Practice Free AZ-500 Exam Online Questions
You have an Azure Active Directory (Azure AD) tenant that contains a user named Admin1. Admin1 is assigned the Application developer role.
You purchase a cloud app named App1 and register App1 in Azure AD.
Admin1 reports that the option to enable token encryption for App1 is unavailable.
You need to ensure that Admin1 can enable token encryption for App1 in the Azure portal.
What should you do?
- A . Upload a certificate for App1.
- B . Modify the API permissions of App1.
- C . Add App1 as an enterprise application.
- D . Assign Admin1 the Cloud application administrator role.
C
Explanation:
This is a tricky one because uploading a certificate is also required. However, the question states that the Token Encryption option is unavailable. This is because the app is not added as an enterprise application. When the app is added as an enterprise application, the Token Encryption option will be available. Then you can upload the certificate.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/howto-saml-token-encryption
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant that contains two users named User1 and User2 and a registered app named App1.
You create an app-specific role named Role1.
You need to assign Role1 to User1 and enable User2 to request access to App1.
Which two settings should you modify? To answer select the appropriate settings in the answer area NOTE: Each correct selection is worth one pant.
You need to ensure that users can access VM0. The solution must meet the platform protection requirements.
What should you do?
- A . Move VM0 to Subnet1.
- B . On Firewall, configure a network traffic filtering rule.
- C . Assign RT1 to AzureFirewallSubnet.
- D . On Firewall, configure a DNAT rule.
D
Explanation:
https://docs.microsoft.com/en-us/azure/firewall/tutorial-firewall-dnat
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center for the centralized policy management of three Azure subscriptions.
You use several policy definitions to manage the security of the subscriptions.
You need to deploy the policy definitions as a group to all three subscriptions.
Solution: You create an initiative and an assignment that is scoped to a management group.
Does this meet the goal?
- A . Yes
- B . No
A
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/governance/policy/overview
You have a Microsoft Entra tenant that uses Microsoft Entra Permissions Management and contains the accounts shown in the following table:
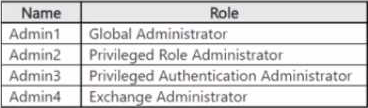
Which accounts will be listed as assigned to highly privileged roles on the Azure AD insights tab in the Entra Permissions Management portal?
- A . Admin1 only
- B . Admin2 and Admin3 only
- C . Admin2 and Admin4 only
- D . Admin1. Admin2, and Admin3 only
- E . Admin2. Admin3, and Admin4 only
- F . Admin1. Admin2, Admin3. and Admin4
You have an Azure subscription.
You plan to deploy an Azure SQL managed instance named AzSQL1.
You need to recommend an encryption solution for AzSQL1.
The solution must meet the following requirements:
* The database engine must be prevented from performing key provisioning, data encryption, and decryption operations.
* Database administrators must be prevented from viewing the encrypted data in plain text.
What should you include in the recommendation?
- A . Azure Disk Encryption
- B . TLS
- C . Transparent Data Encryption (TDE) with customer-managed keys
- D . Always Encrypted
- E . Transparent Data Encryption (TDE) with Microsoft-managed keys
You have an Azure Active Directory (Azure AD) tenant named Contoso.com and an Azure Service (AKS) cluster AKS1.
You discover that AKS1 cannot be accessed by using accounts from Contoso.com
You need to ensure AKS1 can be accessed by using accounts from Contoso.com The solution must minimize administrative effort.
What should you do first?
- A . From Azure recreate AKS1,
- B . From AKS1, upgrade the version of Kubermetes.
- C . From Azure AD, implement Azure AD Premium P2.
- D . From Azure AD, configure the User settings
A
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/aks/azure-ad-integration-cli
You need to ensure that you can meet the security operations requirements.
What should you do first?
- A . Turn on Auto Provisioning in Security Center.
- B . Integrate Security Center and Microsoft Cloud App Security.
- C . Upgrade the pricing tier of Security Center to Standard.
- D . Modify the Security Center workspace configuration.
C
Explanation:
The Standard tier extends the capabilities of the Free tier to workloads running in private and other public clouds, providing unified security management and threat protection across your hybrid cloud workloads. The Standard tier also adds advanced threat detection capabilities, which uses built-in behavioral analytics and machine learning to identify attacks and zero-day exploits, access and application controls to reduce exposure to network attacks and malware, and more.
Scenario: Security Operations Requirements
Litware must be able to customize the operating system security configurations in Azure Security Center.
Reference: https://docs.microsoft.com/en-us/azure/security-center/security-center-pricing
You have an Azure subscription that contains a virtual machine named VM1.
You create an Azure key vault that has the following configurations:
– Name: Vault5
– Region: West US
– Resource group: RG1
You need to use Vault5 to enable Azure Disk Encryption on VM1. The solution must support backing up VM1 by using Azure Backup.
Which key vault settings should you configure?
- A . Access policies
- B . Secrets
- C . Keys
- D . Locks
A
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/key-vault/key-vault-secure-your-key-vault
You have an Azure subscription that contains a
You need to grant user1 access to blob1. The solution must ensure that the access expires after six days.
What should you use?
- A . a shared access policy
- B . a shared access signature (SAS)
- C . role-based access control (RBAC)
- D . a managed identity
B
Explanation:
Depending on how you want to authorize access to blob data in the Azure portal, you’ll need specific permissions. In most cases, these permissions are provided via Azure role-based access control (Azure RBAC). For more information about Azure RBAC, see What is Azure role-based access control (Azure RBAC)
https://learn.microsoft.com/en-us/azure/storage/blobs/authorize-data-operations-portal
