Practice Free XK0-005 Exam Online Questions
When trying to log in remotely to a server, a user receives the following message:

The server administrator is investigating the issue on the server and receives the following outputs:
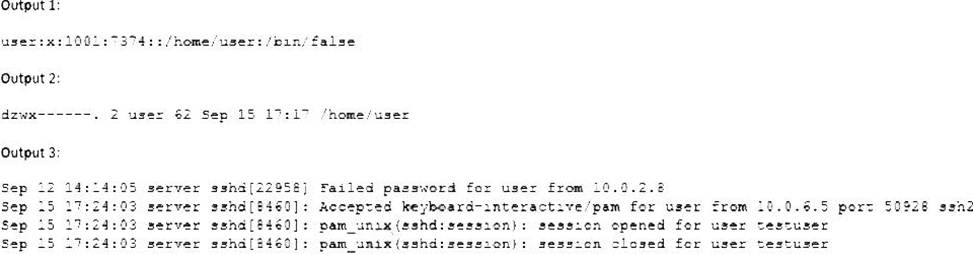
Which of the following is causing the issue?
- A . The wrong permissions are on the user’s home directory.
- B . The account was locked out due to three failed logins.
- C . The user entered the wrong password.
- D . The user has the wrong shell assigned to the account.
D
Explanation:
The user has the wrong shell assigned to the account, which is causing the issue. The output 1 shows that the user’s shell is set to /bin/false, which is not a valid shell and will prevent the user from logging in. The output 2 shows that the user’s home directory has the correct permissions (drwxr-xr-x), and the output 3 shows that the user entered the correct password and was accepted by the SSH daemon, but the session was closed immediately due to the invalid shell. The other options are incorrect because they are not supported by the outputs. CompTIA Linux+ (XK0-005) Certification Study Guide, Chapter 13: Managing Network Services, page 413.
A systems administrator is investigating why one of the servers has stopped connecting to the internet.
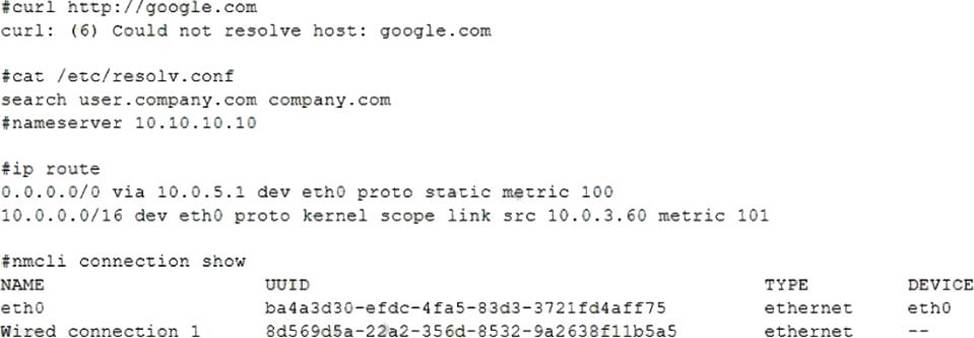
Which of the following is causing the issue?
- A . The DNS address has been commented out in the configuration file.
- B . The search entry in the /etc/resolv.conf file is incorrect.
- C . Wired connection 1 is offline.
- D . No default route is defined.
D
Explanation:
The issue is caused by the lack of a default route defined in the /etc/sysconfig/network-scripts/ifcfg-enp0s3 file. A default route is a special route that specifies where to send packets that do not match any other routes in the routing table. Without a default route, the server will not be able to communicate with hosts outside its local network. The default route is usually configured with the
GATEWAY option in the network interface configuration file. For example, to set the default gateway to 192.168.1.1, the file should contain:
GATEWAY=192.168.1.1
The other options are not causing the issue. The DNS address is not commented out in the configuration file, it is specified with the DNS1 option. The search entry in the /etc/resolv.conf file is correct, it specifies the domain name to append to unqualified hostnames. Wired connection 1 is online, as indicated by the ONBOOT=yes option and the output of ip link show enp0s3 command. Configuring IP Networking with nmcli; Configuring IP Networking with ifcfg Files
A systems technician needs to install a third-party software package.
Which of the following commands would allow the technician to download this software package from a remote server?
- A . netstat
- B . nc
- C . telnet
- D . wget
D
Explanation:
The wget command is used to download files from remote servers via HTTP, HTTPS, and FTP.
Option D (Correct): wget retrieves files from a specified URL.
Option A (netstat): Used to display network connections, not for downloading files.
Option B (nc C Netcat): Used for networking and port scanning, not file downloads.
Option C (telnet): Used for remote terminal connections, not for downloading files.
Reference: CompTIA Linux+ XK0-005 Official Guide C Chapter on Package Management.
A Linux administrator needs to list the packages that are currently installed on a server.
Which of the following commands should the administrator use?
- A . snap install list
- B . snap list
- C . snap show
- D . snap packages
B
Explanation:
The snap list command lists all installed Snap packages on the system. Snap is a package management system that is used for installing and managing software packages in Linux. It shows information about the installed Snap packages, including the version, publisher, and whether the package is active.
A systems administrator has been tasked with disabling the nginx service from the environment to prevent it from being automatically and manually started.
Which of the following commands will accomplish this task?
- A . systemct1 cancel nginx
- B . systemct1 disable nginx
- C . systemct1 mask nginx
- D . systemct1 stop nginx
C
Explanation:
The command systemct1 mask nginx disables the nginx service from the environment and prevents it from being automatically and manually started. This command creates a symbolic link from the service unit file to /dev/null, which makes the service impossible to start. This is the correct way to accomplish the task. The other options are incorrect because they either do not exist (systemct1 cancel nginx), do not prevent manual start (systemct1 disable nginx), or do not prevent automatic start (systemct1 stop nginx). CompTIA Linux+ (XK0-005) Certification Study Guide, Chapter 14: Managing Processes and Scheduling Tasks, page 429.
A Linux administrator needs to deploy an Apache web server in a container. In addition, the container needs to run in the background, and the web server needs to be exposed on port 8080 of the host machine.
Which of the following commands will satisfy these requirements?
- A . sudo docker run -b -t -p 8080:80 –name mywebserver httpd
- B . sudo docker run -d -t -p 8080:80 –name myweb httpd
- C . sudo docker run -d -t -p 80:8080 –name myweb httpd
- D . sudo docker run -b -t -p 80:8080 –name mywebserver httpd
B
Explanation:
-d: run in detached (background) mode
-p 8080:80: expose port 80 inside container on 8080 on host
–name myweb: sets container name
Only B is correctly structured.
Reference: CompTIA Linux+ XK0-005 Official Study Guide, Domain 2.5 C Containers
“Use docker run -d -p host_port:container_port to deploy containers and expose services.”
A systems administrator detected corruption in the /data filesystem.
Given the following output:
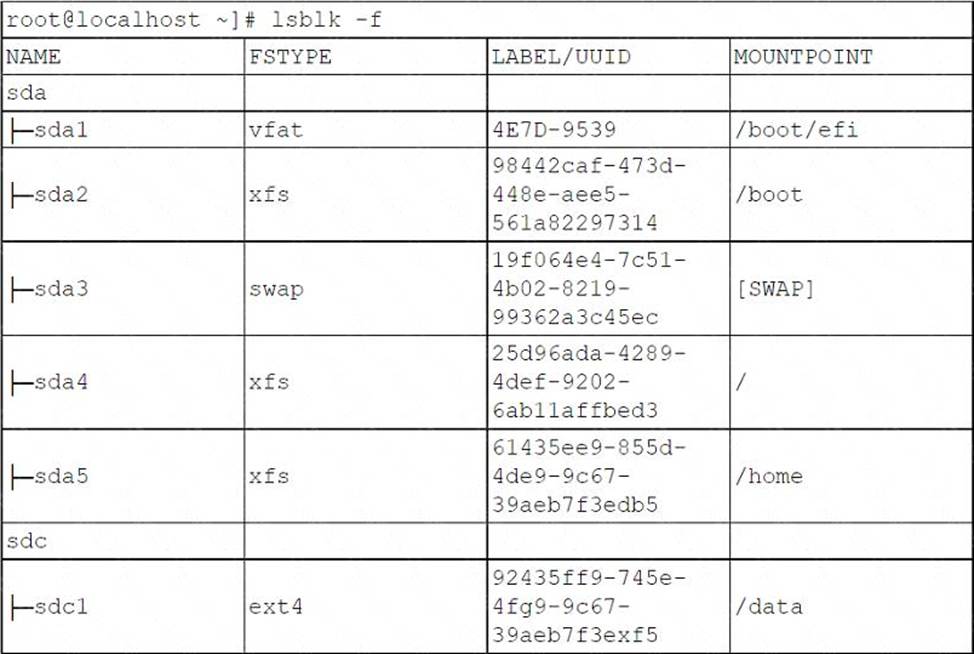
Which of the following commands can the administrator use to best address this issue?
- A . umount /data mkfs. xfs /dev/sclcl mount /data
- B . umount /data xfs repair /dev/ sdcl mount /data
- C . umount /data fsck /dev/ sdcl mount / data
- D . umount /data pvs /dev/sdcl mount /data
B
Explanation:
The xfs repair command is used to check and repair an XFS filesystem, which is the type of filesystem used for the /data partition, as shown in the output. The administrator needs to unmount the /data partition before running the xfs repair command on it, and then mount it back after the repair is done.
For example: umount /data; xfs_repair /dev/sdcl; mount /data. The mkfs.xfs command is used to create a new XFS filesystem, which would erase all the data on the partition. The fsck command is used to check and repair other types of filesystems, such as ext4, but not XFS. The pvs command is used to display information about physical volumes in a logical volume manager (LVM) setup, which is not relevant for this issue.
A diagnostic tool reports a "host seems down" event for a server with an IP address of 192.168.47.44.
Which of the following commands should the administrator use to confirm the host down event?
- A . nmap 192.168.47.0/32
- B . netcat 192.168.47.44
- C . nmap 192.168.47.44 -Pn
- D . ping -c 1 192.168.47.44
D
Explanation:
The ping -c 1 192.168.47.44 command sends one ICMP echo request to the specified host to check its availability. If the host is down, there will be no response. This is the quickest way to confirm if a host is reachable. nmap -Pn can also be used to check a host status, but ping is faster and lighter.
Which of the following tools is commonly used for creating CI/CD pipelines?
- A . Chef
- B . Puppet
- C . Jenkins
- D . Ansible
C
Explanation:
The tool that is commonly used for creating CI/CD pipelines is Jenkins. Jenkins is an open-source automation server that enables continuous integration and continuous delivery (CI/CD) of software projects. Jenkins allows developers to build, test, and deploy code changes automatically and frequently using various plugins and integrations. Jenkins also supports distributed builds, parallel execution, pipelines as code, and real-time feedback. CompTIA Linux+ (XK0-005) Certification Study Guide, Chapter 19: Managing Source Code; Jenkins
Which of the following concepts describes the approach of keeping all configurations in a repository?
- A . Inventory
- B . Infrastructure as Code
- C . Orchestration
- D . Agentless deployment
B
Explanation:
Infrastructure as Code (IaC) is the practice of storing system configuration (e.g., Ansible, Terraform) in
version-controlled repositories.
Incorrect Options:
A: Inventory is a list of hosts or devices.
C: Orchestration refers to process coordination.
D: Refers to execution model (e.g., Ansible), not config storage.
Reference: CompTIA Linux+ XK0-005 Study Guide, Chapter 12 IaC definition and tools
