Practice Free MD-102 Exam Online Questions
You use the Microsoft Deployment Toolkit (MDT) to deploy Windows 11.
You create a new task sequence by using the Standard Client Task Sequence template to deploy
Windows 11 Enterprise to new computers. The computers have a single hard disk.
You need to modify the task sequence to create a system volume and a data volume.
Which phase should you modify in the task sequence?
- A . Initialization
- B . State Restore
- C . Preinstall
- D . Postinstall
HOTSPOT
To which devices do Policy1 and Policy2 apply? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/intune/device-profile-assign
You have a Microsoft 365 subscription.
You need provide a user the ability to disable Security defaults and principle of least privilege.
Which role should you assign to the user?
- A . Global Administrator
- B . Conditional Access Administrator
- C . Security Administrator
- D . Intune Administrator
B
Explanation:
To enable or disable security defaults in your directory, sign in to the Azure portal as a security administrator, Conditional Access administrator, or global administrator.
Note: Conditional Access Administrator
Users with this role have the ability to manage Azure Active Directory Conditional Access settings.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults
You have computer that run Windows 10 and connect to an Azure Log Analytics workspace. The workspace is configured to collect all available events from Windows event logs.
The computers have the logged events shown in the following table.
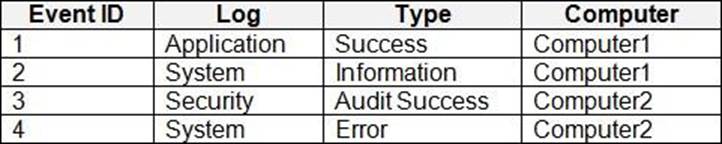
Which events are collected in the Log Analytics workspace?
- A . 1 only
- B . 2 and 3 only
- C . 1 and 3 only
- D . 1, 2, and 4 on
- E . 1, 2, 3, and 4
E
Explanation:
All events from Windows event logs are collected in the Log Analytics workspace, regardless of the event level or source. Therefore, events 1, 2, 3, and 4 are all collected in the workspace.
Reference: https://docs.microsoft.com/en-us/azure/azure-monitor/agents/data-sources-windows-events
HOTSPOT
You need to recommend a solution to meet the device management requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
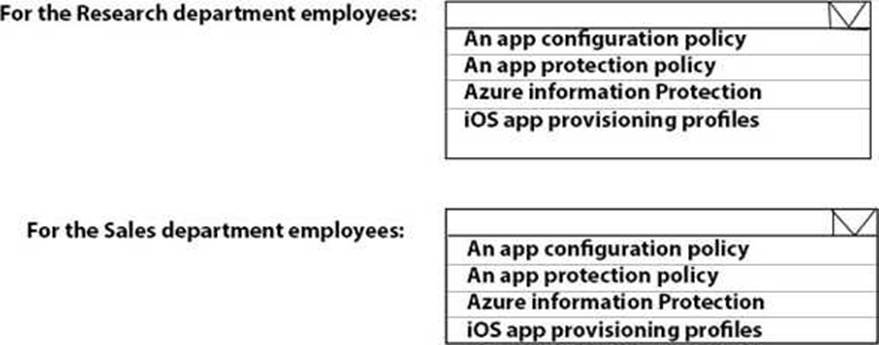
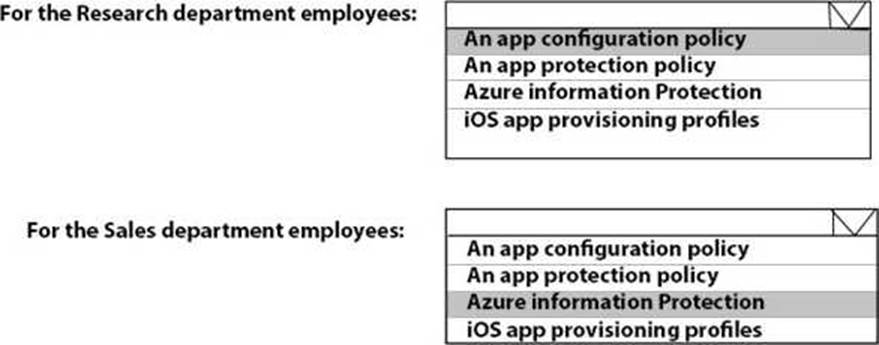
Explanation:
Reference:
https://github.com/MicrosoftDocs/IntuneDocs/blob/master/intune/app-protection-policy.md
https://docs.microsoft.com/en-us/azure/information-protection/configure-usage-rights#do-not-forward-option-for-emails
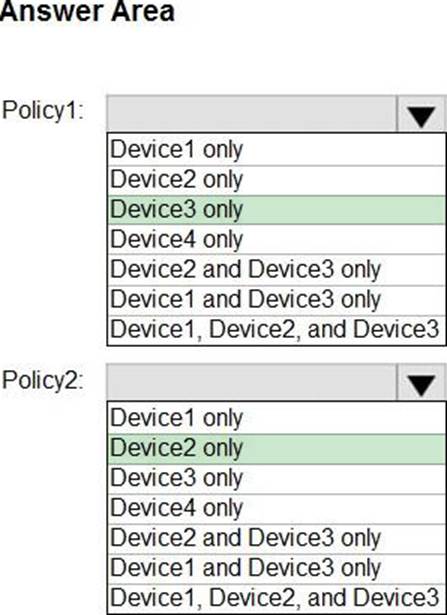
HOTSPOT
You have devices enrolled in Microsoft Intune as shown in the following table.
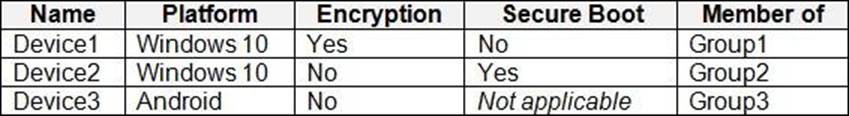
Intune includes the device compliance policies shown in the following table.
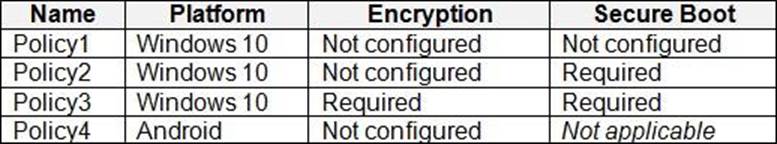
The device compliance policies have the assignments shown in the following table.
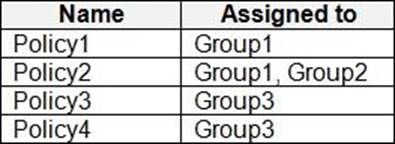
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
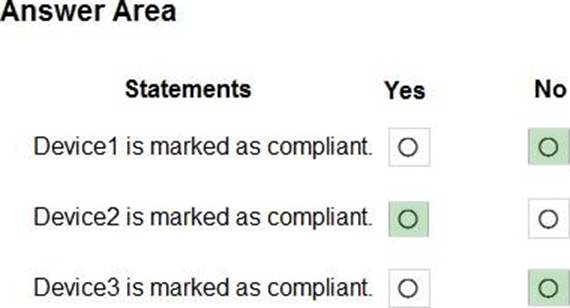
Explanation:
Device1 is marked as compliant = No
Device2 is marked as compliant = Yes
Device3 is marked as compliant = No
Device1 is marked as noncompliant because it does not meet the minimum OS version requirement of Policy1, which is 11.0.0. Device1 has an OS version of 10.0.0, which is lower than the required version1.
Device2 is marked as compliant because it meets all the requirements of Policy2, which are: minimum OS version of 10.0.0, password required, and encryption enabled. Device2 has an OS version of 11.0.0, a password set, and encryption enabled1.
Device3 is marked as noncompliant because it does not meet the encryption requirement of Policy3, which is enabled. Device3 has encryption disabled1.
Your company has devices enrolled in Microsoft Intune as shown in the following table.
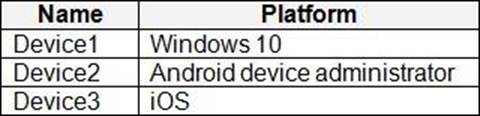
In Microsoft Endpoint Manager, you define the company’s network as a location named Location1.
Which devices can use network location-based compliance policies?
- A . Device2 and Device3 only
- B . Device2 only
- C . Device1 and Device2 only
- D . Device1 only
- E . Device1, Device2, and Device3
E
Explanation:
Intune supported operating systems
Intune supports devices running the following operating systems (OS):
iOS
Android
Windows
macOS
Note: View the device compliance settings for the different device platforms:
Android device administrator
Android Enterprise
iOS
macOS
Windows Holographic for Business
Windows 8.1 and later
Windows 10/11
Reference:
https://docs.microsoft.com/en-us/mem/intune/fundamentals/supported-devices-browsers
https://docs.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started
HOTSPOT
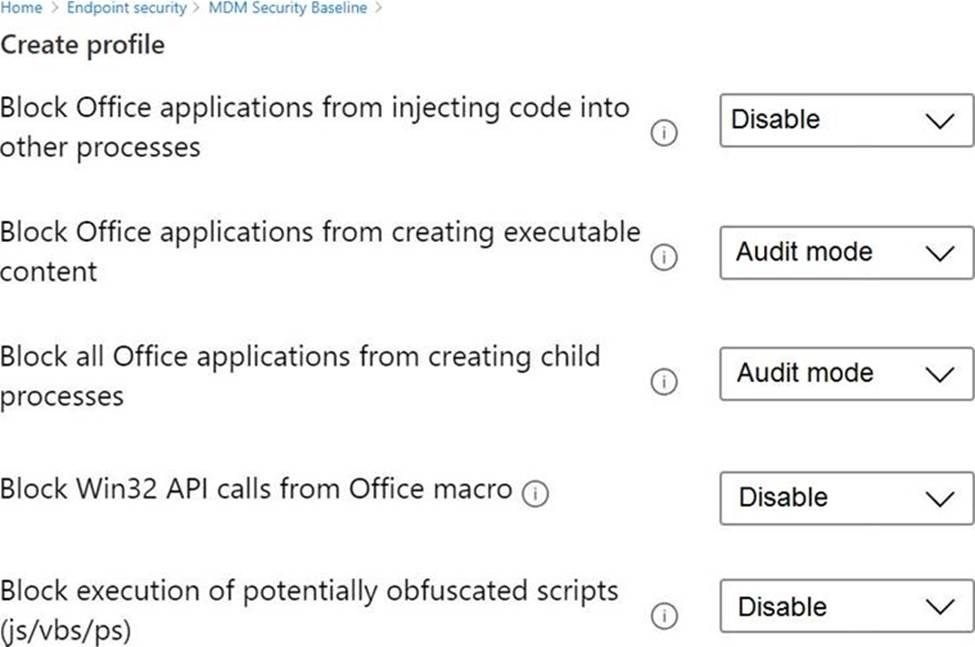
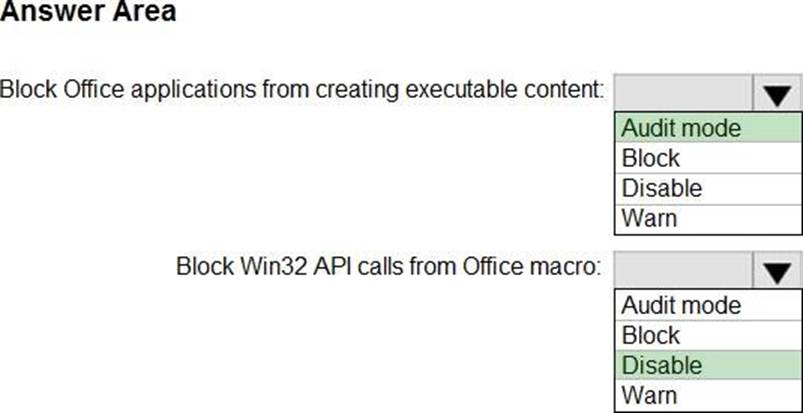
You have the MDM Security Baseline profile shown in the MDM exhibit. (Click the MDM tab.)
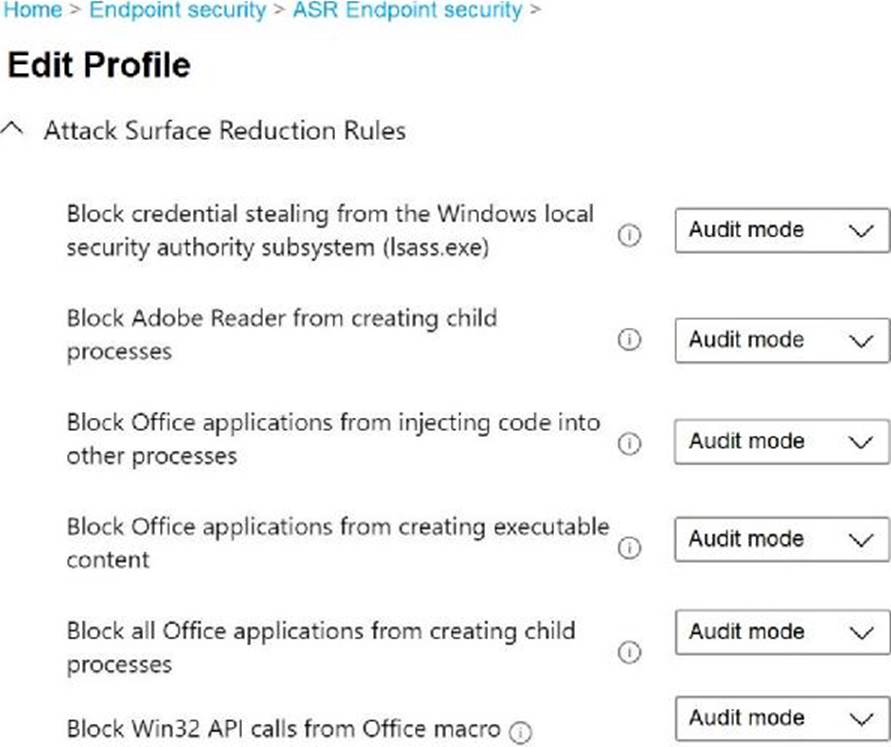
You have the ASR Endpoint Security profile shown in the ASR exhibit. (Click the ASR tab.)
You plan to deploy both profiles to devices enrolled in Microsoft Intune.
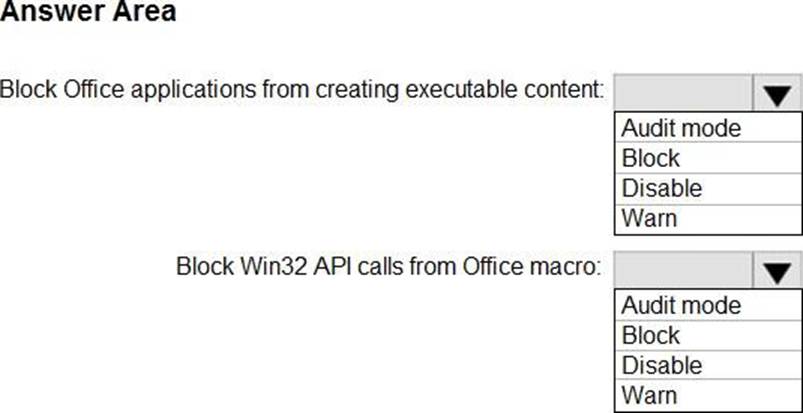
You need to identify how the following settings will be configured on the devices:
• Block Office applications from creating executable content
• Block Win32 API calls from Office macro
• Currently, the settings are disabled locally on each device.
What are the effective settings on the devices? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 tenant that contains the objects shown in the following table.
You are creating a compliance policy named Compliance1.
Which objects can you specify in Compliance1 as additional recipients of noncompliance notifications?
- A . Group3 and Group4 only
- B . Group3, Group4, and Admin1 only
- C . Group1, Group2, and Group3 only
- D . Group1, Group2, Group3, and Group4 only
- E . Group1, Group2, Group3, Group4, and Admin1
C
Explanation:
Reference:
https://www.ravenswoodtechnology.com/microsoft-intune-compliance-notifications/
https://docs.microsoft.com/en-us/microsoft-365/admin/create-groups/compare-groups?view=o365-worldwide
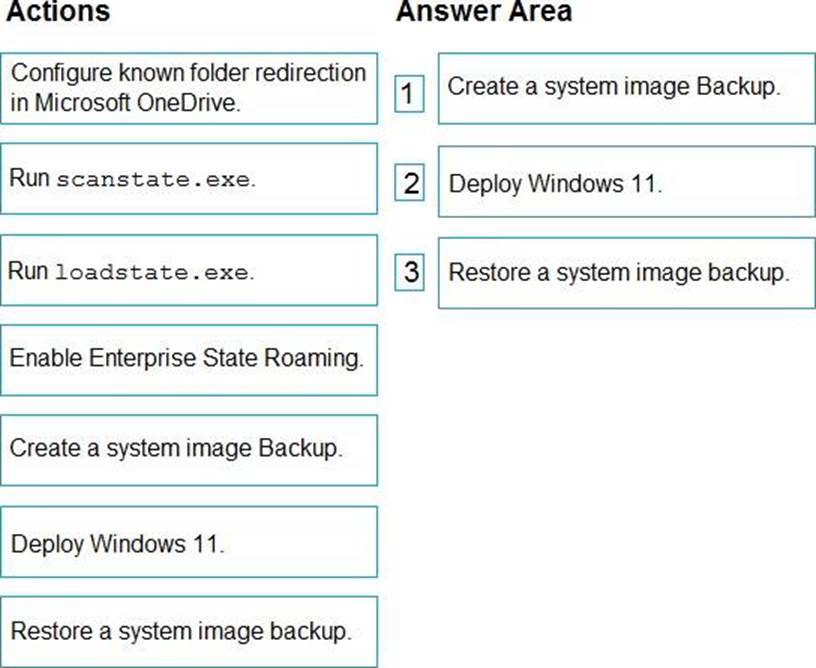
DRAG DROP
You have 100 computers that run Windows 10.
You plan to deploy Windows 11 to the computers by performing a wipe and load installation.
You need to recommend a method to retain the user settings and the user data.
Which three actions should you recommend be performed in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.