Practice Free AZ-500 Exam Online Questions
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription named Sub1.
You have an Azure Storage account named sa1 in a resource group named RG1.
Users and applications access the blob service and the file service in sa1 by using several shared access signatures (SASs) and stored access policies.
You discover that unauthorized users accessed both the file service and the blob service.
You need to revoke all access to sa1.
Solution: You regenerate the Azure storage account access keys.
Does this meet the goal?
- A . Yes
- B . No
A
Explanation:
Generating new storage account keys will invalidate all SAS’s that were based on the previous keys.
You have an Azure subscription that contains a key vault and an Azure SQL server.
You need to deploy an Azure SQL database that uses Transparent Data Encryption (TDE) and a customer-managed key.
What should you create before you deploy the database?
- A . An app registration
- B . A standard general-purpose v2 storage account
- C . A user-assigned managed identity
- D . A user account that is assigned the SQL Security Manager role
HOTSPOT
You have an Azure subscription that contains the storage accounts shown in the following table.
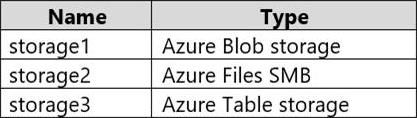
You need to configure authorization access.
Which authorization types can you use for each storage account? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
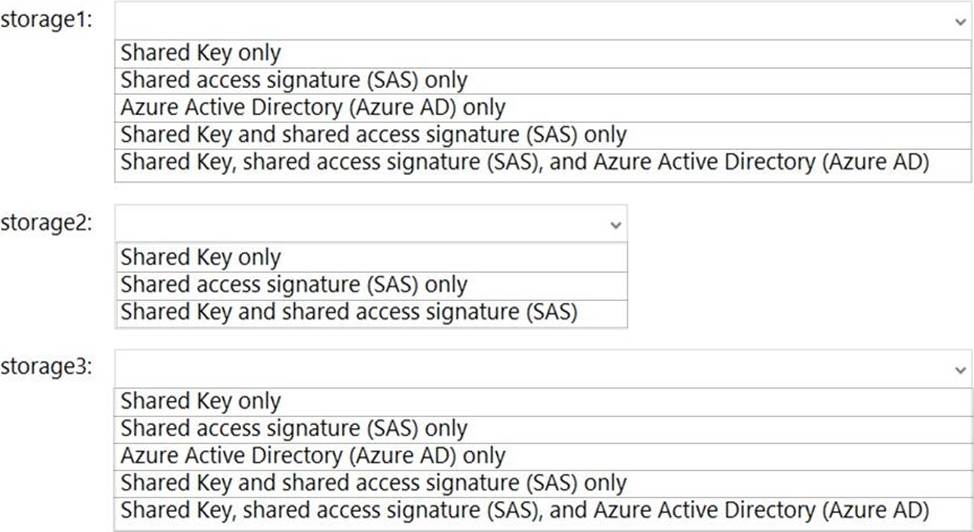
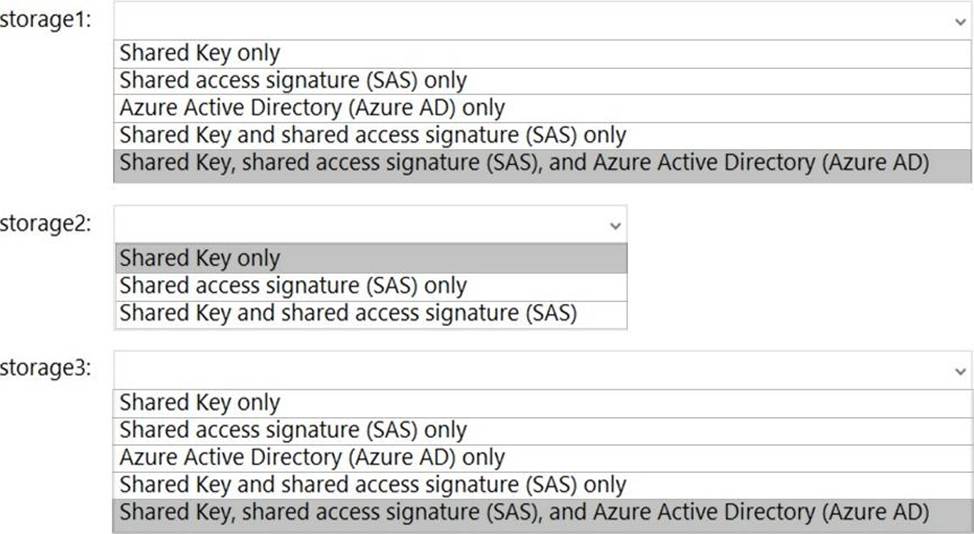
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/storage/common/authorize-data-access
HOTSPOT
You have an Azure Storage account that contains a blob container named container1 and a client application named App1.
You need to enable App1 access to container1 by using Azure Active Directory (Azure AD) authentication.
What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
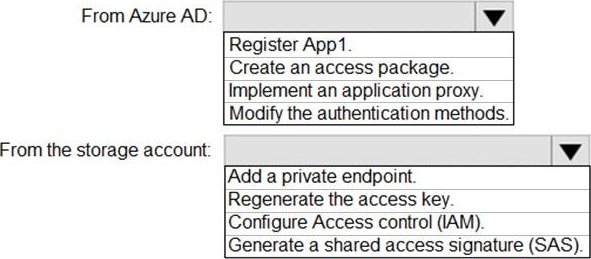
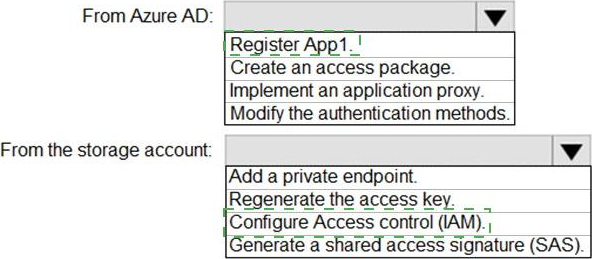
Explanation:
Reference:
https://azure.microsoft.com/en-in/blog/announcing-the-preview-of-aad-authentication-for-storage/
https://github.com/MicrosoftDocs/azure-docs/blob/master/articles/storage/common/storage-auth-aad-rbac-portal.md
DRAG DROP
You have an Azure subscription that contains the following resources:
✑ A network virtual appliance (NVA) that runs non-Microsoft firewall software and routes all outbound traffic from the virtual machines to the internet
✑ An Azure function that contains a script to manage the firewall rules of the NVA
✑ Azure Security Center standard tier enabled for all virtual machines
✑ An Azure Sentinel workspace
✑ 30 virtual machines
You need to ensure that when a high-priority alert is generated in Security Center for a virtual machine, an incident is created in Azure Sentinel and then a script is initiated to configure a firewall rule for the NVA.
How should you configure Azure Sentinel to meet the requirements? To answer, drag the appropriate components to the correct requirements. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.

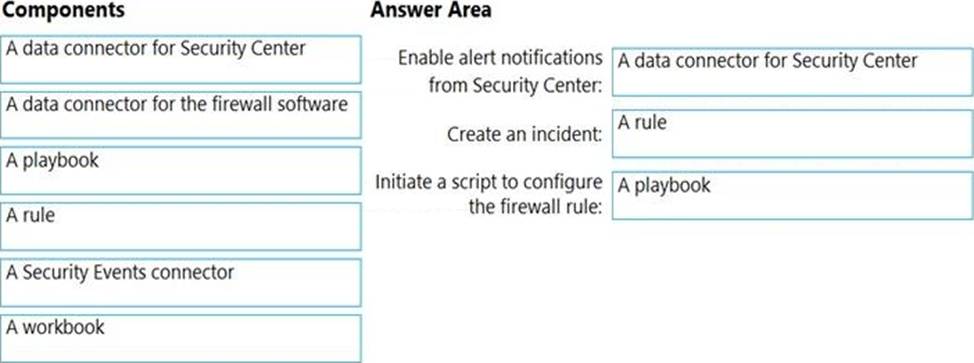
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/create-incidents-from-alerts
https://docs.microsoft.com/en-us/azure/sentinel/connect-azure-security-center
HOTSPOT
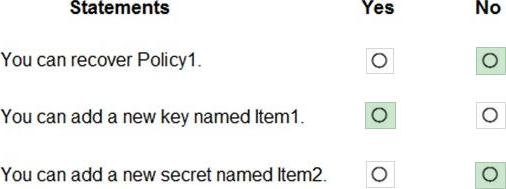
You have an Azure key vault named KeyVault1 that contains the items shown in the following table.
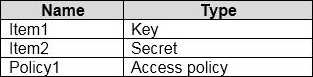
In KeyVault, the following events occur in sequence:
– Item1 is deleted
– Administrator enables soft delete
– Item2 and Policy1 are deleted.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
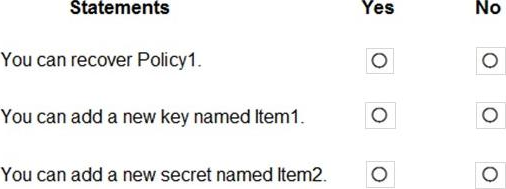
Explanation:
NO. Policies cannot be recovered
YES, Item1 is permanently deleted
NO, You cannot use the same name cause Item2 is in Seoft-deleted status https://docs.microsoft.com/en-us/azure/key-vault/general/soft-delete-overview
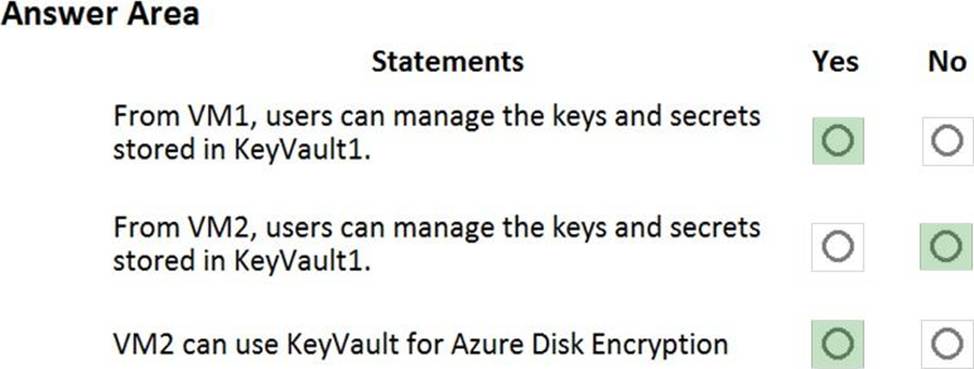
HOTSPOT
You have an Azure subscription that contains an Azure key vault named KeyVault1 and the virtual machines shown in the following table.
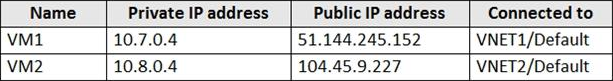
You set the Key Vault access policy to Enable access to Azure Disk Encryption for volume encryption.
KeyVault1 is configured as shown in the following exhibit.
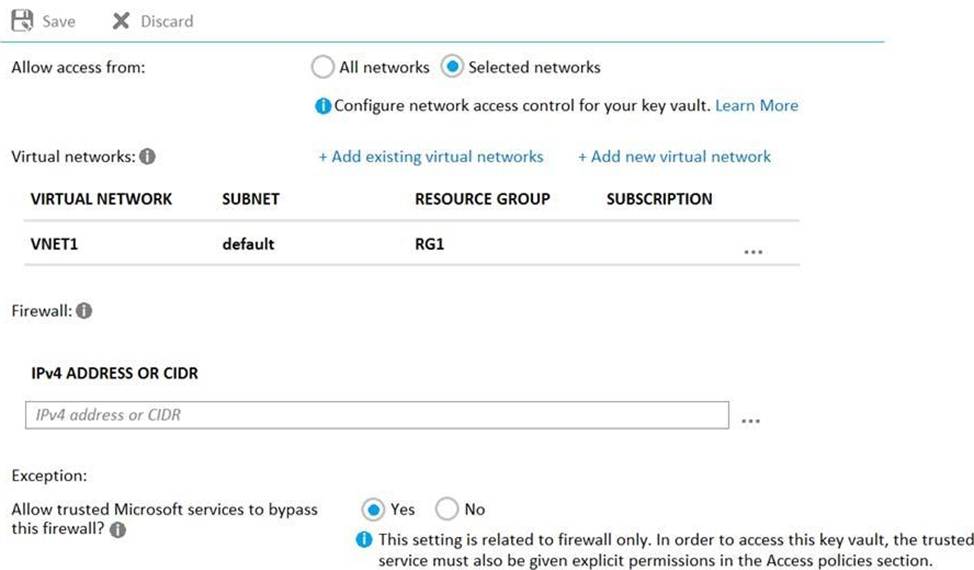
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
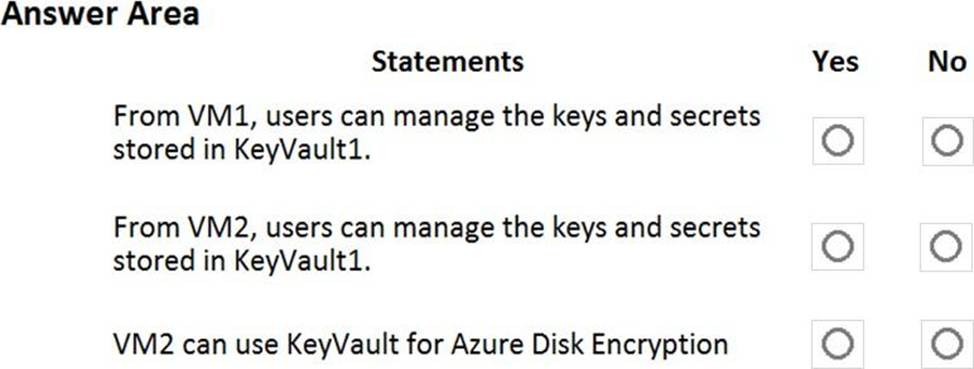
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your company has an Active Directory forest with a single domain, named weylandindustries.com.
They also have an Azure Active Directory (Azure AD) tenant with the same name.
You have been tasked with integrating Active Directory and the Azure AD tenant. You intend to deploy Azure AD Connect.
Your strategy for the integration must make sure that password policies and user logon limitations affect user accounts that are synced to the Azure AD tenant, and that the amount of necessary servers are reduced.
Solution: You recommend the use of password hash synchronization and seamless SSO.
Does the solution meet the goal?
- A . Yes
- B . No
You are securing access to the resources in an Azure subscription.
A new company policy states that all the Azure virtual machines in the subscription must use managed disks.
You need to prevent users from creating virtual machines that use unmanaged disks.
What should you use?
- A . Azure Monitor
- B . Azure Policy
- C . Azure Security Center
- D . Azure Service Health
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains an Azure Kubernetes Service (AKS) cluster named AKS1 and an Azure container registry named AZCR1.
You need to ensure that AKS1 can deploy container images stored in AZCR1.
Solution: You assign the AcrPush role-based access control (RBAC) role to the system-assigned managed identity of AKS1.
Does this meet the requirement?
- A . Yes
- B . No
