Practice Free SC-401 Exam Online Questions
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1.
You need to implement Microsoft Purview data lifecycle management.
What should you create first?
- A . a sensitivity label policy
- B . a data loss prevention (DLP) policy
- C . an auto-labeling policy
- D . a retention label
D
Explanation:
To implement Microsoft Purview Data Lifecycle Management for SharePoint Online (Site1), you need to create a retention label first. Retention labels define how long content should be retained or deleted based on compliance requirements. Once a retention label is created, it can be manually or automatically applied to content in SharePoint Online, Exchange, OneDrive, and Teams. After creating a retention label, you can configure label policies to apply them to Site1 and other locations.
You have a Microsoft 36S E5 subscription that has a Microsoft Purview exact data match (EDM) classifier named EDM1.
You plan to create the Microsoft Purview policies shown in the following table.
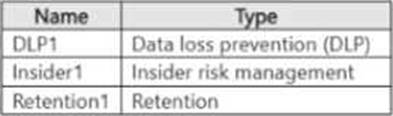
Which policies can use EDM1?
- A . DLP1 only
- B . Retention 1 only
- C . DLP1 and Insider1 only
- D . Insider1 and Retention1 only
- E . DLP1. Insider1, and Retention1
You have a Microsoft 365 E5 subscription that contains three users named User1, User2, and User3 and a file named Filetdocx.
You create a sensitivity label named Label1 as shown in the following exhibit.
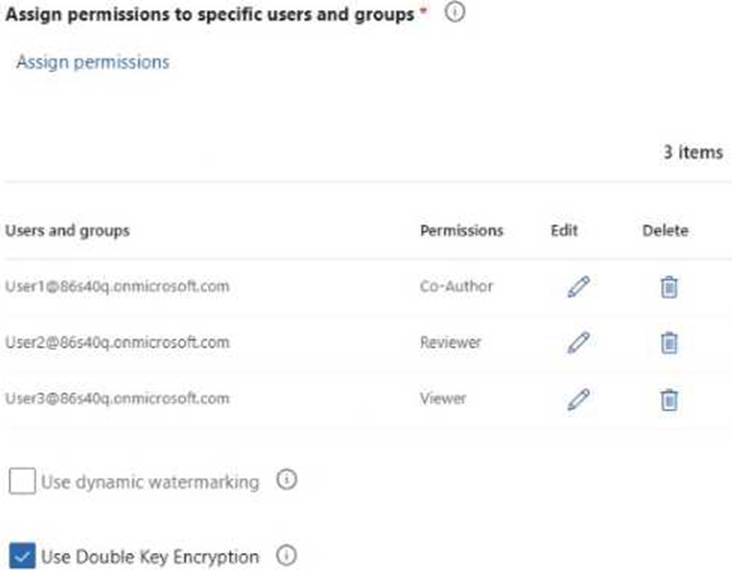
You apply Label1 to File1.
For which users can Microsoft 365 Copilot summarize File1?
- A . No user
- B . User 1 only
- C . User1 and User2 only
- D . User1, User2, and User3
You have a Microsoft J65 ES subscription.
You need to create a Microsoft Defender for Cloud Apps policy that will detect data loss prevention (DIP) violations.
What should you create?
- A . a file policy
- B . an activity policy
- C . a session policy
- D . an access policy
You have a Microsoft J65 E5 subscription. You plan to implement retention policies for Microsoft Teams.
Which item types can be retained?
- A . voice memos from the Teams mobile client
- B . embedded images
- C . code snippets
You have a Microsoft J65 E5 subscription. You plan to implement retention policies for Microsoft Teams.
Which item types can be retained?
- A . voice memos from the Teams mobile client
- B . embedded images
- C . code snippets
You have a Microsoft 565 E5 subscription.
You plan to use Microsoft Purview insider risk management.
You need to create an insider risk management policy that will detect data theft from Microsoft SharePoint Online by users that submitted their resignation or are near their employment termination date.
What should you do first?
- A . Configure a HR data connector.
- B . Configure Office indicators.
- C . Configure a Physical badging connector.
- D . Onboard devices to Microsoft Defender for Endpoint.
You have a Microsoft 365 E5 subscription.
You need to create a sensitivity label named Label1. The solution must ensure that users can use Microsoft 365 Copilot to summarize files that have Label1 applied.
Which permission should you select for Label1?
- A . Export content(EXPORT)
- B . Copy and extract content(EXTRACT)
- C . Edit content(DOCEDIT)
- D . View rights(VIEW)
B
Explanation:
To allow Microsoft 365 Copilot to summarize files that have Label1 applied, the label must grant permission to extract content from the document. The correct permission for this is Copy and extract content (EXTRACT).
Microsoft 365 Copilot requires access to read and process content in documents to generate summaries. The EXTRACT permission allows users (and AI tools like Copilot) to copy and extract content for processing while still maintaining the protection applied by the sensitivity label.
At the end of a project, you upload project documents to a Microsoft SharePoint Online library that contains many files.
The following is a sample of the project document file names:
• aei_AA989.docx
• bd_WS098.docx
• cei_DF112.docx
• ebc_QQ454.docx
• ecc_BB565.docx
All documents that use this naming format must be labeled as Project Documents:
You need to create an auto-apply retention label policy.
What should you use to identify the files?
- A . A retention label
- B . A trainable classifier
- C . A sensitive info type
HOTSPOT
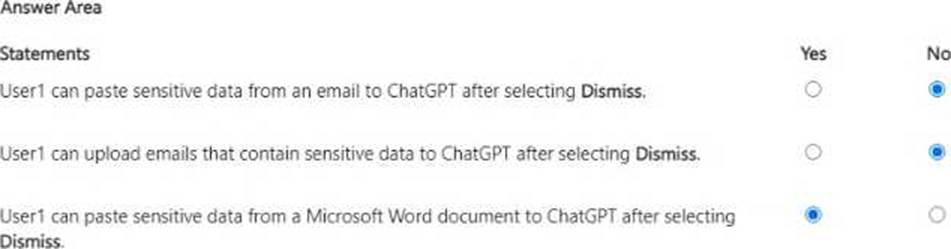
You have a Microsoft 365 E5 subscription that contains a user named User1.
The subscription contains an Endpoint data loss prevention (Endpoint DLP) policy as shown in the Actions exhibit. (Click the Actions tab.)
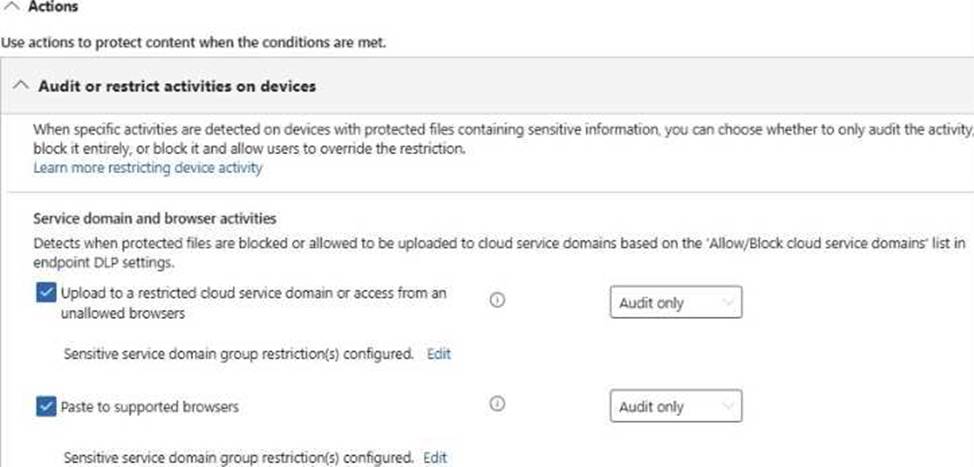
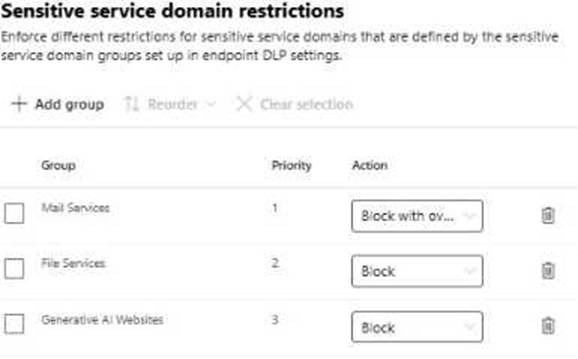
You configure the Upload to a restricted cloud service domain or access from an unallowed browsers settings as shown in the Upload restrictions exhibit. (Click the Upload restrictions tab.)
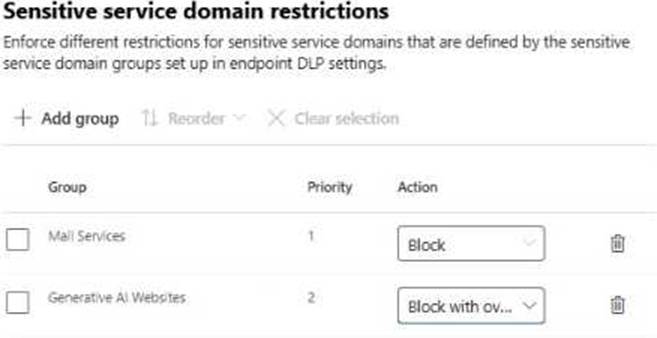
You configure the Paste to supported browsers settings as shown in the Paste restrictions exhibit. (Click the Paste restrictions tab.)
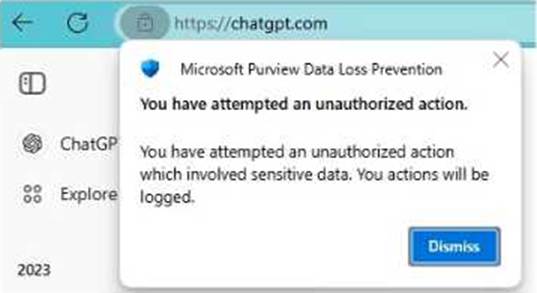
When User1 pastes content into ChatGPT, the user receives the error message shown in the Error exhibit. (Click the Error tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.