Practice Free AZ-500 Exam Online Questions
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center for the centralized policy management of three Azure subscriptions.
You use several policy definitions to manage the security of the subscriptions.
You need to deploy the policy definitions as a group to all three subscriptions.
Solution: You create a resource graph and an assignment that is scoped to a management group.
Does this meet the goal?
- A . Yes
- B . No
A
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/governance/management-groups/create
You have an Azure subscription that contains the users shown in the following table.
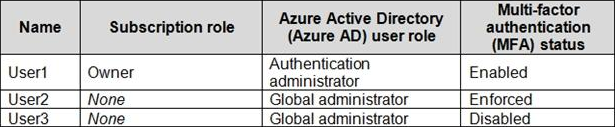
Which users can enable Azure AD Privileged Identity Management (PIM)?
- A . User2 and User3 only
- B . User1 and User2 only
- C . User2 only
- D . User1 only
B
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-deployment-plan
You have an Azure Storage account named storage1 that has a container named container1. You need to prevent the blobs in container1 from being modified.
What should you do?
- A . From container1, change the access level.
- B . From container1 add an access policy.
- C . From container1, modify the Access Control (1AM) settings.
- D . From storage1, enable soft delete for blobs.
B
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/storage/blobs/storage-blob-immutable-storage?tabs=azure-portal
You have an Azure subscription that contains the storage accounts shown in the following, table.
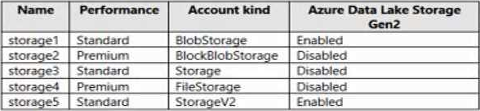
You enable Microsoft Defender for Storage.
Which storage services of storages are monitored by Microsoft Defender for Storage, and which storage accounts are protected by Microsoft Defender for Storage? To answer, select the appropriate options in the answer area.

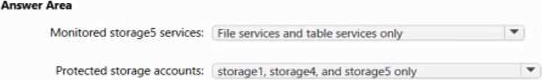
HOTSPOT
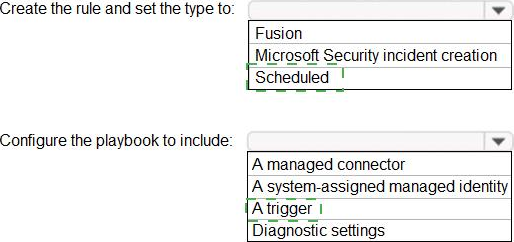
You have an Azure Sentinel workspace that contains an Azure Active Directory (Azure AD) connector, an Azure Log Analytics query named Query1 and a playbook named Playbook1.
Query1 returns a subset of security events generated by Azure AD.
You plan to create an Azure Sentinel analytic rule based on Query1 that will trigger Playbook1.
You need to ensure that you can add Playbook1 to the new rule.
What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
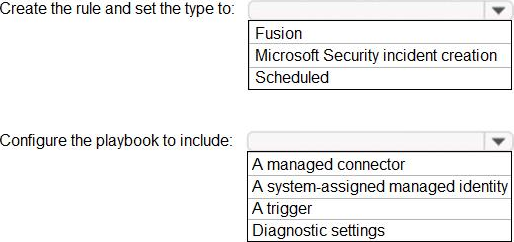
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/tutorial-detect-threats-custom
https://docs.microsoft.com/en-us/azure/sentinel/tutorial-respond-threats-playbook
HOTSPOT
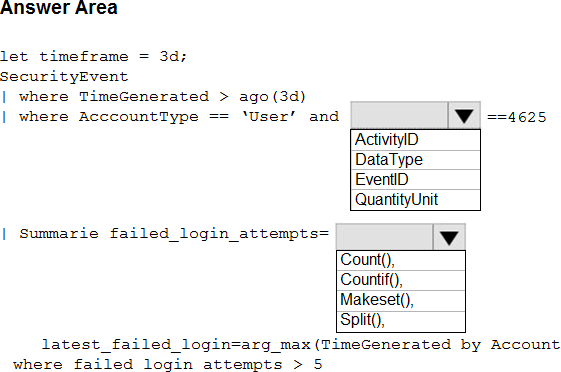
You suspect that users are attempting to sign in to resources to which they have no access.
You need to create an Azure Log Analytics query to identify failed user sign-in attempts from the last three days. The results must only show users who had more than five failed sign-in attempts.
How should you configure the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
The following example identifies user accounts that failed to log in more than five times in the last day, and when they last attempted to log in.
let timeframe = 1d;
SecurityEvent
| where TimeGenerated > ago(1d)
| where AccountType == ‘User’ and EventID == 4625 // 4625 – failed log in
| summarize failed_login_attempts=count(), latest_failed_login=arg_max(TimeGenerated, Account) by Account
| where failed_login_attempts > 5
| project-away Account1
Reference: https://docs.microsoft.com/en-us/azure/azure-monitor/log-query/examples
HOTSPOT
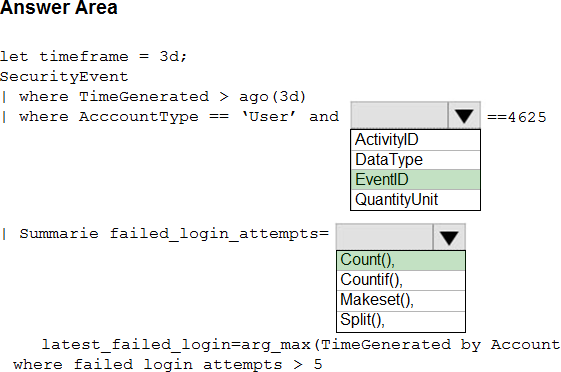
You suspect that users are attempting to sign in to resources to which they have no access.
You need to create an Azure Log Analytics query to identify failed user sign-in attempts from the last three days. The results must only show users who had more than five failed sign-in attempts.
How should you configure the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.


Explanation:
The following example identifies user accounts that failed to log in more than five times in the last day, and when they last attempted to log in.
let timeframe = 1d;
SecurityEvent
| where TimeGenerated > ago(1d)
| where AccountType == ‘User’ and EventID == 4625 // 4625 – failed log in
| summarize failed_login_attempts=count(), latest_failed_login=arg_max(TimeGenerated, Account) by Account
| where failed_login_attempts > 5
| project-away Account1
Reference: https://docs.microsoft.com/en-us/azure/azure-monitor/log-query/examples
HOTSPOT
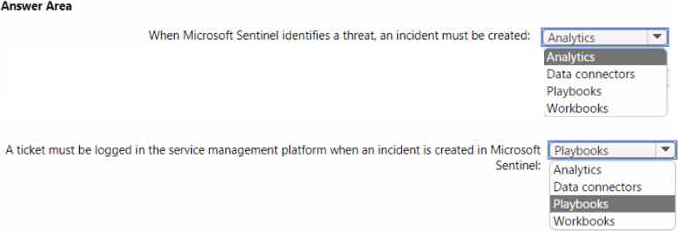
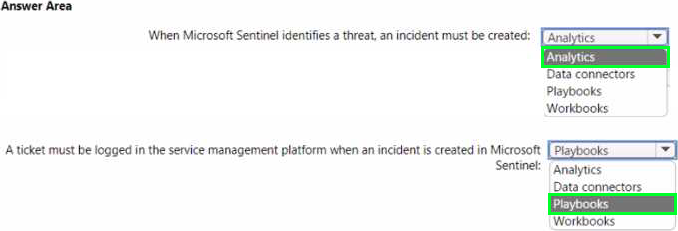
You have an Azure subscription that contains a Microsoft Sentinel workspace.
Microsoft Sentinel is configured to ingest logs from several Azure workloads. A third-party service management platform is used to manage incidents.
You need to identify which Microsoft Sentinel components to configure to meet the following requirements:
• When Microsoft Sentinel identifies a threat an incident must be created.
• A ticket must be logged in the service management platform when an incident is created in Microsoft Sentinel.
Which component should you identify for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure Active Directory (Azure AD) tenant. The tenant contains users that are assigned Azure AD Premium Plan 2 licenses.
You have an partner company that has a domain named The fabrikam.com domain contains a user named user’. User’ has an email address of [email protected].
You to provide User1 with to the resources in the tenant.
The solution must meet the following requirements:
– user1 must be able to sign in by using the [email protected] credentials
– You must be able to grant User1 access to the resources in the tenant
– Administrative effort must be minimized.
What should you do?
- A . Create a user account for user1.
- B . Create an invite for User1.
- C . To the tenant add fabrikamcom as a custom domain
- D . Set Enable guest self-service sign up via user flows to Yes for the tenant.
You have an Azure subscription that contains a user named Adminl1 and a virtual machine named VM1. VM1 runs Windows Server 2019 and was deployed by using an Azure Resource Manager template. VM1 is the member of a backend pool of a public Azure Basic Load Balancer.
Admin1 reports that VM1 is listed as Unsupported on the Just in time VM access blade of Azure Security Center.
You need to ensure that Admin1 can enable just in time (JIT) VM access for VM1.
What should you do?
- A . Create and configure an additional public IP address for VM 1.
- B . Replace the Basic Load Balancer with an Azure Standard Load Balancer.
- C . Assign an Azure Active Directory Premium Plan 1 license to Admin1.
- D . Create and configure a network security group (NSG).
D
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/security-center/security-center-just-in-time?tabs=jit-config-asc%2Cjit-request-asc
