Practice Free SC-401 Exam Online Questions
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 11. The computers are onboarded to Microsoft Purview.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Microsoft Defender for Cloud Apps, you mark the application as Unsanctioned.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
Marking Tailspin_scanner.exe as "Unsanctioned" in Microsoft Defender for Cloud Apps only blocks its usage in cloud-based activities (such as accessing SharePoint, OneDrive, or Exchange Online). However, it does not prevent a locally installed application on Windows 11 devices from accessing sensitive files.
To block Tailspin_scanner.exe from accessing sensitive documents while allowing it to access other files, the correct solution is to use Microsoft Purview Endpoint Data Loss Prevention (Endpoint DLP) and add Tailspin_scanner.exe to the Restricted Apps list.
Endpoint DLP allows you to block specific applications from accessing sensitive files while keeping general access available. Restricted Apps List in Endpoint DLP ensures that Tailspin_scanner.exe cannot open, copy, or process protected documents, but it can still function normally for non-sensitive content.
You are creating a custom trainable classifier to Identify organizational product codes referenced in Microsoft 36S content. You identify 300 files to use as seed content When? should you store the seed content?
- A . a Microsoft OneDrive folder
- B . a Microsoft Exchange Online shared mailbox
- C . an Azure file share
- D . a Microsoft SharePoint Online folder
You have Microsoft 365 E5 subscription.
You create two alert policies named Policy1 and Policy2 that will be triggered at the times shown in the following table.
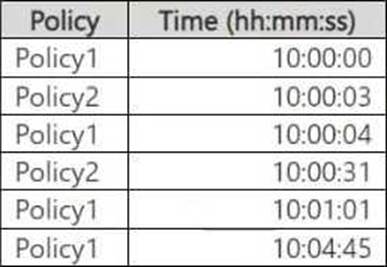
How many alerts will be added to the Microsoft Purview portal?
- A . 2
- B . 3
- C . 4
- D . 5
- E . 6
D
Explanation:
In Microsoft Purview, when multiple alert policies trigger alerts, duplicate alerts within a short period (typically 5 minutes) may be suppressed to avoid redundancy.
Step-by-step Analysis:
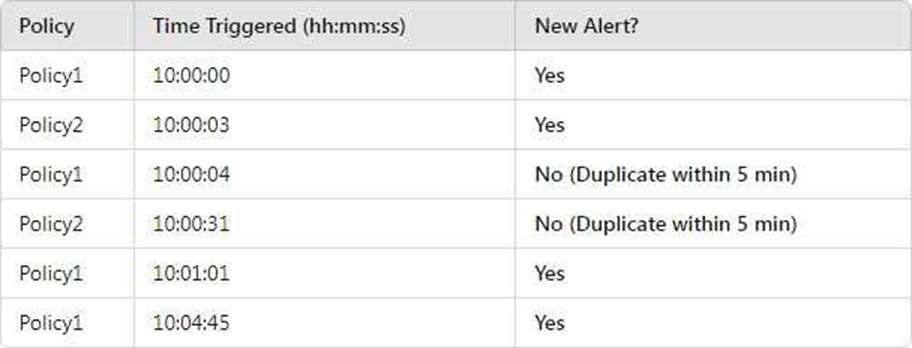
● Policy1 at 10:00:04 is ignored because Policy1 already triggered at 10:00:00, and it’s within 5 minutes.
● Policy2 at 10:00:31 is ignored because Policy2 already triggered at 10:00:03, and it’s within 5 minutes.
● Policy1 at 10:01:01 is a new alert because it’s over 1 minute after the previous Policy1 alert.
● Policy1 at 10:04:45 is a new alert because it’s over 3 minutes after the previous Policy1 alert.
You have a Microsoft 365 tenant that is opt-in for trainable classifiers.
You need to ensure that a user named User1 can create custom trainable classifiers. The solution must use the principle of least privilege.
Which role should you assign to User1?
- A . Security Administrator
- B . Compliance Administrator
- C . Global Administrator
- D . Security Operator
You have a Microsoft 365 E5 subscription.
You plan to use insider risk management to collect and investigate forensic evidence.
You need to enable forensic evidence capturing.
What should you do first?
- A . Configure the information protection scanner.
- B . Claim capacity.
- C . Enable Adaptive Protection.
- D . Create priority user groups.
HOTSPOT
You have a Microsoft 365 E5 subscription.
You have a file named Customer.csv that contains a list of 1,000 customer names.
You plan to use Customer.csv to classify documents stored in a Microsoft SharePoint Online library.
What should you create in the Microsoft Purview portal, and which type of element should you select? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
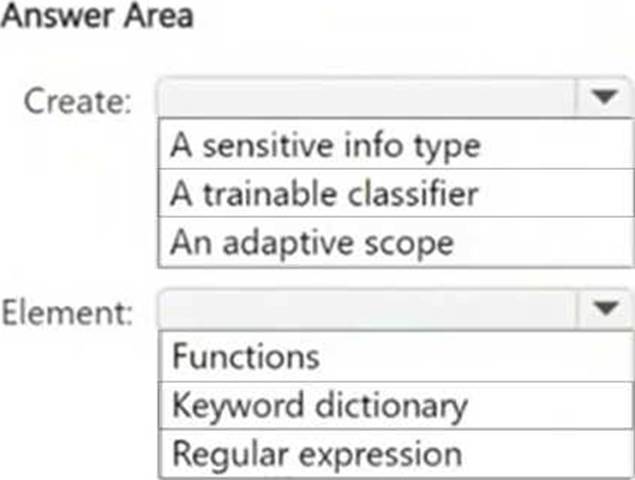
HOTSPOT
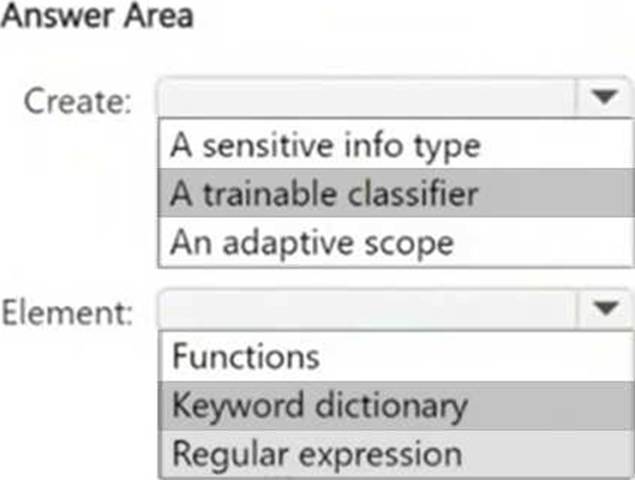
You have a Microsoft 365 E5 subscription.
You have a file named Customer.csv that contains a list of 1,000 customer names.
You plan to use Customer.csv to classify documents stored in a Microsoft SharePoint Online library.
What should you create in the Microsoft Purview portal, and which type of element should you select? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.


HOTSPOT
You have a Microsoft 365 tenant
You need to create a new sensitive into type for items that contain the following:
• An employee ID number that consists of the hire date of the employee followed by a three digit number
• The words "Employee", "ID", or "Identification" within 300 characters of the employee ID number
What should you use for the primary and secondary elements? To answer, select the appropriate options m the answer area. NOTE: Each correct selection is worth one point
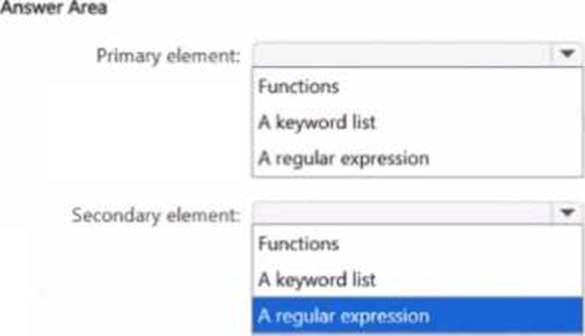
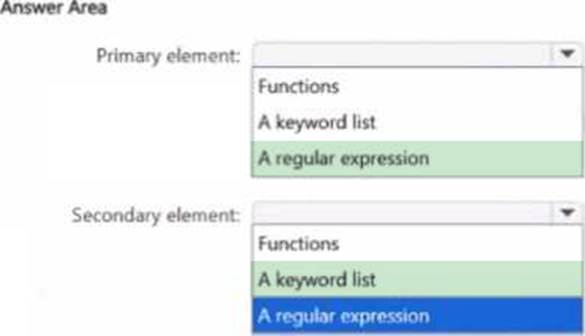
HOTSPOT
You have a Microsoft 36S subscription that contains the sensitive information types (SITs) shown in the following exhibit.
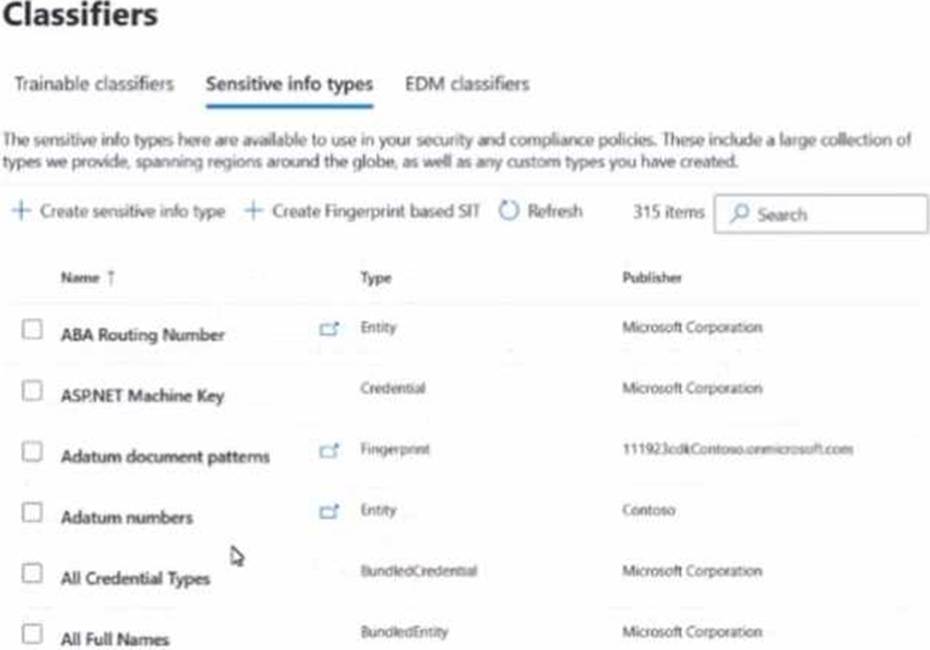
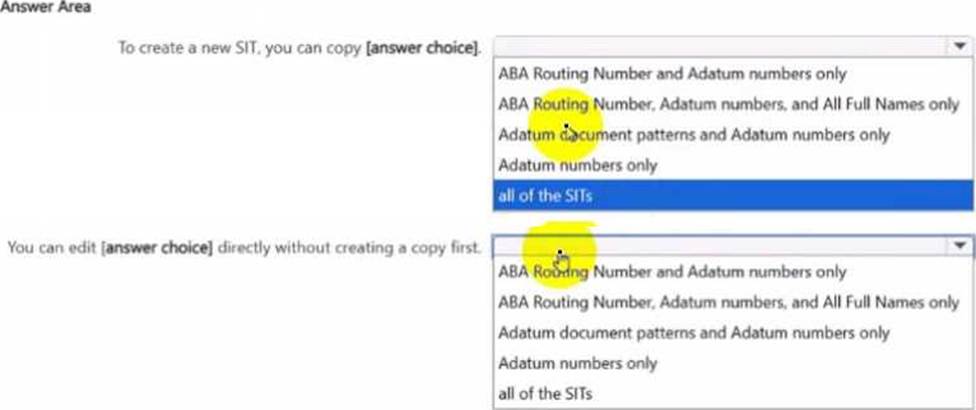
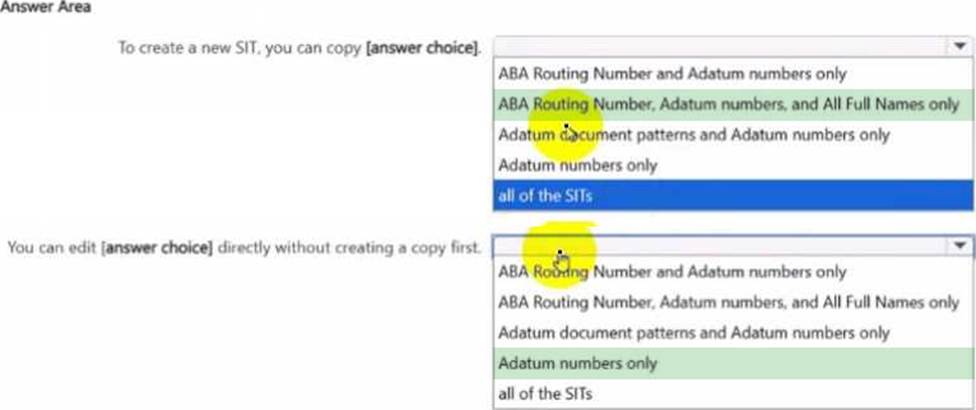
Use the drop-down menus To select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct flection is worth one point.
HOTSPOT
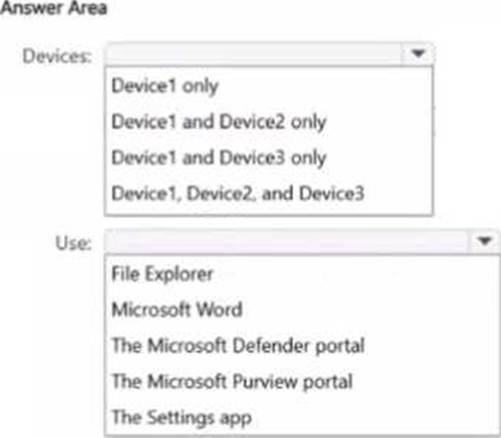
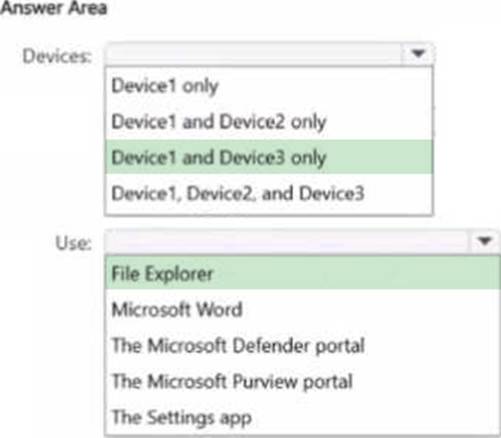
You have a Microsoft 36S ES subscription that contains the devices shown in the following table.
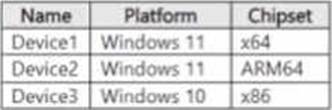
You publish Microsoft Purview Information Protection sensitivity labels.
You plan to deploy the information protection client to the devices. The solution must ensure that the labels can be applied to sensitive images and documents
On which devices can you install the information protection client, and what should users use to apply labels? To answer, select the appropriate options in the answer area.