Practice Free HPE7-A02 Exam Online Questions
Refer to the exhibit.
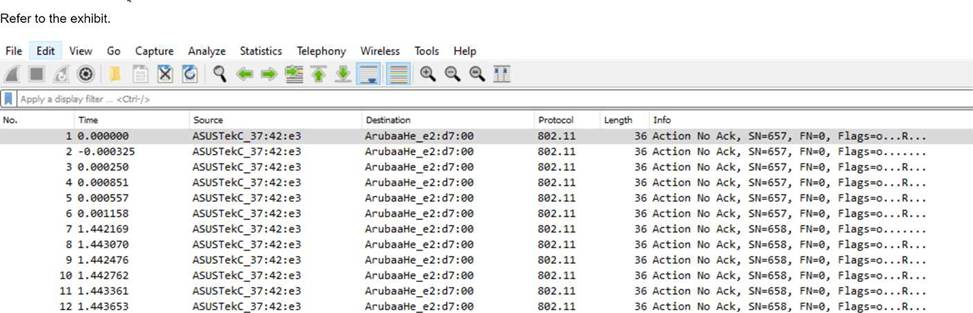
You have downloaded a packet capture that you generated on HPE Aruba Networking Central. When you open the capture in Wireshark, you see the output shown in the exhibit.
What should you do in Wireshark so that you can better interpret the packets?
- A . Choose to decode UDP port 5555 packets as ARUBA_ERM and set the Aruba ERM Type to 0.
- B . Edit preferences for IEEE 802.11 and chose to ignore the Protection bit with IV.
- C . Apply the following display filter: wlan.fc.type == 1.
- D . Edit the Enabled Protocols and make sure that 802.11, GRE, and Aruba_ERM are enabled.
A
Explanation:
To better interpret the packets shown in the Wireshark capture, you should choose to decode UDP port 5555 packets as ARUBA_ERM and set the Aruba ERM Type to 0. This configuration will allow Wireshark to properly decode and display the Aruba-specific encapsulated remote mirroring (ERM) packets, providing a clearer understanding of the traffic.
Which use case is fulfilled by applying a time range to a firewall rule on an AOS device?
- A . Enforcing the rule only during the specified time range
- B . Tuning the session timeout for sessions established with this rule
- C . Locking clients that violate the rule for the specified time range
- D . Setting the time range over which hit counts for the rule are aggregated
A
Explanation:
Applying a time range to a firewall rule on an AOS device fulfills the use case of enforcing the rule only during the specified time range. This allows administrators to control when specific firewall rules are active, which can be useful for implementing policies that only need to be in effect during certain hours, such as blocking or allowing access to specific resources outside of business hours.
You need to set up HPE Aruba Networking ClearPass Policy Manager (CPPM) to provide certificate-based authentication of 802.1X supplicants.
How should you upload the root CA certificate for the supplicants’ certificates?
- A . As a ClearPass Server certificate with the RADIUS/EAP usage
- B . As a Trusted CA with the AD/LDAP usage
- C . As a Trusted CA with the EAP usage
- D . As a ClearPass Server certificate with the Database usage
C
Explanation:
To set up HPE Aruba Networking ClearPass Policy Manager (CPPM) for certificate-based authentication of 802.1X supplicants, you need to upload the root CA certificate as a Trusted CA with the EAP usage. This configuration allows the ClearPass server to validate the certificates presented by the supplicants during the 802.1X authentication process. By marking the certificate for EAP usage, ClearPass can properly authenticate the supplicant devices using the trusted certificate authority (CA) that issued their certificates.
Reference: Configuration guidelines and best practices for ClearPass Policy Manager are available in Aruba’s ClearPass documentation, specifically detailing the steps for uploading and configuring root CA certificates for EAP-based authentication.
You need to set up HPE Aruba Networking ClearPass Policy Manager (CPPM) to provide certificate-based authentication of 802.1X supplicants.
How should you upload the root CA certificate for the supplicants’ certificates?
- A . As a ClearPass Server certificate with the RADIUS/EAP usage
- B . As a Trusted CA with the AD/LDAP usage
- C . As a Trusted CA with the EAP usage
- D . As a ClearPass Server certificate with the Database usage
C
Explanation:
To set up HPE Aruba Networking ClearPass Policy Manager (CPPM) for certificate-based authentication of 802.1X supplicants, you need to upload the root CA certificate as a Trusted CA with the EAP usage. This configuration allows the ClearPass server to validate the certificates presented by the supplicants during the 802.1X authentication process. By marking the certificate for EAP usage, ClearPass can properly authenticate the supplicant devices using the trusted certificate authority (CA) that issued their certificates.
Reference: Configuration guidelines and best practices for ClearPass Policy Manager are available in Aruba’s ClearPass documentation, specifically detailing the steps for uploading and configuring root CA certificates for EAP-based authentication.
A company wants HPE Aruba Networking ClearPass Policy Manager (CPPM) to respond to Syslog messages from its Check Point firewall. You have added the firewall as an event source and set up an event service. However, test Syslog messages are not triggering the expected actions.
What is one CPPM setting that you should check?
- A . ClearPass Device Insight integration is disabled.
- B . The Check Point Extension is installed through ClearPass Guest.
- C . The CoA delay value is set to 0 on the server.
- D . Ingress Event Dictionaries for Check Point messages are enabled.
D
Explanation:
To ensure that HPE Aruba Networking ClearPass Policy Manager (CPPM) responds correctly to Syslog messages from a Check Point firewall, you need to check that the Ingress Event Dictionaries for Check Point messages are enabled. These dictionaries are necessary for CPPM to properly interpret and respond to the Syslog messages received from the firewall.
A company wants HPE Aruba Networking ClearPass Policy Manager (CPPM) to respond to Syslog messages from its Check Point firewall. You have added the firewall as an event source and set up an event service. However, test Syslog messages are not triggering the expected actions.
What is one CPPM setting that you should check?
- A . ClearPass Device Insight integration is disabled.
- B . The Check Point Extension is installed through ClearPass Guest.
- C . The CoA delay value is set to 0 on the server.
- D . Ingress Event Dictionaries for Check Point messages are enabled.
D
Explanation:
To ensure that HPE Aruba Networking ClearPass Policy Manager (CPPM) responds correctly to Syslog messages from a Check Point firewall, you need to check that the Ingress Event Dictionaries for Check Point messages are enabled. These dictionaries are necessary for CPPM to properly interpret and respond to the Syslog messages received from the firewall.
You are using Wireshark to view packets captured from HPE Aruba Networking infrastructure, but you are not sure that the packets are displaying correctly.
In which circumstance does it make sense to ensure that Wireshark has GRE enabled as one of its analyzed protocols?
- A . When the traffic was captured on an HPE Aruba Networking gateway and sent to a remote IP
- B . When the traffic was captured on an HPE Aruba Networking gateway dataplane and saved to a file
- C . When the traffic was captured on an HPE Aruba Networking Mobility Controller (MC) control plane and saved to a file
- D . When the traffic was captured on an HPE Aruba Networking MC dataplane and saved to a file
D
Explanation:
On Aruba Mobility Controllers, dataplane captures can include wireless frames encapsulated inside GRE (for example, ERM / remote mirroring or tunneled 802.11 data). If Wireshark does not have GRE dissection enabled, these packets may appear as generic IP/UDP payloads, and the inner traffic (client frames) will not decode correctly.
MC dataplane is exactly where GRE-encapsulated user traffic is likely to appear. Enabling GRE in Wireshark allows you to see and decode the inner payload (802.11/Ethernet/IP).
MC control plane traffic is generally not GRE encapsulated data traffic.
For gateways, captures exported as ERM over UDP often require different decoding (e.g., ARUBA_ERM, not generic GRE).
Thus, the most appropriate case to ensure GRE is enabled is when the capture came from the MC dataplane → Option D.
A company has a variety of HPE Aruba Networking solutions, including an HPE Aruba Networking infrastructure and HPE Aruba Networking ClearPass Policy Manager (CPPM). The company passes traffic from the corporate LAN destined to the data center through a third-party SRX firewall. The company would like to further protect itself from internal threats.
What is one solution that you can recommend?
- A . Have the third-party firewall send Syslogs to CPPM, which can work with network devices to lock internal attackers out of the network.
- B . Use tunnel mode SSIDs and user-based tunneling (UBT) on AOS-CX switches to pass all internal traffic directly through the third-party firewall.
- C . Add ClearPass Device Insight (CPDI) to the solution; integrate it with the third-party firewall to develop more complete device profiles.
- D . Configure CPPM to poll the third-party firewall for a broad array of information about internal clients, such as profile and posture.
A
Explanation:
To further protect the company from internal threats, you can recommend having the third-party SRX firewall send Syslogs to HPE Aruba Networking ClearPass Policy Manager (CPPM). ClearPass can analyze these logs to detect potential security incidents and coordinate with network devices to respond to threats. By integrating Syslog data from the firewall, CPPM can identify malicious activities and take actions such as locking internal attackers out of the network or triggering specific security policies. This approach enhances the company’s internal threat detection and response capabilities.
Reference: Aruba’s ClearPass documentation on integrating with third-party security solutions and utilizing Syslog data for enhanced network security provides detailed guidance on setting up and using these features.
A company has a variety of HPE Aruba Networking solutions, including an HPE Aruba Networking infrastructure and HPE Aruba Networking ClearPass Policy Manager (CPPM). The company passes traffic from the corporate LAN destined to the data center through a third-party SRX firewall. The company would like to further protect itself from internal threats.
What is one solution that you can recommend?
- A . Have the third-party firewall send Syslogs to CPPM, which can work with network devices to lock internal attackers out of the network.
- B . Use tunnel mode SSIDs and user-based tunneling (UBT) on AOS-CX switches to pass all internal traffic directly through the third-party firewall.
- C . Add ClearPass Device Insight (CPDI) to the solution; integrate it with the third-party firewall to develop more complete device profiles.
- D . Configure CPPM to poll the third-party firewall for a broad array of information about internal clients, such as profile and posture.
A
Explanation:
To further protect the company from internal threats, you can recommend having the third-party SRX firewall send Syslogs to HPE Aruba Networking ClearPass Policy Manager (CPPM). ClearPass can analyze these logs to detect potential security incidents and coordinate with network devices to respond to threats. By integrating Syslog data from the firewall, CPPM can identify malicious activities and take actions such as locking internal attackers out of the network or triggering specific security policies. This approach enhances the company’s internal threat detection and response capabilities.
Reference: Aruba’s ClearPass documentation on integrating with third-party security solutions and utilizing Syslog data for enhanced network security provides detailed guidance on setting up and using these features.
You need to set up HPE Aruba Networking ClearPass Policy Manager (CPPM) to provide certificate-based authentication of 802.1X supplicants.
How should you upload the root CA certificate for the supplicants’ certificates?
- A . As a ClearPass Server certificate with the RADIUS/EAP usage.
- B . As a ClearPass Server certificate with the Database usage.
- C . As a Trusted CA with the AD/LDAP usage.
- D . As a Trusted CA with the EAP usage.
D
Explanation:
