Practice Free SC-401 Exam Online Questions
You have a Microsoft 365 E5 subscription.
You need to prevent users from uploading data loss prevention (DLP)-protected documents to the following third-party websites:
● web1.contoso.com
● web2.contoso.com
The solution must minimize administrative effort.
To what should you set the Service domains setting for Endpoint DLP?
- A . *.contoso.com
- B . contoso.com
- C . web1.contoso.com and web2.contoso.com
- D . web*.contoso.com
C
Explanation:
The Service domains setting in Microsoft 365 Endpoint Data Loss Prevention (Endpoint DLP) allows administrators to block or allow specific domains for file uploads. The goal is to prevent users from uploading DLP-protected documents to web1.contoso.com and web2.contoso.com.
Setting the Service domains to "web1.contoso.com and web2.contoso.com" precisely targets the two specific third-party websites, minimizing administrative effort while ensuring strict control.
You have a Microsoft SharePoint Online site named Site! that contains the files shown in the following table.

You have a data loss prevention (DLP) policy named DLP1 that has the advanced DLP rules shown in the following table.
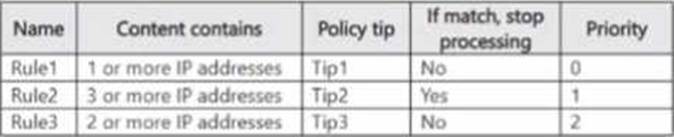
You apply DLP1 toSite1.
Which policy tips will appear for File2?
- A . Tip1 only
- B . Tip2 only
- C . Tip3 only
- D . Tip1 and Tip2 only
HOTSPOT
You have a Microsoft 36S ES subscription that contains two Windows devices named Devicel1and Device2 Device1 has the default browser set to Microsoft Edge. Devke2 has the default browser set to Google Chrome.
You need to ensure that Microsoft Purview insider risk management can collect signals when a user copies files to a USB device by using their default browser.
What should you deploy to each device? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
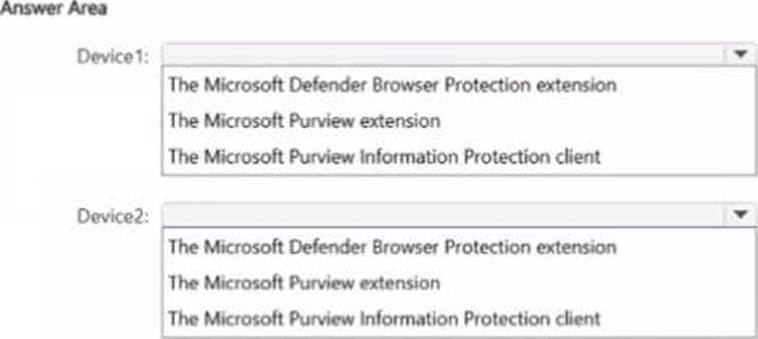
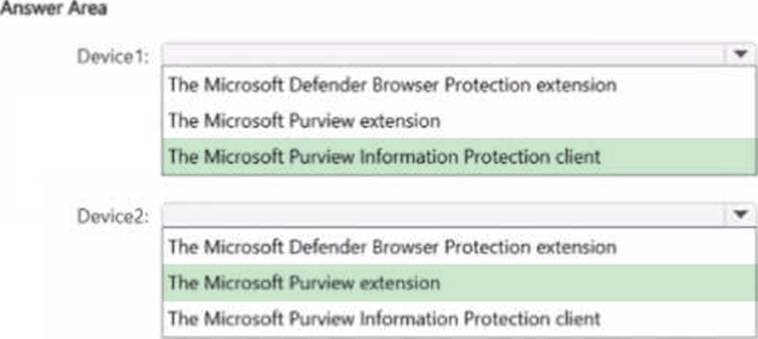
You are planning a data loss prevention (DLP) solution that will apply to Windows Client computers.
You need to ensure that when users attempt to copy a file that contains sensitive information to a USB storage device, the following requirements are met:
● If the users are members of a group named Group1, the users must be allowed to copy the file, and an event must be recorded in the audit log.
● All other users must be blocked from copying the file.
What should you create?
- A . one DLP policy that contains one DLP rule
- B . one DLP policy that contains two DLP rules
- C . two DLP policies that each contains one DLP rule
B
Explanation:
To meet the requirements, you need one DLP policy with two separate DLP rules to handle the different conditions:
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site! and the data loss prevention (DLP) policies shown in the following table.
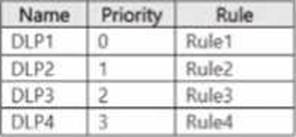
The DLP rules are configured as shown In the following table.
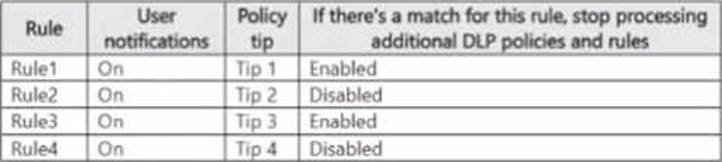
All the policies are assigned to Site1.
You need to ensure that if a user uploads a document to Site1 that matches all the rules, the user will be shown the Tip 2 policy tip.
What should you do?
- A . Change the priority of DLP2 to 0.
- B . Prevent additional processing of the policies if there is a match for Rule2
- C . Change the priority of DLP2 to 3.
- D . Enable additional processing of the policies if there is a match for Rule1.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You recently discovered that the developers at your company emailed Azure Storage Account keys in plain text to third parties.
You need to ensure that when Azure Storage Account keys are emailed, the emails are encrypted.
Solution: You configure a mail flow rule that matches a sensitive info type.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
To ensure Azure Storage Account keys are encrypted when sent via email, you need a Data Loss Prevention (DLP) policy that detects Azure Storage Account keys using a sensitive information type and automatically encrypts emails containing these keys.
Mail flow rules (transport rules) can detect sensitive info, but they are limited in encryption capabilities.
DLP policies provide more advanced protection and integration with Microsoft Purview for sensitive info detection.
Your company has offices in multiple countries.
The company has a Microsoft 365 E5 subscription that uses Microsoft Purview insider risk management.
You plan to perform the following actions:
● In a new country, open an office named Office1.
● Create a new user named User1.
● Deploy insider risk management to Office1.
● Add User1 to the Insider Risk Management Admins role group.
You need to ensure that User1 can perform insider risk management tasks for only the users and the devices in Office1.
What should you create first?
- A . a dynamic device group
- B . a dynamic user group
- C . an administrative unit
- D . a management group
C
Explanation:
To ensure User1 can perform insider risk management tasks only for the users and devices in Office1, the first step is to create an administrative unit in Microsoft Entra ID (formerly Azure AD).
Administrative units allow you to scope permissions to specific users, devices, and locations. By creating an administrative unit for Office1 and assigning User1 to the Insider Risk Management Admins role group within that unit, User1 will only have access to users and devices in Office1.
You have a Microsoft 365 E5 subscription that uses Microsoft Purview.
You create a communication compliance policy named Policy1 and select Detect Microsoft Copilot interactions.
Which two trainable classifiers will be added to Policy1 automatically? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Unauthorized disclosure
- B . Prompt Shields
- C . Threat
- D . Corporate Sabotage
- E . Protected Materials
A, E
Explanation:
When you create a communication compliance policy in Microsoft Purview and select "Detect Microsoft Copilot interactions," certain trainable classifiers are automatically added to help detect sensitive or inappropriate AI usage.
The "Unauthorized disclosure" classifier helps detect cases where users might share confidential or sensitive information via Copilot interactions, preventing unintended data leaks. The "Protected Materials" classifier is used to identify sensitive or restricted content that should not be shared through Copilot, ensuring compliance with organizational policies.
You have a Microsoft 365 E5 subscription that uses Microsoft Purview.
You create a communication compliance policy named Policy1 and select Detect Microsoft Copilot interactions.
Which two trainable classifiers will be added to Policy1 automatically? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Unauthorized disclosure
- B . Prompt Shields
- C . Threat
- D . Corporate Sabotage
- E . Protected Materials
A, E
Explanation:
When you create a communication compliance policy in Microsoft Purview and select "Detect Microsoft Copilot interactions," certain trainable classifiers are automatically added to help detect sensitive or inappropriate AI usage.
The "Unauthorized disclosure" classifier helps detect cases where users might share confidential or sensitive information via Copilot interactions, preventing unintended data leaks. The "Protected Materials" classifier is used to identify sensitive or restricted content that should not be shared through Copilot, ensuring compliance with organizational policies.
HOTSPOT
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
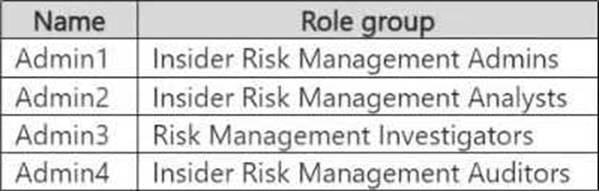
You plan to create a Microsoft Purview insider risk management case named Case1.
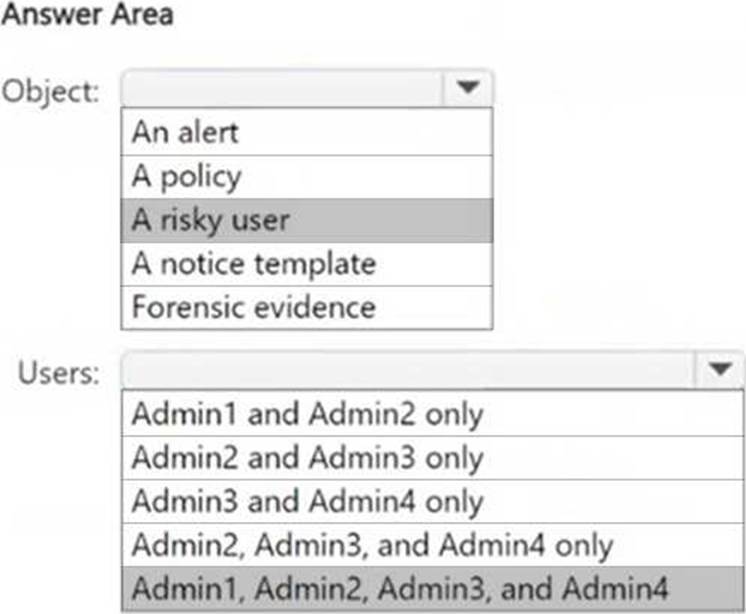
Which insider risk management object should you select first, and which users will be added as contributors for Case1 by default? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Box 1: When creating a Microsoft Purview Insider Risk Management case, you must first select a risky user to investigate. The case will be built around this specific user’s activities, linking alerts and risk signals to the investigation.
Box 2: The Insider Risk Management role groups determine who can access and contribute to cases:
● Admin1 (Insider Risk Management Admins) → Full admin access.
● Admin2 (Insider Risk Management Analysts) → Analysts who review cases.
● Admin3 (Risk Management Investigators) → Investigators who work on cases.
● Admin4 (Insider Risk Management Auditors) → Auditors who oversee cases.
All these roles have default access to insider risk cases in Microsoft Purview, so all four admins are added as contributors.
