Practice Free 220-1201 Exam Online Questions
Which of the following connectors can be used to charge most modern mobile devices and may have the capacity to send data audio and video?
- A . Lightning
- B . USB-C
- C . Micro USB
- D . MiniUSB
B
Explanation:
B. USB-C:
USB-C is a versatile connector that supports charging, high-speed data transfer, and the ability to send audio and video signals (e.g., DisplayPort over USB-C).
It is used by most modern mobile devices and laptops because of its fast transfer speeds and power delivery capabilities.
Incorrect Options:
Which of the following networking technologies allows for high-speed data transmission over short distances between devices like smartphones and tablets?
- A . Near-field communication
- B . Zigbee
- C . Infrared
- D . Wi-Fi Direct
D
Explanation:
Wi-Fi Direct is designed to provide high-speed, short-range wireless communication directly between devices such as smartphones, tablets, laptops, and printers without requiring a traditional wireless access point. According to CompTIA Core 1 (220-1201) networking objectives, Wi-Fi Direct uses standard Wi-Fi radio technology, allowing devices to communicate at speeds comparable to typical wireless LAN connections.
Near-field communication (NFC) operates at extremely short distances (typically a few centimeters) and supports very low data transfer rates, making it unsuitable for high-speed data transmission. Zigbee is a low-power, low-bandwidth protocol commonly used for IoT and home automation devices, not for high-speed data sharing. Infrared requires line-of-sight and offers limited data rates, which restricts its usefulness for modern mobile devices.
Wi-Fi Direct is commonly used for tasks such as file sharing, screen mirroring, and device-to-device printing. CompTIA emphasizes understanding the differences between short-range wireless technologies, particularly distinguishing high-throughput solutions like Wi-Fi Direct from low-power or proximity-based technologies.
Reference: CompTIA A+ Core 1 (220-1201) Official Study Guide C Wireless Networking Technologies
A company is testing the latest model of a laptop. After turning on the laptop, there is a noticeable burning smell.
Which of the following steps should a technician take to troubleshoot the laptop issue? (Select two).
- A . Turn it off and disconnect all power sources.
- B . Submit an emergency request to the local facilities manager.
- C . Check for foreign objects, liquid spills, and internal damage.
- D . Contact the vendor and submit a return request.
- E . Remove the device from the MDM.
- F . Try an alternate AC adapter.
A,C
Explanation:
When a technician encounters a burning smell, it is a critical safety issue. The first response must be to immediately power down and disconnect the device from all power sources to prevent electric shock, fire, or further hardware damage.
From the CompTIA A+ 220-1101 Official Study Guide, Objective 4.1 C Troubleshoot common hardware problems:
"Signs of electrical issues such as burning smells, smoke, or sparks require an immediate shutdown of the system and disconnection from any power source."
After ensuring safety, the technician should inspect the hardware for visible signs of damage:
From the same Objective (4.1):
"Inspect for foreign objects, liquid damage, or burnt components. These can cause short circuits or thermal events that may damage the motherboard or other internal components."
These steps are standard practice in the industry to ensure safe and accurate diagnosis of faulty devices. Trying a different adapter (Option F) may make the problem worse, and contacting vendors (Option D) comes after initial safety and inspection.
Verified Source:
CompTIA A+ Core 1 (220-1101) Official Study Guide, Chapter 4: Troubleshooting Hardware Problems CompTIA Exam Objectives 220-1101, Domain 4.0 C Hardware and Network Troubleshooting
Which of the following can be used to logically segment networks?
- A . MAC
- B . VLAN
- C . NIC
- D . DSL
B
Explanation:
A VLAN (Virtual Local Area Network) is a network technology used to logically segment a physical network into multiple distinct broadcast domains, even if they share the same hardware.
From the CompTIA A+ 220-1101 Official Study Guide, Objective 2.2 C Compare and contrast common networking hardware:
“VLANs allow network administrators to segment a network logically, isolating broadcast traffic and improving security and management, regardless of the physical network layout.”
Other options explained:
MAC (Media Access Control) is a hardware address, not a segmentation method. NIC (Network Interface Card) is network hardware, not for logical segmentation. DSL (Digital Subscriber Line) is an internet connection type. Verified Source:
CompTIA A+ Core 1 (220-1101) Official Study Guide, Chapter 2: Networking Concepts CompTIA Exam Objectives 220-1101, Domain 2.2
Which of the following printing initiatives would be best to accomplish environmentally friendly objectives?
- A . Requiring user authentication for printing
- B . Locking down printing to only certain individuals
- C . Modifying duplex settings to double-sided
- D . Changing the print quality settings to best
C
Explanation:
Comprehensive and Detailed Step-by-Step
Modifying duplex settings to double-sided:
Printing on both sides of the paper (duplex printing) reduces paper usage, making it one of the most effective environmentally friendly printing initiatives.
It directly minimizes waste and supports sustainability goals in the workplace.
Incorrect Options:
Which of the following best describes a Type 2 hypervisor?
- A . It works as a firewall to control network traffic.
- B . It interacts directly with the underlying hardware.
- C . It runs on a host operating system.
- D . It brings higher CPU capabilities to virtual machines.
C
Explanation:
CompTIA A+ divides hypervisors into two main categories: Type 1 (bare-metal) and Type 2 (hosted). A Type 2 hypervisor runs on top of an existing host operating system such as Windows, macOS, or Linux. It relies on the host OS for device drivers, hardware interaction, and resource management. Examples include VMware Workstation, Oracle VirtualBox, and Parallels Desktop.
Type 2 hypervisors are ideal for lab environments, testing, learning, and small-scale virtualization because they do not require dedicated hardware or direct hardware control. The host OS loads first, and the hypervisor runs as an application, allowing users to create and manage virtual machines from within the OS environment.
Option B describes a Type 1 hypervisor, which installs directly on hardware without a host OS.
Option A is unrelated, as firewalls are separate from virtualization technology.
Option D is incorrect because hypervisors do not inherently increase CPU capabilities; they merely allocate existing hardware resources to virtual machines.
Thus, the correct and CompTIA-aligned description of a Type 2 hypervisor is that it runs on a host operating system.
Two workstations are connected to a LAN that does not have internet access. A user reports that they are unable to access a network service after a power outage. The web page warns the user that the site is insecure.
Which of the following will most likely resolve the certificate error? (Select two)
- A . Renewing the SSL certificate
- B . Setting the system date and time in the BIOS
- C . Replacing the CMOS battery
- D . Adjusting the browser security settings
- E . Opening the HTTPS port on the workstation’s firewall
- F . Scanning the LAN for unauthorized devices
AB
Explanation:
Certificate security warnings commonly occur when a system cannot properly validate the validity period of an SSL/TLS certificate. According to CompTIA Core 1 (220-1201) networking and security fundamentals, two of the most common causes of certificate errors are expired certificates and incorrect system date and time.
After a power outage, systems without internet access cannot automatically synchronize time with an NTP server. If the system clock resets or becomes inaccurate, the browser may interpret a valid certificate as expired or not yet valid, triggering an “insecure site” warning. Setting the correct system date and time in the BIOS immediately resolves this mismatch and is a primary troubleshooting step.
Additionally, renewing the SSL certificate resolves errors if the certificate has legitimately expired or was invalid at the time of access. This is especially relevant for internal network services using self-signed or internally managed certificates.
Replacing the CMOS battery can prevent future time resets but does not immediately correct the certificate error. Adjusting browser security settings is unsafe and not recommended. Firewall port configuration and network scanning are unrelated to certificate validation.
CompTIA emphasizes validating time/date accuracy and certificate status as core steps when resolving certificate-related security warnings.
Reference: CompTIA A+ Core 1 (220-1201) Official Study Guide C Certificates, HTTPS, System Time, and Network Security
Which of the following internet connection types is primarily used for high-speed internet access in rural areas where traditional broadband services are unavailable?
- A . Fiber
- B . Satellite
- C . DSL
- D . Cable
B
Explanation:
Satellite internet is commonly used in rural or remote locations where wired broadband options such as cable and fiber are not available and where DSL service may be limited by distance from the provider’s equipment. CompTIA A+ Core 1 emphasizes understanding internet connection types and where each is typically deployed. Satellite works by using a dish at the customer site to communicate with a satellite, which then relays traffic to a ground station connected to the internet backbone. Because it does not depend on local cable plant, telephone central office proximity, or neighborhood fiber buildouts, it can be deployed in areas with minimal infrastructure.
Fiber (A) provides very high speeds and low latency but requires extensive physical infrastructure that is often lacking in rural regions. Cable (D) also requires a local cable network buildout and is usually concentrated in more populated areas. DSL (C) uses existing telephone lines, but performance and availability depend heavily on distance from the DSL provider’s equipment, making it unreliable or unavailable in sparsely populated regions. While satellite often involves higher latency and can be affected by weather, it remains a primary option when traditional broadband services are not present.
HOTSPOT
A technician is diagnosing several device issues reported by employees.
INSTRUCTIONS
Click on each device to review the issue. Then select the appropriate issue and solution from the drop-down menu. Each option may be used more than once.


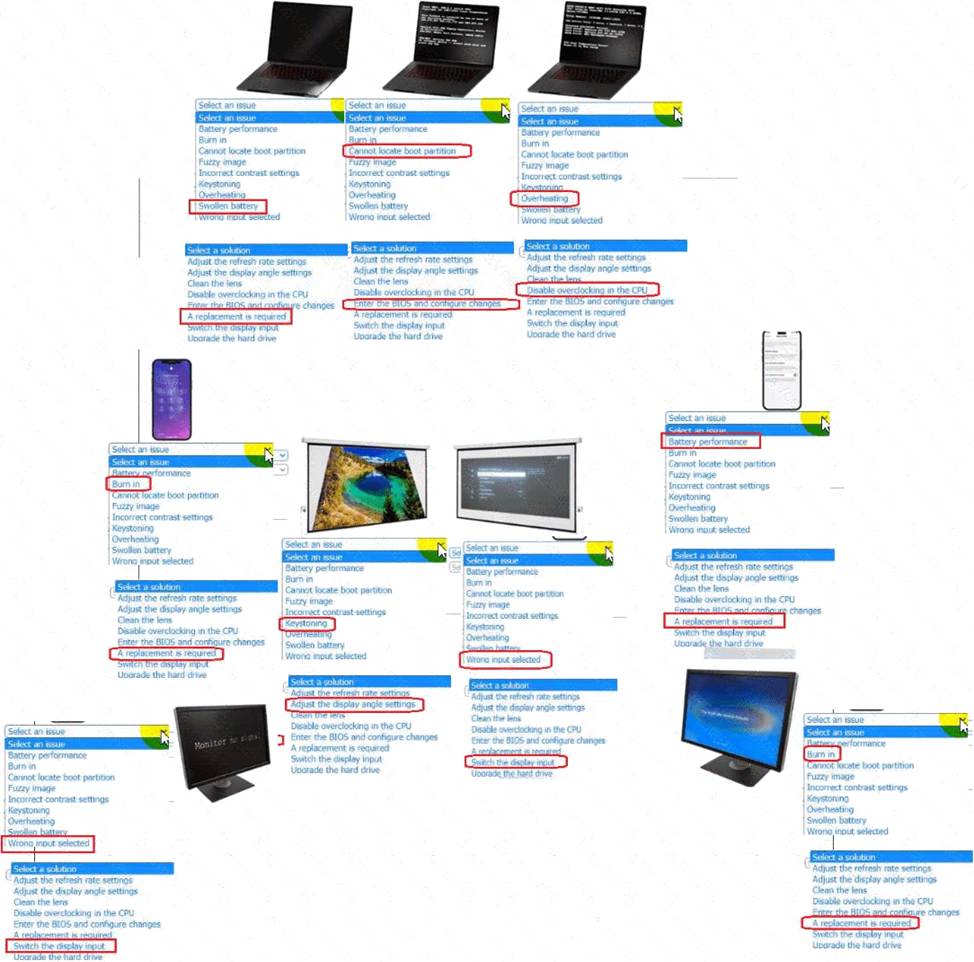
Explanation:
A screenshot of a computer AI-generated content may be incorrect.
A client is unable to unlock their smartphone. When they try to enter their code, the input is unsuccessful.
Which of the following components has most likely failed?
- A . Charging port
- B . Touch screen
- C . OLED
- D . Biometric scanner
B
Explanation:
The most likely failed component in this scenario is the touch screen. According to CompTIA Core 1 (220-1201) mobile device hardware and troubleshooting objectives, smartphones rely on the digitizer (touch screen layer) to detect user input such as taps, swipes, and on-screen keyboard presses. If the device powers on and displays the lock screen but does not register code input, this strongly indicates a failure in the touch input functionality.
A failed charging port would prevent the device from charging but would not affect the ability to enter a passcode if the device is powered on. An OLED failure would result in display issues such as a blank screen, flickering, discoloration, or no image at all―none of which are described in this scenario. A biometric scanner (fingerprint or facial recognition) failure would only impact biometric authentication methods; users would still be able to unlock the phone using a PIN or passcode.
CompTIA emphasizes distinguishing between display output issues and input issues when troubleshooting mobile devices. Since the problem specifically involves unsuccessful code entry despite the phone being operational, the root cause is the touch screen.
Reference: CompTIA A+ Core 1 (220-1201) Official Study Guide C Mobile Device Components, Touchscreens, and Troubleshooting
