Practice Free AZ-500 Exam Online Questions
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription named Sub1.
You have an Azure Storage account named Sa1 in a resource group named RG1.
Users and applications access the blob service and the file service in Sa1 by using several shared access signatures (SASs) and stored access policies.
You discover that unauthorized users accessed both the file service and the blob service.
You need to revoke all access to Sa1.
Solution: You create a lock on Sa1.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
To revoke a stored access policy, you can either delete it, or rename it by changing the signed identifier. Changing the signed identifier breaks the associations between any existing signatures and the stored access policy. Deleting or renaming the stored access policy immediately affects all of the shared access signatures associated with it.
Reference: https://docs.microsoft.com/en-us/rest/api/storageservices/Establishing-a-Stored-Access-Policy
HOTSPOT
You implement the planned changes for ASG1 and ASG2.
In which NSGs can you use ASG1. and the network interfaces of which virtual machines can you assign to ASG2?
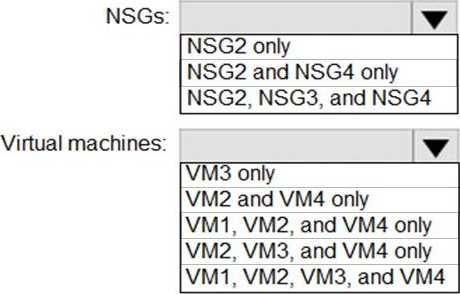
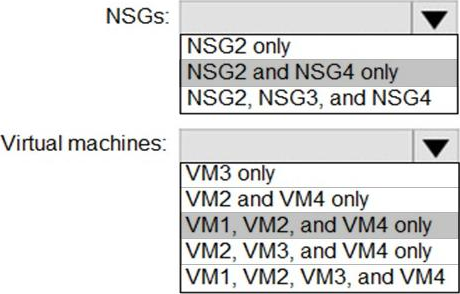
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
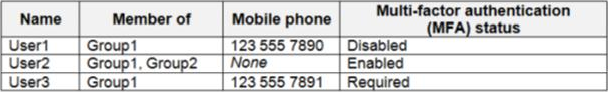
You create and enforce an Azure AD Identity Protection user risk policy that has the following settings:
– Assignment: Include Group1, Exclude Group2
– Conditions: Sign-in risk of Medium and above
– Access: Allow access, Require password change
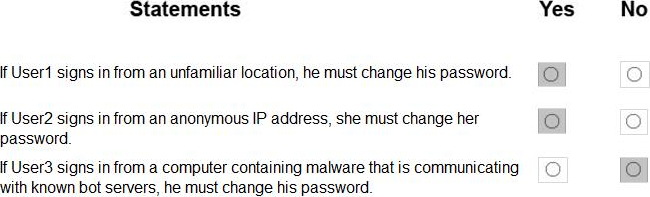
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
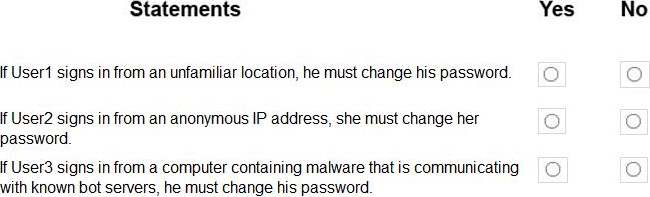
Explanation:
Box 1: Yes
User1 is member of Group1. Sign in from unfamiliar location is risk level Medium.
Box 2: Yes
User2 is member of Group1. Sign in from anonymous IP address is risk level Medium.
Box 3: No
Sign-ins from IP addresses with suspicious activity is low.
Note:
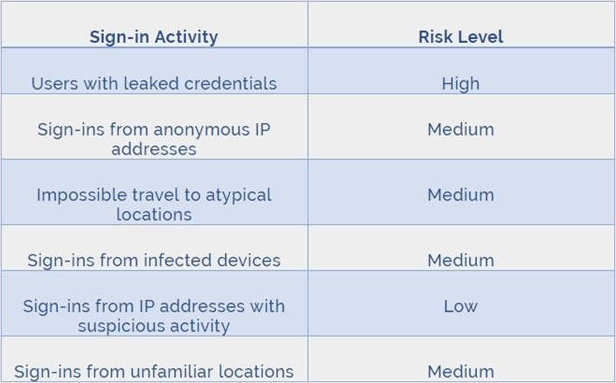
Azure AD Identity protection can detect six types of suspicious sign-in activities:
Users with leaked credentials
Sign-ins from anonymous IP addresses
Impossible travel to atypical locations
Sign-ins from infected devices
Sign-ins from IP addresses with suspicious activity
Sign-ins from unfamiliar locations
These six types of events are categorized in to 3 levels of risks C High, Medium & Low:
Reference: http://www.rebeladmin.com/2018/09/step-step-guide-configure-risk-based-azure-conditional-access-policies/
You have an Azure subscription that contains the resources shown in the following table.
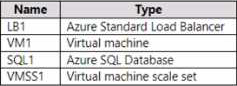
You plan to deploy an Azure Private Link service named APL1.
Which resource must you reference during the creation of APL1?
- A . VMSS1
- B . VM1
- C . SQL
- D . LB1
DRAG DROP
You have an on-premises datacenter.
You have an Azure subscription that contains a virtual machine named VM1. VM1 is connected to a virtual network named VNet1. VNet1 is connected to the on-premises datacenter by using a Site-to-Site (S2S) VPN.
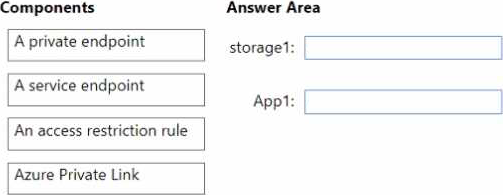
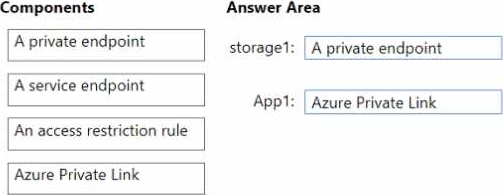
You plan to create an Azure storage account named storage1 and App1.
You need to ensure that network communication to each resource meets the following requirements:
• Connections to App1 must be allowed only from corporate network NAT addresses.
• Connections from VNet1 to storage1 must use the Microsoft backbone network.
• The solution must minimize costs.
What should you configure for each resource? To answer, drag the appropriate components to the correct resources. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
DRAG DROP
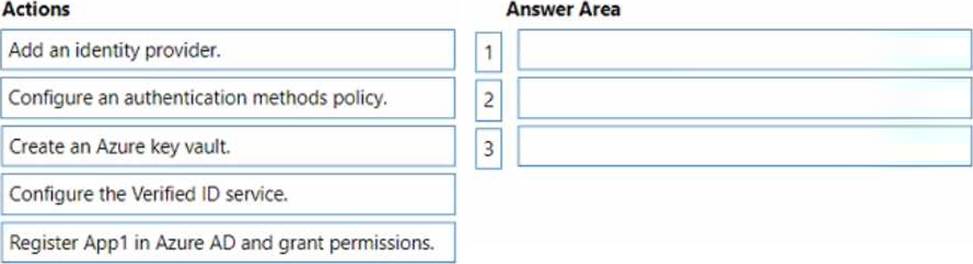
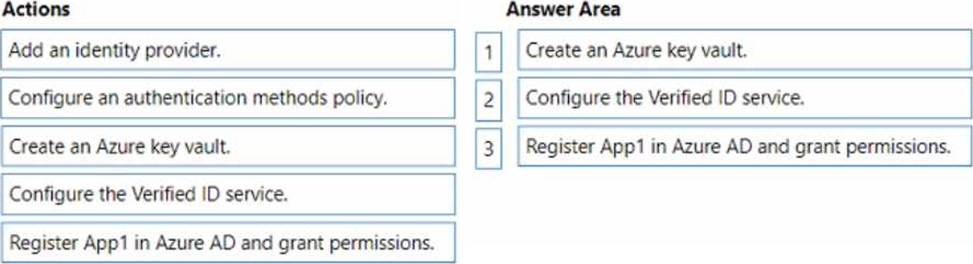
You have an Azure AD Tenant and an application named App1.
You need to ensure that App1 can use Microsoft Entra Verified ID to verify credentials.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Explanation:
https://learn.microsoft.com/en-us/azure/active-directory/verifiable-credentials/verifiable-credentials-configure-tenant
SIMULATION
Lab Task
Task 5
A user named Debbie has the Azure app installed on her mobile device.
You need to ensure that [email protected] is alerted when a resource lock is deleted.
Grant permission to the service principal to access the secrets in the key vault. You can use the Azure portal, Azure PowerShell, or the Azure CLI to do this. You need to assign the Key Vault Secrets User role to the service principal at the scope of the key vault or individual secrets.
Enable template deployment for the key vault. You can use the Azure portal, Azure PowerShell, or the Azure CLI to do this. You need to set the enabledForTemplateDeployment property of the key vault to true.
Reference the secrets in the template by using their resource ID. You can use the listSecrets function to get the resource ID of a secret in the key vault. You need to specify the name of the key vault and the name of the secret as parameters.
Deploy the template by using Azure PowerShell, Azure CLI, or REST API. You can use the New-AzResourceGroupDeployment cmdlet, the az deployment group create command, or the Deployments – Create Or Update REST API to do this. You need to provide the template file or URI and any required parameters. You also need to provide the credentials of the service principal.
You have an Azure subscription.
You plan to create a workflow automation in Microsoft Defender for Cloud that will automatically remediate a security vulnerability.
What should you create first?
- A . an Azure function app
- B . an automation account
- C . a managed identity
- D . an alert rule
- E . an Azure logic app
You have an Azure AD turned that contains a user named User1.
You purchase an App named App1.
User1 needs to publish App1 by using Azure AD Application Proxy.
Which role should you assign to User1?
- A . Hybrid identity Administrator
- B . Cloud App Security Administrator
- C . Application Administrator
- D . Cloud Application Administrate
HOTSPOT
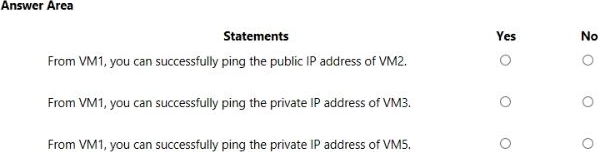
You are evaluating the security of the network communication between the virtual machines in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
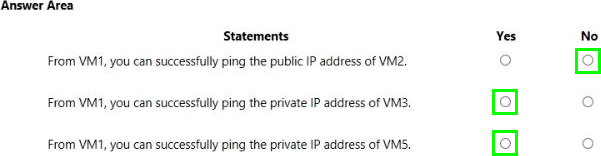
Explanation:
Q1: No {and it should not be allowed as only TCP 80 is allowed from the "Internet" service tag
Q2: Yes {as it should be for VMs in the same local subnet pinging each other on private IP and no NSG configured}
Q3: Yes {VM5 is in subnet where 1st rule of NSG allows any traffic from any source to the destination}
