Practice Free AZ-500 Exam Online Questions
You have an Azure key vault named Vault1 that stores the resources shown in the following table.
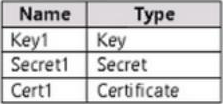
Which resources support the creation of a rotation policy?
- A . Key 1 only
- B . Cert1 only
- C . Key1 and Secret1 only
- D . Key1 and Cert1 only
- E . Secret1 and Cert1 only
- F . Key1, Secret1, and Cert1
You have a Microsoft 365 tenant that uses an Azure Active Directory (Azure AD) tenant The Azure AD tenant syncs to an on-premises Active Directory domain by using an instance of Azure AD Connect.
You create a new Azure subscription
You discover that the synced on-premises user accounts cannot be assigned rotes in the new subscription.
You need to ensure that you can assign Azure and Microsoft 365 roles to the synced Azure AD user accounts.
What should you do first?
- A . Change the Azure AD tenant used by the new subscription.
- B . Configure the Azure AD tenant used by the new subscription to use pass-through authenticate
- C . Configure the Azure AD tenant used by the new subscription to use federated authentication.
- D . Configure a second instance of Azure AD Connect.
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant that contains the resources shown in the following table.
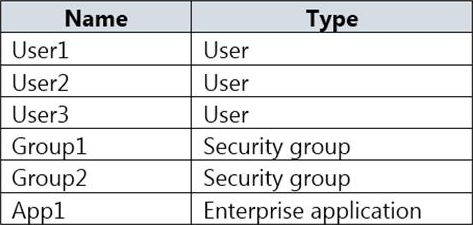
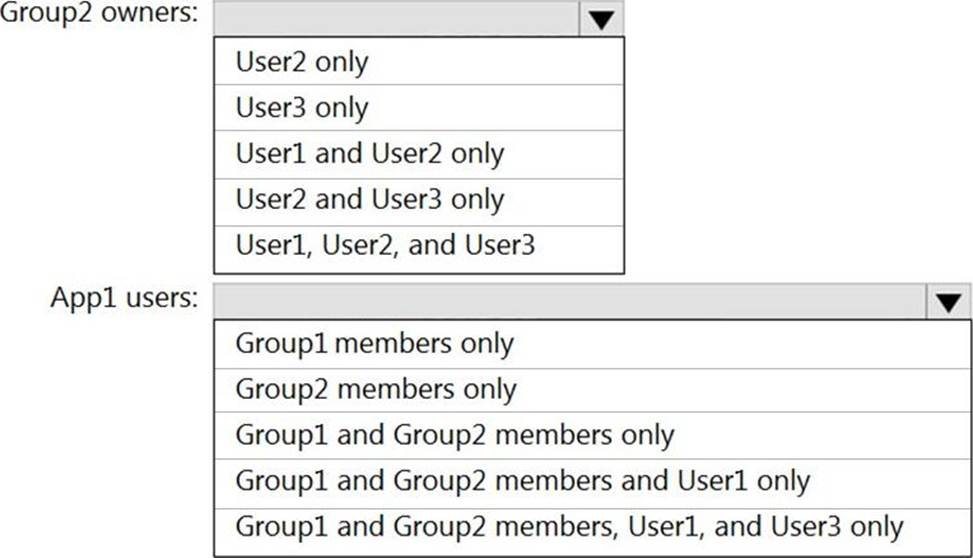
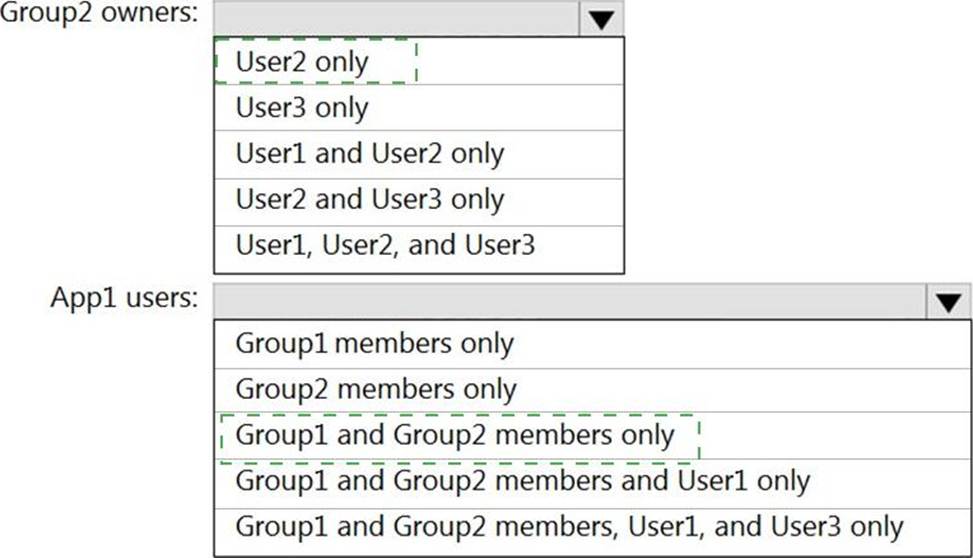
User2 is the owner of Group2.
The user and group settings for App1 are configured as shown in the following exhibit.
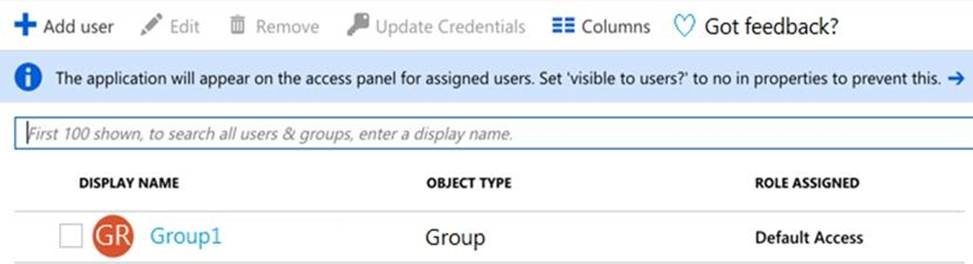
You enable self-service application access for App1 as shown in the following exhibit.
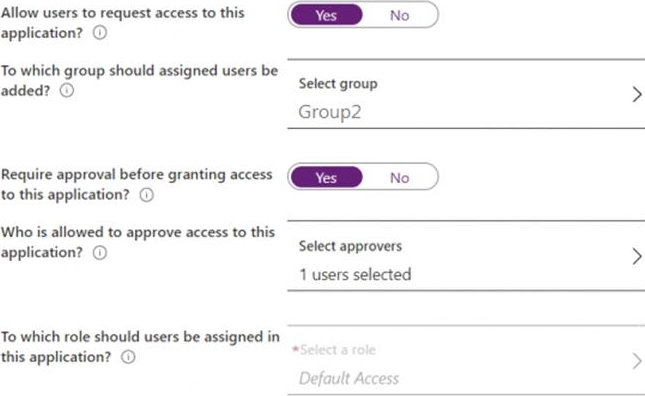
User3 is configured to approve access to Appl.
You need to identify the owners of Group2 and the users of Appl.
What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/manage-self-service-access
HOTSPOT
You have an Azure subscription that contains the resources shown in the following table.
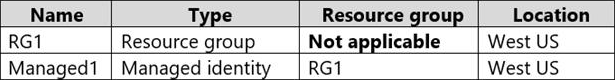
The subscription is linked to an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.

You create the groups shown in the following table.
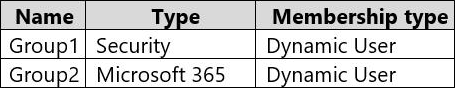
The membership rules for Group1 and Group2 are configured as shown in the following exhibit.
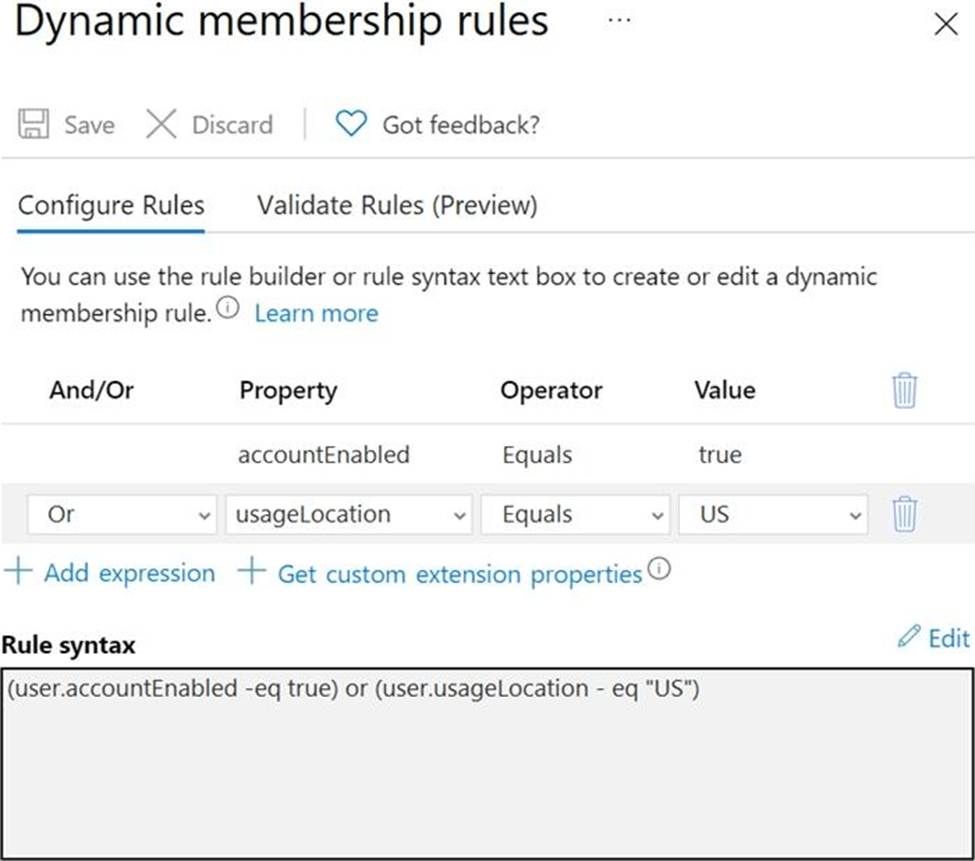
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/enterprise-users/groups-dynamic-membership
You create a new Azure subscription.
You need to ensure that you can create custom alert rules in Azure Security Center.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Onboard Azure Active Directory (Azure AD) Identity Protection.
- B . Create an Azure Storage account.
- C . Implement Azure Advisor recommendations.
- D . Create an Azure Log Analytics workspace.
- E . Upgrade the pricing tier of Security Center to Standard.
DE
Explanation:
D: You need write permission in the workspace that you select to store your custom alert.
Reference: https://docs.microsoft.com/en-us/azure/security-center/security-center-custom-alert
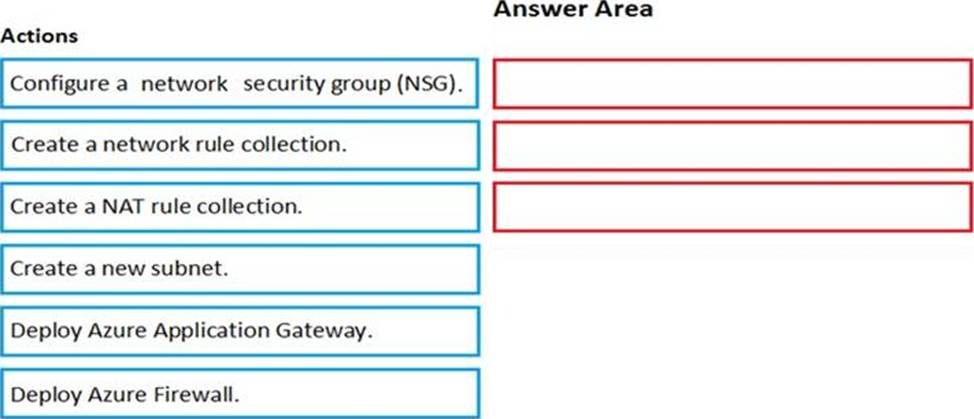
DRAG DROP
You have an Azure subscription that contains the following resources:
A virtual network named VNET1 that contains two subnets named Subnet1 and Subnet2.
A virtual machine named VM1 that has only a private IP address and connects to Subnet1.
You need to ensure that Remote Desktop connections can be established to VM1 from the internet.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange then in the correct order.
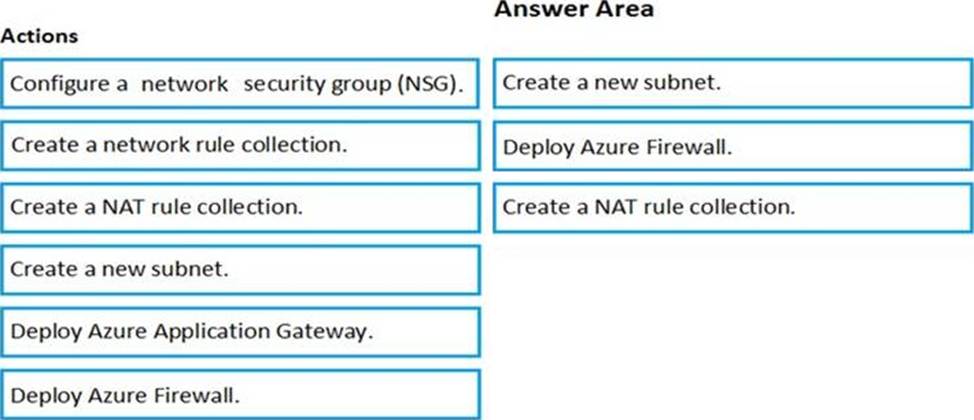
You have an Azure subscription that contains an Azure key vault named Vault1 and a virtual machine named VM1.
VM1 is connected to a virtual network named VNet1.
You need to allow access to Vault1 only from VM1.
What should you do in the Networking settings of Vault1?
- A . From the Firewalls and virtual networks tab, set Allow trusted Microsoft services to bypass this firewall to Yes for Vault1.
- B . From the Firewalls and virtual networks tab, add the IP address of VM1.
- C . From the Firewalls and virtual networks tab, add VNet1.
- D . From the Private endpoint connections tab, create a private endpoint for VM1.
HOTSPOT
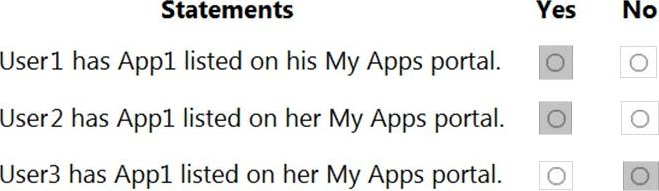
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains three security groups named Group1, Group2, and Group3 and the users shown in the following table.
Group3 is a member of Group2.
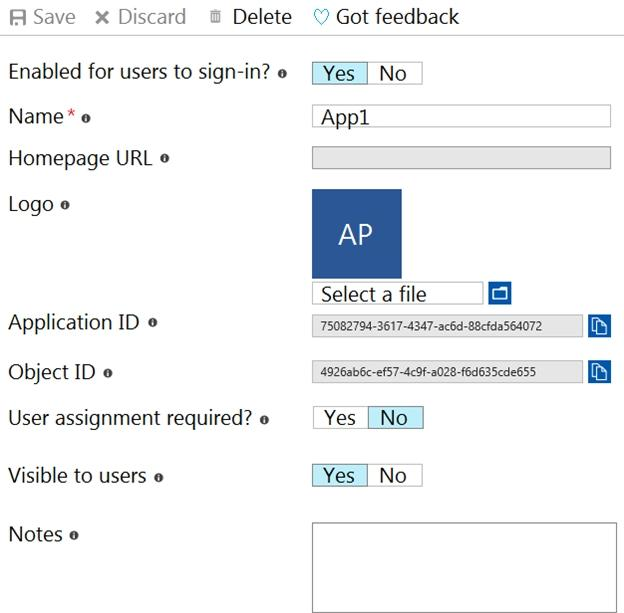
In contoso.com, you register an enterprise application named App1 that has the following settings:
✑ Owners: User1
✑ Users and groups: Group2
You configure the properties of App1 as shown in the following exhibit.
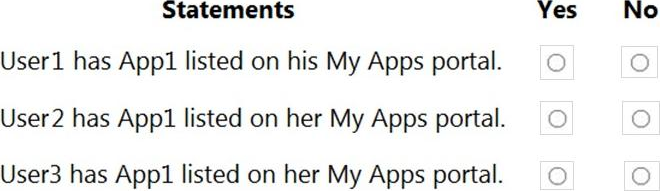
For each of the following statements, select Yes if the statement is true. Otherwise, select no. NOTE: Each correct selection is worth one point.
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/assign-user-or-group-access-portal
You have an Azure subscription named Sub1 that contains the virtual machines shown in the following table.
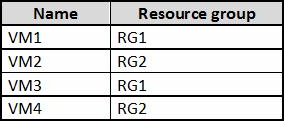
You need to ensure that the virtual machines in RG1 have the Remote Desktop port closed until an authorized user requests access.
What should you configure?
- A . Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
- B . an application security group
- C . Azure Active Directory (Azure AD) conditional access
- D . just in time (JIT) VM access
D
Explanation:
Just-in-time (JIT) virtual machine (VM) access can be used to lock down inbound traffic to your Azure VMs, reducing exposure to attacks while providing easy access to connect to VMs when needed.
Note: When just-in-time is enabled, Security Center locks down inbound traffic to your Azure VMs by creating an NSG rule. You select the ports on the VM to which inbound traffic will be locked down. These ports are controlled by the just-in-time solution.
When a user requests access to a VM, Security Center checks that the user has Role-Based Access Control (RBAC) permissions that permit them to successfully request access to a VM. If the request is approved, Security Center automatically configures the Network Security Groups (NSGs) and Azure Firewall to allow inbound traffic to the selected ports and requested source IP addresses or ranges, for the amount of time that was specified. After the time has expired, Security Center restores the NSGs to their previous states. Those connections that are already established are not being interrupted, however.
Reference: https://docs.microsoft.com/en-us/azure/security-center/security-center-just-in-time
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.
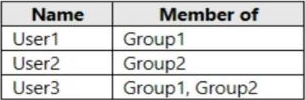
From Azure AD Privileged Identity Management (PIM), you configure the settings for the Security Administrator role as shown in the following exhibit.
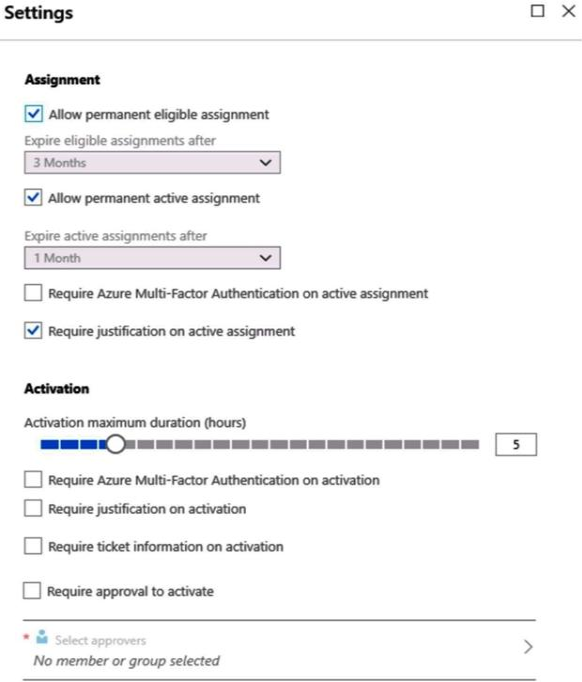
From PIM, you assign the Security Administrator role to the following groups:
– Group1: Active assignment type, permanently assigned
– Group2: Eligible assignment type, permanently eligible
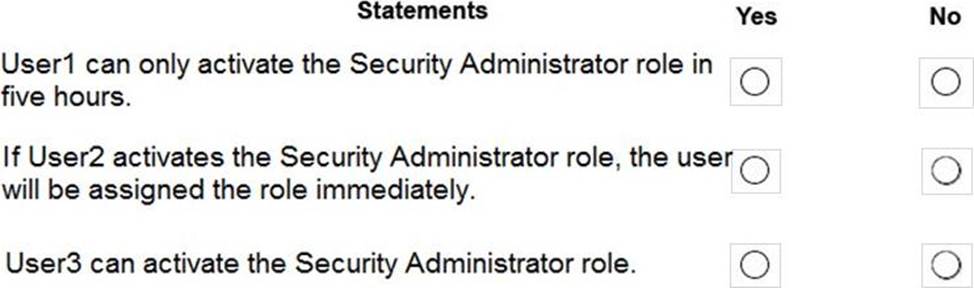
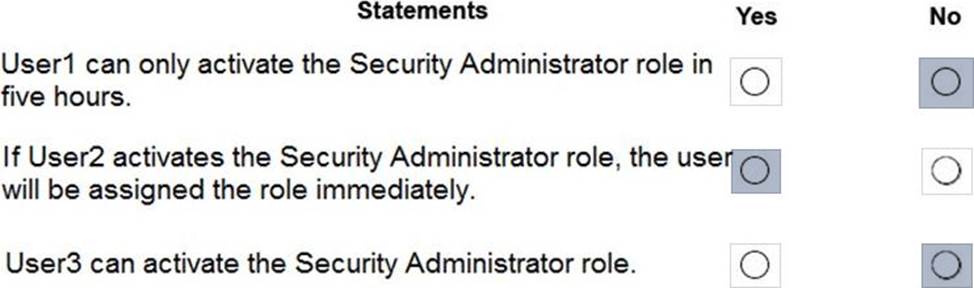
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
Box 1: Yes
Eligible Type: A role assignment that requires a user to perform one or more actions to use the role. If a user has been made eligible for a role, that means they can activate the role when they need to perform privileged tasks. There’s no difference in the access given to someone with a permanent versus an eligible role assignment. The only difference is that some people don’t need that access all the time.
You can choose from two assignment duration options for each assignment type (eligible and active) when you configure settings for a role. These options become the default maximum duration when a user is assigned to the role in Privileged Identity Management.
Use the Activation maximum duration slider to set the maximum time, in hours, that a role stays active before it expires. This value can be from one to 24 hours.
Box 2: Yes
Active Type: A role assignment that doesn’t require a user to perform any action to use the role. Users assigned as active have the privileges assigned to the role
Box 3: Yes
User3 is member of Group2.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
https://docs.microsoft.com/bs-cyrl-ba/azure/active-directory/privileged-identity-management/pim-resource-roles-configure-role-settings
