Practice Free SC-300 Exam Online Questions
You create a conditional access policy that blocks access when a user triggers a high-seventy sign-in alert.
You need to test the policy under the following conditions;
• A user signs in from another country.
• A user triggers a sign-in risk.
What should you use to complete the test?
- A . the Conditional Access What If tool
- B . sign-ins logs in Azure AD
- C . access reviews in Azure AD
- D . the activity logs in Microsoft Defender for Cloud Apps
You have an Azure AD tenant
You open the risk detections report.
Which risk detection type is classified as a user risk?
- A . password spray
- B . anonymous IP address
- C . unfamiliar sign-in properties
- D . Azure AD threat intelligence
You have a Microsoft 365 E5 subscription that contains a web app named App1.
Guest users are regularly granted access to App1.
You need to ensure that the guest users that have NOT accessed App1 during the past 30 days have their access removed the solution must minimize administrative effort.
What should you configure?
- A . a compliance policy
- B . an access review for application access
- C . a guest access review
- D . a Conditional Access policy
You have a Microsoft 365 E5 subscription.
Users authorize third-party cloud apps to access their data.
You need to configure an alert that will be triggered when an app requires high permissions and is authorized by more than 20 users.
Which type of policy should you create in the Microsoft Defender for Cloud Apps portal?
- A . anomaly detection policy
- B . OAuth app policy
- C . access policy
- D . activity policy
You have an Azure Active Directory (Azure AD) tenant that syncs to an Active Directory domain. The on-premises network contains a VPN server that authenticates to the on-premises Active Directory domain. The VPN server does NOT support Azure Multi-Factor Authentication (MFA). You need to recommend a solution to provide Azure MFA for VPN connections.
What should you include in the recommendation?
- A . Azure AD Application Proxy
- B . an Azure AD Password Protection proxy
- C . Network Policy Server (NPS)
- D . a pass-through authentication proxy
DRAG DROP
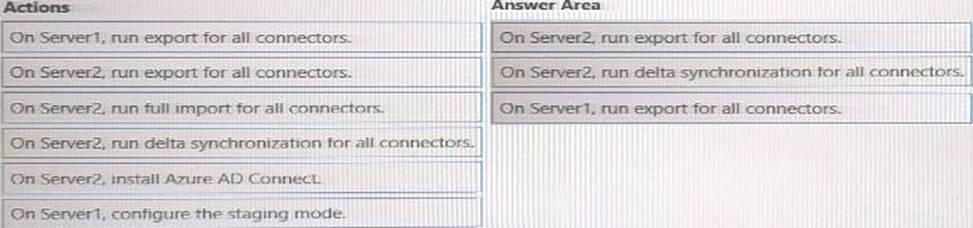
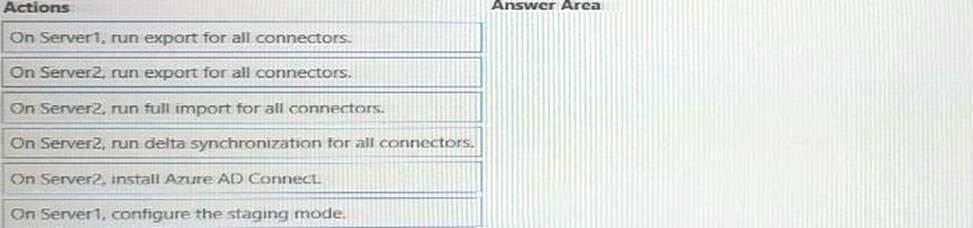
Your network contains an Active Directory forest named contoso.com that is linked to an Azure Active Directory (Azure AD) tenant named contoso.com by using Azure AD Connect. Attire AD Connect is installed on a server named Server 1.
You deploy a new server named Server? that runs Windows Server 2019.
You need to implement a failover server for Azure AD Connect. The solution must minimize how long it takes to fail over if Server1 fails.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
DRAG DROP
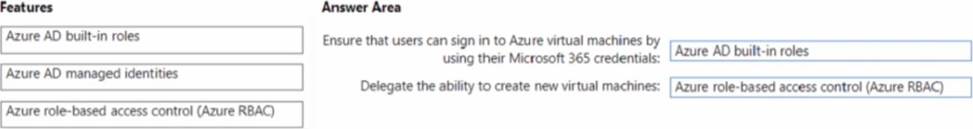
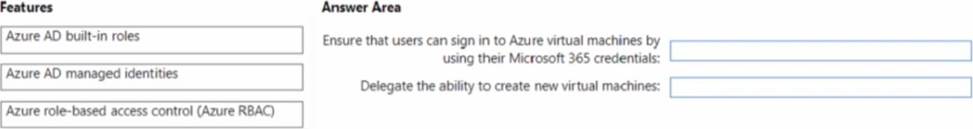
You have a Microsoft 365 E5 subscription and an Azure subscription.
You need to meet the following requirements:
• Ensure that users can sign in to Azure virtual machines by using their Microsoft 365 credentials.
• Delegate the ability to create new virtual machines.
What should you use for each requirement? To answer, drag the appropriate features to the correct requirements. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
You have a Microsoft 365 subscription that contains a Microsoft SharePoint Online site named Site1 and a Microsoft 365 group named Group1. You need to ensure that the members of Group1 can access Site1 for 90 days. The solution must minimize administrative effort.
What should you use?
- A . an access review
- B . a lifecycle workflow
- C . an access package
- D . a Conditional Access policy
You have an Azure subscription that is linked to a Microsoft Entra tenant. The tenant contains a registered app named App1. You have a partner organization that has a Microsoft Entra tenant. The tenant contains a registered app named App2. You need to ensure that App1 can access App2.
Which two types of credentials can App1 use? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . certificate
- B . managed identity
- C . secret
- D . user account
- E . one-time password
You have a Microsoft 365 tenant.
All users have mobile phones and laptops.
The users frequently work from remote locations that do not have Wi-Fi access or mobile phone connectivity.
While working from the remote locations, the users connect their laptop to a wired network that has internet access.
You plan to implement multi-factor authentication (MFA).
Which MFA authentication method can the users use from the remote location?
- A . a notification through the Microsoft Authenticator app
- B . security questions
- C . voice
- D . an app password