Practice Free AZ-500 Exam Online Questions
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains an Azure Kubernetes Service (AKS) cluster named AKS1 and an Azure container registry named AZCR1.
You need to ensure that AKS1 can deploy container images stored in AZCR1.
Solution: You configure AKS1 to use a user-assigned managed identity and assign the Azure Kubernetes Service Cluster Admin Role to the managed identity.
Does this meet the requirement?
- A . Yes
- B . No
You have an Azure subscription and the computers shown in the following table.
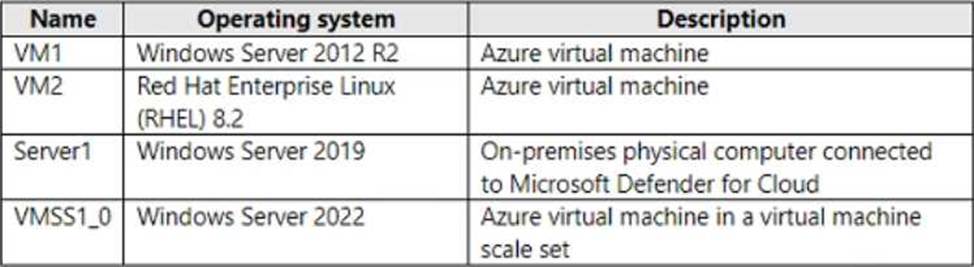
You need to perform a vulnerability scan of the computers by using Microsoft Defender for Cloud.
Which computers can you scan?
- A . VM1 only
- B . VM1 and VM2 only
- C . Server1 and VMSS1.0 only
- D . VM1, VM2, and Server1 only
- E . VM1, VM2, Server1, and VMSS1.0
You have an Azure subscription that contains the virtual machines shown in the following table.
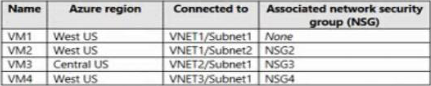
VNET1, VNET2, and VNET3 are peered with each other.
You perform the following actions:
* Create two application security groups named ASG1 and ASG2 in the West US region.
* Add the network interface of VM1 to ASG1.
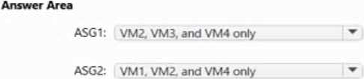
HOTSPOT
You have an Azure subscription that contains three storage accounts, an Azure SQL managed instance named SQL and three Azure SQL databases.
The storage accounts are configured as shown in the following table.
SQ11 has the following settings:
• Auditing: On
• Audit tog destination: storage1
The Azure SQL databases are configured as shown in the following table.
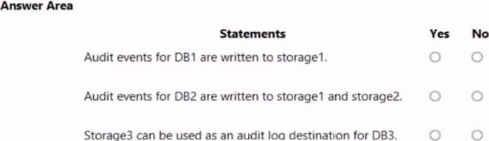

Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/azure-sql/managed-instance/auditing-configure
https://docs.microsoft.com/en-us/azure/azure-sql/database/auditing-overview
You have an Azure subscription that is linked to an Azure AD tenant and contains the resources shown in the following table.
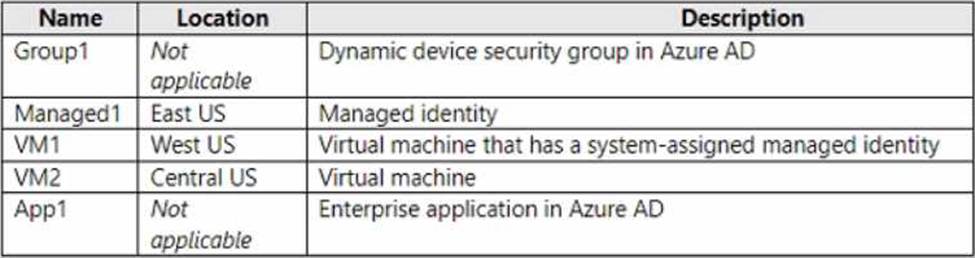
Which resources can be assigned the Contributor role for VM1?
- A . Managed1 and App1 only
- B . Group1 and Managed1 only
- C . Group1. Managed1, and VM2only
- D . Group1, Managed1, VM1. and App1 only
From the Azure portal, you are configuring an Azure policy.
You plan to assign policies that use the DeployIfNotExist, AuditIfNotExist, Append, and Deny effects.
Which effect requires a managed identity for the assignment?
- A . AuditIfNotExist
- B . Append
- C . DeployIfNotExist
- D . Deny
C
Explanation:
When Azure Policy runs the template in the deployIfNotExists policy definition, it does so using a managed identity.
Reference: https://docs.microsoft.com/bs-latn-ba/azure/governance/policy/how-to/remediate-resources
You are collecting events from Azure virtual machines to an Azure Log Analytics workspace. You plan to create alerts based on the collected events
You need to identify which Azure services can be used to create the alerts.
Which two services should you identify? Each correct answer presents a complete solution NOTE: Each correct selection is worth one point.
- A . Azure Monitor
- B . Azure Security Center
- C . Azure Analytics Services
- D . Azure Sentinel
- E . Azure Advisor
AD
Explanation:
https://docs.microsoft.com/en-us/azure/analysis-services/analysis-services-overview
HOTSPOT
You have an Azure subscription that contains the virtual machines shown in the following table.
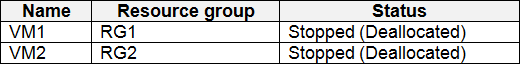
You create the Azure policies shown in the following table.
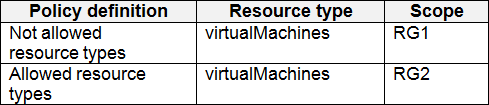
You create the resource locks shown in the following table.
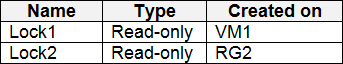
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
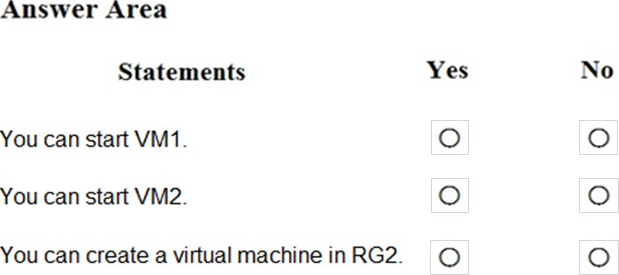
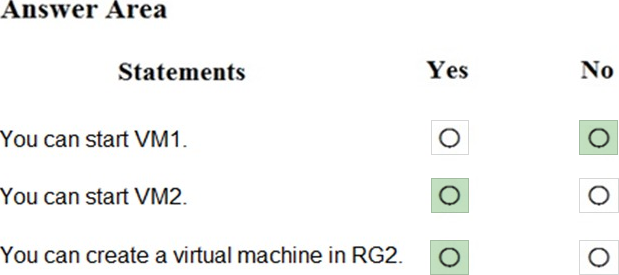
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/governance/blueprints/concepts/resource-locking
You are testing an Azure Kubernetes Service (AKS) cluster.
The cluster is configured as shown in the exhibit. (Click the Exhibit tab.)
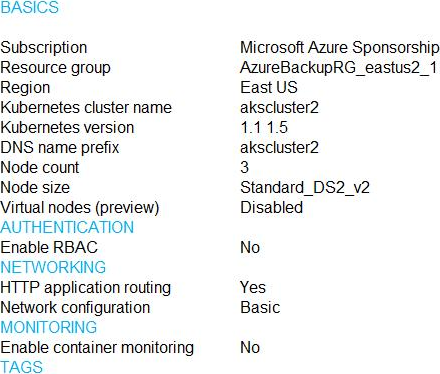
You plan to deploy the cluster to production. You disable HTTP application routing.
You need to implement application routing that will provide reverse proxy and TLS termination for AKS services by using a single IP address.
What should you do?
- A . Create an AKS Ingress controller.
- B . Install the container network interface (CNI) plug-in.
- C . Create an Azure Standard Load Balancer.
- D . Create an Azure Basic Load Balancer.
A
Explanation:
An ingress controller is a piece of software that provides reverse proxy, configurable traffic routing, and TLS termination for Kubernetes services.
Reference: https://docs.microsoft.com/en-us/azure/aks/ingress-tls
HOTSPOT
You have an Azure subscription that contains the resources shown in the following table.
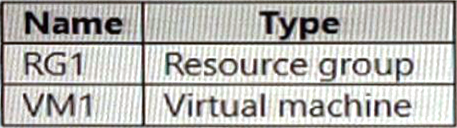
You perform the following tasks:
– Create a managed identity named Managed1.
– Create a Microsoft 365 group named Group1.
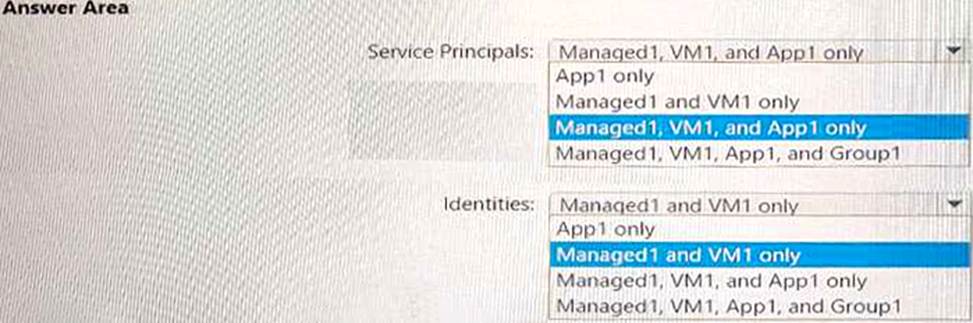
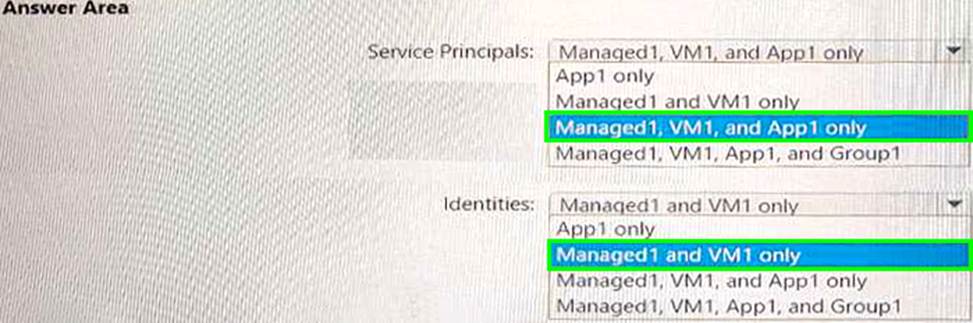
You need to identify which service principals were created and which identities can be assigned the Reader role for RG1.
What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.