Practice Free MD-102 Exam Online Questions
HOTSPOT
Your on-premises network contains an Active Directory domain named contoso.com.
The domain contains a user account named Admin1 and the resources shown in the following table.
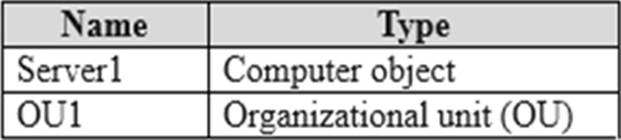
You have a Microsoft 365 E5 subscription.
You have a Microsoft Entra tenant that syncs with contoso.com.
Admin! plans to use Windows Autopilot to deploy 10X3 Windows 11 devices.
The deployment must meet the following requirements:
• The devices must be Microsoft Entra hybrid joined during the deployment.
• Computer objects must be created in 0U1.
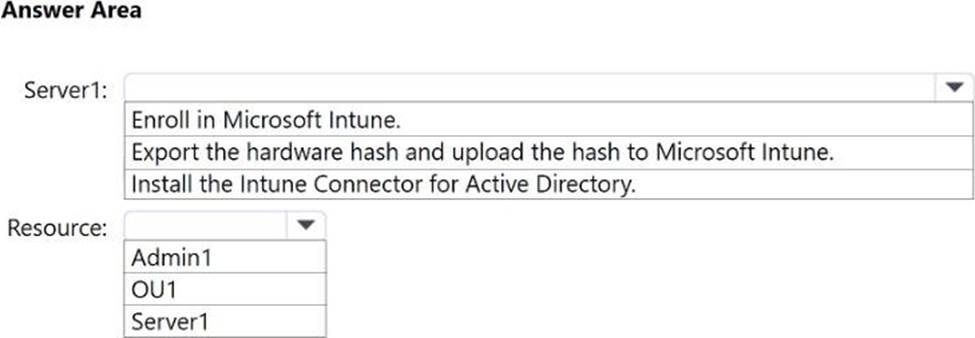
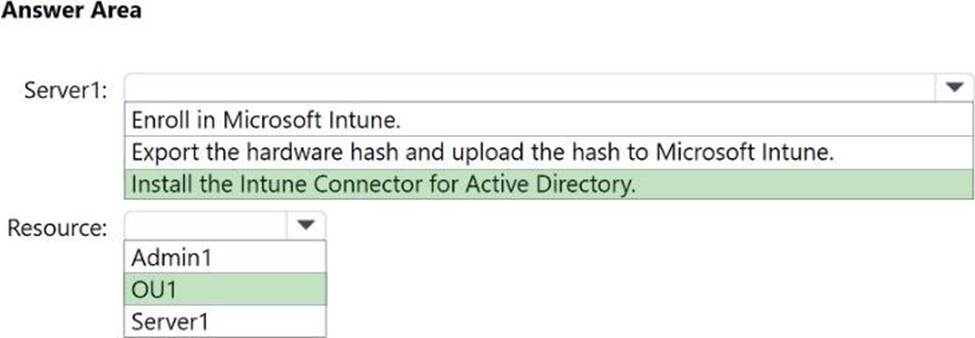
You need to configure Server1 and Active Directory delegation to support the deployment.
How should you configure Server1, and on which resource should you configure delegated permissions? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that contains a user named User1 and 500 Windows devices enrolled in Microsoft Intune.
You configure an attack surface reduction {ASR) rule and enable the rule in Warn mode.
User1 downloads a file named file1.exe. When User1 attempts to run file1.exe he receives a prompt that the content has been blocked. The user unblocks the content.
How much time will pass until the user is prompted next to unblock the content?
- A . 10 minutes
- B . one hour
- C . 24 hours
- D . one week
You have a Microsoft 365 subscription that uses Microsoft Intune Suite.
You use Microsoft Intune to manage devices.
You need to ensure that the startup performance of managed Windows 11 devices is captured and available for review in the Intune admin center.
What should you configure?
- A . the Azure Monitor agent
- B . a device compliance policy
- C . a Conditional Access policy
- D . an Intune data collection policy
DRAG DROP
You have SOO Windows 10 devices enrolled in Microsoft Intune.
You plan to use Exploit protection in Microsoft Intune to enable the following system settings on the devices:
• Data Execution Prevention (DEP)
• Force randomization for images (Mandatory ASlR)
You need to configure a Windows 10 device that will be used to create a template file.
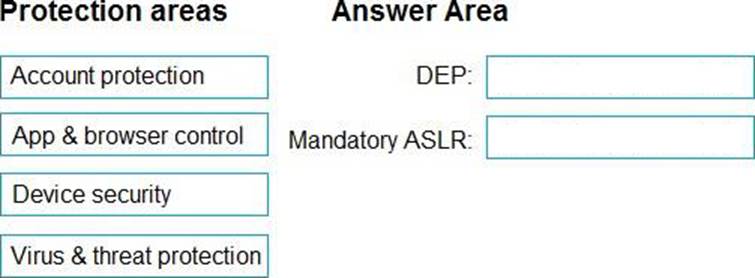
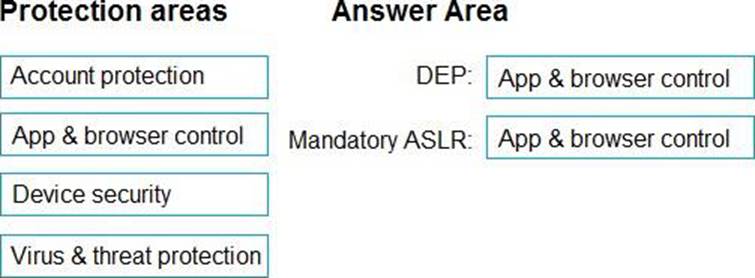
Which protection areas on the device should you configure in the Windows Security app before you create the template file? To answer, drag the appropriate protection areas to the correct settings. Each protection area may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
Explanation:
Exploit protection is a feature that helps protect against malware that uses exploits to infect devices and spread. Exploit protection consists of many mitigations that can be applied to either the operating system or individual apps1.
To configure a Windows 10 device that will be used to create a template file for Exploit protection, you need to configure the following protection areas on the device in the Windows Security app: DEP: Device security. Data Execution Prevention (DEP) is a mitigation that prevents code from running in memory regions marked as non-executable. You can enable DEP system-wide or for specific apps in the Device security section of the Windows Security app1.
Mandatory ASLR: App & browser control. Force randomization for images (Mandatory ASLR) is a mitigation that randomizes the location of executable images in memory, making it harder for attackers to predict where to inject code. You can enable Mandatory ASLR system-wide or for specific apps in the App & browser control section of the Windows Security app1.
HOTSPOT
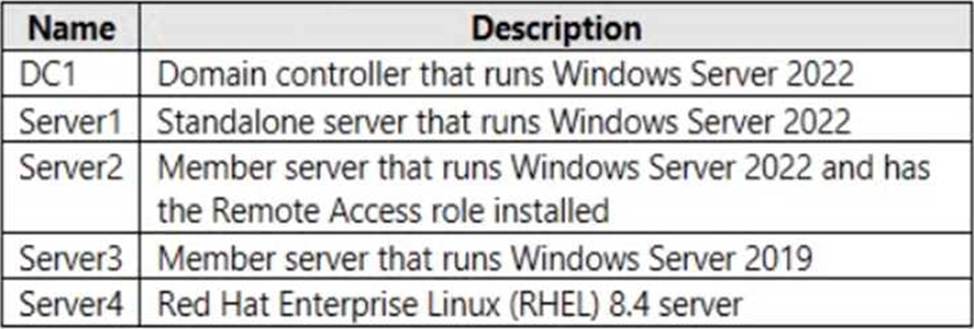
You have the on-premises servers shown in the following table.
You have a Microsoft 365 E5 subscription that contains Android and iOS devices. All the devices are managed by using Microsoft Intune.
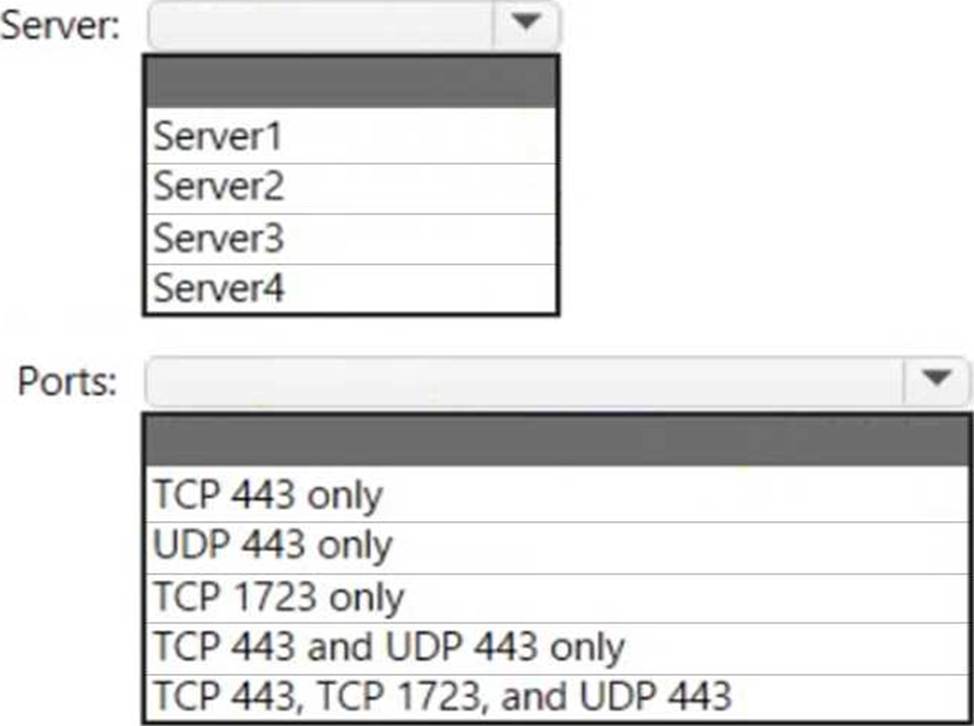
You need to implement Microsoft Tunnel for Intune. The solution must minimize the number of open firewall ports.
To which server can you deploy a Tunnel Gateway server, and which inbound ports should be allowed on the server to support Microsoft Tunnel connections? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
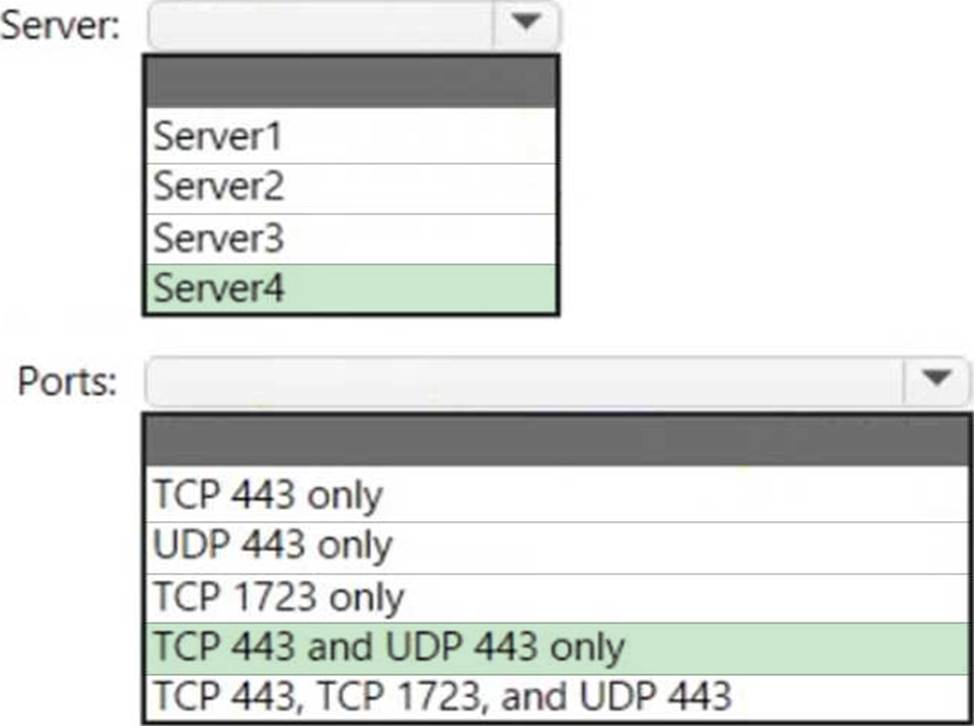
Box 1: Server4
Microsoft Tunnel is a VPN gateway solution for Microsoft Intune that runs in a container on Linux and allows access to on-premises resources from iOS/iPadOS and Android Enterprise devices using modern authentication and Conditional Access.
Box 2: TCP 443 and UDP 443 only
Some traffic goes to your public facing IP address for the Tunnel. The VPN channel will use TCP, TLS, UDP, and DTLS over port 443.
By default, port 443 is used for both TCP and UDP, but this can be customized via the Intune Saerver Configuration C Server port setting. If changing the default port (443) ensure your inbound firewall rules are adjusted to the custom port.
Incorrect:
TCP 1723 is not used.
Reference: https://docs.microsoft.com/en-us/mem/intune/protect/microsoft-tunnel-overview
Note: This section contains one or more sets of questions with the same scenario and problem. Each question presents a unique solution to the problem. You must determine whether the solution meets the stated goals. More than one solution in the set might solve the problem. It is also possible that none of the solutions in the set solve the problem.
After you answer a question in this section, you will NOT be able to return. As a result, these questions do not appear on the Review Screen.
You have a Microsoft 365 E5 subscription. The subscription contains devices that are Microsoft Entra joined and enrolled in Microsoft Intune.
You create a user named User1.
You need to ensure that User1 can rotate BitLocker recovery keys by using Intune.
Solution: From the Microsoft Entra admin center, you assign the Cloud Device Administrator role to User1.
Does this meet the goal?
- A . Yes
- B . No
You have a Microsoft Entra tenant that contains the devices shown in the following table.
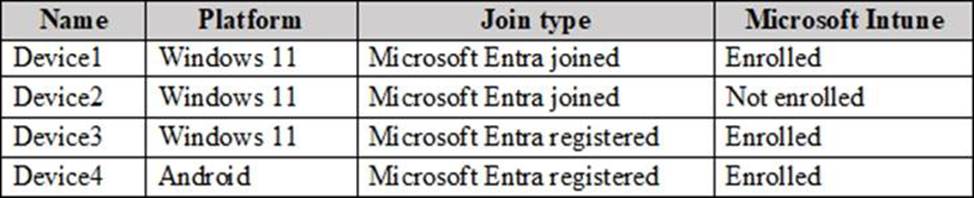
On which devices can you implement Endpoint Privilege Management (EPM)?
- A . Device1 only
- B . Device1 and Device2 only
- C . Device1 and Device3 only
- D . Device1, Device3, and Device4 only
- E . Device1, Device2. Device3, and Device4
