Practice Free AZ-500 Exam Online Questions
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains an Azure Kubernetes Service (AKS) cluster named AKS1 and an Azure container registry named AZCR1.
You need to ensure that AKS1 can deploy container images stored in AZCR1.
Solution: You assign the AcrPush role-based access control (RBAC) role to the system-assigned managed identity of AKS1.
Does this meet the requirement?
- A . Yes
- B . No
You have an Azure subscription that contains an Azure SQL database named sql1.
You plan to audit sql1.
You need to configure the audit log destination. The solution must meet the following requirements:
Support querying events by using the Kusto query language.
Minimize administrative effort.
What should you configure?
- A . an event hub
- B . a storage account
- C . a Log Analytics workspace
C
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/reports-monitoring/tutorial-log-analytics-wizard
You have an Azure subscription that uses Microsoft Defender for Cloud.
You need to use Defender for Cloud to review regulatory compliance with the Azure CIS 1.4,0 standard. The solution must minimize administrative effort.
What should you do first?
- A . Assign an Azure policy.
- B . Manually add the Azure CIS 1.4.0 standard.
- C . Disable one of the Out of the box standards.
- D . Add a custom initiative.
You company has an Azure Active Directory (Azure AD) tenant named contoso.com.
You plan to create several security alerts by using Azure Monitor.
You need to prepare the Azure subscription for the alerts.
What should you create first?
- A . An Azure Storage account
- B . an Azure Log Analytics workspace
- C . an Azure event hub
- D . an Azure Automation account
B
Explanation:
https://docs.microsoft.com/en-us/azure/azure-monitor/learn/quick-create-workspace
You have an Azure subscription that contains the virtual machines shown in the following table.
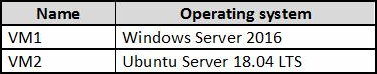
From Azure Security Center, you turn on Auto Provisioning.
You deploy the virtual machines shown in the following table.
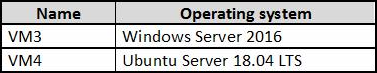
On which virtual machines is the Microsoft Monitoring agent installed?
- A . VM3 only
- B . VM1 and VM3 only
- C . VM3 and VM4 only
- D . VM1, VM2, VM3, and VM4
D
Explanation:
When automatic provisioning is enabled, Security Center provisions the Microsoft Monitoring Agent on all supported Azure VMs and any new ones that are created.
Supported Operating systems include: Ubuntu 14.04 LTS (x86/x64), 16.04 LTS (x86/x64), and 18.04 LTS (x64) and Windows Server 2008 R2, 2012, 2012 R2, 2016, version 1709 and 1803.
Reference: https://docs.microsoft.com/en-us/azure/security-center/security-center-faq
You have an Azure subscription that contains the resources shown in the following table.
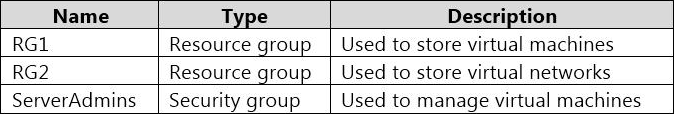
You need to ensure that ServerAdmins can perform the following tasks:
Create virtual machine to the existing virtual network in RG2 only.
The solution must use the principle of least privilege.
Which two role-based access control (RBAC) roles should you assign to ServerAdmins? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . the Contributor role for the subscription
- B . the Network Contributor role for RG2
- C . A custom RBAC role for the subscription
- D . a custom RBAC role for RG2
- E . the Network Contributor role for RG1.
- F . the Virtual Machine Contributor role for RG1.
You are configuring an Azure Kubernetes Service (AKS) cluster that will connect to an Azure Container
Registry.
You need to use the auto-generated service principal to authenticate to the Azure Container Registry.
What should you create?
- A . an Azure Active Directory (Azure AD) group
- B . an Azure Active Directory (Azure AD) role assignment
- C . an Azure Active Directory (Azure AD) user
- D . a secret in Azure Key Vault
B
Explanation:
When you create an AKS cluster, Azure also creates a service principal to support cluster operability with other Azure resources. You can use this auto-generated service principal for authentication with an ACR registry. To do so, you need to create an Azure AD role assignment that grants the cluster’s service principal access to the container registry.
Reference: https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-auth-aks
HOTSPOT
You network contains an on-premises Active Directory domain that syncs to an Azure Active Directory (Azure AD) tenant.
The tenant contains the users shown in the following table.
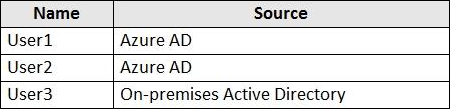
The tenant contains the groups shown in the following table.
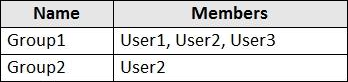
You configure a multi-factor authentication (MFA) registration policy that and the following settings:
• Assignments:
• Include: Group1
• Exclude Group2
• Controls: Require Azure MFA registration
• Enforce Policy: On
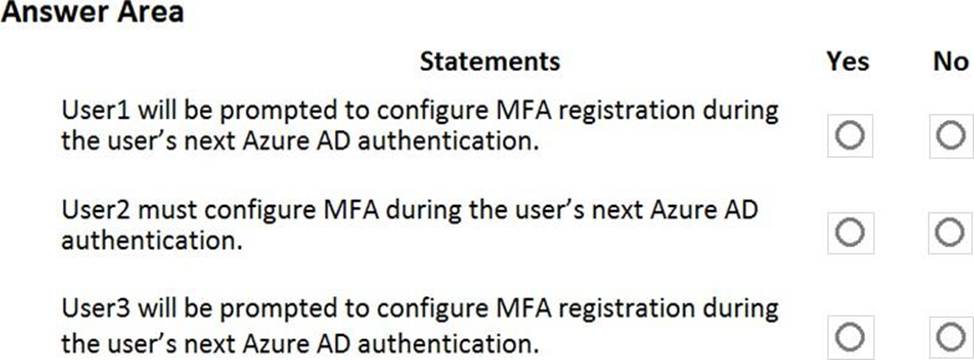
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
You have an Azure subscription.
You create a new virtual network named VNet1.
You plan to deploy an Azure web app named App1 that will use VNet1 and will be reachable by using private IP addresses. The solution must support inbound and outbound network traffic.
What should you do?
- A . Create an Azure App Service Hybrid Connection.
- B . Configure regional virtual network integration.
- C . Create an App Service Environment
- D . Create an Azure application gateway.
You have an Azure subscription that contains a virtual network named VNet1 VNet1 contains a single subnet. The subscription contains a virtual machine named VM1 that is connected to VNet1.
You plan to deploy an Azure SQL managed instance named SQL1.
You need to ensure that VM1 can access SQL1.
Which three components should you create? Each correct answer presents pan of the solution. NOTE: Each correct selection is worth one point.
- A . a virtual network gateway
- B . a network security group (NSG)
- C . a route table
- D . a subnet
- E . a network security perimeter
