Practice Free SC-401 Exam Online Questions
You have a Microsoft 365 E5 subscription that contains a trainable classifier named Trainable1.
You plan to create the items shown in the following table.
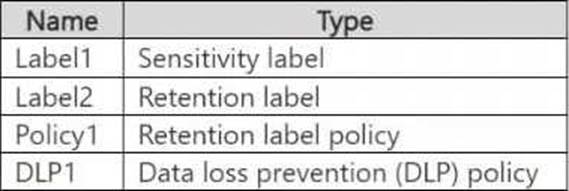
Which items can use Trainable 1?
- A . Label2 only
- B . Label1 and Label2 only
- C . Label1 and Policy1 only
- D . Label2, Policy1, and DLP1 only
- E . Label1, Label2, Policy1, and DLP1
D
Explanation:
A trainable classifier in Microsoft Purview is used to automatically identify and classify unstructured data based on content patterns.
The classifier can be used in:
HOTSPOT
You have a Microsoft 365 E5 subscription.
You receive the data loss prevention (DLP) alert shown in the following exhibit.
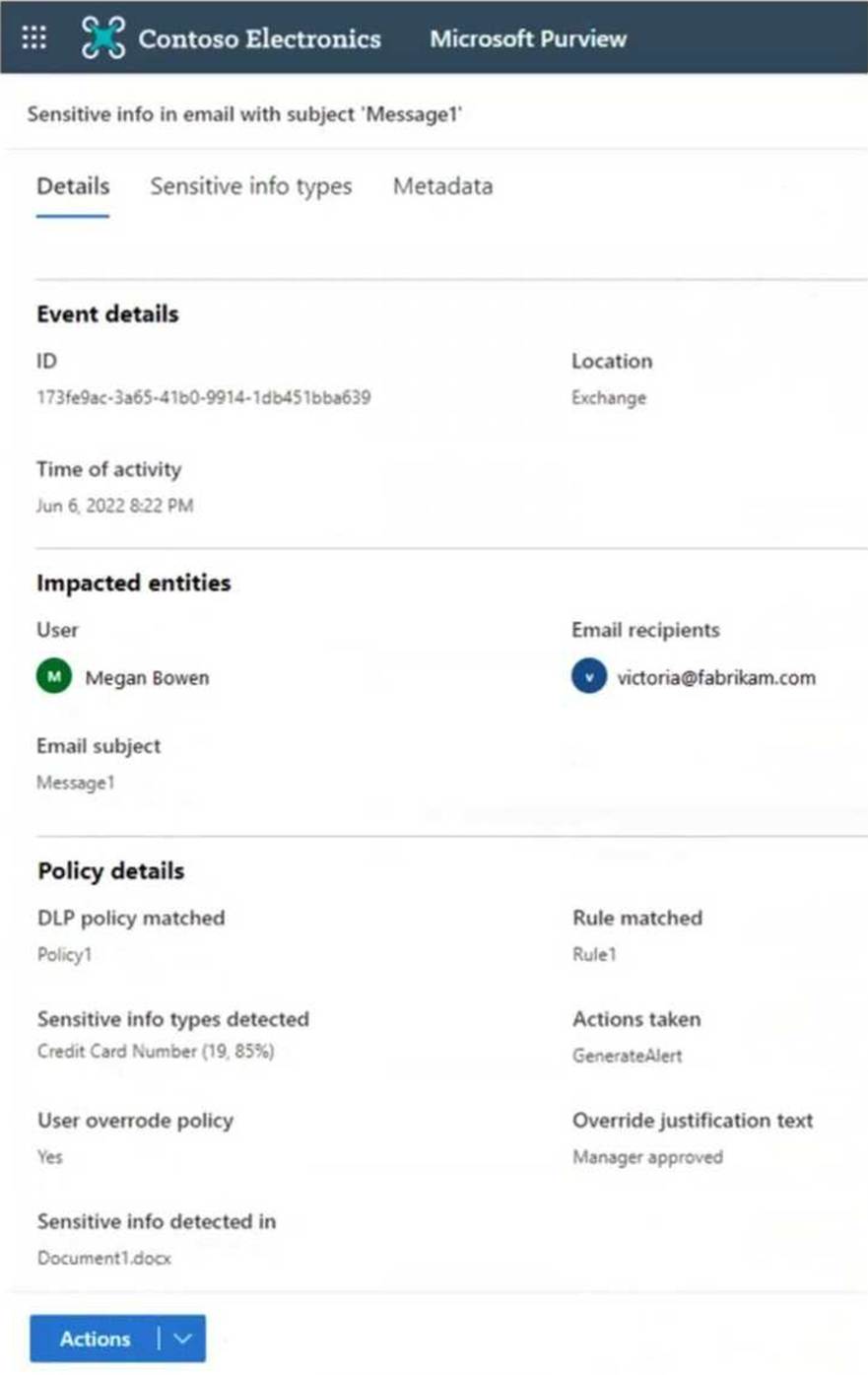
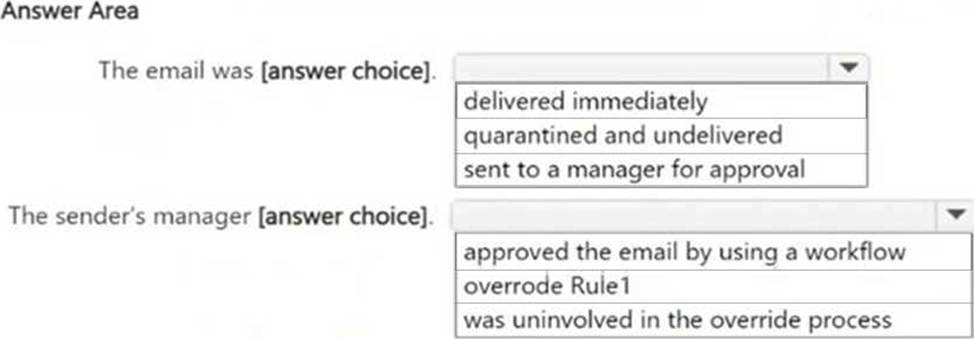
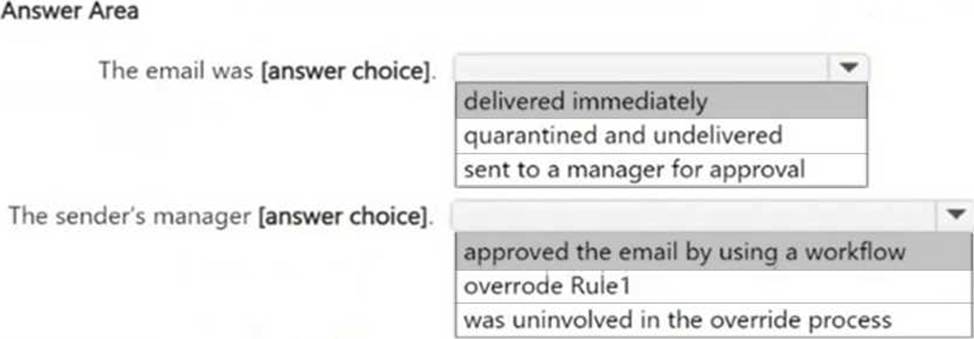
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
HOTSPOT
You have a Microsoft 365 E5 subscription that uses Microsoft Purview.
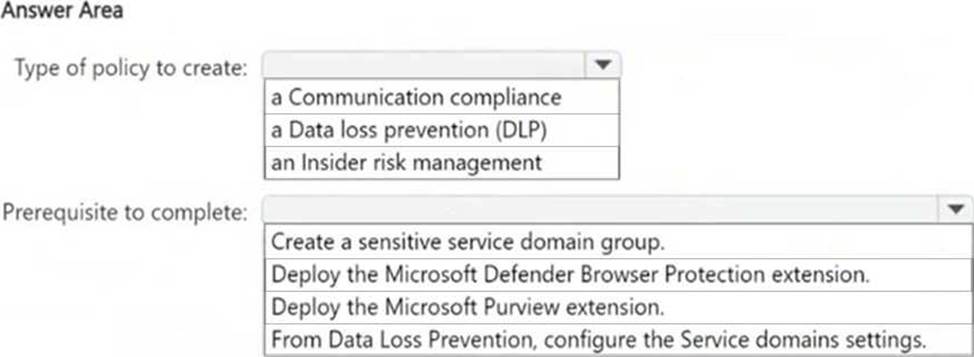
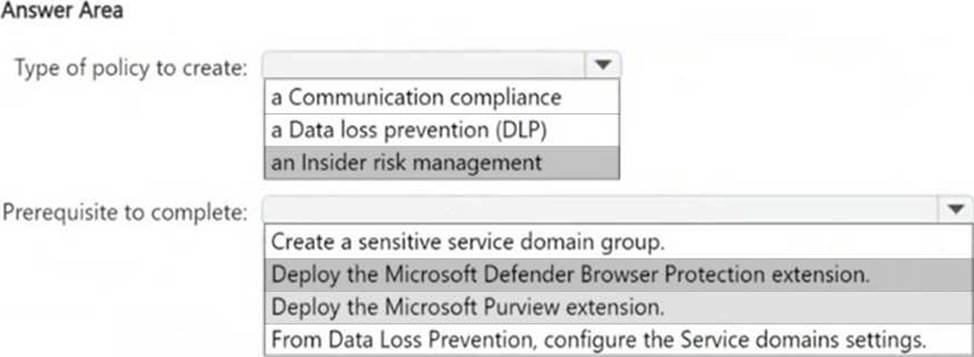
You need ensure that an incident will be generated when a user visits a phishing website.
What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Box 1: Insider Risk Management policies in Microsoft Purview can be configured to detect risky behavior, such as accessing phishing websites. These policies monitor user activity, generate alerts, and help organizations investigate potential security threats.
Box 2: Microsoft Defender Browser Protection extension helps in detecting unsafe or phishing websites and integrating this detection with Insider Risk Management policies. This extension works with Microsoft Edge and Google Chrome to identify risky browsing activity and trigger alerts.
HOTSPOT
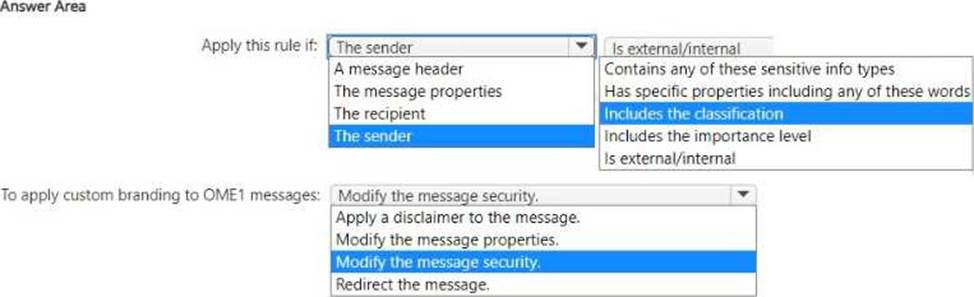
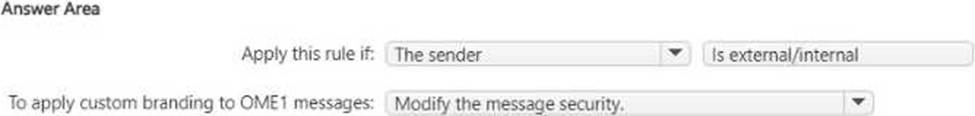
You have a Microsoft 365 £5 subscription.
You have a Microsoft Purview Advanced Message Encryption branding template named 0ME1.
You need to create a Microsoft Exchange Online mail flow rule to apply OME1 to email.
How should you configure the rule? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You need to enable support for sensitivity labels in Microsoft SharePoint Online.
What should you use?
- A . the Microsoft Purview portal
- B . the Microsoft Entra admin center
- C . the SharePoint admin center
- D . the Microsoft 365 admin center
C
Explanation:
To enable support for sensitivity labels in Microsoft SharePoint Online, you must configure the setting in the SharePoint admin center.
Sensitivity labels in SharePoint Online allow labeling and protection of files stored in SharePoint and OneDrive. This feature must be enabled in the SharePoint admin center → Settings → Information protection to allow sensitivity labels to apply encryption and protection to stored documents.
You have a Microsoft 365 E5 subscription that contains a data loss prevention (DLP) policy named DLP1.
DLP1 contains the DLP rules shown in the table.
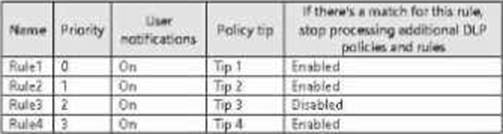
You need to ensure that when a document matches all the rules, users will see Tip 2.
What should you change?
- A . the priority setting of Rule2 to 0
- B . the priority setting of Rule2 to 2
- C . the priority setting of Rule3 and Rule4 to 0
- D . the If there’s a match for this rule, stop processing additional DLP policies and rules setting for Rule3 to Enabled
HOTSPOT
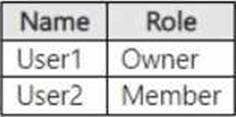
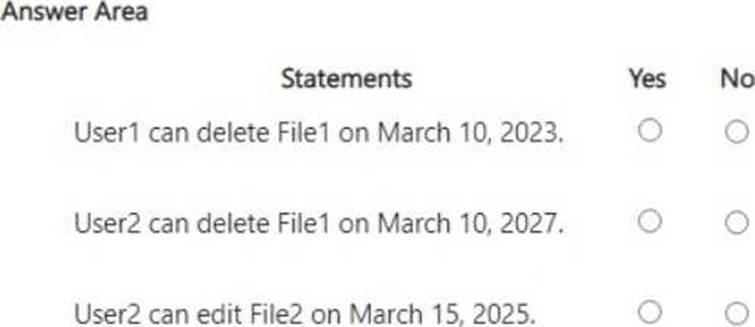
You have a Microsoft SharePoint Online site named Site1 that has the users shown in the following table.
You create the retention labels shown in the following table.
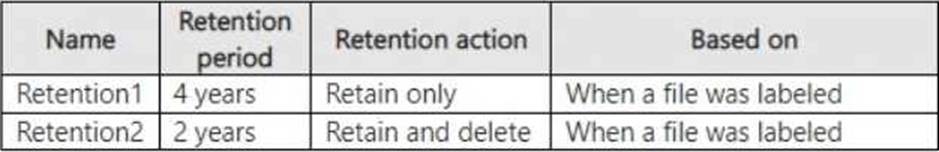
You publish the retention labels to Site1.
On March 1,2023, you assign the retention labels to the files shown in the following table.
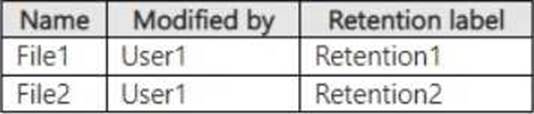
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT
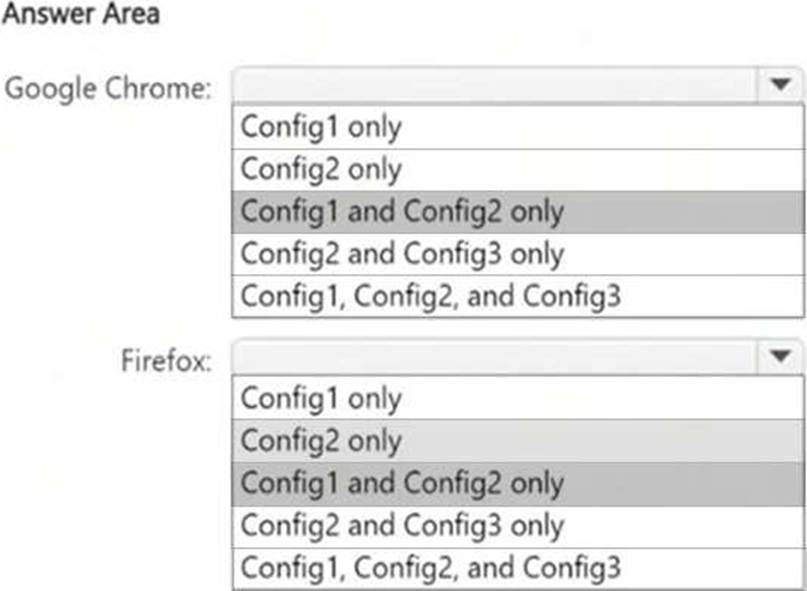
You have a Microsoft 365 E5 subscription that contains the device configurations shown in the following table.
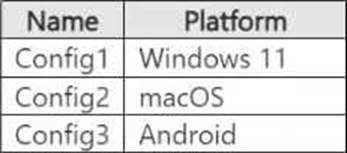
Each configuration uses either Google Chrome or Firefox as a default browser.
You need to implement Microsoft Purview and deploy the Microsoft Purview browser extension to the configurations.
To which configuration can each extension be deployed? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Microsoft Purview browser extensions for Endpoint DLP are supported on:
● Windows 10/11 (Config1)
● macOS (Config2)
● Not supported on Android (Config3)
Since Microsoft Purview does not support browser extensions on Android, Config3 is excluded from both Google Chrome and Firefox.
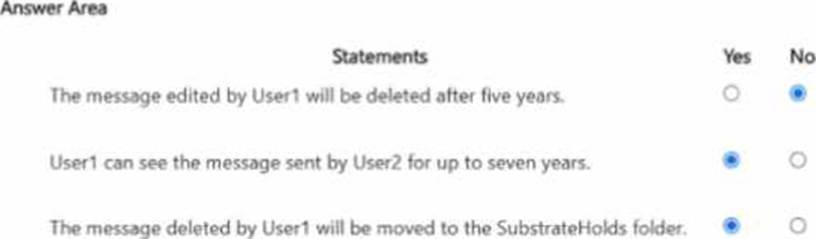
HOTSPOT
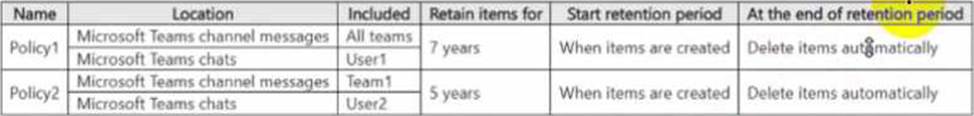
You have a Microsoft 365 ES subscription that uses Microsoft Teams and contains the users shown in the following table.

You have the retention policies shown in the following table.
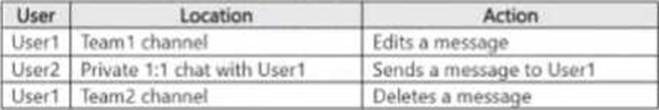
The users perform the actions shown in the following table.
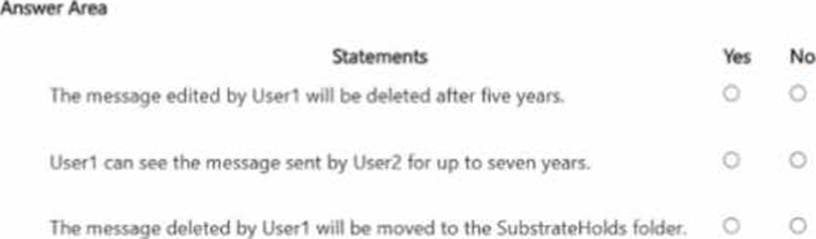
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps.
You need to ensure that you receive an alert when a user uploads a document to a third-party cloud storage service.
What should you use?
- A . an activity policy
- B . a sensitivity label
- C . a file policy
- D . an insider risk policy
