Practice Free SC-100 Exam Online Questions
Your company has a hybrid cloud infrastructure.
The company plans to hire several temporary employees within a brief period. The temporary employees will need to access applications and data on the company’ premises network.
The company’s security policy prevents the use of personal devices for accessing company data and applications.
You need to recommend a solution to provide the temporary employee with access to company
resources. The solution must be able to scale on demand.
What should you include in the recommendation?
- A . Migrate the on-premises applications to cloud-based applications.
- B . Redesign the VPN infrastructure by adopting a split tunnel configuration.
- C . Deploy Microsoft Endpoint Manager and Azure Active Directory (Azure AD) Conditional Access.
- D . Deploy Azure Virtual Desktop, Azure Active Directory (Azure AD) Conditional Access, and Microsoft Defender for Cloud Apps.
D
Explanation:
https://docs.microsoft.com/en-us/azure/architecture/example-scenario/wvd/windows-virtual-desktop
https://docs.microsoft.com/en-us/azure/virtual-desktop/security-guide
https://techcommunity.microsoft.com/t5/security-compliance-and-identity/announcing-microsoft-defender-for-cloud-apps/ba-p/2835842
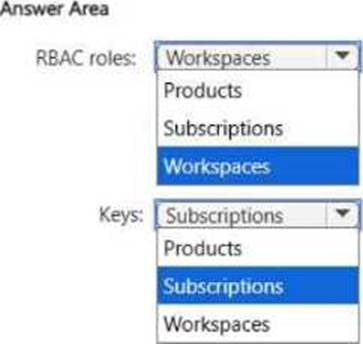
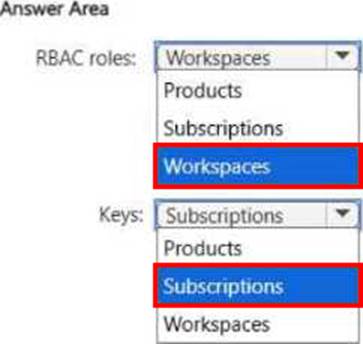
HOTSPOT
You have an Azure subscription.
You need to use a federated model in Azure API Management to control access to your organization’s
APIs.
The solution must meet the following requirements:
• Support the use of role-based access control (RBAC) to manage the APIs.
• Support the use of keys to control the consumption of the APIs.
To which scope should you associate each control method? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription and a Microsoft 365 subscription.
Your company uses several software as a service (SaaS) applications.
To align with Microsoft cloud security benchmark (MCSB) and Microsoft Cybersecurity Reference Architectures (MCRA), you plan to design a solution to provide visibility into user activity across the applications and detect potentially risky behavior in real time.
Which service should you recommend?
- A . Microsoft Purview Information Protection
- B . Microsoft Defender for Cloud Apps
- C . Microsoft Defender for Endpoint
- D . Microsoft Sentinel
You have an Azure subscription that contains 100 virtual machines, a virtual network named VNet1, and 20 users. The virtual machines run Windows Server and are connected to VNet1. The users work remotely and access Azure resources from Linux workstations.
You need to ensure that the users can connect to the virtual machines from the workstations by using
Secure Shell {SSH).
The solution must meet the following requirements:
• Ensure that the users authenticate by using their Microsoft Entra credentials.
• Prevent the users from transferring files from the virtual machines by using SSH.
• Prevent the users from directly accessing the virtual machines by using the public IP address of the virtual machines.
What should you include in the solution?
- A . Azure Bastion
- B . Azure NAT Gateway
- C . just-in-time (JIT) VM access
- D . Point-to-Site (P2S) VPN
DRAG DROP
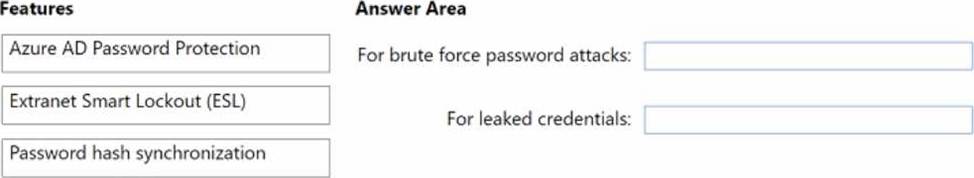
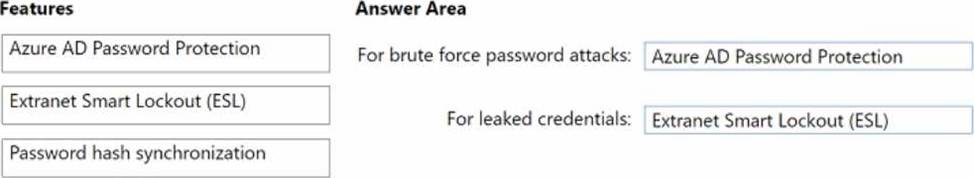
You have a hybrid Azure AD tenant that has pass-through authentication enabled.
You are designing an identity security strategy.
You need to minimize the impact of brute force password attacks and leaked credentials of hybrid identities.
What should you include in the design? To answer, drag the appropriate features to the correct requirements. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.