Practice Free SCS-C02 Exam Online Questions
A company wants to create a log analytics solution for logs generated from its on-premises devices. The logs are collected from the devices onto a server on premises. The company wants to use AWS services to perform near real-time log analysis. The company also wants to store these logs for 365 days for pattern matching and substring search capabilities later.
Which solution will meet these requirements with the LEAST development overhead?
- A . Install Amazon Kinesis Agent on the on-premises server to send the logs to Amazon DynamoDB.
Configure an AWS Lambda trigger on DynamoDB streams to perform near real-time log analysis. Export the DynamoDB data to Amazon S3 periodically. Run Amazon Athena queries for pattern matching and substring search. Set up S3 Ufecycle policies to delete the log data after 365 days. - B . Install Amazon Managed Streaming for Apache Kafka (Amazon MSK) on the on-premises server. Create an MSK cluster to collect the streaming data and analyze the data in real time. Set the data retention period to 365 days to store the logs persistently for pattern matching and substring search.
- C . Install Amazon Kinesis Agent on the on-premises server to send the logs to Amazon Data Firehose. Configure Amazon Managed Service for Apache Flink (previously known as Amazon Kinesis Data Analytics) as the destination for real-time processing. Store the logs in Amazon OpenSearch Service for pattern matching and substring search. Configure an OpenSearch Service Index State Management (ISM) policy to delete the data after 365 days.
- D . Use Amazon API Gateway and AWS Lambda to write the logs from the on-premises server to Amazon DynamoDB. Configure a Lambda trigger on DynamoDB streams to perform near real-time log analysis. Run Amazon Athena federated queries on DynamoDB data for pattern matching and substring search. Set up TTL to delete data after 365 days.
A company needs to retain tog data archives for several years to be compliant with regulations. The tog data is no longer used but It must be retained
What Is the MOST secure and cost-effective solution to meet these requirements?
- A . Archive the data to Amazon S3 and apply a restrictive bucket policy to deny the s3 DeleteOotect API
- B . Archive the data to Amazon S3 Glacier and apply a Vault Lock policy
- C . Archive the data to Amazon S3 and replicate it to a second bucket in a second IAM Region Choose the S3 Standard-Infrequent Access (S3 Standard-1A) storage class and apply a restrictive bucket policy to deny the s3 DeleteObject API
- D . Migrate the log data to a 16 T8 Amazon Elastic Block Store (Amazon EBS) volume Create a snapshot of the EBS volume
A Security Engineer has been tasked with enabling IAM Security Hub to monitor Amazon EC2 instances fix CVE in a single IAM account The Engineer has already enabled IAM Security Hub and Amazon Inspector m the IAM Management Console and has installed me Amazon Inspector agent on an EC2 instances that need to be monitored.
Which additional steps should the Security Engineer lake 10 meet this requirement?
- A . Configure the Amazon inspector agent to use the CVE rule package
- B . Configure the Amazon Inspector agent to use the CVE rule package Configure Security Hub to ingest from IAM inspector by writing a custom resource policy
- C . Configure the Security Hub agent to use the CVE rule package Configure IAM Inspector lo ingest from Security Hub by writing a custom resource policy
- D . Configure the Amazon Inspector agent to use the CVE rule package Install an additional Integration library Allow the Amazon Inspector agent to communicate with Security Hub
A company uses infrastructure as code (IaC) to create AWS infrastructure. The company writes the code as AWS CloudFormation templates to deploy the infrastructure. The company has an existing CI/CD pipeline that the company can use to deploy these templates.
After a recent security audit, the company decides to adopt a policy-as-code approach to improve the company’s security posture on AWS. The company must prevent the deployment of any infrastructure that would violate a security policy, such as an unencrypted Amazon Elastic Block Store (Amazon EBS) volume.
Which solution will meet these requirements?
- A . Turn on AWS Trusted Advisor. Configure security notifications as webhooks in the preferences section of the CI/CD pipeline.
- B . Turn on AWS Config. Use the prebuilt rules or customized rules. Subscribe the CI/CD pipeline to an Amazon Simple Notification Service (Amazon SNS) topic that receives notifications from AWS Config.
- C . Create rule sets in AWS CloudFormation Guard. Run validation checks for CloudFormation templates as a phase of the CI/CD process.
- D . Create rule sets as SCPs. Integrate the SCPs as a part of validation control in a phase of the CI/CD process.
C
Explanation:
The correct answer is C. Create rule sets in AWS CloudFormation Guard. Run validation checks for CloudFormation templates as a phase of the CI/CD process.
This answer is correct because AWS CloudFormation Guard is a tool that helps you implement policy-as-code for your CloudFormation templates. You can use Guard to write rules that define your security policies, such as requiring encryption for EBS volumes, and then validate your templates against those rules before deploying them. You can integrate Guard into your CI/CD pipeline as a step that runs the validation checks and prevents the deployment of any non-compliant templates12.
The other options are incorrect because:
A) Turning on AWS Trusted Advisor and configuring security notifications as webhooks in the preferences section of the CI/CD pipeline is not a solution, because AWS Trusted Advisor is not a policy-as-code tool, but a service that provides recommendations to help you follow AWS best practices. Trusted Advisor does not allow you to define your own security policies or validate your CloudFormation templates against them3.
B) Turning on AWS Config and using the prebuilt or customized rules is not a solution, because AWS Config is not a policy-as-code tool, but a service that monitors and records the configuration changes of your AWS resources. AWS Config does not allow you to validate your CloudFormation templates before deploying them, but only evaluates the compliance of your resources after they are created4.
D) Creating rule sets as SCPs and integrating them as a part of validation control in a phase of the CI/CD process is not a solution, because SCPs are not policy-as-code tools, but policies that you can use to manage permissions in your AWS Organizations. SCPs do not allow you to validate your CloudFormation templates, but only restrict the actions that users and roles can perform in your accounts5.
Reference: 1: What is AWS CloudFormation Guard?
2: Introducing AWS CloudFormation Guard 2.0
3: AWS Trusted Advisor
4: What Is AWS Config?
5: Service control policies – AWS Organizations
A company needs a security engineer to implement a scalable solution for multi-account authentication and authorization. The solution should not introduce additional user-managed architectural components. Native IAM features should be used as much as possible. The security engineer has set up IAM Organizations w1th all features activated and IAM SSO enabled.
Which additional steps should the security engineer take to complete the task?
- A . Use AD Connector to create users and groups for all employees that require access to IAM accounts. Assign AD Connector groups to IAM accounts and link to the IAM roles in accordance with the employees‘job functions and access requirements Instruct employees to access IAM accounts by using the IAM Directory Service user portal.
- B . Use an IAM SSO default directory to create users and groups for all employees that require access to IAM accounts. Assign groups to IAM accounts and link to permission sets in accordance with the employees‘job functions and access requirements. Instruct employees to access IAM accounts by using the IAM SSO user portal.
- C . Use an IAM SSO default directory to create users and groups for all employees that require access to IAM accounts. Link IAM SSO groups to the IAM users present in all accounts to inherit existing permissions. Instruct employees to access IAM accounts by using the IAM SSO user portal.
- D . Use IAM Directory Service tor Microsoft Active Directory to create users and groups for all employees that require access to IAM accounts Enable IAM Management Console access in the created directory and specify IAM SSO as a source cl information tor integrated accounts and permission sets. Instruct employees to access IAM accounts by using the IAM Directory Service user portal.
A company is storing data in Amazon S3 Glacier. A security engineer implemented a new vault lock policy for 10 TB of data and called the initiate-vault-lock operation 12 hours ago. The audit team identified a typo in the policy that is allowing unintended access to the vault.
What is the MOST cost-effective way to correct this error?
- A . Call the abort-vault-lock operation. Update the policy. Call the initiate-vault-lock operation again.
- B . Copy the vault data to a new S3 bucket. Delete the vault. Create a new vault with the data.
- C . Update the policy to keep the vault lock in place
- D . Update the policy. Call the initiate-vault-lock operation again to apply the new policy.
A
Explanation:
The most cost-effective way to correct a typo in a vault lock policy during the 24-hour initiation period is to call the abort-vault-lock operation. This action stops the vault lock process, allowing the security engineer to correct the policy and re-initiate the vault lock with the corrected policy. This approach avoids the need for data transfer or creating a new vault, thus minimizing costs and operational overhead.
A developer signed in to a new account within an IAM Organization organizational unit (OU) containing multiple accounts.
Access to the Amazon $3 service is restricted with the following SCP.
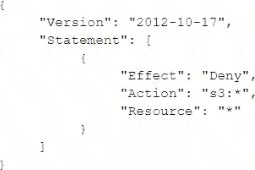
How can the security engineer provide the developer with Amazon $3 access without affecting other account?
- A . Move the SCP to the root OU of organization to remove the restriction to access Amazon $3.
- B . Add an IAM policy for the developer, which grants $3 access.
- C . Create a new OU without applying the SCP restricting $3 access. Move the developer account to this new OU.
- D . Add an allow list for the developer account for the $3 service.
You need to create a policy and apply it for just an individual user.
How could you accomplish this in the right way?
- A . Add an IAM managed policy for the user
- B . Add a service policy for the user
- C . Add an IAM role for the user
- D . Add an inline policy for the user
D
Explanation:
Options A and B are incorrect since you need to add an inline policy just for the user
Option C is invalid because you don’t assign an IAM role to a user
The IAM Documentation mentions the following
An inline policy is a policy that’s embedded in a principal entity (a user, group, or role)―that is, the policy is an inherent part of the principal entity. You can create a policy and embed it in a principal entity, either when you create the principal entity or later.
For more information on IAM Access and Inline policies, just browse to the below URL:
https://docs.IAM.amazon.com/IAM/latest/UserGuide/access
The correct answer is: Add an inline policy for the user Submit your Feedback/Queries to our Experts
A company’s Security Team received an email notification from the Amazon EC2 Abuse team that one or more of the company’s Amazon EC2 instances may have been compromised
Which combination of actions should the Security team take to respond to (be current modem? (Select TWO.)
- A . Open a support case with the IAM Security team and ask them to remove the malicious code from the affected instance
- B . Respond to the notification and list the actions that have been taken to address the incident
- C . Delete all IAM users and resources in the account
- D . Detach the internet gateway from the VPC remove aft rules that contain 0.0.0.0V0 from the security groups, and create a NACL rule to deny all traffic Inbound from the internet
- E . Delete the identified compromised instances and delete any associated resources that the Security team did not create.
A company is running internal microservices on Amazon Elastic Container Service (Amazon ECS) with the Amazon EC2 launch type. The company is using Amazon Elastic Container Registry (Amazon ECR) private repositories.
A security engineer needs to encrypt the private repositories by using AWS Key Management Service (AWS KMS). The security engineer also needs to analyze the container images for any common vulnerabilities and exposures (CVEs).
Which solution will meet these requirements?
- A . Enable KMS encryption on the existing ECR repositories. Install Amazon Inspector Agent from the ECS container instances’ user data. Run an assessment with the CVE rules.
- B . Recreate the ECR repositories with KMS encryption and ECR scanning enabled. Analyze the scan report after the next push of images.
- C . Recreate the ECR repositories with KMS encryption and ECR scanning enabled. Install AWS Systems
Manager Agent on the ECS container instances. Run an inventory report. - D . Enable KMS encryption on the existing ECR repositories. Use AWS Trusted Advisor to check the ECS container instances and to verily the findings against a list of current CVEs.
