Practice Free SC-401 Exam Online Questions
HOTSPOT
You have a Microsoft 365 E5 subscription that contains a user named User1.
You deploy Microsoft Purview Data Security Posture Management for AI (DSPM for AI).
You need to ensure that User1 can perform the following actions:
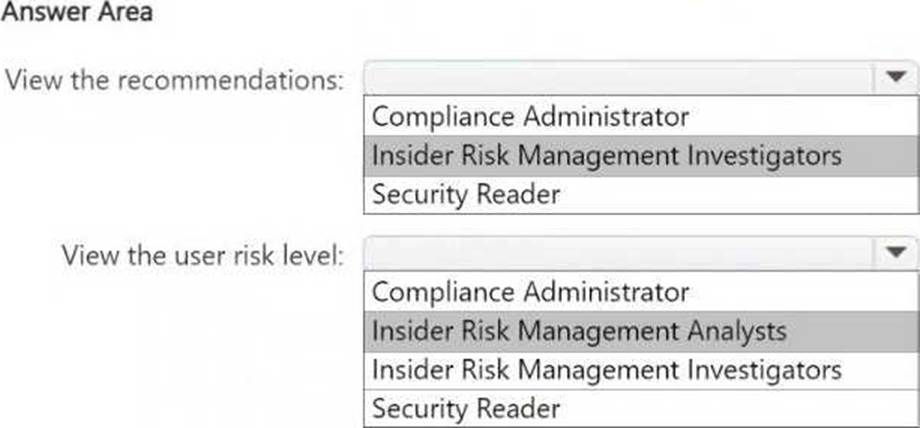
● View recommendations from the Recommendations page.
● View the user risk level for all events by using Activity explorer.
The solution must follow the principle of least privilege.
To which role group should you add User1 for each action? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
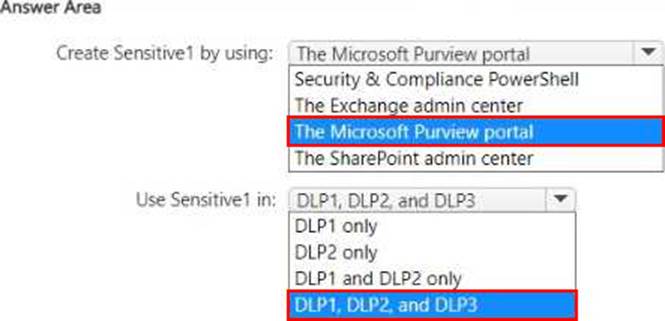
Explanation:
Box 1: The Insider Risk Management Investigators role allows users to view recommendations related to insider risk cases and Microsoft Purview DSPM for AI insights. This role is appropriate because it grants access to review AI-related risk recommendations without unnecessary administrative privileges.
Box 2: The Insider Risk Management Analysts role allows users to analyze user risk levels and events using Activity Explorer. This follows the principle of least privilege, ensuring that User1 can only view risk levels and investigate but does not gain full administrative control over insider risk policies.
HOTSPOT
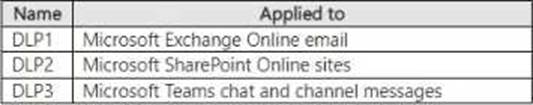
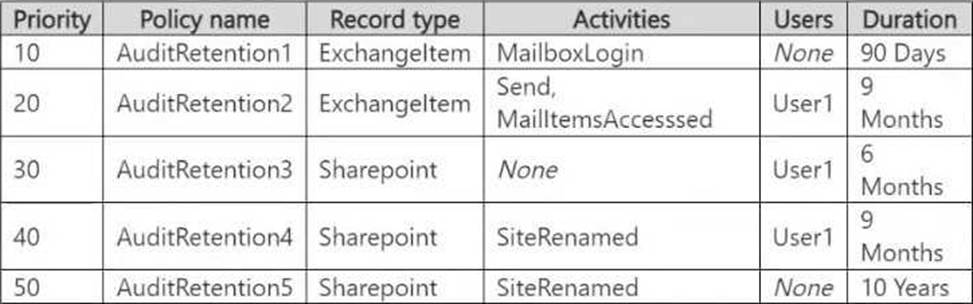
You have a Microsoft 365 E5 subscription that contains the data loss prevention (DLP) policies shown in the following table.
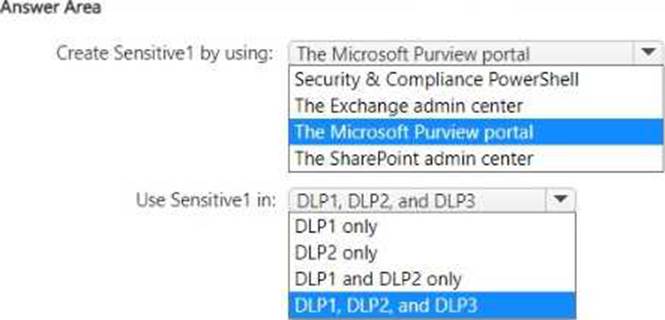
You have a custom employee information form named Template1 .docx.
You plan to create a sensitive info type named Sensitive! that will use the document fingerprint from Template1.docx.
What should you use to create Sensitive1, and in which DLP policies can you use Sensitive1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a user named User1. You deploy Microsoft Purview Data Security Posture Management for AD (DSPM for AD). You need to ensure that User1 can verify the auditing status of the subscription. The solution must follow the principle of least privilege.
To which role group should you add User1?
- A . Insider Risk Management Analysts
- B . Security Reader
- C . Insider Risk Management Investigators
- D . View-Only Organization Management for Microsoft Exchange Online
You have a Microsoft 365 subscription that contains two Microsoft SharePoint Online sites named
Site1 and Site2.
You plan to use policies to meet the following requirements:
• Add a watermark of Confidential to a document if the document contains the words Project1 or Project2.
• Retain a document for seven years if the document contains credit card information.
• Add a watermark of Internal Use Only to all the documents stored on Site2.
• Add a watermark of Confidential to all the documents stored on Site1.
You need to recommend the minimum number of sensitive info types required.
How many sensitive info types should you recommend?
- A . 1
- B . 2
- C . 3
- D . 4
You have a Microsoft 365 E5 subscription.
You need to create static retention policies for the following locations:
● Teams chats
● Exchange email
● SharePoint sites
● Microsoft 365 Groups
● Teams channel messages
What is the minimum number of retention policies required?
- A . 1
- B . 2
- C . 3
- D . 4
- E . 5
C
Explanation:
In Microsoft Purview Data Lifecycle Management, different Microsoft 365 locations require separate retention policies because they fall under different storage and compliance models.
Teams Chats & Teams Channel Messages (1 Policy) require a separate retention policy because Teams messages are stored differently than Exchange and SharePoint content. One policy can cover both Teams chats and Teams channel messages. Exchange Email (1 Policy) requires its own separate policy since emails are managed differently than Teams or SharePoint content. SharePoint Sites & Microsoft 365 Groups (1 Policy) are both stored in SharePoint Online, so they can be managed under one policy.
You have a Microsoft 365 E5 subscription that uses Microsoft Purview.
You are evaluating the use of custom data assessment scans to identify the potential oversharing of data in the subscription.
What is the maximum number of items the data assessments can support per location?
- A . 50.000
- B . 100.000
- C . 200.000
- D . 500.000
HOTSPOT
You have a Microsoft 365 E5 subscription that contains two users named User1 and User2.
You create the audit retention policies shown in the following table.
The users perform the following actions:
● User1 renames a Microsoft SharePoint Online site.
● User2 sends an email message.
How long will the audit log records be retained for each action? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
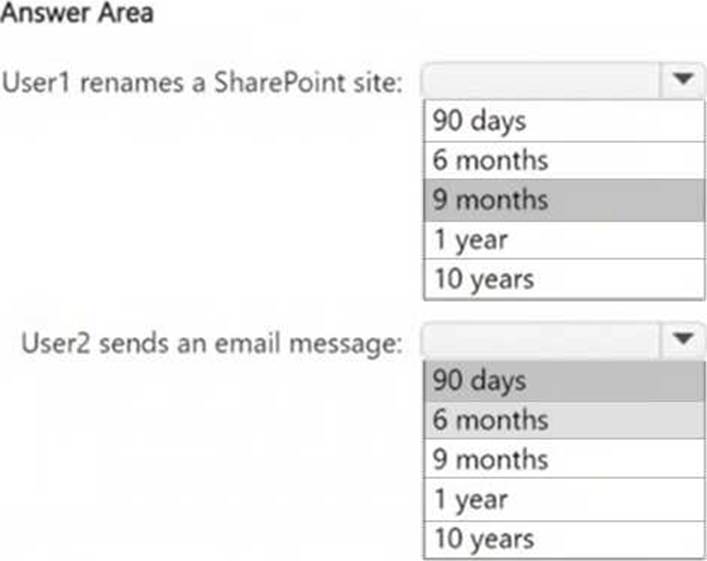
The action "SiteRenamed" for SharePoint is covered under the AuditRetention4 policy, which applies to User1 and retains logs for 9 months.
The action "Send" for ExchangeItem is covered under the AuditRetention2 policy, but this policy applies only to User1. Since User2 is not covered under a specific policy, the default retention period for audit logs in Microsoft Purview is 90 days.
HOTSPOT
You have a Microsoft 365 E5 subscription that contains two users named User1 and User2.
You create the audit retention policies shown in the following table.

The users perform the following actions:
● User1 renames a Microsoft SharePoint Online site.
● User2 sends an email message.
How long will the audit log records be retained for each action? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.


Explanation:
The action "SiteRenamed" for SharePoint is covered under the AuditRetention4 policy, which applies to User1 and retains logs for 9 months.
The action "Send" for ExchangeItem is covered under the AuditRetention2 policy, but this policy applies only to User1. Since User2 is not covered under a specific policy, the default retention period for audit logs in Microsoft Purview is 90 days.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You recently discovered that the developers at your company emailed Azure Storage Account keys in plain text to third parties.
You need to ensure that when Azure Storage Account keys are emailed, the emails are encrypted. Solution: You create a data loss prevention (DLP) policy that has only the Exchange email location selected.
Does this meet the goal?
- A . Yes
- B . No
A
Explanation:
To ensure Azure Storage Account keys are encrypted when sent via email, you need a Data Loss Prevention (DLP) policy that detects Azure Storage Account keys using a sensitive information type and automatically encrypts emails containing these keys.
A DLP policy with Exchange email as the only location meets this requirement because it identifies sensitive data in email messages and it applies protection actions, such as encryption, blocking, or alerts.
Nate: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You have computers that run Windows 11 and have Microsoft 365 Apps installed. The computers are joined to a Microsoft Entra tenant.
You need to ensure that Endpoint DLP policies can protect content on the computers.
Solution: You onboard the computers to Microsoft Defender for Endpoint.
Does this meet the goal?
- A . Yes
- B . No
