Practice Free SCS-C02 Exam Online Questions
A company deploys a set of standard IAM roles in AWS accounts. The IAM roles are based on job functions within the company. To balance operational efficiency and security, a security engineer implemented AWS Organizations SCPs to restrict access to critical security services in all company accounts.
All of the company’s accounts and OUs within AWS Organizations have a default FullAWSAccess SCP that is attached. The security engineer needs to ensure that no one can disable Amazon GuardDuty and AWS Security Hub. The security engineer also must not override other permissions that are granted by IAM policies that are defined in the accounts.
Which SCP should the security engineer attach to the root of the organization to meet these requirements?
A)
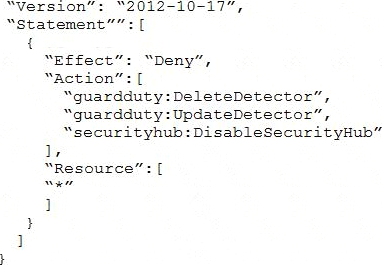
B)
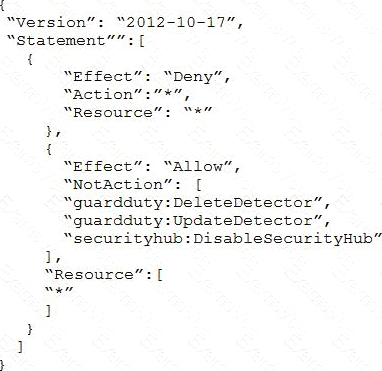
C)
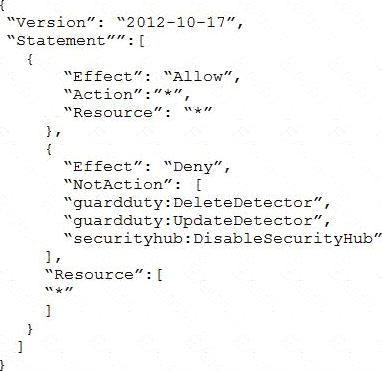
D)
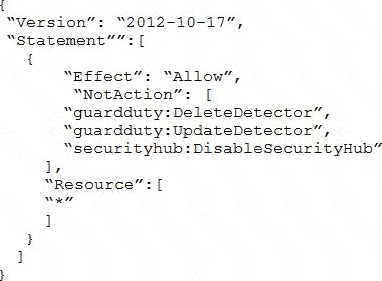
- A . Option A
- B . Option B
- C . Option C
- D . Option D
A company has an application on Amazon EC2 instances that store confidential customer data. The company must restrict access to customer data. A security engineer requires secure access to the instances that host the application. According to company policy, users must not open any inbound ports, maintain bastion hosts, or manage SSH keys for the EC2 instances.
The security engineer wants lo monitor, store, and access all session activity logs. The logs must be encrypted.
Which solution will meet these requirements?
- A . Use AWS Control Tower to connect to the EC2 instances. Configure Amazon CloudWatch logging for the sessions. Select the upload session logs option and allow only encrypted CloudWatch Logs log groups.
- B . Use AWS Security Hub to connect to the EC2 instances. Configure Amazon CloudWatch logging for the sessions. Select the upload session logs option and allow only encrypted CloudWatch Logs log groups.
- C . Use AWS Systems Manager Session Manager to connect to the EC2 instances. Configure Amazon CloudWatch monitoring to record the sessions. Select the store session logs option for the desired CloudWatch Logs log groups.
- D . Use AWS Systems Manager Session Manager to connect to the EC2 instances. Configure Amazon CloudWatch logging. Select the upload session logs option and allow only encrypted CloudWatch Logs log groups.
A company hosts multiple externally facing applications, each isolated in its own IAM account. The company’B Security team has enabled IAM WAF. IAM Config. and Amazon GuardDuty on all accounts. The company’s Operations team has also joined all of the accounts to IAM Organizations and established centralized logging for CloudTrail. IAM Config, and GuardDuty. The company wants the Security team to take a reactive remediation in one account, and automate implementing this remediation as proactive prevention in all the other accounts.
How should the Security team accomplish this?
- A . Update the IAM WAF rules in the affected account and use IAM Firewall Manager to push updated IAM WAF rules across all other accounts.
- B . Use GuardDuty centralized logging and Amazon SNS to set up alerts to notify all application teams of security incidents.
- C . Use GuardDuty alerts to write an IAM Lambda function that updates all accounts by adding additional NACLs on the Amazon EC2 instances to block known malicious IP addresses.
- D . Use IAM Shield Advanced to identify threats in each individual account and then apply the account-based protections to all other accounts through Organizations.
A company is deploying an Amazon EC2-based application. The application will include a custom health-checking component that produces health status data in JSON format. A Security Engineer must implement a secure solution to monitor application availability in near-real time by analyzing the hearth status data.
Which approach should the Security Engineer use?
- A . Use Amazon CloudWatch monitoring to capture Amazon EC2 and networking metrics Visualize metrics using Amazon CloudWatch dashboards.
- B . Run the Amazon Kinesis Agent to write the status data to Amazon Kinesis Data Firehose Store the streaming data from Kinesis Data Firehose in Amazon Redshift. (hen run a script on the pool data and analyze the data in Amazon Redshift
- C . Write the status data directly to a public Amazon S3 bucket from the health-checking component Configure S3 events to invoke an IAM Lambda function that analyzes the data
- D . Generate events from the health-checking component and send them to Amazon CloudWatch Events. Include the status data as event payloads. Use CloudWatch Events rules to invoke an IAM Lambda function that analyzes the data.
A security engineer needs to configure an Amazon S3 bucket policy to restrict access to an S3 bucket that is named DOC-EXAMPLE-BUCKET. The policy must allow access to only DOC-EXAMPLE-BUCKET from only the following endpoint: vpce-1a2b3c4d. The policy must deny all access to DOC-EXAMPLE-BUCKET if the specified endpoint is not used.
Which bucket policy statement meets these requirements?
A)
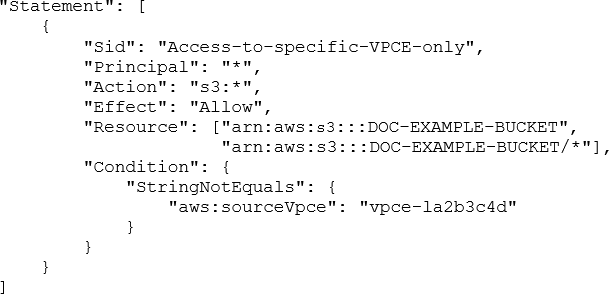
B)
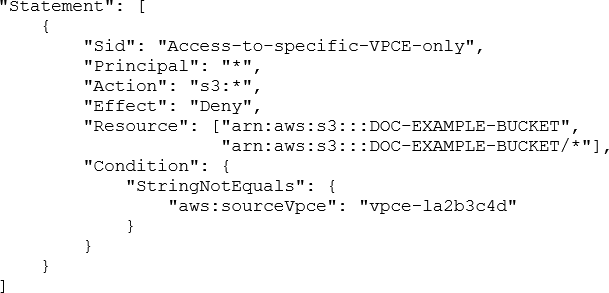
C)
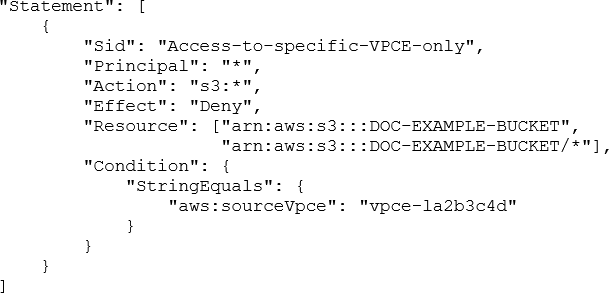
D)
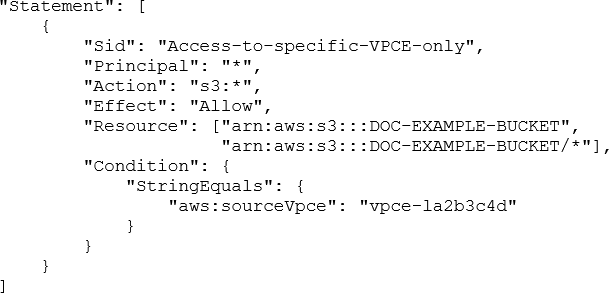
- A . Option A
- B . Option B
- C . Option C
- D . Option D
B
Explanation:
https://docs.aws.amazon.com/AmazonS3/latest/userguide/example-bucket-policies-vpc-endpoint.html
A company has a new web-based account management system for an online game Players create a unique username and password to log in to the system.
The company has implemented an AWS WAF web ACL for the system. The web ACL includes the core rule set (CRS) AWS managed rule group on the Application Load Balancer that serves the system. The company’s security team finds that the system was the target of a credential stuffing attack Credentials that were exposed in other breaches were used to try to log in to the system
The security team must implement a solution to reduce the chance of a successful credential stuffing attack in the future The solution also must minimize impact on legitimate users of the system Which combination of actions will meet these requirements? (Select TWO.)
- A . Create an Amazon CloudWatch custom metric to analyze the number of successful login responses from a single IP address
- B . Add the account takeover prevention (ATP) AWS managed rule group to the web ACL Configure the rule group to inspect login requests to the system Block any requests that have the awswaf managed awsatp signal credential_compromised label
- C . Configure a default web ACL action that requires all users to solve a CAPTCHA puzzle when they log in
- D . Implement IP-based match rules in the web ACL for any IP addresses that generate many successful login responses Block any IP addresses that generate many successful logins
- E . Create a custom block response that redirects users to a secure workflow to reset their password inside the system
A company wants to migrate its static primary domain website to AWS. The company hosts the website and DNS servers internally. The company wants the website to enforce SSL/TLS encryption block IP addresses from outside the United States (US), and take advantage of managed services whenever possible.
Which solution will meet these requirements?
- A . Migrate the website to Amazon S3 Import a public SSL certificate to an Application Load. Balancer with rules to block traffic from outside the US Migrate DNS to Amazon Route 53.
- B . Migrate the website to Amazon EC2 Import a public SSL certificate that is created by AWS Certificate Manager (ACM) to an Application Load Balancer with rules to block traffic from outside the US Update DNS accordingly.
- C . Migrate the website to Amazon S3. Import a public SSL certificate to Amazon CloudFront Use AWS WAF rules to block traffic from outside the US Update DNS. accordingly
- D . Migrate the website to Amazon S3 Import a public SSL certificate that is created by AWS Certificate Manager (ACM) to Amazon. CloudFront Configure CloudFront to block traffic from outside the US. Migrate DNS to Amazon Route 53.
D
Explanation:
To migrate the static website to AWS and meet the requirements, the following steps are required:
Migrate the website to Amazon S3, which is a highly scalable and durable object storage service that can host static websites. To do this, create an S3 bucket with the same name as the domain name of the website, enable static website hosting for the bucket, upload the website files to the bucket, and configure the bucket policy to allow public read access to the objects. For more information, see Hosting a static website on Amazon S3.
Import a public SSL certificate that is created by AWS Certificate Manager (ACM) to Amazon CloudFront, which is a global content delivery network (CDN) service that can improve the performance and security of web applications. To do this, request or import a public SSL certificate for the domain name of the website using ACM, create a CloudFront distribution with the S3 bucket as the origin, and associate the SSL certificate with the distribution. For more information, see Using alternate domain names and HTTPS.
Configure CloudFront to block traffic from outside the US, which is one of the requirements. To do this, create a CloudFront web ACL using AWS WAF, which is a web application firewall service that lets you control access to your web applications. In the web ACL, create a rule that uses a geo match condition to block requests that originate from countries other than the US. Associate the web ACL with the CloudFront distribution. For more information, see How AWS WAF works with Amazon CloudFront features.
Migrate DNS to Amazon Route 53, which is a highly available and scalable cloud DNS service that can route traffic to various AWS services. To do this, register or transfer your domain name to Route 53, create a hosted zone for your domain name, and create an alias record that points your domain name to your CloudFront distribution. For more information, see Routing traffic to an Amazon CloudFront web distribution by using your domain name.
The other options are incorrect because they either do not implement SSL/TLS encryption for the website (A), do not use managed services whenever possible (B), or do not block IP addresses from outside the US ©.
Verified References:
https://docs.aws.amazon.com/AmazonS3/latest/userguide/HostingWebsiteOnS3Setup.html
https://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/using-https-alternate-domain-na
https://docs.aws.amazon.com/waf/latest/developerguide/waf-cloudfront.html
https://docs.aws.amazon.com/Route53/latest/DeveloperGuide/routing-to-cloudfront-distribution.html
A company that uses AWS Organizations is migrating workloads to AWS. The companys application team determines that the workloads will use Amazon EC2 instances, Amazon S3 buckets, Amazon DynamoDB tables, and Application Load Balancers.
For each resource type, the company mandates that deployments must comply with the following requirements:
• All EC2 instances must be launched from approved AWS accounts.
• All DynamoDB tables must be provisioned with a standardized naming convention.
• All infrastructure that is provisioned in any accounts in the organization must be deployed by AWS CloudFormation templates.
Which combination of steps should the application team take to meet these requirements? (Select TWO.)
- A . Create CloudFormation templates in an administrator AWS account. Share the stack sets with an application AWS account. Restrict the template to be used specifically by the application AWS account.
- B . Create CloudFormation templates in an application AWS account. Share the output with an administrator AWS account to review compliant resources. Restrict output to only the administrator AWS account.
- C . Use permissions boundaries to prevent the application AWS account from provisioning specific resources unless conditions for the internal compliance requirements are met.
- D . Use SCPs to prevent the application AWS account from provisioning specific resources unless conditions for the internal compliance requirements are met.
- E . Activate AWS Config managed rules for each service in the application AWS account.
A company has a relational database workload that runs on Amazon Aurora MySQL. According to new compliance standards the company must rotate all database credentials every 30 days. The company needs a solution that maximizes security and minimizes development effort.
Which solution will meet these requirements?
- A . Store the database credentials in AWS Secrets Manager. Configure automatic credential rotation tor every 30 days.
- B . Store the database credentials in AWS Systems Manager Parameter Store. Create an AWS Lambda function to rotate the credentials every 30 days.
- C . Store the database credentials in an environment file or in a configuration file. Modify the credentials every 30 days.
- D . Store the database credentials in an environment file or in a configuration file. Create an AWS Lambda function to rotate the credentials every 30 days.
A
Explanation:
To rotate database credentials every 30 days, the most secure and efficient solution is to store the database credentials in AWS Secrets Manager and configure automatic credential rotation for every 30 days. Secrets Manager can handle the rotation of the credentials in both the secret and the database, and it can use AWS KMS to encrypt the credentials. Option B is incorrect because it requires creating a custom Lambda function to rotate the credentials, which is more effort than using Secrets Manager. Option C is incorrect because it stores the database credentials in an environment file or a configuration file, which is less secure than using Secrets Manager. Option D is incorrect because it combines the drawbacks of option B and option C.
Verified References:
https://docs.aws.amazon.com/secretsmanager/latest/userguide/rotating-secrets.html
https://docs.aws.amazon.com/secretsmanager/latest/userguide/rotate-secrets_turn-on-for-other.html
A company runs a cuslom online gaming application. The company uses Amazon Cognito for user authentication and authorization.
A security engineer wants to use AWS to implement fine-grained authorization on resources in the custom application. The security engineer must implement a solution that uses the user attributes that exist in Cognito. The company has already set up a user pool and an identity pool in Cognito.
Which solution will meet these requirements?
- A . Create a set of 1AM roles and 1AM policies Configure the Cognito identity pool to assign users to the 1AM roles.
- B . Create a policy store in Amazon Verified Permissions. Configure Cognito as the identity source Map Cognito access tokens to the Verified Permissions schema.
- C . Create customer managed permissions by using AWS Resource Access Manager (AWS RAM) Configure the Cognito identity pool to assign users to the customer managed permissions
- D . Create a set of 1AM users and 1AM policies. Configure the Cognito user pool to assign users to the 1AM users.
