Practice Free 300-410 Exam Online Questions
A network engineer is investigating a flapping (up/down) interface issue on a core switch that is synchronized to an NTP server. Log output currently does not show the time of the flap.
Which command allows the logging on the switch to show the time of the flap according to the clock on the device?
- A . service timestamps log uptime
- B . clock summer-time mst recurring 2 Sunday mar 2:00 1 Sunday nov 2:00
- C . service timestamps log datetime localtime show-timezone
- D . clock calendar-valid
C
Explanation:
By default, Catalyst switches add a simple uptime timestamp to logging messages. This is a cumulative counter that shows the hours, minutes, and seconds since the switch has been booted up
What are the two reasons for RD and VPNv4 addresses in an MPLS Layer 3 VPN? (Choose two.)
- A . RD is prepended to each prefix to make routes unique.
- B . VPN RT communities are used to identify customer unique routes.
- C . When the PE redistributes customer routes into MP-BGP, they must be unique.
- D . They are on a CE device to use for static configuration.
- E . They are used for a BGP session with the CE device.
What are the two reasons for RD and VPNv4 addresses in an MPLS Layer 3 VPN? (Choose two.)
- A . RD is prepended to each prefix to make routes unique.
- B . VPN RT communities are used to identify customer unique routes.
- C . When the PE redistributes customer routes into MP-BGP, they must be unique.
- D . They are on a CE device to use for static configuration.
- E . They are used for a BGP session with the CE device.
Refer to the exhibit.
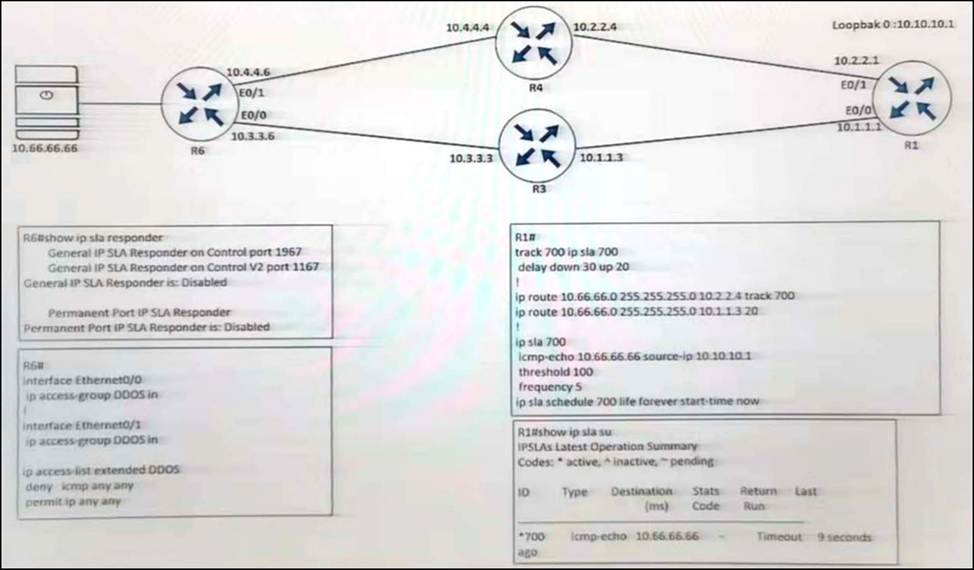
R1 is configured with IP SLA to check the availability of the server behind R6 but it kept failing.
Which configuration resolves the issue?
- A . R6(config)# ip sla responder
- B . R6(config)# ip sla responder udp-echo ip address 10.10.10.1 port 5000
- C . R6(config)# ip access-list extended DDOS
R6(config ext-nac)# 5 permit icmp host 10.66 66.66 host 10.10.10.1 - D . R6(config)# ip access-list extended DDOS
R6(config ext-nac)# 5 permit icmp host 10.10.10.1 host 10.66.66.66
D
Explanation:
In this IP SLA tracking, we don’t need a IP SLA Responder so the command “ip sla responder” on R6 is not necessary.
We also notice that the ACL is blocking ICMP packets on both interfaces E0/0 & E0/1 of R6 so we need to allow ICMP from source 10.10.10.1 to destination 10.66.66.66.
Refer to the exhibit.
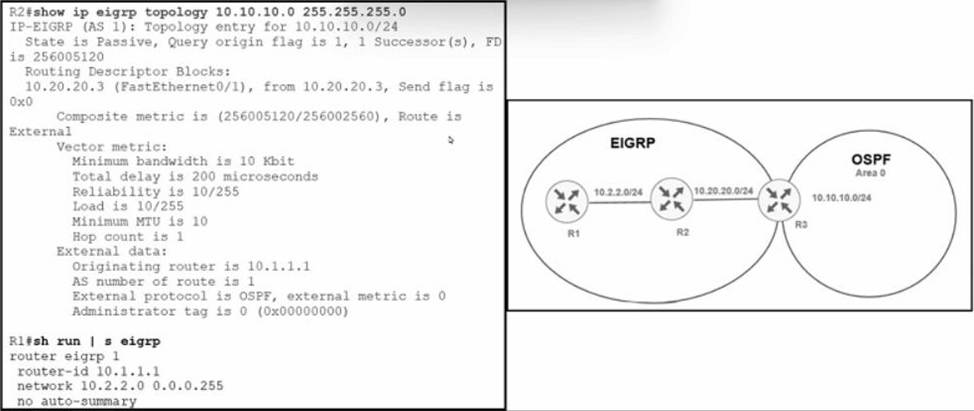
An engineer configured router R3 to redistribute the prefix 10.10.10.0/24 from OSPF into EIGRP R1 has no connectivity to the prefix.
Which action enables receipt of prefixes on R1?
- A . R3 is advertising the 10.20.20 0’24 prefix with a TTL of 1, R3 must set the TTL to 2 for this prefix.
- B . R1 docs not have a neighbor relationship with R2. The EIGRP process should be cleared on R1.
- C . Duplicate router IDs on R1 and R3, R1 should modify its router ID.
- D . R1 is not receiving the next-hop IP address of R3. R2 must enable the network 10 20.20.0V24 within EIGRP.
Refer to the exhibit.
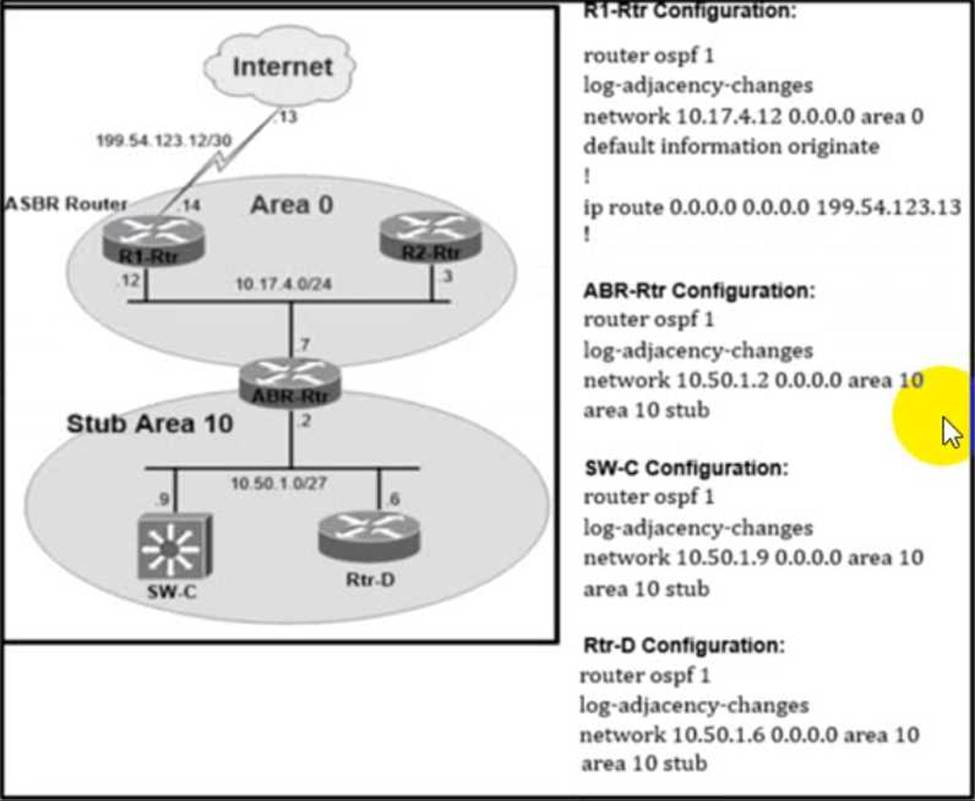
Router ABR-Rtr is not propagating the internet routes in OSPF area 10. which causes internet reachability problems in the area.
Which action resolves the issue?
- A . ABR-Rtr must configure the default-information originate always command.
- B . ABR-Rtr must configure the area 10 stub no-summary command.
- C . ABR-Rtr network type must be broadcast network.
- D . ABR-Rtr must advertise the 0.0.0.0/0 default route in area 10.
A network administrator is tasked to permit http and https traffic only toward the internet from the User1 laptop to adhere to company’s security policy. The administrator can still ping to www.cisco.com.
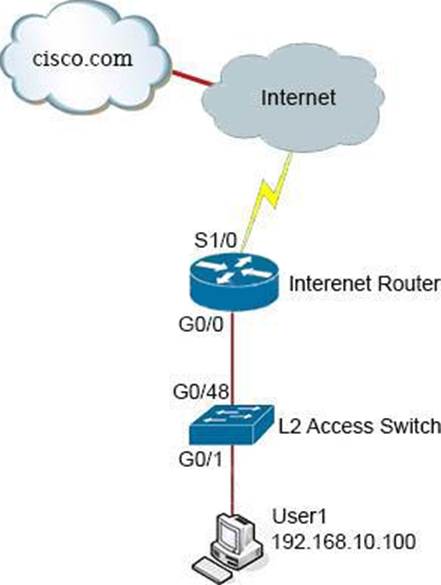
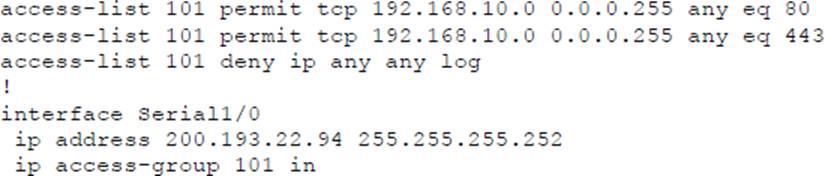
Which interface should the access list 101 be applied to resolve this issue?
- A . Interface G0/48 in the incoming direction
- B . Interface G0/0 in the outgoing direction.
- C . Interface S1/0 in the outgoing direction.
- D . Interface G0/0 in the incoming direction.
Refer to the exhibit.
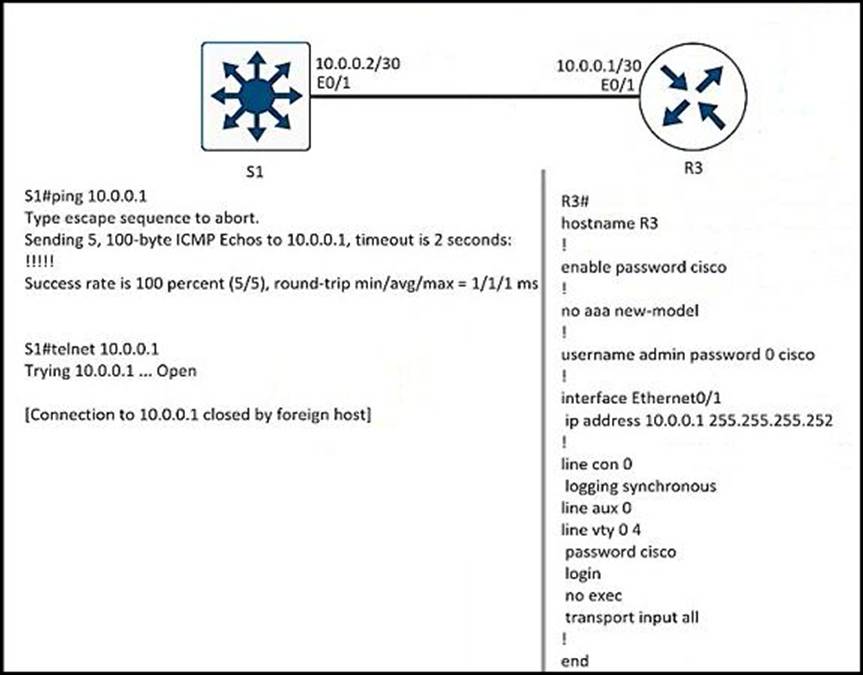
A network engineer cannot remote access R3 using Telnet from switch S1.
Which action resolves the issue?
- A . Allow the inbound connection via the exec command on R3.
- B . Add the transport input telnet command on R3.
- C . Allow to use the ssh -I admin 10.0.0.1 command on the switch.
- D . Add the login admin command on the switch.
Refer to the exhibit.
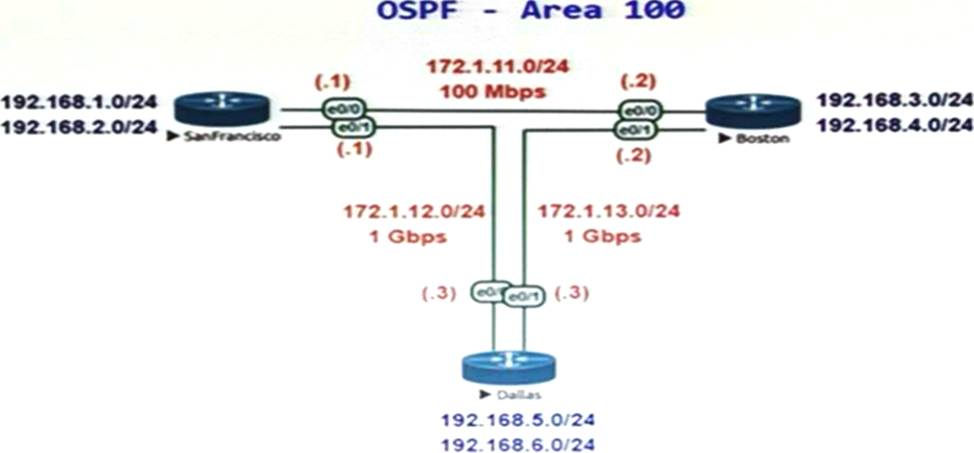
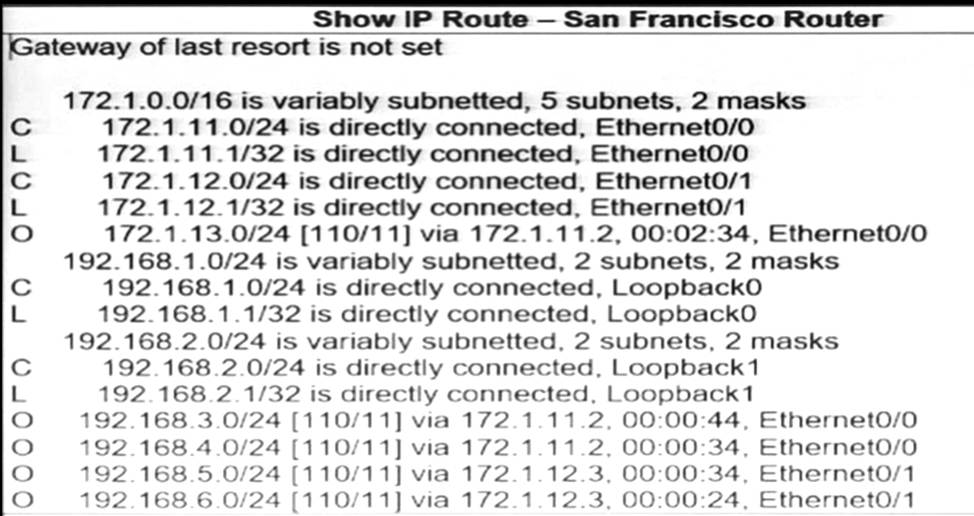
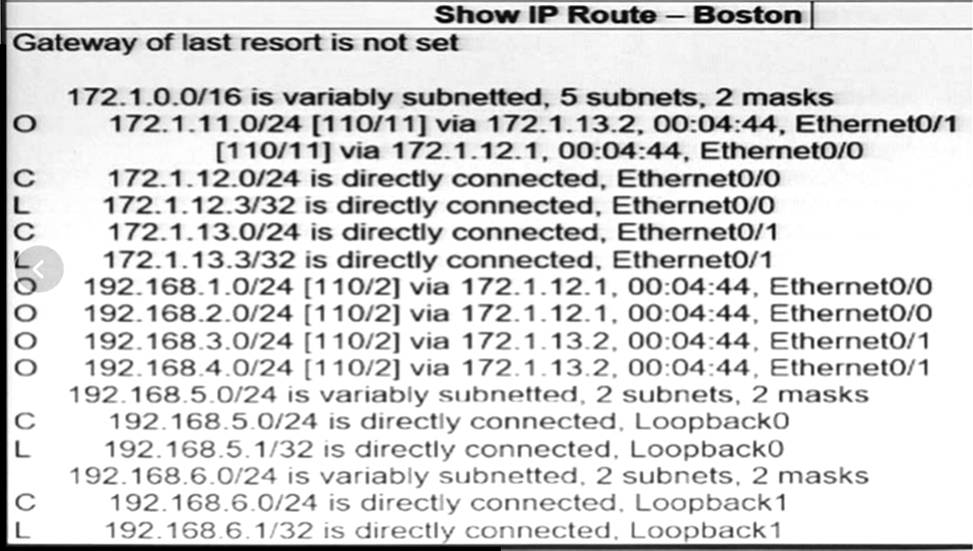
SanFrancisco and Boston routers are choosing slower links to reach each other despite the direct links being up.
Which configuration fixes the issue?

- A . Option A
- B . Option B
- C . Option C
- D . Option D
Refer to the exhibit.
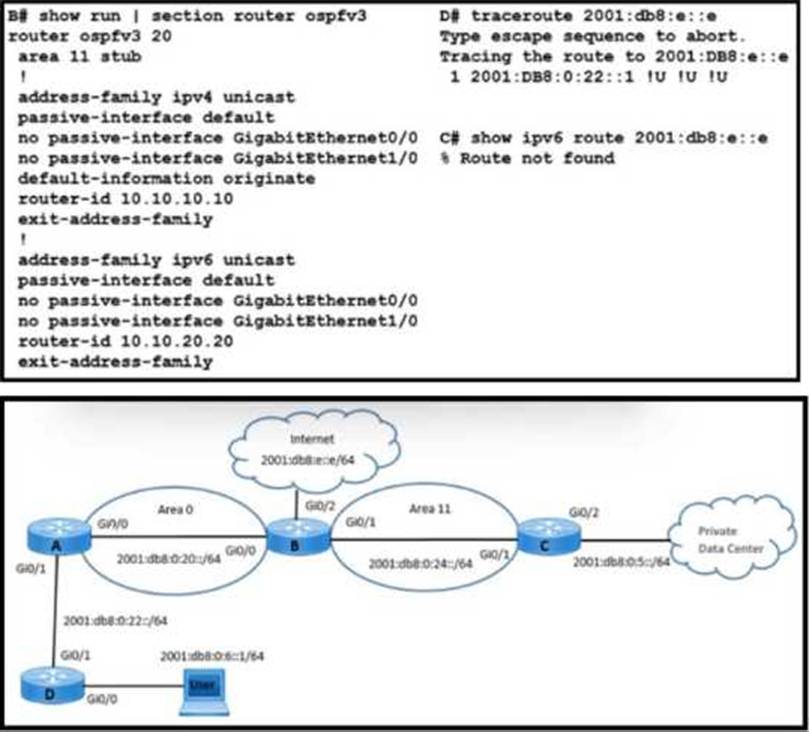
An enterprise user reports an access issue with IPv6 content on the Internet. The user can access IPv4 content that is at the data center.
Which action resolves the issue with IPv6 content?
- A . Change Area 11 to Area 0 between routers B and C.
- B . Add a static route for 2001: db8:0:6::1/64 on router B RIB.
- C . Advertise the 2001:db8: e::e/64 route on the router D OSPF process.
- D . Enable default information to originate in IPv6 AF on router B.
