Practice Free DP-300 Exam Online Questions
You have a Microsoft SQL Server 2019 instance in an on-premises datacenter. The instance contains a 4-TB database named DB1.
You plan to migrate DB1 to an Azure SQL Database managed instance.
What should you use to minimize downtime and data loss during the migration?
- A . distributed availability groups
- B . database mirroring
- C . log shipping
- D . Database Migration Assistant
D
Explanation:
Ref: https://docs.microsoft.com/en-us/azure/dms/tutorial-sql-server-to-azure-sql
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Synapse Analytics dedicated SQL pool that contains a table named Table1.
You have files that are ingested and loaded into an Azure Data Lake Storage Gen2 container named container1.
You plan to insert data from the files into Table1 and transform the data. Each row of data in the files will produce one row in the serving layer of Table1.
You need to ensure that when the source data files are loaded to container1, the DateTime is stored as an additional column in Table1.
Solution: You use an Azure Synapse Analytics serverless SQL pool to create an external table that has an additional DateTime column.
Does this meet the goal?
- A . Yes
- B . No
A
Explanation:
In dedicated SQL pools you can only use Parquet native external tables. Native external tables are generally available in serverless SQL pools.
Reference: https://docs.microsoft.com/en-us/azure/synapse-analytics/sql/create-use-external-tables
You have an Azure subscription that contains an instance of SQL Server on an Azure virtual machine named VM1 and a Microsoft Entra Domain Services domain that contains two users named User1 and User2.
On the default instance of SQL Server on VM1, you create a credential named Credentiall for User1.
You need to ensure that User2 can create a SQL Server Agent proxy that will use Credential1. The solution must use the principle of least privilege.
Which role should you assign to User2?
- A . sysadmin
- B . SQLAgentUserRole
- C . SQLAgentOperatorRole
- D . SQLAgentReaderRole
You have an Azure subscription that contains an Azure SQL database. The database contains a table named tablet.
You execute the following Transact-SQL statements.
![]()
You need to reduce the time it takes to perform analytic queries on the database.
Which configuration should you enable?
- A . ROW_ MODE_MEMORY GRANT_FEEDBACK
- B . BATCH MODE_MEMORY GRAIJT_FEEDBACK
- C . BATCH_MODE_ADAPTIVE_TOIMS
- D . BATC H_MODE_ON_ROWSTOR E
DRAG DROP
You need to implement statistics maintenance for SalesSQLDb1. The solution must meet the technical requirements.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
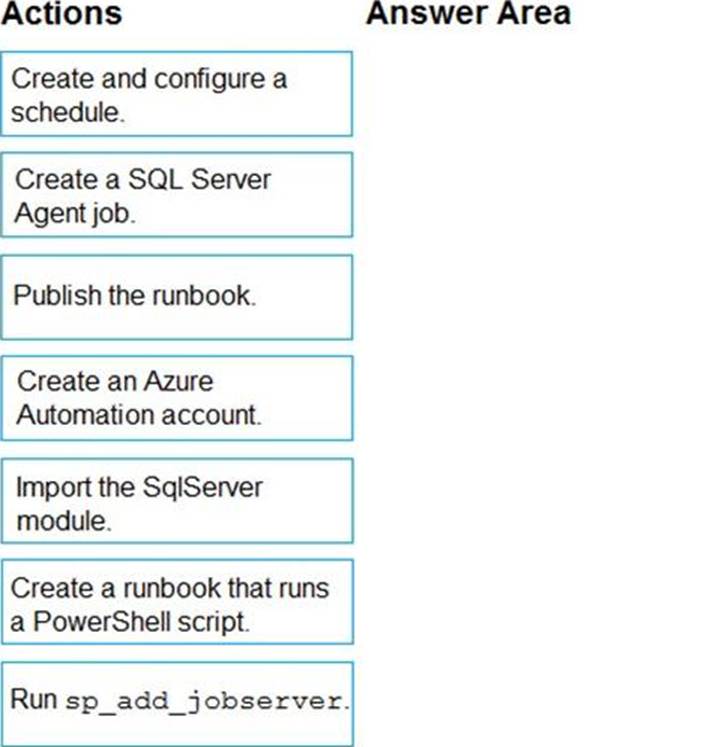
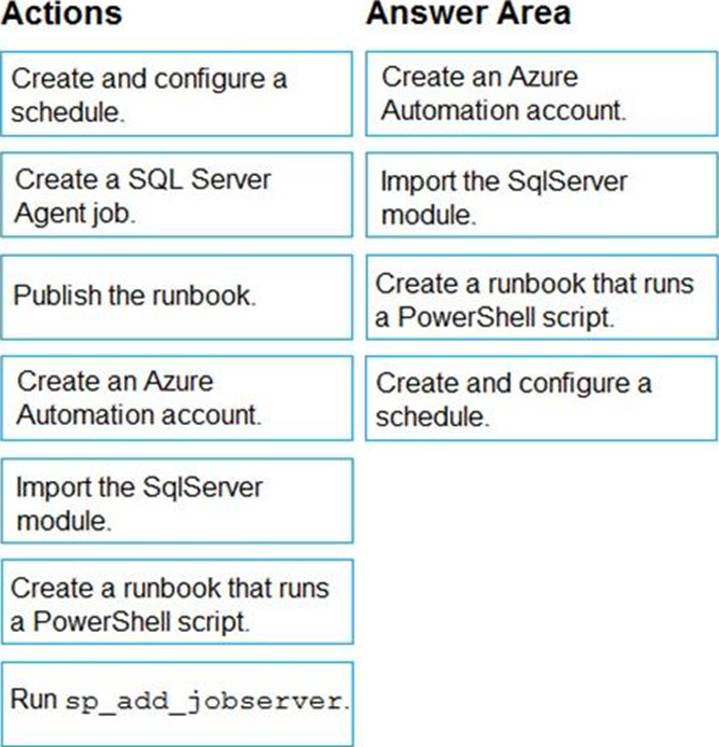
Explanation:
Automating Azure SQL DB index and statistics maintenance using Azure Automation:
DRAG DROP
You have an Azure SQL database that contains a table named Employees. Employees contains a column named Salary.
You need to encrypt the Salary column. The solution must prevent database administrators from reading the data in the Salary column and must provide the most secure encryption.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
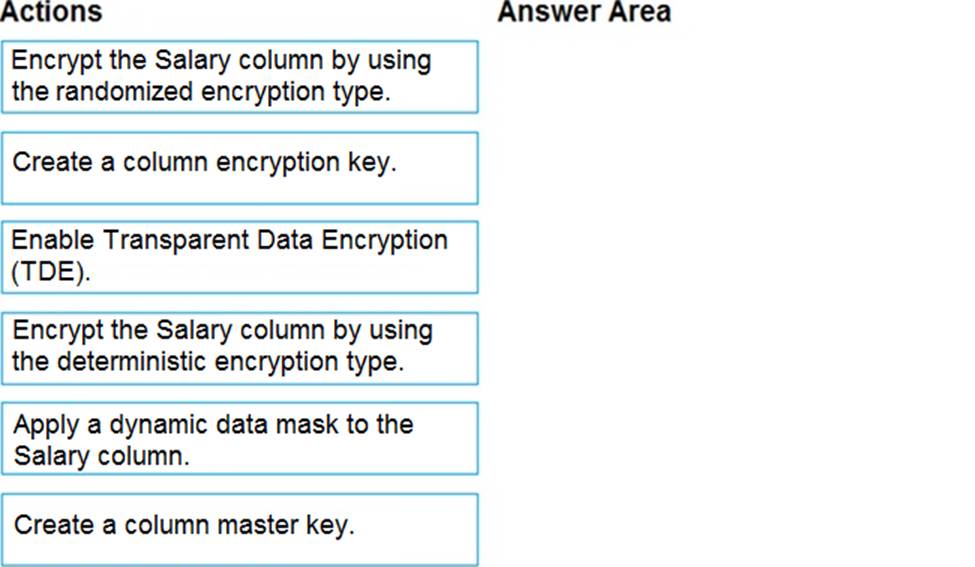
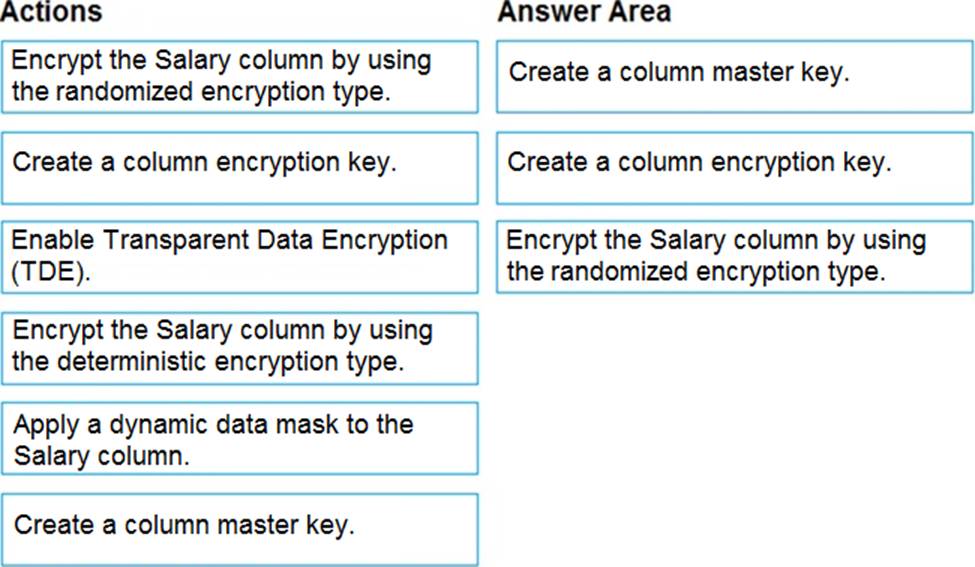
Explanation:
Step 1: Create a column master key
Create a column master key metadata entry before you create a column encryption key metadata entry in the database and before any column in the database can be encrypted using Always Encrypted.
Step 2: Create a column encryption key.
Step 3: Encrypt the Salary column by using the randomized encryption type.
Randomized encryption uses a method that encrypts data in a less predictable manner. Randomized encryption is more secure, but prevents searching, grouping, indexing, and joining on encrypted columns.
Note: A column encryption key metadata object contains one or two encrypted values of a column encryption key that is used to encrypt data in a column. Each value is encrypted using a column master key.
Incorrect Answers:
Deterministic encryption.
Deterministic encryption always generates the same encrypted value for any given plain text value. Using deterministic encryption allows point lookups, equality joins, grouping and indexing on encrypted columns. However, it may also allow unauthorized users to guess information about encrypted values by examining patterns in the encrypted column, especially if there’s a small set of possible encrypted values, such as True/False, or North/South/East/West region.
Reference: https://docs.microsoft.com/en-us/sql/relational-databases/security/encryption/always-encrypted-database-engine
