Practice Free AZ-500 Exam Online Questions
You have an Azure SQL Database server named SQL1.
You plan to turn on Advanced Threat Protection for SQL1 to detect all threat detection types.
Which action will Advanced Threat Protection detect as a threat?
- A . A user updates more than 50 percent of the records in a table.
- B . A user attempts to sign as SELECT * from table1.
- C . A user is added to the db_owner database role.
- D . A user deletes more than 100 records from the same table.
B
Explanation:
Advanced Threat Protection can detect potential SQL injections: This alert is triggered when an active exploit happens against an identified application vulnerability to SQL injection. This means the attacker is trying to inject malicious SQL statements using the vulnerable application code or stored procedures.
Reference: https://docs.microsoft.com/en-us/azure/sql-database/sql-database-threat-detection-overview
HOTSPOT
You need to deploy Microsoft Antimalware to meet the platform protection requirements.
What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
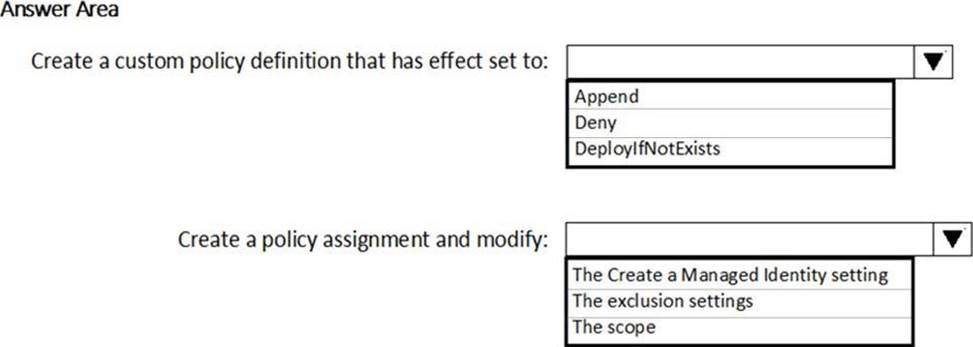
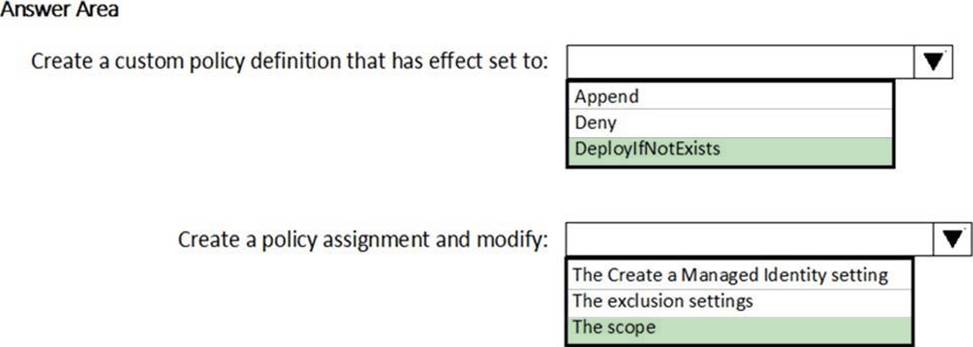
Explanation:
DRAG DROP
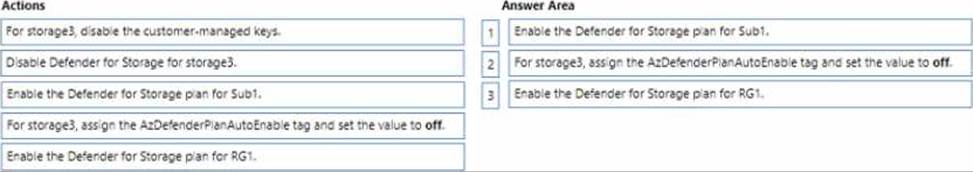
You have an Azure subscription named Sub1 that contains the storage accounts shown in the following table
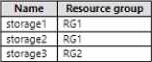
The storage3 storage account is encrypted by using customer-managed keys.
YOU need to enable Microsoft Defender for storage to meet the following requirements.
* The storage1 and storage2 account must be include in the defender for storage requirement.
* The storage3 account must be exclude from the Defender for Storage protections.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and them in the correct order.
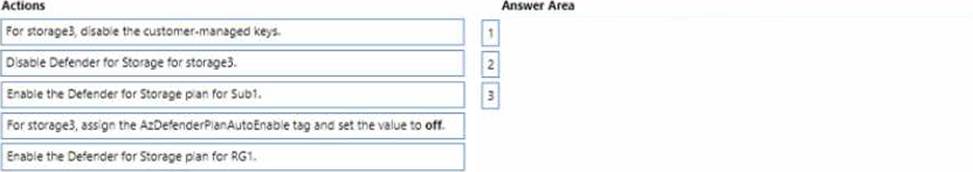
DRAG DROP
You are implementing conditional access policies.
You must evaluate the existing Azure Active Directory (Azure AD) risk events and risk levels to configure and implement the policies.
You need to identify the risk level of the following risk events:
Users with leaked credentials
Impossible travel to atypical locations
Sign ins from IP addresses with suspicious activity
Which level should you identify for each risk event? To answer, drag the appropriate levels to the correct risk events. Each level may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.


Explanation:
Medium
High
Medium
Refer https://docs.microsoft.com/en-us/azure/active-directory/reports-monitoring/concept-risk-events#sign-ins-from-ip-addresses-with-suspicious-activity
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain.
You have an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named contoso.com.
You plan to deploy Azure AD Connect and to integrate Active Directory and the Azure AD tenant.
You need to recommend an integration solution that meets the following requirements:
Ensures that password policies and user logon restrictions apply to user accounts that are synced to the Tenant Minimizes the number of servers required for the solution.
Which authentication method should you include in the recommendation?
- A . federated identity with Active Directory Federation Services (AD FS)
- B . password hash synchronization with seamless single sign-on (SSO)
- C . pass-through authentication with seamless single sign-on (SSO)
C
Explanation:
You have an Azure Active Directory (Azure AD) tenant and a root management group.
You create 10 Azure subscriptions and add the subscriptions to the rout management group.
You need to create an Azure Blueprints definition that will be stored in the root management group.
What should you do first?
- A . Add an Azure Policy definition to the root management group.
- B . Modify the role-based access control (RBAC) role assignments for the root management group.
- C . Create a user-assigned identity.
- D . Create a service principal.
B
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/role-based-access-control/elevate-access-global-admin
Your company recently created an Azure subscription.
You have been tasked with making sure that a specified user is able to implement Azure AD Privileged Identity Management (PIM).
Which of the following is the role you should assign to the user?
- A . The Global administrator role.
- B . The Security administrator role.
- C . The Password administrator role.
- D . The Compliance administrator role.
A
Explanation:
To start using PIM in your directory, you must first enable PIM.
Your company recently created an Azure subscription.
You have been tasked with making sure that a specified user is able to implement Azure AD Privileged Identity Management (PIM).
Which of the following is the role you should assign to the user?
- A . The Global administrator role.
- B . The Security administrator role.
- C . The Password administrator role.
- D . The Compliance administrator role.
A
Explanation:
To start using PIM in your directory, you must first enable PIM.
HOTSPOT
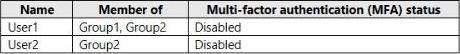
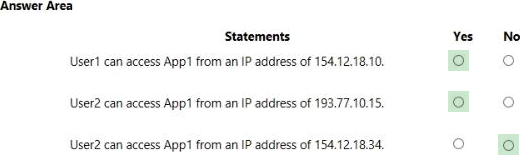
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.
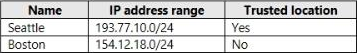
The tenant contains the named locations shown in the following table.
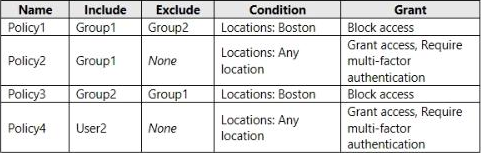
You create the conditional access policies for a cloud app named App1 as shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have an Azure subscription.
You need to deploy an Azure virtual WAN to meet the following requirements:
• Create three secured virtual hubs located in the East US, West US, and North Europe Azure regions.
• Ensure that security rules sync between the regions.
What should you use?
- A . Azure Firewall Manager
- B . Azure Virtual Network Manager
- C . Azure Network Function Manager
- D . Azure Front Door
