A . A compliance policy
- B . An app protection policy
- C . A Deployment profile
- D . A device configuration profile
D
Explanation:
Reference:
https://docs.microsoft.com/en-us/intune/device-restrictions-configure
https://docs.microsoft.com/en-us/intune/device-restrictions-ios
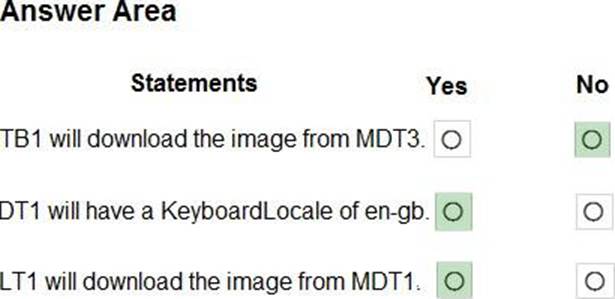
HOTSPOT
You have the Microsoft Deployment Toolkit (MDT) installed in three sites as shown in the following table.
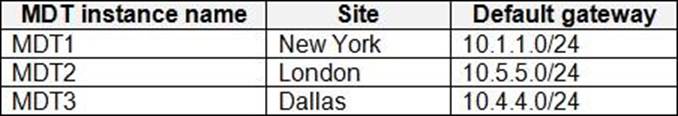
You use Distributed File System (DFS) Replication to replicate images in a share named Production.
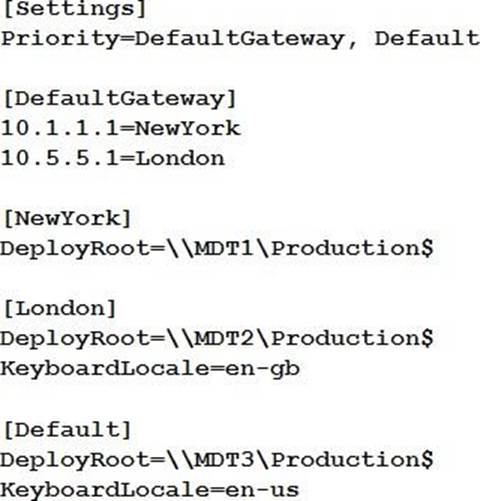
You configure the following settings in the Bootstrap.ini file.
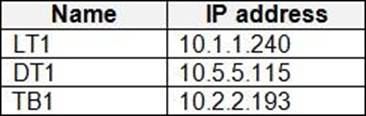
You plan to deploy Windows 10 to the computers shown in the following table.
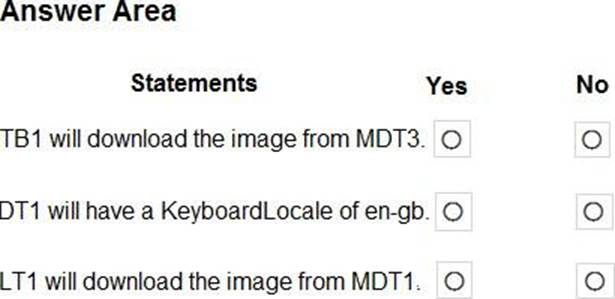
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have the devices shown in the following table.
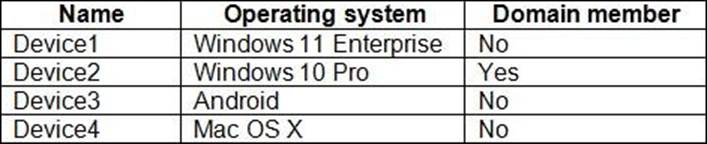
You plan to implement Microsoft Defender for Endpoint.
You need to identify which devices can be onboarded to Microsoft Defender for Endpoint.
What should you identify?
- A . Device1 only
- B . Device2 only
- C . Device1, Device2 only
- D . Device1, Device2, and Device3 only
- E . Device1, Device2, Device3, and Device4
D
Explanation:
Here is the list of Windows versions. Win10 and Win11 supported. The sentence "(standalone or as part of other Microsoft 365 plans)" excludes the domain needs. https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/minimum-requirements?view=o365-worldwide
Here is the link for Android. No information about the specific version therefore it is supported. https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint-android?view=o365-worldwide
Here is the link for MacOS
System requirements: 14 (Sonoma), 13 (Ventura), 12 (Monterey). MAC OS X is older therefore unsupported.
https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint-mac?view=o365-worldwide
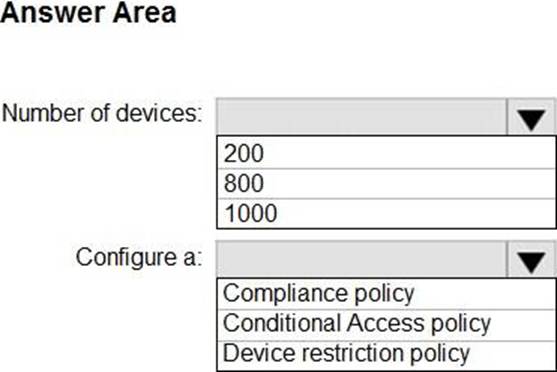
HOTSPOT
You have a Microsoft 365 subscription that contains 1,000 iOS devices.
The devices are enrolled in Microsoft Intune as follows:
• Two hundred devices are enrolled by using the Intune Company Portal.
• Eight hundred devices are enrolled by using Apple Automated Device Enrollment (ADE). You create an iOS/iPadOS software updates policy named Policy 1 that is configured to install iOS/iPadOS 15.5.
How many iOS devices will Policy1 update, and what should you configure to ensure that only iOS/iPadOS 15.5 is installed? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
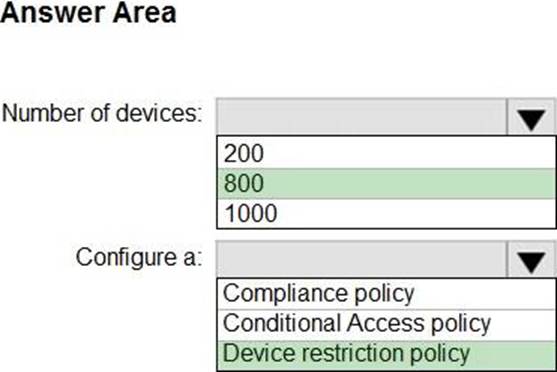
Explanation:
Policy 1 will update 800 iOS devices that are enrolled by using Apple Automated Device Enrollment (ADE). This is because ADE devices are supervised devices that support software update policies in Intune1. Devices that are enrolled by using the Intune Company Portal are not supervised devices
and do not support software update policies2.
To ensure that only iOS/iPadOS 15.5 is installed, you should configure a device restriction policy that restricts visibility of software updates. This will prevent users from manually updating the OS to a newer version than the one you specified in Policy 11. You can use the Deployment Workbench to create and assign a device restriction profile to your ADE devices3.
HOTSPOT
You have two computers that run Windows 10.
The computers are enrolled in Microsoft Intune as shown in the following table.
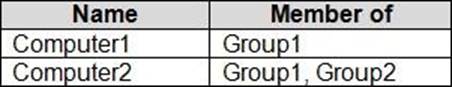
Windows 10 update rings are defined in Intune as shown in the following table.
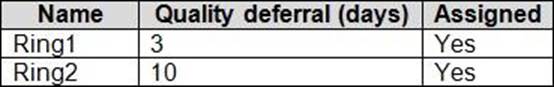
You assign the update rings as shown in the following table.
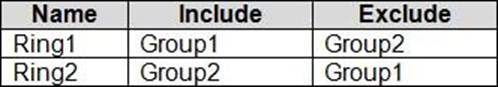
What is the effect of the configurations on Computer1 and Computer2? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
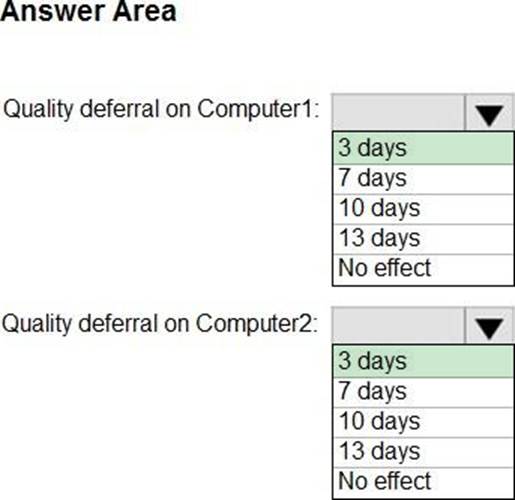
Explanation:
Computer1 and Computer2 are members of Group1. Ring1 is applied to Group1.
Note: The term "Exclude" is misleading. It means that the ring is not applied to that group, rather than that group being blocked.
Reference:
https://docs.microsoft.com/en-us/windows/deployment/update/waas-wufb-intune
https://allthingscloud.blog/configure-windows-update-business-using-microsoft-intune/
You have a Microsoft 365 subscription.
You plan to use Windows Autopilot to provision 25 Windows 11 devices.
You need to configure the Out-of-box experience (OOBE) settings.
What should you create in the Microsoft Intune admin center?
- A . an enrollment status page (ESP)
- B . a deployment profile
- C . a compliance policy
- D . a PowerShell script
- E . a configuration profile
You have an Azure AD tenant named contoso.com.
You need to ensure that users are not added automatically to the local Administrators group when they join their Windows 11 device to contoso.com.
What should you configure?
- A . Windows Autopilot
- B . provisioning packages for Windows
- C . Security defaults in Azure AD
- D . Device settings in Azure AD
D
Explanation:
To ensure that users are not added automatically to the local Administrators group when they join their Windows 11 device to contoso.com, you should configure the Device settings in Azure AD. The Device settings allow you to manage which users can join devices to Azure AD and whether they are added as local administrators or standard users. By default, users who join devices to Azure AD are added to the local Administrators group, but you can change this setting to None or Selected1.
The other options are not relevant for this scenario because:
Windows Autopilot is a service that allows you to pre-configure new devices and enroll them automatically to Azure AD and Microsoft Intune. It does not control the local administrator role of the users who join the devices2.
Provisioning packages for Windows are files that contain custom settings and policies that can be applied to Windows devices during the setup process. They do not affect the Azure AD join process or the local administrator role of the users3.
Security defaults in Azure AD are a set of basic identity security mechanisms that are enabled by default to protect your organization from common attacks. They do not include any settings related to device management or local administrator role4.
Reference: Manage device identities using the Microsoft Entra admin center, Windows Autopilot, Provisioning packages for Windows 10, What are security defaults?
