Practice Free AZ-500 Exam Online Questions
You need to meet the technical requirements for the finance department users.
Which CAPolicy1 settings should you modify?
- A . Cloud apps or actions
- B . Conditions
- C . Grant
- D . Session
D
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-session-lifetime
HOTSPOT
You have an Azure subscription that contains the custom roles shown in the following table.
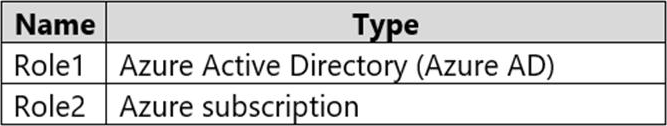
In the Azure portal, you plan to create new custom roles by cloning existing roles.
The new roles will be configured as shown in the following table.

Which roles can you clone to create each new role? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
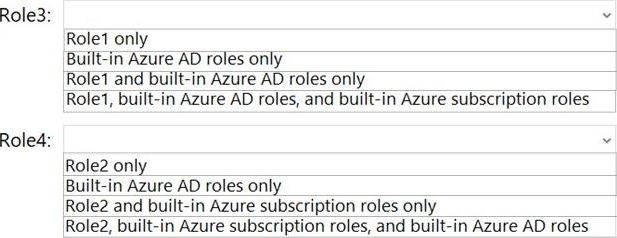
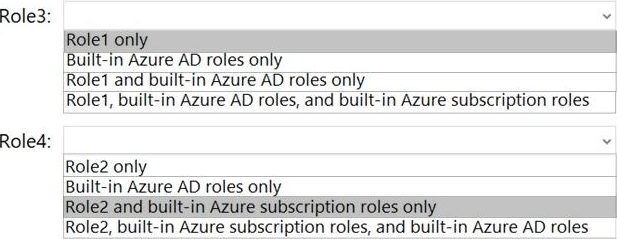
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/roles/custom-create
https://docs.microsoft.com/en-us/azure/role-based-access-control/custom-roles-portal
HOTSPOT
You have an Azure subscription that contains the virtual networks shown in the following table.

NSG1 and NSG2 both have default rules only.
The subscription contains the virtual machines shown in the following table.
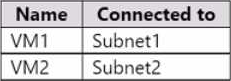
The subscription contains the web apps shown in the following table.
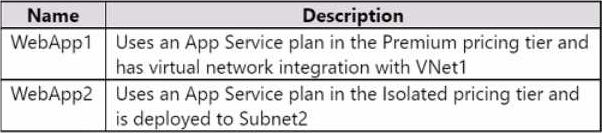
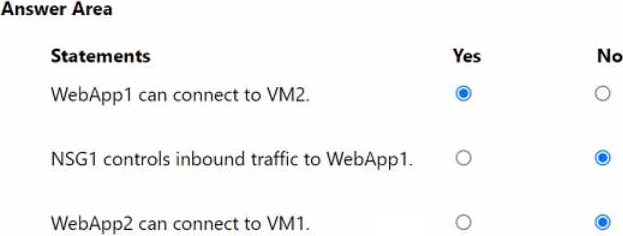
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
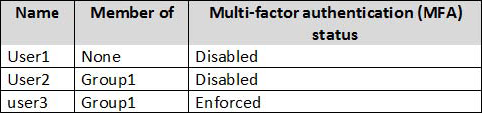
Azure AD Privileged Identity Management (PIM) is enabled for the tenant.
In PIM, the Password Administrator role has the following settings:
✑ Maximum activation duration (hours): 2
✑ Send email notifying admins of activation: Disable
✑ Require incident/request ticket number during activation: Disable
✑ Require Azure Multi-Factor Authentication for activation: Enable
✑ Require approval to activate this role: Enable
✑ Selected approver: Group1
You assign users the Password Administrator role as shown in the following table.
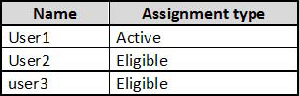
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
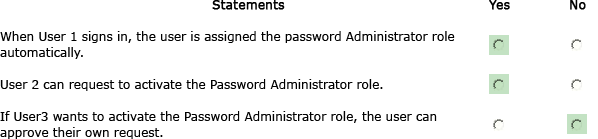
Explanation:
YES (Already active)
YES (The user will be prompted for MFA regardless the MFA Status of the user)
NO (Even the user is included in the group, a user can’t approve itself)
https://docs.microsoft.com/es-es/azure/active-directory/privileged-identity-management/pim-deployment-plan (Require approval section)
HOTSPOT
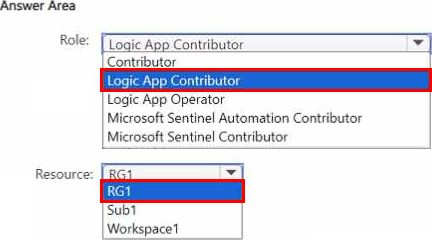
You have an Azure subscription named Sub1 and use Microsoft Defender for Cloud. Sub1 contains a user named User1 and a resource group named RG1. RG1 contains a Log Analytics workspace named Workspace1.
You need to ensure that User1 can modify Azure Logic Apps workflows triggered in response to security incidents. The solution must follow the principle of least privilege.
Which role should you assign to User1. and to which resource should you assign the role? To answer, select the appropriate options in the answer area. NOTE; Each correct selection is worth one point.
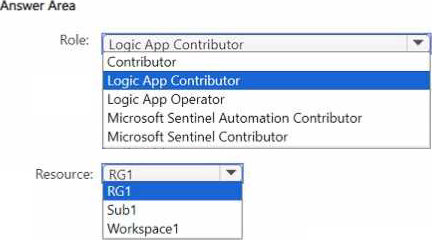
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to rt As a result, these questions will not appear in the review screen.
You have an Azure subscription named Sub1.
You have an Azure Storage account named Sa1 in a resource group named RG1.
Users and applications access the blob service and the file service in Sal by using several shared access signatures {SASs) and stored access policies.
You discover that unauthorized users accessed both the rile service and the blob service.
You need to revoke all access to Sa1.
Solution: You regenerate the access keys.
Does this meet the goal?
- A . Yes
- B . No
A
Explanation:
To revoke a stored access policy, you can either delete it, or rename it by changing the signed identifier. Changing the signed identifier breaks the associations between any existing signatures and the stored access policy. Deleting or renaming the stored access policy immediately effects all of the shared access signatures associated with it.
Reference: https://docs.microsoft.com/en-us/rest/api/storageservices/Establishing-a-Stored-Access-Policy
HOTSPOT
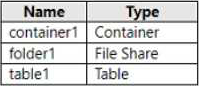
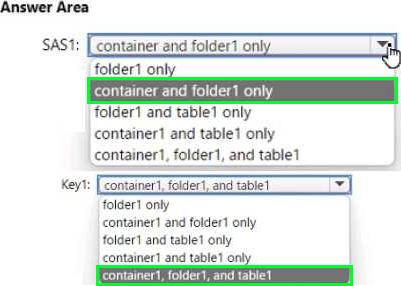
You have an Azure subscription that contains a user named User1 and a storage account named storage1.
The storage1 account contains the resources shown in the following table.
In storage1, you create a shared access signature (SAS) named SAS1 as shown in the following exhibit.
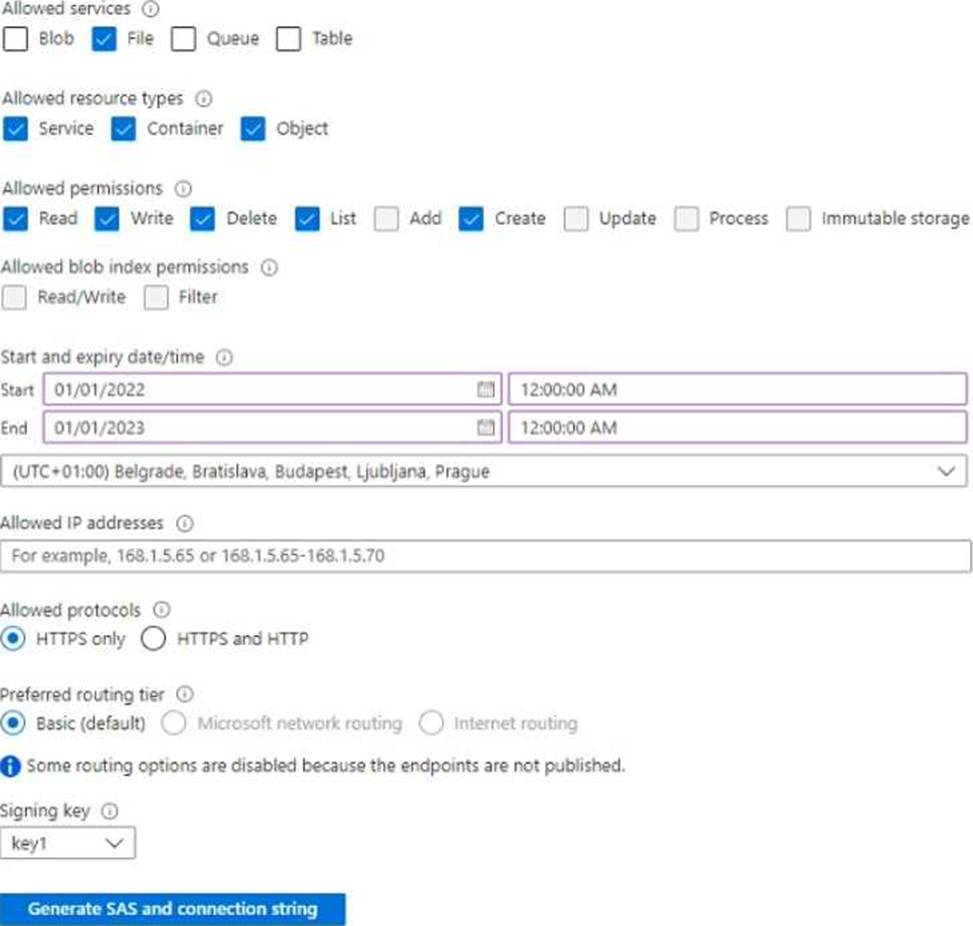
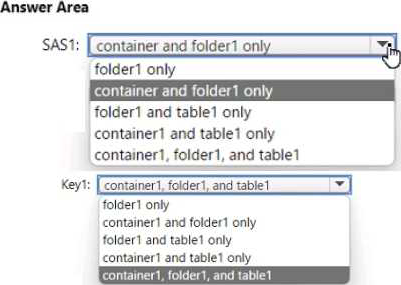
To which resources can User! write on July 1, 2022 by using SAS1 and key 1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains an Azure SQL server named sqlsrv1 and an Azure SQL database named DB1. Sqlsrv1 is configured for Microsoft Entra authentication only.
You have the Microsoft Entra identities shown in the following table.
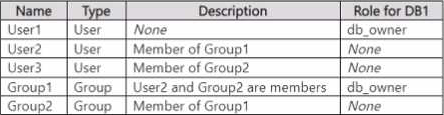
Which users can create scoped credentials for DB1?
- A . User1 only
- B . User1 and User2 only
- C . User1, User2, and User3
HOTSPOT
You have an Azure subscription that contains an Azure Sentinel workspace.
Azure Sentinel is configured to ingest logs from several Azure workloads. A third-party service management platform is used to manage incidents.
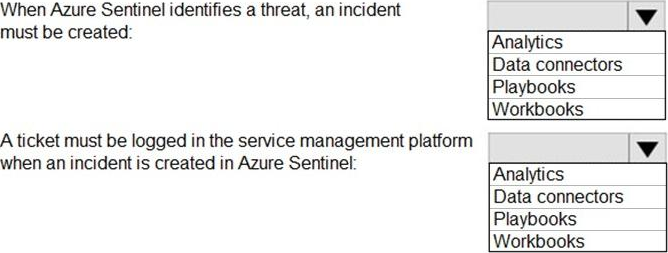
You need to identify which Azure Sentinel components to configure to meet the following requirements:
When Azure Sentinel identifies a threat, an incident must be created.
A ticket must be logged in the service management platform when an incident is created in Azure Sentinel.
Which component should you identify for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
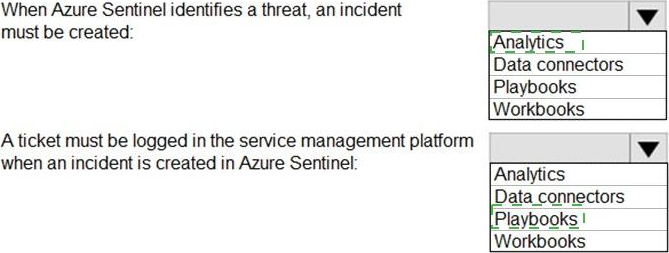
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/create-incidents-from-alerts
https://docs.microsoft.com/en-us/azure/sentinel/tutorial-respond-threats-playbook
You have an Azure subscription that contains a virtual network named VNet1. The subscription contains an Azure App Service web app named App1.
You have an Azure Front Door profile named AFD1 that has an Azure Web Application Firewall (WAF) policy.
You need to ensure that all inbound traffic to App1 is filtered through AFD1.
What should you do?
- A . For VNet1, configure network security group (NSG) rules.
- B . For App1, configure the HTTP headers filter settings.
- C . For App1, enable virtual network integration.
- D . Configure Microsoft Entra application proxy.
