Practice Free 300-410 Exam Online Questions
What are two MPLS label characteristics? (Choose two.)
- A . The label edge router swaps labels on the received packets.
- B . Labels are imposed in packets after the Layer 3 header.
- C . LDP uses TCP for reliable delivery of information.
- D . An MPLS label is a short identifier that identifies a forwarding equivalence class.
- E . A maximum of two labels can be imposed on an MPLS packet.
C,D
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/multiprotocol-label-switching-mpls/mpls/4649-mpls-faq-4649.html
A network administrator opens a telnet connection to the router and gets the message:
R1#telnet 10.1.1.2
Trying 10 1.1 2 Open
(Connection to 10.1.1.2 closed by foreign host)
Router R2 is configured with enable secret and password commands.
Which action resolves the issue?
- A . Configure the logging synchronous command on line vty.
- B . Configure the exec command on line vty.
- C . Configure the login local command on line vty
- D . Configure the enable password command on line vty.
Refer to the exhibit.
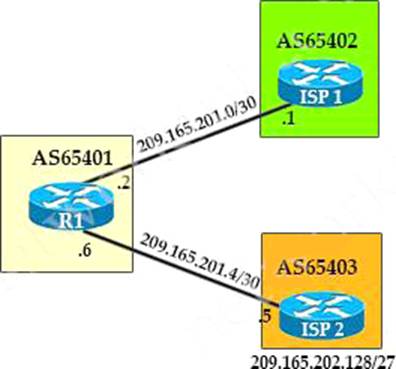
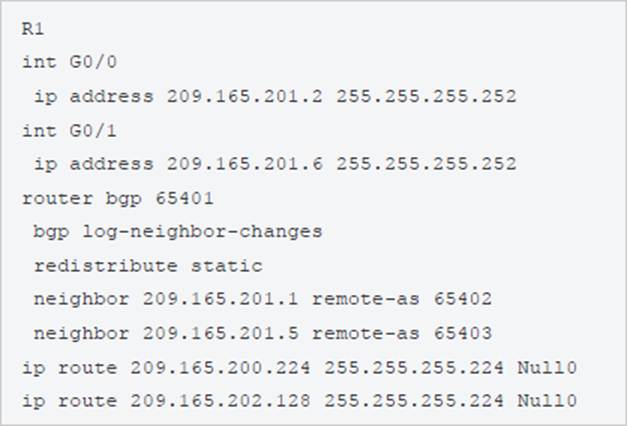
A company with autonomous system number AS65401 has obtained IP address block 209.165.200.224/27 fro, ARIN. The company needed more IP addresses and was assigned block 209.165.202.128/27 from ISP2. An engineer is ISP1 reports they are receiving ISP2 routes from AS65401.
Which configuration onR1 resolves the issue?
- A . access-list 10 deny 209.165.202.128 0.0.0.31
access-list 10 permit any
!
router bgp 65401
neighbor 209.165.201.1 distribute-list 10 out - B . access-list 10 deny 209.165.202.128 0.0.0.31
access-list 10 permit any
!
router bgp 65401
neighbor 209.165.201.1 distribute-list 10 in - C . ip route 209.165.200.224 255.255.255.224 209.165.201.1
ip route 209.165.202.128 255.255.255.224 209.165.201.5 - D . ip route 0.0.0.0 0.0.0.0 209.165.201.1
ip route 0.0.0.0 0.0.0.0 209.165.201.5
A
Explanation:
https://www.cisco.com/c/en/us/support/docs/ip/border-gateway-protocol-bgp/23675-27.html
Which 0S1 model is used to insert an MPLS label?
- A . between Layer 5 and Layer 6
- B . between Layer 1 and Layer 2
- C . between Layer 3 and Layer 4
- D . between Layer 2 and Layer 3
An engineer configured the wrong default gateway for the Cisco DNA Center enterprise interface during the install.
Which command must the engineer run to correct the configuration?
- A . sudo maglev-config update
- B . sudo maglev install config update
- C . sudo maglev reinstall
- D . sudo update config install
Refer to the exhibit.
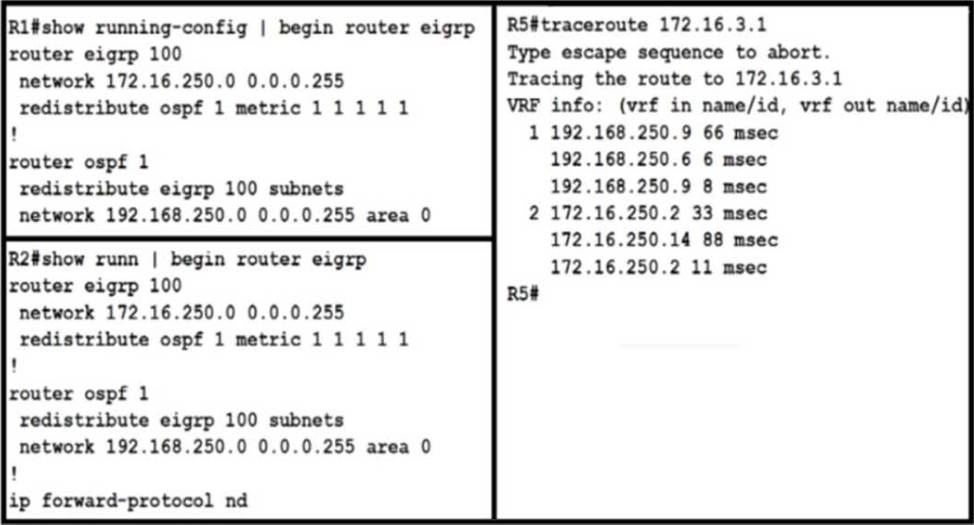
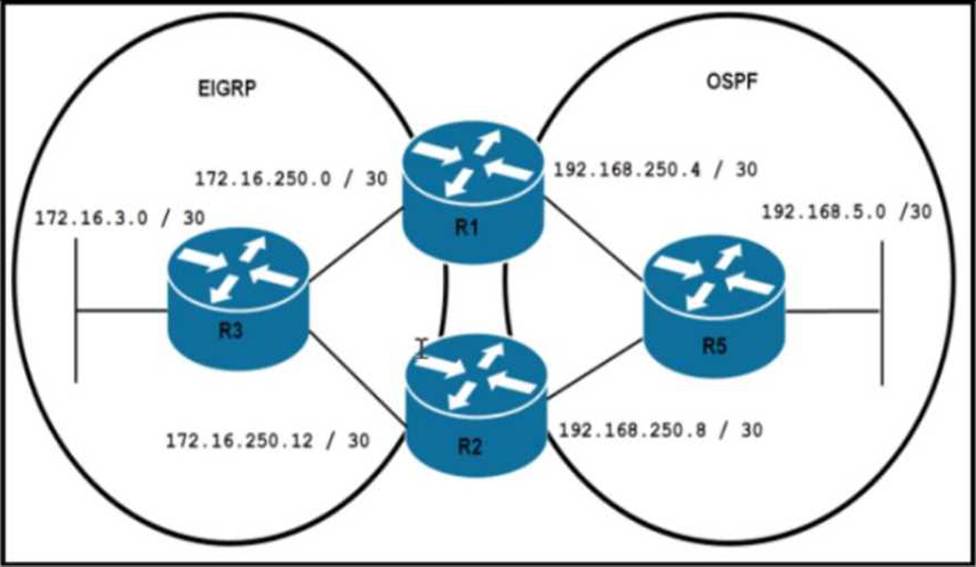
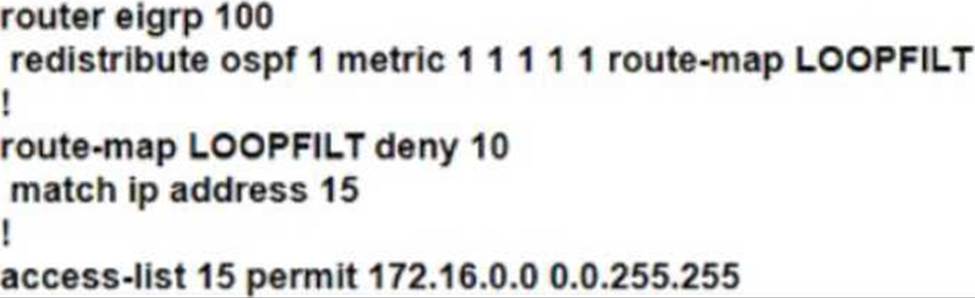
An engineer Is troubleshooting a routing loop on the network to reach the 172.16.3.0/16 from the OSPF domain.
Which configuration on router R1 resolves the Issue?
A)
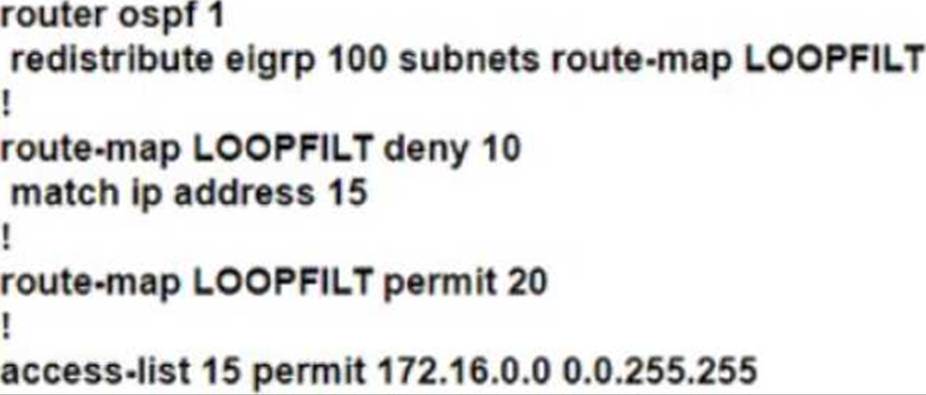
B)
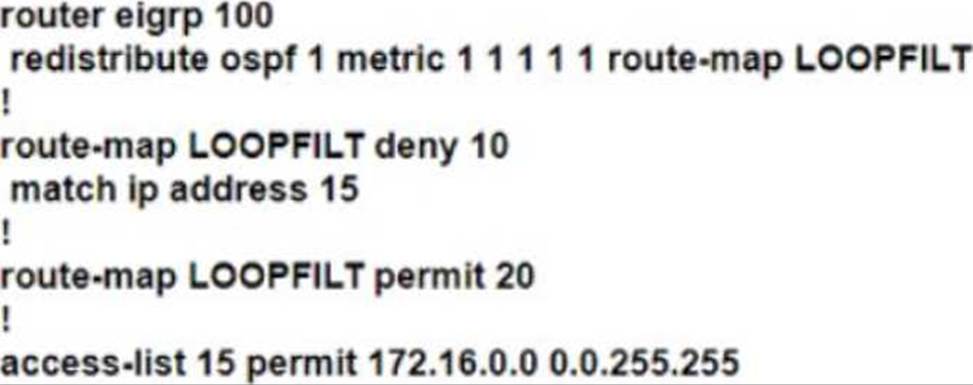
C)
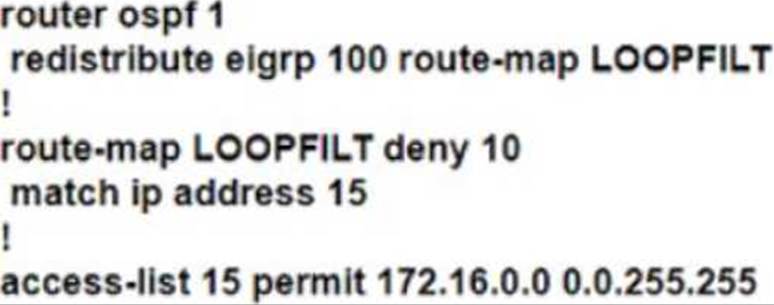
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Refer to the exhibit.
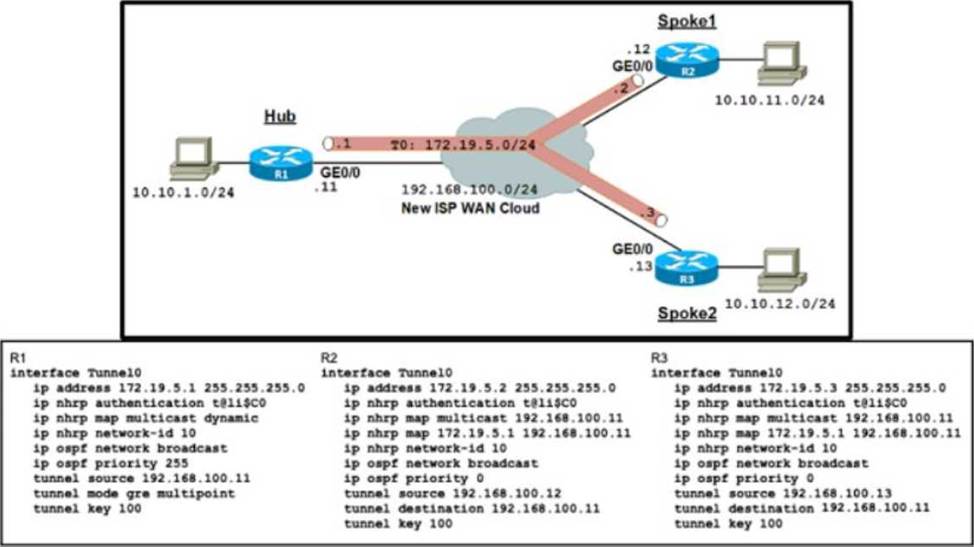
An organization is installing a new L3 MPLS link to establish DM VPN Phase 2 tunnels between the hub and two spoke routers.
Which additional configuration should the engineer implement on each device to achieve optimal routing between the spokes?
A)
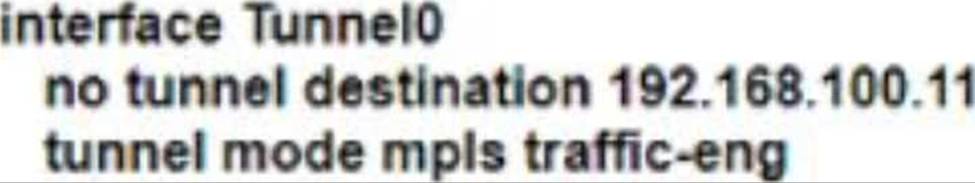
B)
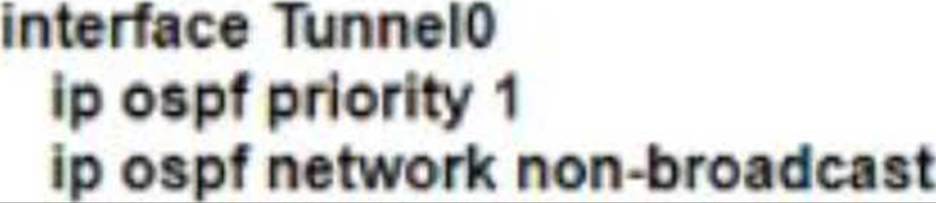
C)
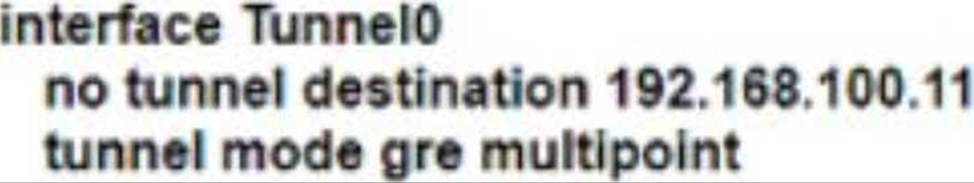
D)

- A . Option A
- B . Option B
- C . Option C
- D . Option D
Refer to the exhibit.
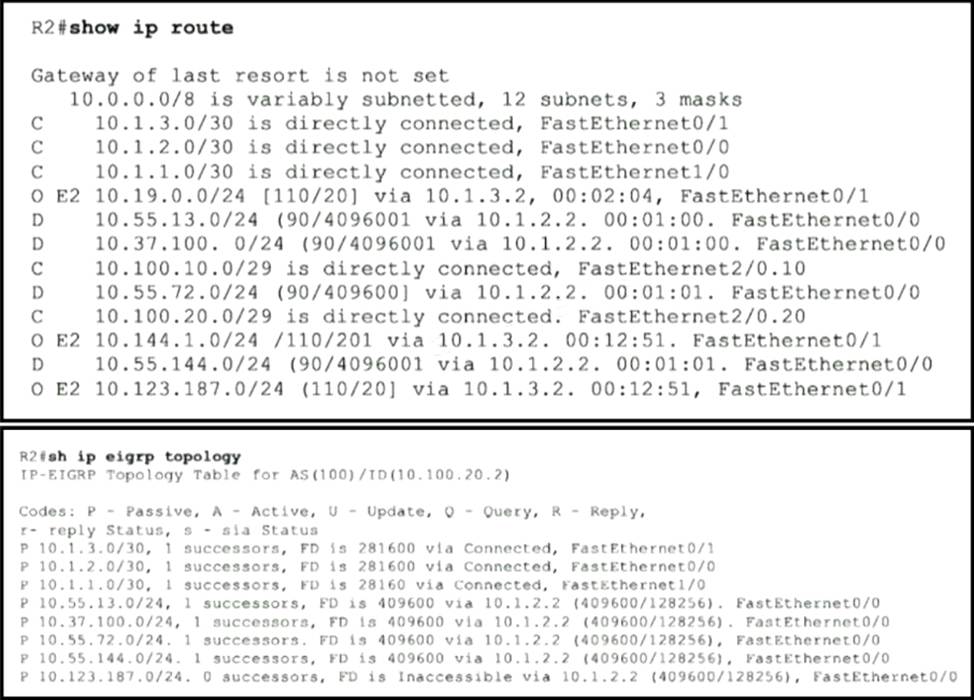
Router R2 should be learning the route for 10.123.187.0/24 via EIGRP.
Which action resolves the issue without introducing more issues?
- A . Use distribute-list to modify the route as an internal EIGRP route
- B . Redistribute the route in EIGRP with metric, delay, and reliability
- C . Use distribute-list to filter the external router in OSPF
- D . Remove route redistribution in R2 for this route in OSPF
Which component of MPLS VPNs is used to extend the IP address so that an engineer is able to identify to which VPN it belongs?
- A . VPNv4 address family
- B . RD
- C . RT
- D . LDP
B
Explanation:

Refer to the exhibit.
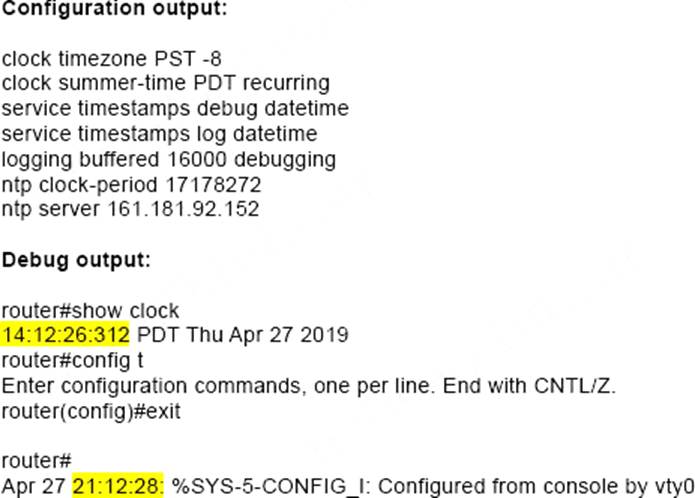
A network administrator configured NTP on a Cisco router to get synchronized time for system and logs from a unified time source The configuration did not work as desired.
Which service must be enabled to resolve the issue?
- A . Enter the service timestamps log datetime localtime global command.
- B . Enter the service timestamps log datetime synchronize global command.
- C . Enter the service timestamps log datetime console global command.
- D . Enter the service timestamps log datetime clock-period global command
A
Explanation:
If a router is configured to get the time from a Network Time Protocol (NTP) server, the times in the router’s log entries may be different from the time on the system clock if the [localtime] option is not in the service timestamps log command. To solve this issue, add the [localtime] option to the service timestamps log command. The times should now be synchronized between the system clock and the log message timestamps.
Reference: https://community.cisco.com/t5/networking-documents/router-log-timestamp-entries-are-different-from-the-system-clock/ta-p/3132258
