Practice Free 220-1201 Exam Online Questions
Several storms cause mission-critical servers to go offline unexpectedly A server also goes offline suddenly due to haro Nvare failure Upon assessment the company purchases new UPSs to condition power and allow the OSs to shut down gracefully in the event of a power failure However, the UPSs are delayed due to supply chain issues.
Which of the following can balance a cost-effective solution with uptime requirements?
- A . Purchasing backup generators
- B . Increasing input voltage
- C . Installing redundant PSUs
- D . Activating a hot site
C
Explanation:
C. Installing redundant PSUs (Power Supply Units):
Redundant PSUs provide fault tolerance by ensuring that if one power supply fails, another will take over seamlessly.
This is a cost-effective way to increase uptime while waiting for the UPSs to arrive.
Incorrect Options:
A network operations analyst receives an automated alert regarding a server with an array. The analyst walks over to the server and sees a blinking orange light at the hard disk bay. The server is configured for RAID 1.
Which of the following should the analyst do to resolve this issue?
- A . Change the array to RAID 0.
- B . Undo the array and create a new one.
- C . Update RAID card firmware.
- D . Replace the hard disk and rebuild the array.
D
Explanation:
A blinking orange light typically indicates a failed hard drive in the RAID array. In RAID 1 (mirroring), you can replace the failed drive and rebuild the array without data loss.
From CompTIA A+ 220-1101 Official Study Guide, Objective 3.4 C RAID configuration and troubleshooting:
"In the event of a hard drive failure in RAID 1, replace the failed disk and allow the array to rebuild using the remaining mirrored disk."
Verified Source:
CompTIA A+ Core 1 (220-1101) Official Study Guide, Chapter 3: RAID and Storage CompTIA Exam Objectives 220-1101, Domain 3.4
A SOHO user cannot connect to the internet.
Their configuration shows:
IP: 192.168.223.15
Mask: 255.255.255.0
Gateway: 192.168.233.1
DNS: 8.8.8.8, 4.2.2.1, 4.2.2.2
Baseline documentation shows valid subnet range: 192.168.200.0C192.168.232.255.
Which setting must be changed?
- A . Tertiary DNS
- B . Secondary DNS
- C . Primary DNS
- D . IP Address
- E . Gateway
- F . Subnet mask
E
Explanation:
The baseline documentation says the valid network range ends at 192.168.232.255, but the user’s gateway is 192.168.233.1, which is outside the permitted network range. CompTIA A+ emphasizes that devices must have a gateway inside their own subnet.
Given a mask of 255.255.255.0, the user’s subnet is 192.168.223.x, so the gateway must be in 192.168.223.x, not 192.168.233.x.
DNS settings are public and acceptable. The IP address and subnet mask are valid within the documented address space.
Therefore, the incorrect setting is the gateway, which prevents external routing. Correcting it resolves the connection issue, matching CompTIA’s routing and TCP/IP troubleshooting procedures.
A help desk technician investigates a laser printer issue. Smudges are appearing on the printed pages, but they are not present on the document that was sent to the printer.
Which of the following should the technician do first to diagnose the issue?
- A . Use a different kind of printing paper.
- B . Inspect the printer drum.
- C . Update the printer firmware.
- D . Replace the toner.
B
Explanation:
Because the smudges are not in the original document, the problem is almost certainly occurring inside the printer’s imaging process, not in software, drivers, or the file being printed. With laser printers, smudges commonly result from issues in the imaging components such as the drum/photoconductor, the toner delivery, or the fuser stage that bonds toner to the page. The best first diagnostic step from the options given is to inspect the printer drum, because damage, contamination, or wear on the drum can cause repeating marks, streaks, or smudges as the drum rotates and transfers toner to paper. Visual inspection can quickly reveal toner buildup, scratches, or a failing drum surface, and it helps confirm whether the issue matches a drum-related symptom before replacing consumables.
Updating firmware is unlikely to fix a physical smudging problem. Switching paper can help if paper is damp or incompatible, but it is less likely when the symptom is consistent and the smudge pattern points to the imaging path. Replacing toner may resolve it, but that is a fix rather than the most targeted first diagnostic action compared to inspecting the drum.
Which of the following, when combined, are used to make sure a workstation always has the same IP address on a network managed with DHCP?
- A . Creating a new scope
- B . Enabling network address translation
- C . Assigning a reservation
- D . Configuring an automatic private IP address
C
Explanation:
To ensure a workstation always receives the same IP address while still using DHCP, the correct method is to configure a DHCP reservation. A reservation “combines” two key pieces: the workstation’s MAC address (hardware address) and a specific IP address within the DHCP scope. When the workstation requests an address, the DHCP server matches the request to the stored MAC address and consistently assigns the reserved IP each time the device connects. This provides the benefits of DHCP (central management, consistent options like gateway/DNS, easier changes) while giving the workstation a predictable IP, which is often needed for management, monitoring, or firewall rules.
Creating a new scope is used to define an address pool and options for an entire subnet, but it does not guarantee one device always gets the same IP. NAT translates private IPs to public IPs and is unrelated to consistent DHCP assignments for a specific workstation. APIPA automatic private IP addressing 169.254.x.x occurs when DHCP fails and is not a controlled way to ensure a consistent, usable network address. Therefore, assigning a reservation is the correct answer.
Which of the following is a Bluetooth network an example of?
- A . PAN
- B . LAN
- C . WAN
- D . SAN
A
Explanation:
Bluetooth is a wireless technology designed for short-range communication between devices. It is a classic example of a Personal Area Network (PAN), which supports communication between devices like smartphones, headsets, keyboards, and mice within a few meters. PANs are smaller in scope compared to LANs or WANs.
Reference: "CompTIA A+ Complete Study Guide" by Quentin Docter C Chapter 5, "Networking Fundamentals", page 275.
Which of the following can a user utilize to share their mobile phone connection with their laptop?
- A . IR
- B . NFC
- C . Wi-Fi Direct
- D . Tethering
D
Explanation:
Tethering refers to sharing a mobile phone’s internet connection with another device, such as a laptop, either through USB, Bluetooth, or Wi-Fi. Tethering effectively turns the mobile phone into a personal hotspot for internet access.
Option A (IR): Incorrect. Infrared (IR) is used for short-range communication, such as remote controls, but it does not support internet sharing.
Option B (NFC): Incorrect. Near-field communication (NFC) is used for close-proximity data transfer, not for internet sharing.
Option C (Wi-Fi Direct): Incorrect. Wi-Fi Direct enables device-to-device communication but does not inherently provide internet sharing.
Reference: CompTIA A+ Core 1 Objectives: 1.4 (Configure basic mobile-device network connectivity)
A technician is having issues replacing a laptop’s wireless card because the cover seems to be stuck.
Which of the following should the technician do next to troubleshoot this issued
- A . Check the product manual for the procedure
- B . Use a pry tool to force the cover open
- C . Insert the wireless card into the M.2 slot
- D . Try to move the cover by sliding it in all directions.
A
Explanation:
SIMULATION
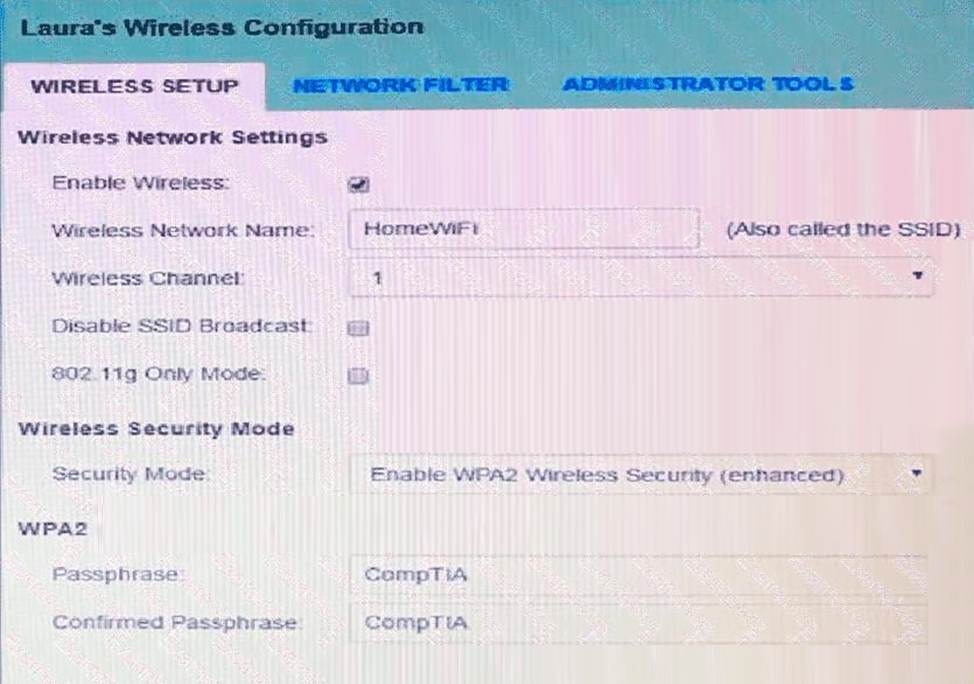
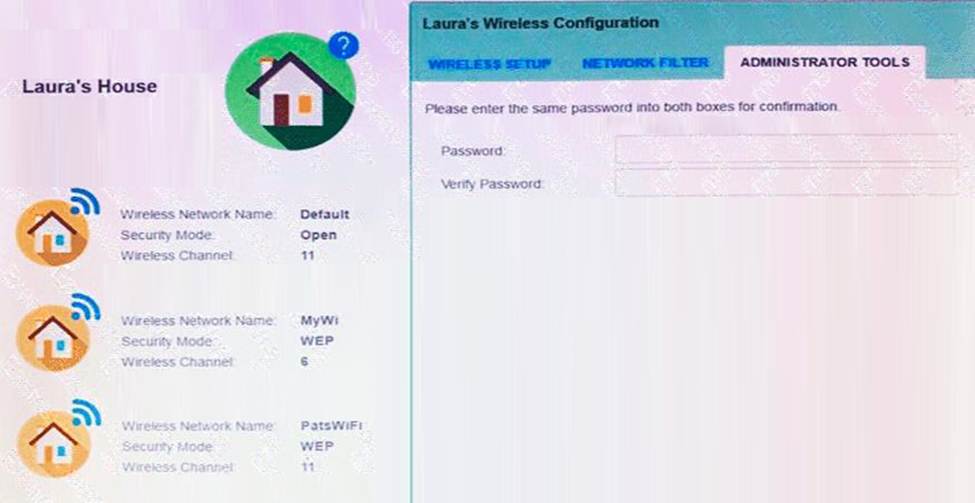
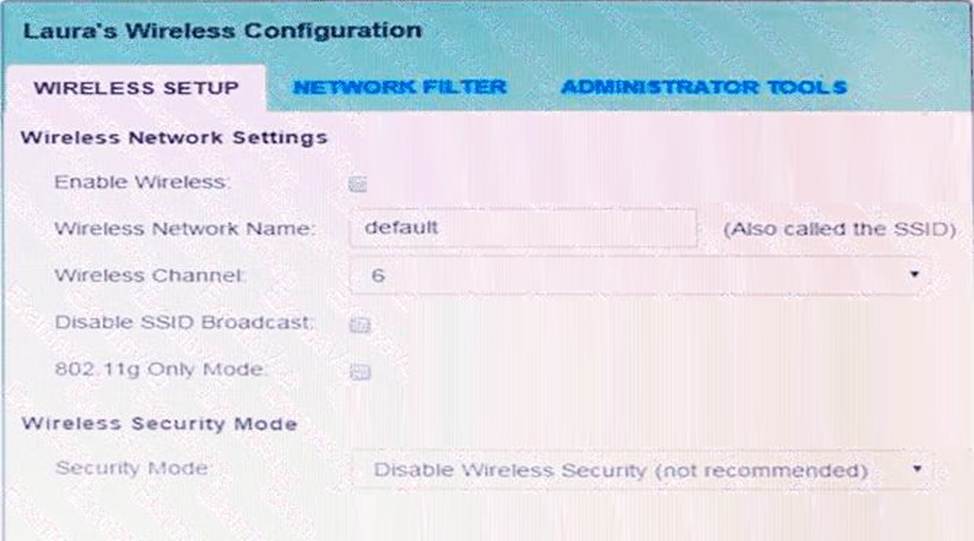
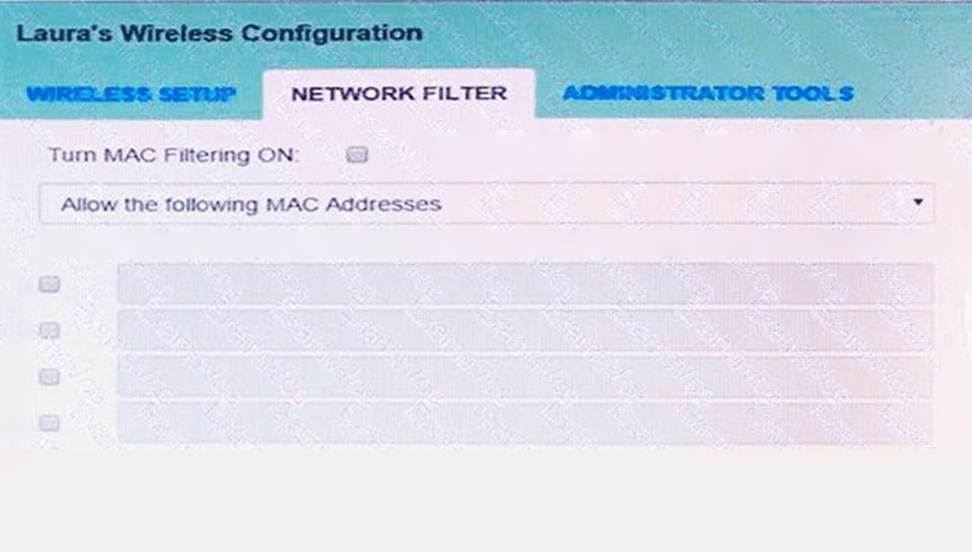
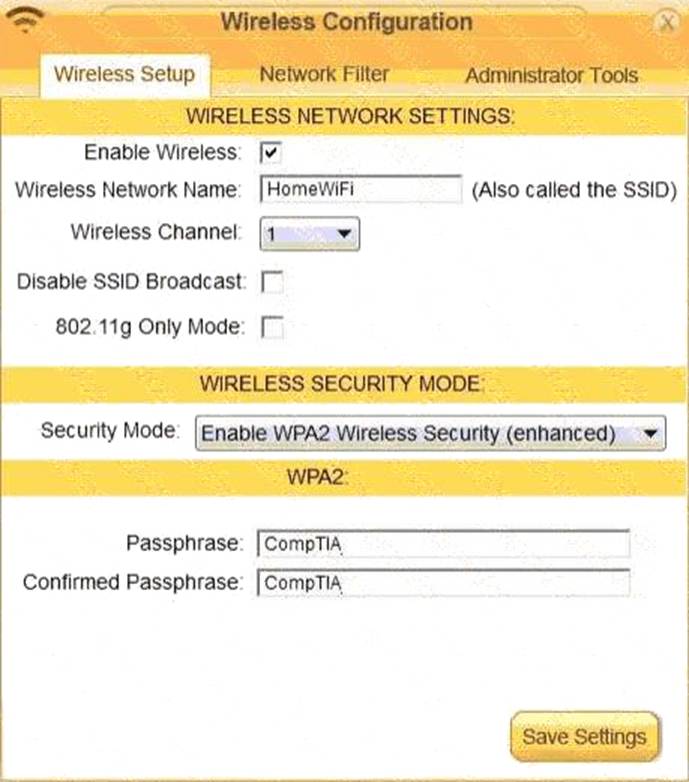
Laura, a customer, has instructed you to configure her home office wireless access point. She plans to use the wireless network for finances and has requested that the network be setup with the highest encryption possible.
Additionally, Laura knows that her neighbors have wireless networks and wants to ensure that her network is not being interfered with by the other networks. She requests that the default settings be changed to the following.
Wireless Name: HomeWiFi
Shared Key: CompTIA
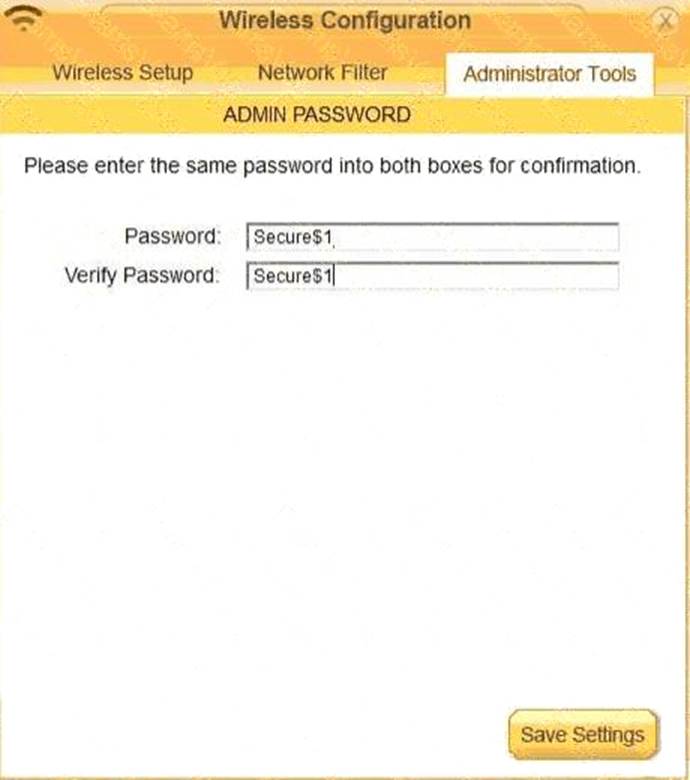
Router Password: Secure$1
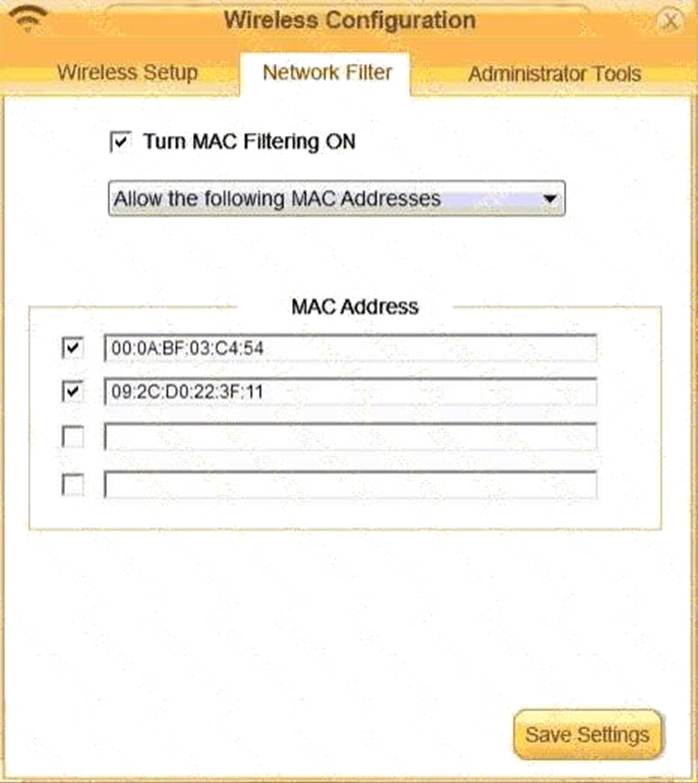
Finally, Laura wants to ensure that only her laptop and Smartphone can connect to the network.
Laptop: IP Address 192.168.1.100
Hardware Address: 00: 0A: BF: 03: C4: 54
Smartphone: IP Address 192.168.1.101
Hardware Address: 09: 2C: D0: 22: 3F: 11
INSTRUCTIONS
Configure Laura’s wireless network using the network adapter window.
If at any time you would like to bring back the initial state of the situation, please click the Reset All button.
A screenshot of a network settings AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.
Which of the following types of RAM is typically used in servers?
- A . SODIMM
- B . Rambus
- C . DDR3
- D . ECC
D
Explanation:
ECC (Error-Correcting Code) RAM is commonly used in servers to provide error detection and correction, improving reliability in critical systems. It is designed to detect and correct single-bit errors, ensuring data integrity in environments where stability is paramount.
Option A (SODIMM): Incorrect. SODIMM is typically used in laptops, not servers.
Option B (Rambus): Incorrect. Rambus is an outdated RAM type and not commonly used today.
Option C (DDR3): Incorrect. While DDR3 is a type of RAM, it is not specific to servers and does not provide error correction.
Reference: CompTIA A+ Core 1 Objectives: 3.2 (RAM types and their uses)
