Practice Free HPE7-A02 Exam Online Questions
You want to examine the applications that a device is using and look for any changes in application usage over several different ranges.
In which HPE Aruba Networking solution can you view this information in an easy-to-view format?
- A . HPE Aruba Networking ClearPass OnGuard agent installed on the device
- B . HPE Aruba Networking Central within a device’s Live Monitoring page
- C . HPE Aruba Networking ClearPass Insight using an Active Endpoint Security report
- D . HPE Aruba Networking ClearPass Device Insight (CPDI) in the device’s network activity
B
Explanation:
HPE Aruba Central Live Monitoring:
Aruba Central provides real-time Live Monitoring of network devices, including:
Application usage statistics.
Trends and changes over time for specific devices.
This information is presented in a clear and easy-to-read format, making it ideal for examining changes in application usage over different time ranges.
Option Analysis:
Option A: Incorrect. ClearPass OnGuard monitors endpoint compliance (e.g., antivirus, OS version) but does not analyze application usage.
Option B: Correct. Aruba Central’s Live Monitoring page is specifically designed for this type of analysis.
Option C: Incorrect. ClearPass Insight generates endpoint security reports but does not track application usage.
Option D: Incorrect. ClearPass Device Insight (CPDI) focuses on device profiling and identification, not continuous application monitoring.
You have created this rule in an HPE Aruba Networking ClearPass Policy Manager (CPPM) service’s enforcement policy:
IF Authorization [Endpoints Repository] Conflict EQUALS true THEN apply "quarantine_profile"
What information can help you determine whether you need to configure cluster-wide profiler parameters to ignore some conflicts?
- A . Whether some devices are running legacy operating systems
- B . Whether the company has rare Internet of Things (IoT) devices
- C . Whether some devices are incapable of captive portal or 802.1X authentication
- D . Whether the company has devices that use PXE boot
D
Explanation:
A conflict in the Endpoints Repository usually indicates that ClearPass has seen different profiling data for the same MAC, which might mean a spoofing attempt―or simply normal behavior for certain device types.
Devices that use PXE boot often:
Boot initially from the network with one set of characteristics (e.g., a minimal OS, different DHCP fingerprint),
Then chain-load into a different OS with a different fingerprint and sometimes even a different network profile.
Aruba exam and design material specifically point out PXE boot as a common, benign cause of profiler conflicts and recommend tuning cluster-wide profiler parameters to ignore or relax some conflicts for these devices.
Therefore, you look at whether the company has devices that use PXE boot when deciding whether to tune profiler conflict behavior → Option D.
You have created this rule in an HPE Aruba Networking ClearPass Policy Manager (CPPM) service’s enforcement policy:
IF Authorization [Endpoints Repository] Conflict EQUALS true THEN apply "quarantine_profile"
What information can help you determine whether you need to configure cluster-wide profiler parameters to ignore some conflicts?
- A . Whether some devices are running legacy operating systems
- B . Whether the company has rare Internet of Things (IoT) devices
- C . Whether some devices are incapable of captive portal or 802.1X authentication
- D . Whether the company has devices that use PXE boot
D
Explanation:
A conflict in the Endpoints Repository usually indicates that ClearPass has seen different profiling data for the same MAC, which might mean a spoofing attempt―or simply normal behavior for certain device types.
Devices that use PXE boot often:
Boot initially from the network with one set of characteristics (e.g., a minimal OS, different DHCP fingerprint),
Then chain-load into a different OS with a different fingerprint and sometimes even a different network profile.
Aruba exam and design material specifically point out PXE boot as a common, benign cause of profiler conflicts and recommend tuning cluster-wide profiler parameters to ignore or relax some conflicts for these devices.
Therefore, you look at whether the company has devices that use PXE boot when deciding whether to tune profiler conflict behavior → Option D.
A port-access role for AOS-CX switches has this policy applied to it: plaintext
Copy code
port-access policy mypolicy 10 class ip zoneC action drop 20 class ip zoneA action drop
100 class ip zoneB
The classes have this configuration:
plaintext
Copy code
class ip zoneC
10 match tcp 10.2.0.0/16 eq https
class ip zoneA
10 match ip any 10.1.0.0/16
class ip zoneB
10 match ip any 10.0.0.0/8
The company wants to permit clients in this role to access 10.2.12.0/24 with HTTPS.
What should you do?
- A . Add this rule to zoneC: 5 match any 10.2.12.0/24 eq https
- B . Add this rule to zoneA: 5 ignore tcp any 10.2.12.0/24 eq https
- C . Add this rule to zoneB: 5 match tcp any 10.2.12.0/24 eq https
- D . Add this rule to zoneC: 5 ignore tcp any 10.2.12.0/24 eq https
A
Explanation:
Comprehensive Detailed Explanation
The requirement is to permit HTTPS traffic from clients to the 10.2.12.0/24 subnet.
Zone C is configured to drop all HTTPS traffic to the 10.2.0.0/16 subnet. Therefore, the first match in the zone C class (priority 10) will drop the desired traffic.
To override this behavior, you must add a higher-priority rule (lower rule number) to zone C that explicitly matches 10.2.12.0/24 and permits the traffic.
Thus, adding the rule 5 match any 10.2.12.0/24 eq https to zone C ensures the desired traffic is permitted while maintaining the drop behavior for the rest of 10.2.0.0/16.
Reference
AOS-CX Role-Based Access Control documentation.
Understanding class priority and policy rule ordering in AOS-CX.
You have set up a mirroring session between an AOS-CX switch and a management station, running Wireshark. You want to capture just the traffic sent in the mirroring session, not the management station’s other traffic.
What should you do?
- A . Apply this capture filter: ip proto 47
- B . Edit protocol preferences and enable ARUBA_ERM.
- C . Edit protocol preferences and enable HPE_ERM.
- D . Apply this capture filter: udp port 5555
D
Explanation:
To capture only the traffic sent in the mirroring session between an AOS-CX switch and a management station running Wireshark, you should apply a capture filter that isolates the specific traffic of interest. In this case, using the filter udp port 5555 will capture the traffic associated with the mirroring session. This is because AOS-CX switches typically use UDP port 5555 for mirrored traffic, ensuring that only the relevant mirrored packets are captured and excluding other traffic generated by the management station.
Reference: Aruba’s AOS-CX documentation and network management guides detail the configuration and monitoring of traffic mirroring sessions, including the use of specific ports for mirrored traffic.
HPE Aruba Networking Central displays an alert about an Infrastructure Attack that was detected. You go to the Security > RAPIDS events and see that the attack was "Detect adhoc using Valid SSID." What is one possible next step?
- A . Make sure that you have tuned the threshold for that check as false positives are common for it.
- B . Make sure that clients have updated drivers, as faulty drivers are a common explanation for this attack type.
- C . Use HPE Aruba Networking Central floorplans or the detecting AP identities to locate the general area for the threat.
- D . Look for the IP address associated with the offender and then check for that IP address among HPE Aruba Networking Central clients.
C
Explanation:
RAPIDS Ad-Hoc Detection:
The alert "Detect ad-hoc using Valid SSID" indicates that a device is broadcasting an SSID that matches a valid network SSID in ad-hoc mode. This can be an indication of an infrastructure attack or misconfiguration.
Next Steps:
Use Aruba Central floorplans or AP location data to identify the physical area where the offending device is detected.
Locate and investigate the device to determine if it is malicious or simply misconfigured.
Option Analysis:
Option A: Incorrect. While tuning thresholds is useful for reducing false positives, this step does not directly address a potential threat.
Option B: Incorrect. Faulty drivers can cause similar behavior, but this step is not immediately actionable without locating the device first.
Option C: Correct. Floorplans or AP identities help locate the threat’s physical area for further investigation.
Option D: Incorrect. RAPIDS focuses on detecting devices via SSID and MAC, not IP addresses, making this approach less relevant.
HPE Aruba Networking Central displays an alert about an Infrastructure Attack that was detected. You go to the Security > RAPIDS events and see that the attack was "Detect adhoc using Valid SSID." What is one possible next step?
- A . Make sure that you have tuned the threshold for that check as false positives are common for it.
- B . Make sure that clients have updated drivers, as faulty drivers are a common explanation for this attack type.
- C . Use HPE Aruba Networking Central floorplans or the detecting AP identities to locate the general area for the threat.
- D . Look for the IP address associated with the offender and then check for that IP address among HPE Aruba Networking Central clients.
C
Explanation:
RAPIDS Ad-Hoc Detection:
The alert "Detect ad-hoc using Valid SSID" indicates that a device is broadcasting an SSID that matches a valid network SSID in ad-hoc mode. This can be an indication of an infrastructure attack or misconfiguration.
Next Steps:
Use Aruba Central floorplans or AP location data to identify the physical area where the offending device is detected.
Locate and investigate the device to determine if it is malicious or simply misconfigured.
Option Analysis:
Option A: Incorrect. While tuning thresholds is useful for reducing false positives, this step does not directly address a potential threat.
Option B: Incorrect. Faulty drivers can cause similar behavior, but this step is not immediately actionable without locating the device first.
Option C: Correct. Floorplans or AP identities help locate the threat’s physical area for further investigation.
Option D: Incorrect. RAPIDS focuses on detecting devices via SSID and MAC, not IP addresses, making this approach less relevant.
Refer to the exhibit.
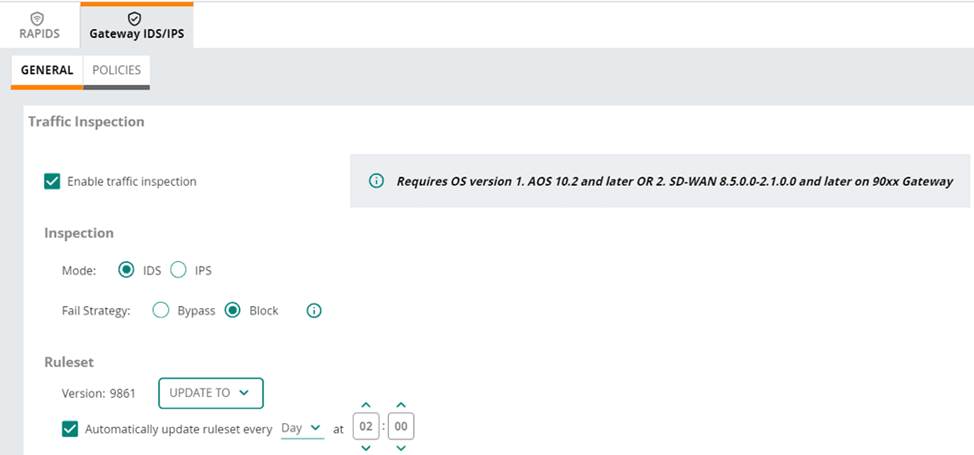
(Note that the HPE Aruba Networking Central interface shown here might look slightly different from what you see in your HPE Aruba Networking Central interface as versions change; however, similar concepts continue to apply.)
An HPE Aruba Networking 9×00 gateway is part of an HPE Aruba Networking Central group that has the settings shown in the exhibit.
What would cause the gateway to drop traffic as part of its IDPS settings?
- A . Its site-to-site VPN connections failing
- B . Traffic matching a rule in the active ruleset
- C . Its IDPS engine failing
- D . Traffic showing anomalous behavior
B
Explanation:
In the exhibit, the HPE Aruba Networking Central settings for the 9×00 gateway show that traffic inspection is enabled, and the gateway is set to operate in IDS (Intrusion Detection System) mode with the fail strategy set to "Block". This configuration means that the gateway will drop traffic if it matches a rule in the active ruleset.
Refer to the exhibit.

(Note that the HPE Aruba Networking Central interface shown here might look slightly different from what you see in your HPE Aruba Networking Central interface as versions change; however, similar concepts continue to apply.)
An HPE Aruba Networking 9×00 gateway is part of an HPE Aruba Networking Central group that has the settings shown in the exhibit.
What would cause the gateway to drop traffic as part of its IDPS settings?
- A . Its site-to-site VPN connections failing
- B . Traffic matching a rule in the active ruleset
- C . Its IDPS engine failing
- D . Traffic showing anomalous behavior
B
Explanation:
In the exhibit, the HPE Aruba Networking Central settings for the 9×00 gateway show that traffic inspection is enabled, and the gateway is set to operate in IDS (Intrusion Detection System) mode with the fail strategy set to "Block". This configuration means that the gateway will drop traffic if it matches a rule in the active ruleset.
Refer to the exhibit.

(Note that the HPE Aruba Networking Central interface shown here might look slightly different from what you see in your HPE Aruba Networking Central interface as versions change; however, similar concepts continue to apply.)
An HPE Aruba Networking 9×00 gateway is part of an HPE Aruba Networking Central group that has the settings shown in the exhibit.
What would cause the gateway to drop traffic as part of its IDPS settings?
- A . Its site-to-site VPN connections failing
- B . Traffic matching a rule in the active ruleset
- C . Its IDPS engine failing
- D . Traffic showing anomalous behavior
B
Explanation:
In the exhibit, the HPE Aruba Networking Central settings for the 9×00 gateway show that traffic inspection is enabled, and the gateway is set to operate in IDS (Intrusion Detection System) mode with the fail strategy set to "Block". This configuration means that the gateway will drop traffic if it matches a rule in the active ruleset.
