Practice Free SC-100 Exam Online Questions
Note: This section contains one or more sets of questions with the same scenario and problem. Each question presents a unique solution to the problem. You must determine whether the solution meets the stated goals. More than one solution in the set might solve the problem. It is also possible that none of the solutions in the set solve the problem.
After you answer a question in this section, you will NOT be able to return. As a result, these questions do not appear on the Review Screen.
You have a Microsoft 365 subscription that uses Microsoft Defender XDR. The subscription contains 500 devices that are enrolled in Microsoft Intune. The subscription contains 500 users that connect to external software as a service (SaaS) apps by using the devices.
You need to implement a solution that meets the following requirements:
• Allows user access to SaaS apps that Microsoft has identified as low risk.
• Blocks user access to Saas apps that Microsoft has identified as high risk.
Solution: From Microsoft Defender for Cloud Apps, you configure a cloud discovery policy and unsanction risky apps.
Does this meet the goal?
- A . Yes
- B . No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points.
You need to recommend configurations to increase the score of the Secure management ports controls.
Solution: You recommend enabling the VMAccess extension on all virtual machines.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
https://docs.microsoft.com/en-us/security/benchmark/azure/security-controls-v3-privileged-access#pa-2-avoid-standing-access-for-user-accounts-and-permissions
Adaptive Network Hardening: https://docs.microsoft.com/en-us/security/benchmark/azure/security-controls-v3-network-security#ns-7-simplify-network-security-configuration
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled.
The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019.
You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application.
Which security control should you recommend?
- A . app discovery anomaly detection policies in Microsoft Defender for Cloud Apps
- B . adaptive application controls in Defender for Cloud
- C . Azure Security Benchmark compliance controls m Defender for Cloud
- D . app protection policies in Microsoft Endpoint Manager
B
Explanation:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/recommendations-reference#compute-recommendations
HOTSPOT
You are designing an auditing solution for Azure landing zones that will contain the following components:
• SQL audit logs for Azure SQL databases
• Windows Security logs from Azure virtual machines
• Azure App Service audit logs from App Service web apps
You need to recommend a centralized logging solution for the landing zones.
The solution must meet the following requirements:
• Log all privileged access.
• Retain logs for at least 365 days.
• Minimize costs.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
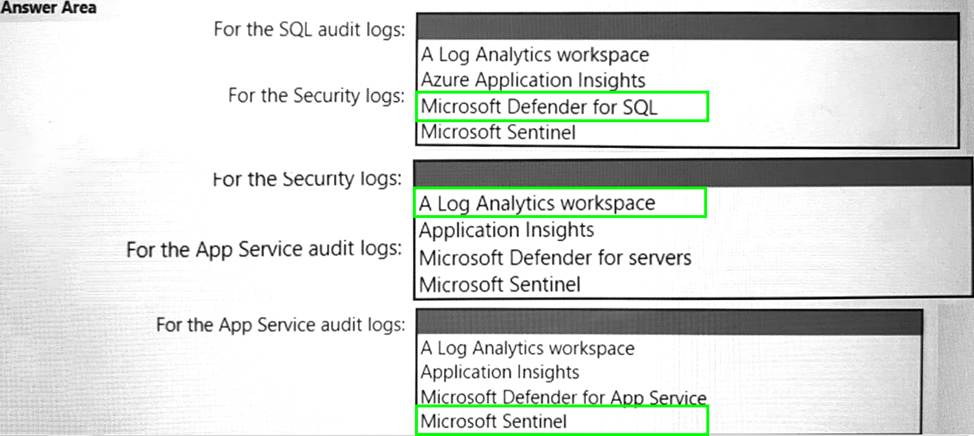
Explanation:
Microsoft Defender for SQL
A Log Analytics workspace
Microsoft Sentinel
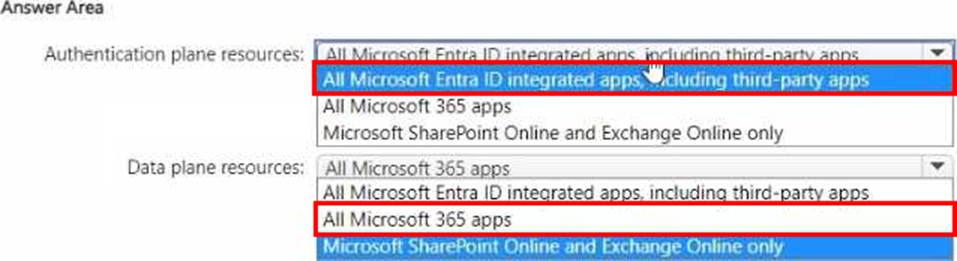
HOTSPOT
You have a Microsoft 365 E5 subscription.
You plan to deploy Global Secure Access universal tenant restrictions v2.
Which authentication plane resources and which data plane resources will be protected? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription.
Your company has a governance requirement that resources must be created in the West Europe or North Europe Azure regions.
What should you recommend using to enforce the governance requirement?
- A . regulatory compliance standards in Microsoft Defender for Cloud
- B . custom Azure roles
- C . Azure Policy assignments
- D . Azure management groups
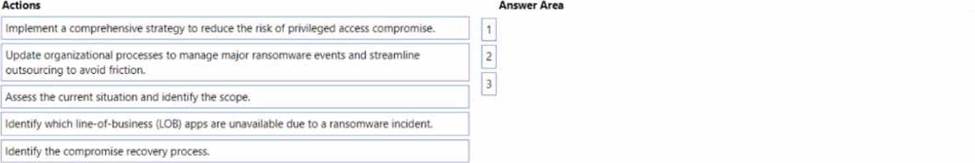
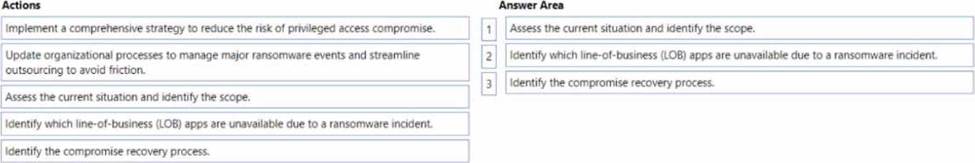
DRAG DROP
Your company wants to optimize ransomware incident investigations.
You need to recommend a plan to investigate ransomware incidents based on the Microsoft Detection and Response Team (DART) approach.
Which three actions should you recommend performing in sequence in the plan? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
A customer uses Azure to develop a mobile app that will be consumed by external users as shown in the following exhibit.
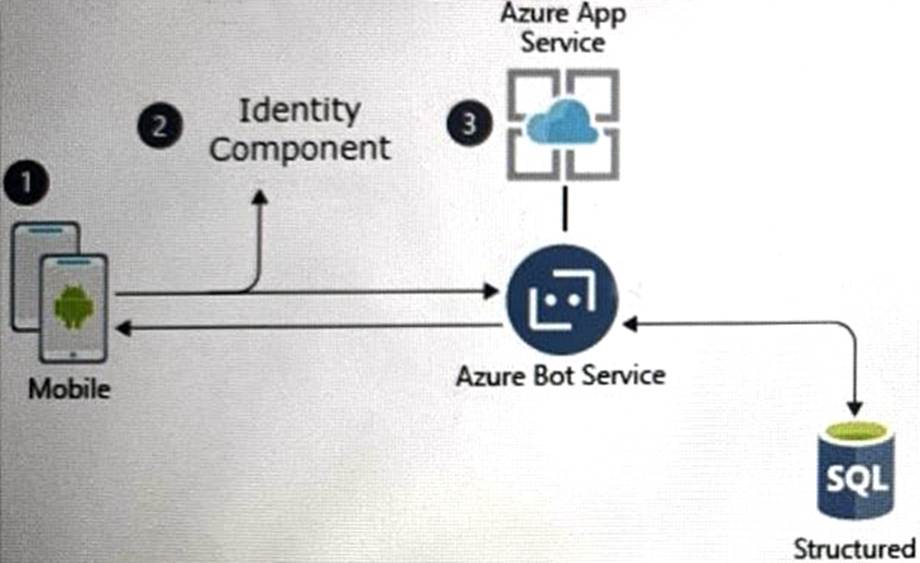
You need to design an identity strategy for the app.
The solution must meet the following requirements:
• Enable the usage of external IDs such as Google, Facebook, and Microsoft accounts.
• Be managed separately from the identity store of the customer.
• Support fully customizable branding for each app.
Which service should you recommend to complete the design?
- A . Azure Active Directory (Azure AD) B2C
- B . Azure Active Directory (Azure AD) B2B
- C . Azure AD Connect
- D . Azure Active Directory Domain Services (Azure AD DS)
A
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory-b2c/identity-provider-facebook?pivots=b2c-user-flow
https://docs.microsoft.com/en-us/azure/active-directory-b2c/customize-ui-with-html?pivots=b2c-user-flow
HOTSPOT
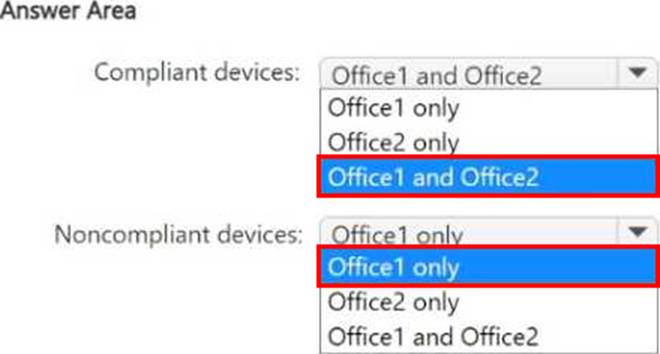
Your company has two offices named Office1 and Office2. The offices contain 1,000 on-premises Windows 11 devices that are Microsoft Entra joined.
You have a Microsoft 365 subscription and use Microsoft Intune.
You plan to deploy Microsoft Entra Internet Access from the offices to Microsoft 365.
You enable the Microsoft 365 profile and configure the following:
• A traffic policy for all Microsoft 365 traffic
• A linked Conditional Access policy that has the following configurations:
° Applies to all users
° Performs compliant network checks
o Allows Microsoft 365 traffic from compliant devices
• An assignment to all devices
• An assignment to the remote network associated with Office1
You deploy the Global Secure Access client to all the devices in Office2 and establish connections.
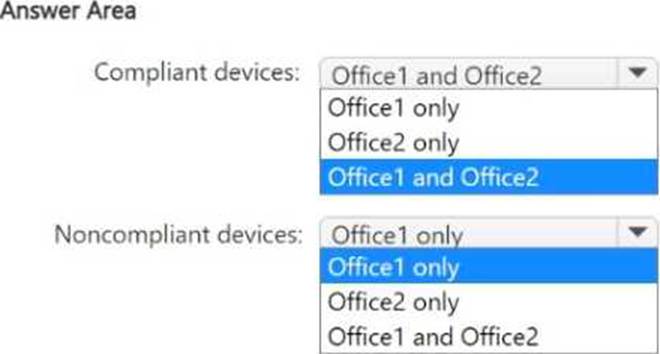
Which users can access Microsoft 365 services from compliant devices, and which users are blocket1 from accessing Microsoft 365 services when using noncompliar devices? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription and a Microsoft 365 subscription. All users are assigned Microsoft 365 E5 licenses. All computers run Windows 11 and are Microsoft Entra joined.
You need to recommend a solution to prevent computers that run early builds of Windows 11 from connecting to Microsoft 365 services.
Which two types of policies should you include in the recommendation? Each correct answer presents part of the solution.
- A . Microsoft Defender for Cloud regulatory compliance policy
- B . Microsoft Defender for Endpoint endpoint security policy
- C . Microsoft Entra ID Protection sign-in risk policy
- D . Microsoft Entra Conditional Access policy
- E . Microsoft Intune compliance policy
