Practice Free AZ-500 Exam Online Questions
You have an Azure subscription that contains an Azure SQL Database logic server named SQL! and an Azure virtual machine named VM1. VM1 uses a private IP address only.
The Firewall and virtual networks settings for SQL1 are shown in the following exhibit.
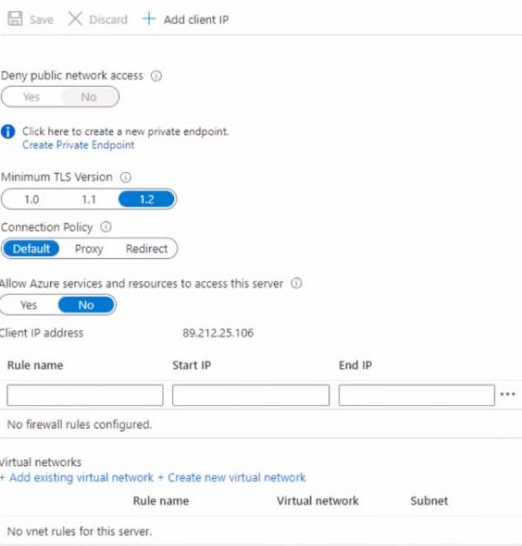
You need to ensure that VM1 can connect to SQL1. The solution must use the principle of least privilege.
What should you do?
- A . Add an existing virtual network.
- B . Set Connection Policy to Proxy.
- C . Create a new firewall rule.
- D . Set Allow Azure services and resources to access this server to Yes.
You have an Azure subscription that contains an Azure SQL Database logic server named SQL! and an Azure virtual machine named VM1. VM1 uses a private IP address only.
The Firewall and virtual networks settings for SQL1 are shown in the following exhibit.

You need to ensure that VM1 can connect to SQL1. The solution must use the principle of least privilege.
What should you do?
- A . Add an existing virtual network.
- B . Set Connection Policy to Proxy.
- C . Create a new firewall rule.
- D . Set Allow Azure services and resources to access this server to Yes.
Which Azure service provides threat protection for virtual machines, SQL databases, and Azure Storage?
- A . Azure Security Center
- B . Azure Monitor
- C . Azure Defender
- D . Azure Sentinel
You have an Azure Kubernetes Service (AKS) cluster that will connect to an Azure Container Registry.
You need to use automatically generated service principal for the AKS cluster to authenticate to the Azure Container Registry.
What should you create?
- A . a secret in Azure Key Vault
- B . a role assignment
- C . an Azure Active Directory (Azure AD) user
- D . an Azure Active Directory (Azure AD) group
B
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/aks/kubernetes-service-principal
HOTSPOT
Your network contains an on-premises Active Directory domain named adatum.com that syncs to Azure Active Directory (Azure AD).
The Azure AD tenant contains the users shown in the following table.
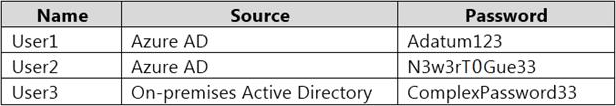
You configure the Authentication methods C Password Protection settings for adatum.com as shown in the following exhibit.
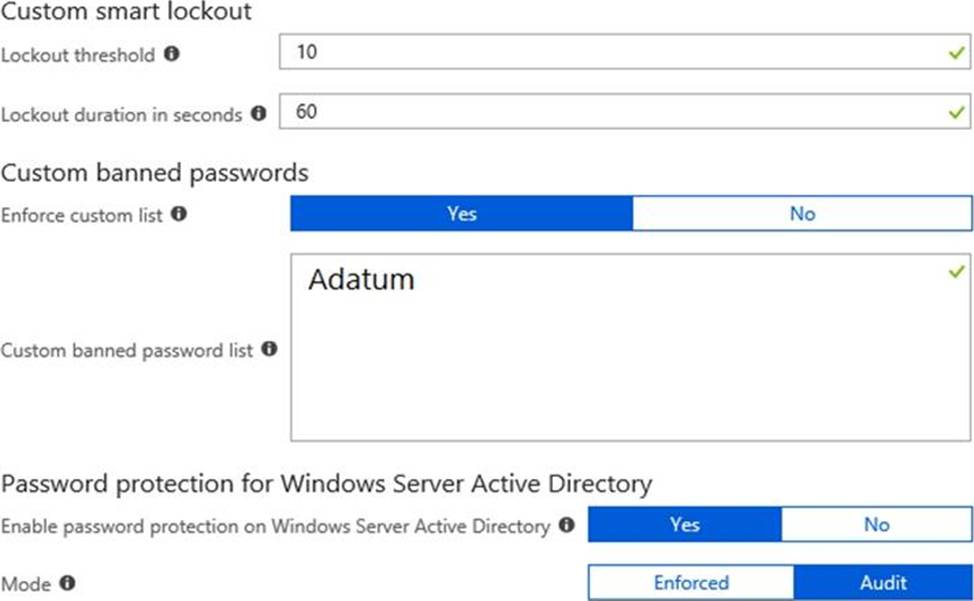
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
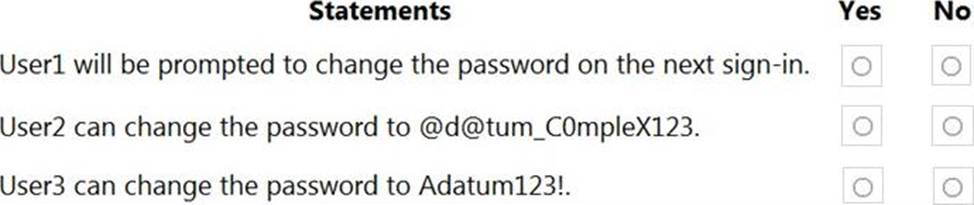
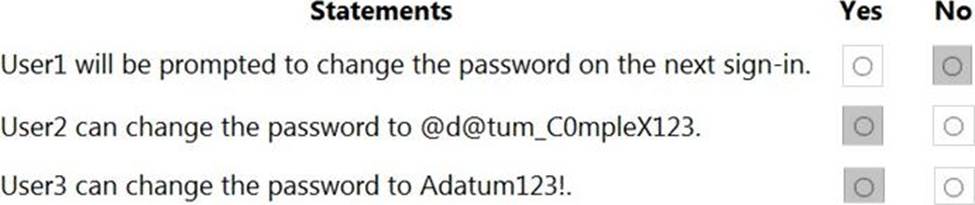
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-password-ban-bad-on-premises-deploy
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-password-ban-bad
DRAG DROP
You have an Azure subscription that contains the virtual networks shown in the following table.
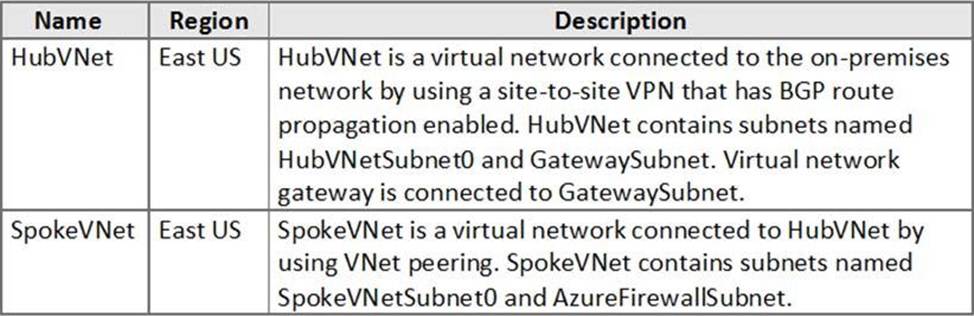
The Azure virtual machines on SpokeVNetSubnet0 can communicate with the computers on the on-premises network.
You plan to deploy an Azure firewall to HubVNet.
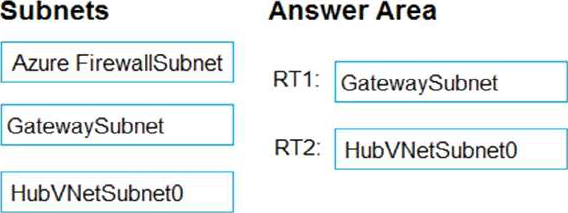
You create the following two routing tables:
✑ RT1: Includes a user-defined route that points to the private IP address of the Azure firewall as a next hop address
✑ RT2: Disables BGP route propagation and defines the private IP address of the Azure firewall as the default gateway
You need to ensure that traffic between SpokeVNetSubnet0 and the on-premises network flows through the Azure firewall.
To which subnet should you associate each route table? To answer, drag the appropriate subnets to the correct route tables. Each subnet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You are configuring and securing a network environment.
You deploy an Azure virtual machine named VM1 that is configured to analyze network traffic.
You need to ensure that all network traffic is routed through VM1.
What should you configure?
- A . a system route
- B . a network security group (NSG)
- C . a user-defined route
C
Explanation:
Although the use of system routes facilitates traffic automatically for your deployment, there are cases in which you want to control the routing of packets through a virtual appliance. You can do so by creating user defined routes that specify the next hop for packets flowing to a specific subnet to go to your virtual appliance instead, and enabling IP forwarding for the VM running as the virtual appliance.
Note: User Defined Routes
For most environments you will only need the system routes already defined by Azure. However, you may need to create a route table and add one or more routes in specific cases, such as:
Force tunneling to the Internet via your on-premises network.
Use of virtual appliances in your Azure environment.
In the scenarios above, you will have to create a route table and add user defined routes to it.
Reference: https://github.com/uglide/azure-content/blob/master/articles/virtual-network/virtual-networks-udr-overview.md
You have an Azure subscription that contains an Azure SQL server named SQL1. SQL1 contains. You need to use Microsoft Defender for Cloud to complete a vulnerability assessment for DB1.
What should you do first?
- A . From Advanced Threat Protection types, select SQL injection vulnerability.
- B . Configure the Send scan report to setting.
- C . Set Periodic recurring scans to ON.
- D . Enable the Microsoft Defender for SQL plan.
DRAG DROP
You have an Azure subscription named Sub1.
You have an Azure Active Directory (Azure AD) group named Group1 that contains all the members of
your IT team.
You need to ensure that the members of Group1 can stop, start, and restart the Azure virtual machines in Sub1. The solution must use the principle of least privilege.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
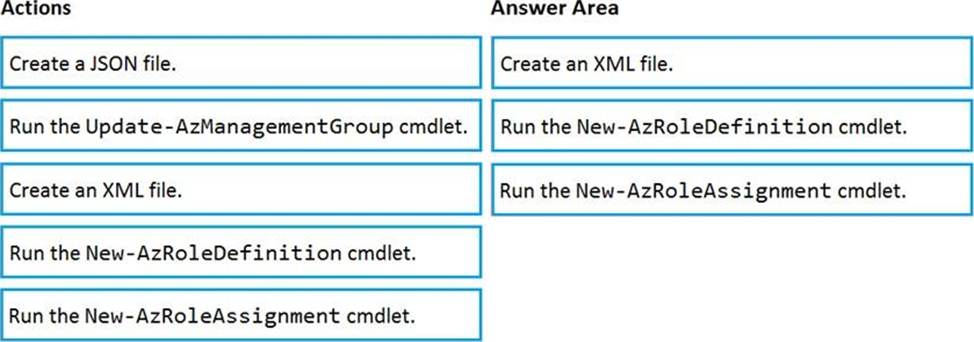
Explanation:
Reference: https://www.petri.com/cloud-security-create-custom-rbac-role-microsoft-azure
DRAG DROP
You have an Azure subscription named Sub1.
You have an Azure Active Directory (Azure AD) group named Group1 that contains all the members of
your IT team.
You need to ensure that the members of Group1 can stop, start, and restart the Azure virtual machines in Sub1. The solution must use the principle of least privilege.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.


Explanation:
Reference: https://www.petri.com/cloud-security-create-custom-rbac-role-microsoft-azure
