Practice Free SC-100 Exam Online Questions
You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend configuring gateway-required virtual network integration.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
https://docs.microsoft.com/en-us/azure/app-service/app-service-ip-restrictions#restrict-access-to-a-specific-azure-front-door-instance
Your on-premises network contains an e-commerce web app that was developed in Angular and Nodejs. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.
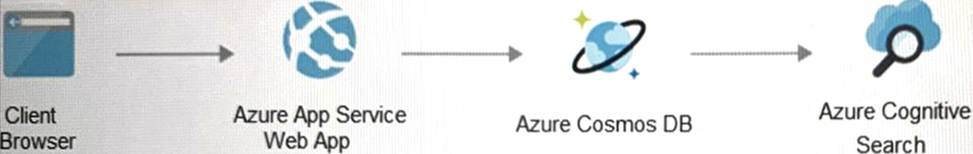
You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model.
Solution: You recommend implementing Azure Key Vault to store credentials.
- A . Yes
- B . No
B
Explanation:
When using Azure-provided PaaS services (e.g., Azure Storage, Azure Cosmos DB, or Azure Web App, use the PrivateLink connectivity option to ensure all data exchanges are over the private IP space and the traffic never leaves the Microsoft network.
You are designing the security standards for a new Azure environment.
You need to design a privileged identity strategy based on the Zero Trust model.
Which framework should you follow to create the design?
- A . Enhanced Security Admin Environment (ESAE)
- B . Microsoft Security Development Lifecycle (SDL)
- C . Rapid Modernization Plan (RaMP)
- D . Microsoft Operational Security Assurance (OSA)
C
Explanation:
https://docs.microsoft.com/en-us/security/compass/security-rapid-modernization-plan
This rapid modernization plan (RAMP) will help you quickly adopt Microsoft’s recommended privileged access strategy.
You have legacy operational technology (OT) devices and loT devices.
You need to recommend best practices for applying Zero Trust principles to the OT and loT devices based on the Microsoft Cybersecurity Reference Architectures (MCRA). The solution must minimize the risk of disrupting business operations.
Which two security methodologies should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point
- A . passive traffic monitoring
- B . active scanning
- C . threat monitoring
- D . software patching
You are designing a ransomware response plan that follows Microsoft Security Best Practices.
You need to recommend a solution to limit the scope of damage of ransomware attacks without being locked out.
What should you include in the recommendations?
- A . Privileged Access Workstations (PAWs)
- B . emergency access accounts
- C . device compliance policies
- D . Customer Lockbox for Microsoft Azure
You have a customer that has a Microsoft 365 subscription and uses the Free edition of Azure Active Directory (Azure AD)
The customer plans to obtain an Azure subscription and provision several Azure resources.
You need to evaluate the customer’s security environment.
What will necessitate an upgrade from the Azure AD Free edition to the Premium edition?
- A . role-based authorization
- B . Azure AD Privileged Identity Management (PIM)
- C . resource-based authorization
- D . Azure AD Multi-Factor Authentication
D
Explanation:
(https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure)
https://www.microsoft.com/en-us/security/business/identity-access/azure-active-directory-pricing?rtc=1
Your company has a Microsoft 365 subscription and uses Microsoft Defender for Identity.
You are informed about incidents that relate to compromised identities.
You need to recommend a solution to expose several accounts for attackers to exploit. When the attackers attempt to exploit the accounts, an alert must be triggered.
Which Defender for Identity feature should you include in the recommendation?
- A . standalone sensors
- B . honeytoken entity tags
- C . sensitivity labels
- D . custom user tags
B
Explanation:
https://docs.microsoft.com/en-us/advanced-threat-analytics/suspicious-activity-guide#honeytoken-activity
The Sensitive tag is used to identify high value assets. (user / devices / groups) Honeytoken entities are used as traps for malicious actors. Any authentication associated with these honeytoken entities triggers an alert. and Defender for Identity considers Exchange servers as high-value assets and automatically tags them as Sensitive
Your on-premises network contains an Active Directory Domain Services (AD DS) domain. The domain contains 500 Windows 11 devices.
You have a Microsoft 365 subscription and an Azure subscription.
You have a Microsoft Entra tenant that syncs with the domain and is linked to the subscriptions. The devices are Microsoft Entra hybrid joined.
You plan to deploy a solution to mitigate attacks against privileged accounts. The solution will include Microsoft Sentinel rules that will detect attempts to use fake cached credentials.
You need to recommend a solution to create the fake cached credentials on client computers.
What should you recommend?
- A . User and Entity Behavior Analytics (UEBA) in Microsoft Sentinel
- B . a deception rule in Microsoft Defender for Endpoint
- C . a Honeytoken tag in Microsoft Defender for Identity
- D . a user risk policy in Microsoft Entra ID Protection
You have an on-premises network that has several legacy applications. The applications perform LDAP queries against an existing directory service. You are migrating the on-premises infrastructure
to a cloud-only infrastructure.
You need to recommend an identity solution for the infrastructure that supports the legacy applications. The solution must minimize the administrative effort to maintain the infrastructure.
Which identity service should you include in the recommendation?
- A . Azure Active Directory Domain Services (Azure AD DS)
- B . Azure Active Directory (Azure AD) B2C
- C . Azure Active Directory (Azure AD)
- D . Active Directory Domain Services (AD DS)
A
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory-domain-services/overview
Your company has a Microsoft 365 E5 subscription.
Users use Microsoft Teams, Exchange Online, SharePoint Online, and OneDrive for sharing and collaborating. The company identifies protected health information (PHI) within stored documents and communications.
What should you recommend using to prevent the PHI from being shared outside the company?
- A . insider risk management policies
- B . data loss prevention (DLP) policies
- C . sensitivity label policies
- D . retention policies
C
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/create-test-tune-dlp-policy?view=o365-worldwide
