Practice Free SC-100 Exam Online Questions
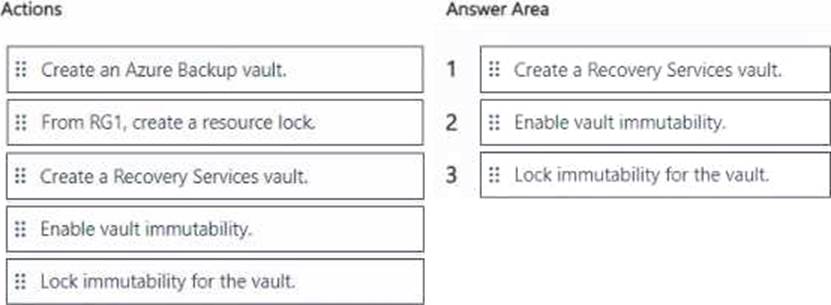
DRAG DROP
You have an Azure subscription that contains a resources group named RG1. RG1 contains multiple Azure Files shares.
You need to recommend a solution to deploy a backup solution for the shares.
The solution must meet the following requirements:
• Prevent the deletion of backups and the vault used to store the backups.
• Prevent privilege escalation attacks against the backup solution.
• Prevent the modification of the backup retention period.
Which three actions should you recommend be performed in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have a Microsoft Entra tenant. The tenant contains 500 Windows devices that have the Global Secure Access client deployed.
You have a third-party software as a service (SaaS) app named App1.
You plan to implement Global Secure Access to manage access to App1.
You need to recommend a solution to manage connections to App1. The solution must ensure that users authenticate by using their Microsoft Entra credentials before they can connect to App1.
What should you include the recommendation?
- A . a Global Secure Access app
- B . a private access traffic forwarding profile
- C . an internet access traffic forwarding profile
- D . a Quick Access app
You are designing a new Azure environment based on the security best practices of the Microsoft Cloud Adoption Framework for Azure. The environment will contain one subscription for shared infrastructure components and three separate subscriptions for applications.
You need to recommend a deployment solution that includes network security groups (NSGs) Azure Key Vault, and Azure Bastion. The solution must minimize deployment effort and follow security best practices of the Microsoft Cloud Adoption Framework for Azure.
What should you include in the recommendation?
- A . the Azure landing zone accelerator
- B . the Azure Will-Architected Framework
- C . Azure Security Benchmark v3
- D . Azure Advisor
Topic 3, Mix Questions
Your company has on-premises Microsoft SQL Server databases.
The company plans to move the databases to Azure.
You need to recommend a secure architecture for the databases that will minimize operational requirements for patching and protect sensitive data by using dynamic data masking. The solution must minimize costs.
What should you include in the recommendation?
- A . Azure SQL Managed Instance
- B . Azure Synapse Analytics dedicated SQL pools
- C . Azure SQL Database
- D . SQL Server on Azure Virtual Machines
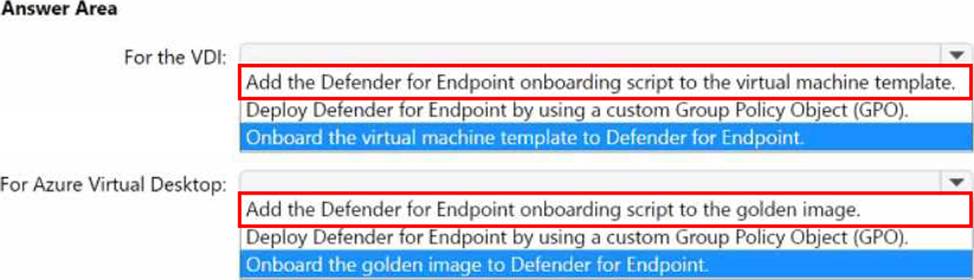
HOTSPOT
You have an Active Directory Domain Services (AD DS) domain that contains a virtual desktop infrastructure (VDI). The VDI uses non-persistent images and cloned virtual machine templates. VDI devices are members of the domain.
You have an Azure subscription that contains an Azure Virtual Desktop environment. The environment contains host pools that use a custom golden image. All the Azure Virtual Desktop deployments are members of a single Azure Active Directory Domain Services (Azure AD DS) domain.
You need to recommend a solution to deploy Microsoft Defender for Endpoint to the hosts.
The solution must meet the following requirements:
• Ensure that the hosts are onboarded to Defender for Endpoint during the first startup sequence.
• Ensure that the Microsoft Defender 365 portal contains a single entry for each deployed VDI host.
• Minimize administrative effort.
What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure AD tenant that contains 10 Windows 11 devices and two groups named Group1 and Group2. The Windows 11 devices are joined to the Azure AD tenant and are managed by using Microsoft Intune.
You are designing a privileged access strategy based on the rapid modernization plan (RaMP).
The strategy will include the following configurations:
• Each user in Group1 will be assigned a Windows 11 device that will be configured as a privileged access device.
• The Security Administrator role will be mapped to the privileged access security level.
• The users in Group1 will be assigned the Security Administrator role.
• The users in Group2 will manage the privileged access devices.
You need to configure the local Administrators group for each privileged access device. The solution must follow the principle of least privilege.
What should you include in the solution?
- A . Only add Group2 to the local Administrators group.
- B . Configure Windows Local Administrator Password Solution (Windows LAPS) in legacy Microsoft LAPS emulation mode.
- C . Add Group2 to the local Administrators group. Add the user that is assigned the Security Administrator role to the local Administrators group of the user’s assigned privileged access device.
Note: This section contains one or more sets of questions with the same scenario and problem. Each question presents a unique solution to the problem. You must determine whether the solution meets the stated goals. More than one solution in the set might solve the problem. It is also possible that none of the solutions in the set solve the problem.
After you answer a question in this section, you will NOT be able to return. As a result, these questions do not appear on the Review Screen.
You have a Microsoft 365 subscription that uses Microsoft Defender XDR. The subscription contains 500 devices that are enrolled in Microsoft Intune. The subscription contains 500 users that connect to external software as a service (SaaS) apps by using the devices.
You need to implement a solution that meets the following requirements:
• Allows user access to SaaS apps that Microsoft has identified as low risk.
• Blocks user access to Saas apps that Microsoft has identified as high risk.
Solution: From Microsoft Defender for Cloud Apps, you configure SaaS security posture management (SSPM) and create an access policy.
Does this meet the goal?
- A . Yes
- B . No
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled.
The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019.
You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application.
Which security control should you recommend?
- A . Azure Active Directory (Azure AD) Conditional Access App Control policies
- B . OAuth app policies in Microsoft Defender for Cloud Apps
- C . app protection policies in Microsoft Endpoint Manager
- D . application control policies in Microsoft Defender for Endpoint
D
Explanation:
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-application-control/select-types-of-rules-to-create#windows-defender-application-control-policy-rules
You have a Microsoft 365 subscription.
You are designing a user access solution that follows the Zero Trust principles of the Microsoft Cybersecurity Reference Architectures (MCRA).
You need to recommend a solution that automatically restricts access to Microsoft Exchange Online.
SharePoint Online, and Teams m near-real-lime (NRT) in response to the following Azure AD events:
• A user account is disabled or deleted
• The password of a user is changed or reset.
• All the refresh tokens for a user are revoked
• Multi-factor authentication (MFA) is enabled for a user
Which two features should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . continuous access evaluation
- B . a sign-in risk policy
- C . Azure AD Privileged Identity Management (PIM)
- D . Conditional Access
- E . Azure AD Application Proxy
You have on-premises Windows 11 devices that have the Global Secure Access client deployed. You have a Microsoft 365 subscription that uses Microsoft SharePoint Online and Exchange Online. You deploy Microsoft Entra Internet Access from the on-premises network to Microsoft 365.
The deployment has the Microsoft 365 profile enabled and contains the following:
• Default traffic policies for Microsoft 365 services
• A linked Conditional Access policy that performs compliant network checks with continuous access evaluation and is applied to all users
• An assignment to all the devices
• An assignment to a remote network associated with the on-premises network
Which Microsoft 365 resources are protected by using continuous access evaluation?
- A . SharePoint Online only
- B . Exchange Online only
- C . both SharePoint Online and Exchange Online
