Practice Free SCS-C03 Exam Online Questions
A company is using AWS to run a long-running analysis process on data that is stored in Amazon S3 buckets. The process runs on a fleet of Amazon EC2 instances in an Auto Scaling group. The EC2 instances are deployed in a private subnet that does not have internet access.
The EC2 instances access Amazon S3 through an S3 gateway endpoint that has the default access policy. Each EC2 instance uses an instance profile role that allows s3:GetObject and s3:PutObject only
for required S3 buckets.
The company learns that one or more EC2 instances are compromised and are exfiltrating data to an S3 bucket that is outside the company’s AWS Organization. The processing job must continue to function.
Which solution will meet these requirements?
- A . Update the policy on the S3 gateway endpoint to allow S3 actions only if aws:ResourceOrgId and aws:PrincipalOrgId match the company’s organization.
- B . Update the instance profile role policy to require aws:ResourceOrgId.
- C . Add a network ACL rule to block outbound traffic on port 443.
- D . Apply an SCP that restricts S3 actions using organization condition keys.
A
Explanation:
Amazon S3 gateway endpoints support endpoint policies that can restrict which S3 resources are accessible through the endpoint. According to AWS Certified Security C Specialty documentation, endpoint policies are evaluated in addition to IAM policies and are ideal for enforcing data exfiltration controls without breaking legitimate workloads.
By updating the S3 gateway endpoint policy to require both aws:ResourceOrgId and aws:PrincipalOrgId to match the company’s AWS Organization, the security engineer ensures that EC2 instances can access only S3 buckets that belong to the organization. This immediately blocks exfiltration to external S3 buckets while allowing legitimate internal data access to continue uninterrupted.
Option B is insufficient because IAM policies alone cannot prevent access when the endpoint allows it.
Option C would break all S3 access and stop the processing job.
Option D applies too broadly and can impact unrelated services across the account.
AWS documentation highlights S3 VPC endpoint policies with organization condition keys as a best practice for preventing S3 data exfiltration in private VPC environments.
AWS Certified Security C Specialty Official Study Guide
Amazon S3 VPC Endpoint Policy Documentation
AWS Organizations Condition Keys Documentation
A company operates an Amazon EC2 instance that is registered as a target of a Network Load Balancer (NLB). The NLB is associated with a security group. The security group allows inbound TCP traffic on port 22 from 10.0.0.0/23.
The company maps the NLB to two subnets that share the same network ACL and route table. The route table has a route for 0.0.0.0/0 to an internet gateway. The network ACL has one inbound rule that has a priority of 20 and that allows TCP traffic on port 22 from 10.0.0.0/16.
A security engineer receives an alert that there is an unauthorized SSH session on the EC2 instance. The unauthorized session originates from 10.0.1.5. The company’s incident response procedure requires unauthorized SSH sessions to be immediately interrupted. The instance must remain running, and its memory must remain intact.
Which solution will meet these requirements?
- A . Restart the EC2 instance from either the AWS Management Console or the AWS CLI.
- B . Add a new inbound rule that has a priority of 10 to the network ACL to deny TCP traffic on port 22 from 10.0.1.5.
- C . Remove the security group rule that allows inbound TCP traffic on port 22 from 10.0.0.0/16.
- D . Update the route table to remove the route to the internet gateway.
B
Explanation:
Network ACLs are stateless and are evaluated in order based on rule number, with lower rule
numbers taking precedence. According to AWS Certified Security C Specialty incident response guidance, network ACLs can be used to immediately block traffic at the subnet level without restarting instances or modifying their runtime state.
By adding a deny rule with a lower priority number (10) that explicitly denies TCP traffic on port 22 from the offending IP address (10.0.1.5), the unauthorized SSH session is immediately interrupted. This approach satisfies the requirement to keep the instance running and to preserve memory for forensic analysis.
Option A violates the requirement because restarting the instance clears memory.
Option C would disrupt all legitimate SSH access, not just the unauthorized session.
Option D would block all internet access and could cause widespread service disruption.
AWS documentation emphasizes using network ACL deny rules for rapid, targeted containment when immediate interruption is required without altering instance state.
AWS Certified Security C Specialty Official Study Guide
Amazon VPC Network ACL Documentation
AWS Incident Response Best Practices
A company is planning to migrate its applications to AWS in a single AWS Region. The company’s applications will use a combination of Amazon EC2 instances, Elastic Load Balancing (ELB) load balancers, and Amazon S3 buckets. The company wants to complete the migration as quickly as possible.
All the applications must meet the following requirements:
• Data must be encrypted at rest.
• Data must be encrypted in transit.
• Endpoints must be monitored for anomalous network traffic.
Which combination of steps should a security engineer take to meet these requirements with the LEAST effort? (Select THREE.)
- A . Install the Amazon Inspector agent on EC2 instances by using AWS Systems Manager Automation.
- B . Enable Amazon GuardDuty in all AWS accounts.
- C . Create VPC endpoints for Amazon EC2 and Amazon S3. Update VPC route tables to use only the secure VPC endpoints.
- D . Configure AWS Certificate Manager (ACM). Configure the load balancers to use certificates from ACM.
- E . Use AWS Key Management Service (AWS KMS) for key management. Create an S3 bucket policy to deny any PutObject command with a condition for x-amz-meta-side-encryption.
- F . Use AWS Key Management Service (AWS KMS) for key management. Create an S3 bucket policy to deny any PutObject command with a condition for x-amz-server-side-encryption.
B, D, F
Explanation:
Amazon GuardDuty provides continuous monitoring for anomalous and malicious network activity by analyzing VPC Flow Logs, DNS logs, and CloudTrail events. Enabling GuardDuty across accounts requires minimal configuration and immediately satisfies the requirement to monitor endpoints for anomalous network traffic, as described in the AWS Certified Security C Specialty Study Guide.
Encrypting data in transit for applications behind Elastic Load Balancing is most efficiently achieved by using AWS Certificate Manager (ACM). ACM provisions and manages TLS certificates automatically, and integrating ACM with ELB enables encrypted communication without manual certificate management.
For encryption at rest in Amazon S3, AWS best practices recommend enforcing server-side encryption using AWS KMS. An S3 bucket policy that denies PutObject requests unless the x-amz-server-side-encryption condition is present ensures that all uploaded objects are encrypted at rest using KMS-managed keys. This provides strong encryption guarantees with minimal operational effort.
Option A is unnecessary because Amazon Inspector focuses on vulnerability assessment, not encryption or network anomaly detection.
Option C adds network complexity and is not required to meet the stated requirements.
Option E is incorrect because x-amz-meta-side-encryption is not a valid enforcement mechanism.
Referenced AWS Specialty Documents:
AWS Certified Security C Specialty Official Study Guide
Amazon GuardDuty Threat Detection
AWS Certificate Manager and ELB Integration
Amazon S3 Encryption Best Practices
A company runs a public web application on Amazon EKS behind Amazon CloudFront and an Application Load Balancer (ALB). A security engineer must send a notification to an existing Amazon SNS topic when the application receives 10,000 requests from the same end-user IP address within any 5-minute period.
Which solution will meet these requirements?
- A . Configure CloudFront standard logging and CloudWatch Logs metric filters.
- B . Configure VPC Flow Logs and CloudWatch Logs metric filters.
- C . Configure an AWS WAF web ACL with an ASN match rule and CloudWatch alarms.
- D . Configure an AWS WAF web ACL with a rate-based rule. Associate it with CloudFront. Create a CloudWatch alarm to notify SNS.
D
Explanation:
AWS WAF rate-based rules are designed specifically to track the number of requests from a single IP address over a configurable time window. According to AWS Certified Security C Specialty guidance, rate-based rules integrate natively with CloudFront and emit CloudWatch metrics that can trigger alarms.
CloudFront logs and VPC Flow Logs are not real-time detection tools. ASN match rules do not count request rates.
Referenced AWS Specialty Documents:
AWS Certified Security C Specialty Official Study Guide
AWS WAF Rate-Based Rules
CloudFront and AWS WAF Integration
A company uses AWS Organizations and has an SCP at the root that prevents sharing resources with external accounts. The company now needs to allow only the marketing account to share resources externally while preventing all other accounts from doing so. All accounts are in the same OU.
Which solution will meet these requirements?
- A . Create a new SCP in the marketing account to explicitly allow sharing.
- B . Edit the existing SCP to add a condition that excludes the marketing account.
- C . Edit the SCP to include an Allow statement for the marketing account.
- D . Use a permissions boundary in the marketing account.
B
Explanation:
Service control policies (SCPs) define the maximum available permissions for accounts and are evaluated as guardrails. AWS Certified Security C Specialty documentation states SCPs are typically used to apply organization-wide restrictions, and exceptions are commonly handled by using conditions (for example, excluding specific accounts) or by structuring OUs differently. Because all accounts are in the same OU and the company must continue blocking external sharing for everyone except one account, modifying the existing SCP to exclude the marketing account is the most direct solution. An SCP attached at the root affects all accounts unless conditions narrow its scope. Adding a condition that excludes the marketing account allows that account to retain the ability to share resources externally while the SCP continues to block sharing for other accounts.
Option A is not feasible because account-level SCPs cannot override a deny applied by a parent SCP; explicit denies always win.
Option C misunderstands SCP behavior because SCPs do not grant permissions; they only limit.
Option D is an IAM control that cannot override an organization-level deny. Therefore, the only secure, scalable option is to modify the existing SCP with an exception condition for the marketing account.
Referenced AWS Specialty Documents:
AWS Certified Security C Specialty Official Study Guide
AWS Organizations SCP Evaluation Logic
SCP Deny Precedence and Exception Patterns
A company has a VPC that has no internet access and has the private DNS hostnames option enabled. An Amazon Aurora database is running inside the VPC. A security engineer wants to use AWS Secrets Manager to automatically rotate the credentials for the Aurora database. The security engineer configures the Secrets Manager default AWS Lambda rotation function to run inside the same VPC that the Aurora database uses. However, the security engineer determines that the password cannot be rotated properly because the Lambda function cannot communicate with the Secrets Manager endpoint.
What is the MOST secure way that the security engineer can give the Lambda function the ability to communicate with the Secrets Manager endpoint?
- A . Add a NAT gateway to the VPC to allow access to the Secrets Manager endpoint.
- B . Add a gateway VPC endpoint to the VPC to allow access to the Secrets Manager endpoint.
- C . Add an interface VPC endpoint to the VPC to allow access to the Secrets Manager endpoint.
- D . Add an internet gateway for the VPC to allow access to the Secrets Manager endpoint.
C
Explanation:
AWS Secrets Manager is a regional service that is accessed through private AWS endpoints. In a VPC without internet access, AWS recommends using AWS Private Link through interface VPC endpoints to enable secure, private connectivity to supported AWS services. According to AWS Certified Security C Specialty documentation, interface VPC endpoints allow resources within a VPC to communicate with AWS services without traversing the public internet, NAT devices, or internet gateways.
An interface VPC endpoint for Secrets Manager creates elastic network interfaces (ENIs) within the VPC subnets and assigns private IP addresses that route traffic directly to the Secrets Manager service. Because the VPC has private DNS enabled, the standard Secrets Manager DNS hostname resolves to the private IP addresses of the interface endpoint, allowing the Lambda rotation function to communicate securely and transparently.
Option A introduces unnecessary complexity and expands the attack surface by allowing outbound internet access.
Option B is incorrect because gateway VPC endpoints are supported only for Amazon S3 and Amazon DynamoDB.
Option D violates the security requirement by exposing the VPC to the internet.
AWS security best practices explicitly recommend interface VPC endpoints as the most secure connectivity method for private VPC workloads accessing AWS managed services.
Referenced AWS Specialty Documents:
AWS Certified Security C Specialty Official Study Guide
AWS Secrets Manager Security Architecture
AWS PrivateLink and Interface VPC Endpoints Documentation
CloudFormation stack deployments fail for some users due to permission inconsistencies.
Which combination of steps will ensure consistent deployments MOST securely? (Select THREE.)
- A . Create a composite principal service role.
- B . Create a service role with cloudformation.amazonaws.com as the principal.
- C . Attach scoped policies to the service role.
- D . Attach service ARNs in policy resources.
- E . Update each stack to use the service role.
- F . Allow iam:PassRole to the service role.
B, E, F
Explanation:
AWS best practices require CloudFormation to assume a dedicated service role. This ensures consistent permissions regardless of the user. Users must have iam:PassRole permission to pass the role. Updating stacks to use the service role enforces uniform deployment behavior.
Referenced AWS Specialty Documents:
AWS Certified Security C Specialty Official Study Guide
AWS CloudFormation Service Roles
A company has a single AWS account and uses an Amazon EC2 instance to test application code. The company recently discovered that the instance was compromised and was serving malware. Analysis showed that the instance was compromised 35 days ago. A security engineer must implement a continuous monitoring solution that automatically notifies the security team by email for high severity findings as soon as possible.
Which combination of steps should the security engineer take to meet these requirements? (Select THREE.)
- A . Enable AWS Security Hub in the AWS account.
- B . Enable Amazon GuardDuty in the AWS account.
- C . Create an Amazon Simple Notification Service (Amazon SNS) topic. Subscribe the security team’s email distribution list to the topic.
- D . Create an Amazon Simple Queue Service (Amazon SQS) queue. Subscribe the security team’s email distribution list to the queue.
- E . Create an Amazon EventBridge rule for GuardDuty findings of high severity. Configure the rule to publish a message to the topic.
- F . Create an Amazon EventBridge rule for Security Hub findings of high severity. Configure the rule to publish a message to the queue.
B, C, E
Explanation:
Amazon GuardDuty provides continuous threat detection for compromised instances by analyzing VPC Flow Logs, DNS logs, and CloudTrail events. According to AWS Certified Security C Specialty guidance, GuardDuty is the fastest service to enable for detecting malware and compromised EC2 instances.
To notify the security team, Amazon SNS provides a native email notification mechanism with minimal setup. Amazon EventBridge integrates directly with GuardDuty findings and can filter based on severity. Creating an EventBridge rule that matches high severity GuardDuty findings and publishes to SNS ensures immediate notification.
Security Hub is not required for this use case and adds additional setup time. Amazon SQS does not support email subscriptions.
Referenced AWS Specialty Documents:
AWS Certified Security C Specialty Official Study Guide
Amazon GuardDuty Findings and Severity
Amazon EventBridge Integration with GuardDuty
HOTSPOT
A security engineer needs to implement AWS IAM Identity Center with an external identity provider (IdP).
Select and order the correct steps from the following list to meet this requirement. Select each step one time or not at all. (Select and order THREE.)
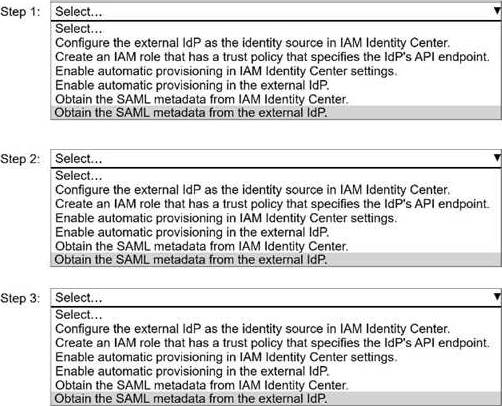
. Configure the external IdP as the identity source in IAM Identity Center.
. Create an IAM role that has a trust policy that specifies the IdP’s API endpoint.
. Enable automatic provisioning in IAM Identity Center settings.
. Enable automatic provisioning in the external IdP.
. Obtain the SAML metadata from IAM Identity Center.
. Obtain the SAML metadata from the external IdP.
Explanation:
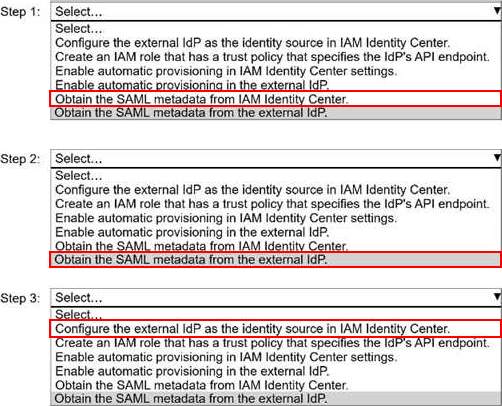
Step 1: Obtain the SAML metadata from IAM Identity Center.
Step 2: Obtain the SAML metadata from the external IdP.
Step 3: Configure the external IdP as the identity source in IAM Identity Center.
When integrating AWS IAM Identity Center (formerly AWS SSO) with an external identity provider (IdP) using SAML 2.0, AWS requires a specific sequence of steps to establish trust and federation correctly.
Step 1: Obtain the SAML metadata from IAM Identity Center
IAM Identity Center acts as the service provider (SP) in the SAML trust. The external IdP must trust IAM Identity Center, so the IdP needs IAM Identity Center’s SAML metadata first. This metadata contains critical information such as the SP entity ID, ACS (Assertion Consumer Service) URL, and signing certificate. Without this metadata, the external IdP cannot be configured to send assertions to AWS.
Step 2: Obtain the SAML metadata from the external IdP
After the external IdP is configured to trust IAM Identity Center, the IdP generates its own SAML metadata. This metadata includes the IdP entity ID, SSO endpoint, and signing certificate. IAM Identity Center requires this information to validate authentication assertions coming from the external IdP.
Step 3: Configure the external IdP as the identity source in IAM Identity Center
Once both metadata files are available, the security engineer configures the external IdP as the identity source in IAM Identity Center. At this stage, IAM Identity Center imports the IdP metadata and establishes the SAML trust relationship. After this configuration, users authenticated by the external IdP can be federated into AWS accounts and applications via IAM Identity Center.
Why the other options are incorrect:
Creating an IAM role with an IdP API endpoint is used for IAM federation, not IAM Identity Center.
Automatic provisioning (SCIM) is optional and is configured after SAML federation is established.
Automatic provisioning must be enabled on both sides, but it is not required to complete the core IdP integration.
This sequence follows AWS best practices for SAML-based federation with IAM Identity Center.
A company is running a containerized application on an Amazon Elastic Container Service (Amazon ECS) cluster that uses AWS Fargate. The application runs as several ECS services.
The ECS services are in individual target groups for an internet-facing Application Load Balancer (ALB). The ALB is the origin for an Amazon CloudFront distribution. An AWS WAF web ACL is associated with the CloudFront distribution.
Web clients access the ECS services through the CloudFront distribution. The company learns that the web clients can bypass the web ACL and can access the ALB directly.
Which solution will prevent the web clients from directly accessing the ALB?
- A . Create an AWS PrivateLink endpoint and set it as the CloudFront origin.
- B . Create a new internal ALB and delete the internet-facing ALB.
- C . Modify the ALB listener rules to allow only CloudFront IP ranges.
- D . Add a custom X-Shared-Secret header in CloudFront and configure the ALB listener rules to allow requests only when the header value matches.
D
Explanation:
When an internet-facing ALB is used as a CloudFront origin, it remains directly accessible unless additional access controls are enforced. According to AWS Certified Security C Specialty guidance, CloudFront IP allow lists alone are insufficient, because CloudFront IP ranges change and are not guaranteed to be exclusive.
The recommended and most secure approach is to configure CloudFront to send a custom origin header (such as X-Shared-Secret) with a secret value on every request to the origin. The ALB listener rules are then configured to forward traffic only when the header exists and matches the expected value. Requests that attempt to bypass CloudFront will not include this header and will be denied.
Option A is invalid because CloudFront does not support PrivateLink origins.
Option B introduces unnecessary architectural changes and is not required.
Option C is brittle and operationally risky due to changing IP ranges.
AWS documentation explicitly recommends custom origin headers as the best practice to ensure that only CloudFront can access an internet-facing ALB when AWS WAF is attached at the CloudFront layer.
AWS Certified Security C Specialty Official Study Guide
Amazon CloudFront Origin Security Documentation
AWS WAF and ALB Integration Guidance
