Practice Free SC-100 Exam Online Questions
DRAG DROP
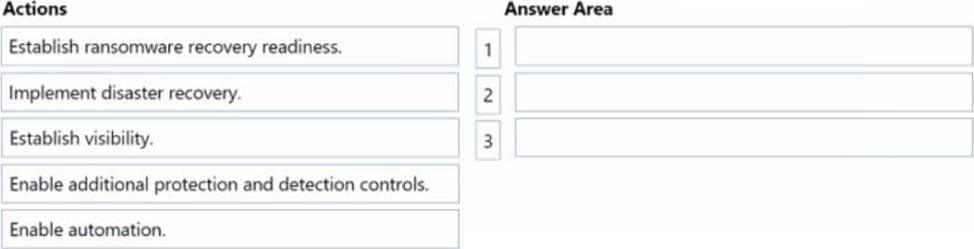
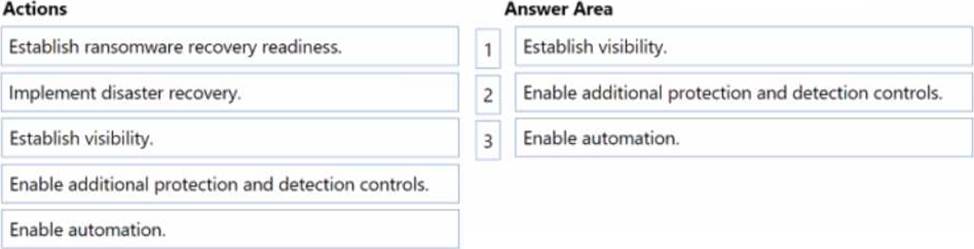
You are designing a security operations strategy based on the Zero Trust framework.
You need to increase the operational efficiency of the Microsoft Security Operations Center (SOC).
Based on the Zero Trust framework, which three deployment objectives should you prioritize in sequence? To answer, move the appropriate objectives from the list of objectives to the answer area and arrange them in the correct order.
You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements.
Which two services should you leverage in the strategy? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Azure AD Conditional Access
- B . Microsoft Defender for Cloud Apps
- C . Microsoft Defender for Cloud
- D . Microsoft Defender for Endpoint
- E . access reviews in Azure AD
B, C
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/concept-conditional-access-session#conditional-access-application-control
https://docs.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-integrate-with-microsoft-cloud-application-security
You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend access restrictions to allow traffic from the backend IP address of the Front Door instance.
Does this meet the goal?
- A . Yes
- B . No
Your company has a Microsoft 365 E5 subscription.
The Chief Compliance Officer plans to enhance privacy management in the working environment. You need to recommend a solution to enhance the privacy management.
The solution must meet the following requirements:
• Identify unused personal data and empower users to make smart data handling decisions.
• Provide users with notifications and guidance when a user sends personal data in Microsoft Teams.
• Provide users with recommendations to mitigate privacy risks.
What should you include in the recommendation?
- A . Microsoft Viva Insights
- B . Advanced eDiscovery
- C . Privacy Risk Management in Microsoft Priva
- D . communication compliance in insider risk management
C
Explanation:
Privacy Risk Management in Microsoft Priva gives you the capability to set up policies that identify privacy risks in your Microsoft 365 environment and enable easy remediation. Privacy Risk Management policies are meant to be internal guides and can help you: Detect overexposed personal data so that users can secure it.
Spot and limit transfers of personal data across departments or regional borders.
Help users identify and reduce the amount of unused personal data that you store.
https://www.microsoft.com/en-us/security/business/privacy/microsoft-priva-risk-management
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You have an Amazon Web Services (AWS) implementation.
You plan to extend the Azure security strategy to the AWS implementation. The solution will NOT use Azure Arc.
Which three services can you use to provide security for the AWS resources? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
- B . Azure Active Directory (Azure AD) Conditional Access
- C . Microsoft Defender for servers
- D . Azure Policy
- E . Microsoft Defender for Containers
BDE
Explanation:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/supported-machines-endpoint-solutions-clouds-containers?tabs=aws-eks
You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend access restrictions that allow traffic from the Front Door service tags.
Does this meet the goal?
- A . Yes
- B . No
A
Explanation:
https://docs.microsoft.com/en-us/azure/app-service/app-service-ip-restrictions#restrict-access-to-a-specific-azure-front-door-instance
A customer has a Microsoft 365 E5 subscription and an Azure subscription.
The customer wants to centrally manage security incidents, analyze log, audit activity, and search for potential threats across all deployed services.
You need to recommend a solution for the customer. The solution must minimize costs.
What should you include in the recommendation?
- A . Microsoft 365 Defender
- B . Microsoft Defender for Cloud
- C . Microsoft Defender for Cloud Apps
- D . Microsoft Sentinel
HOTSPOT
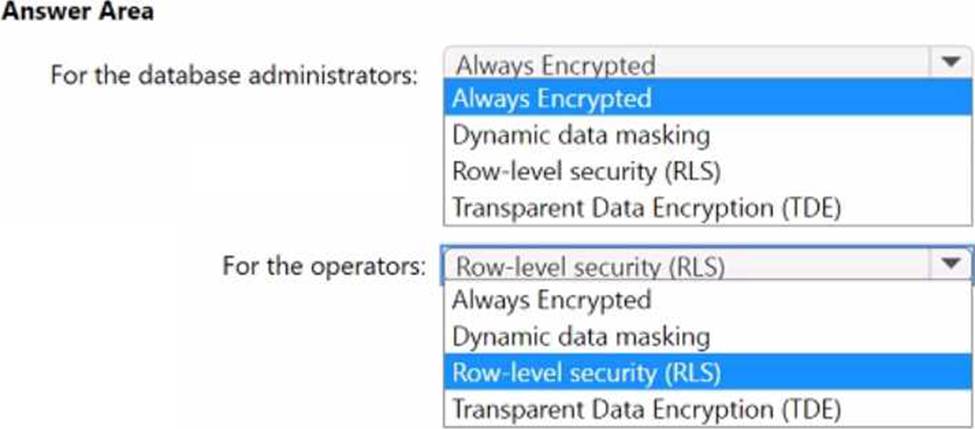
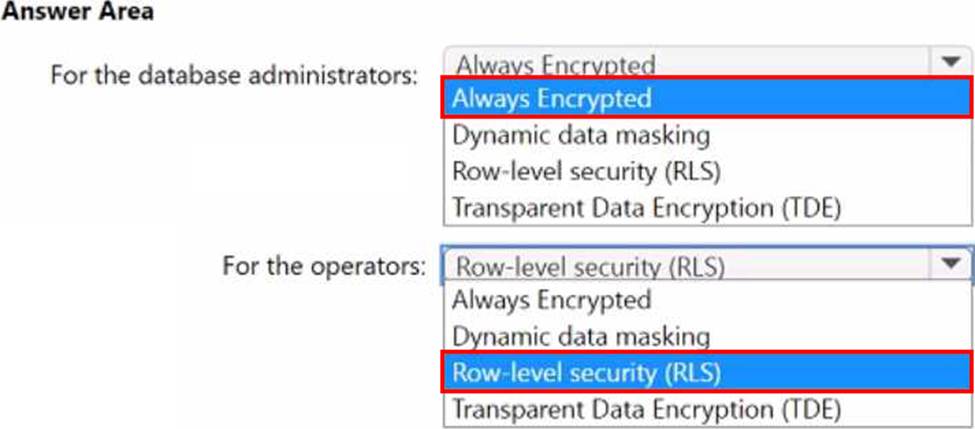
You have an Azure SQL database named DB1 that contains customer information.
A team of database administrators has full access to DB1.
To address customer inquiries, operators in the customer service department use a custom web app named App1 to view the customer information.
You need to design a security strategy for D81.
The solution must meet the following requirements:
• When the database administrators access DB1 by using SQL management tools, they must be prevented from viewing the content of the Credit Card attribute of each customer record.
• When the operators view customer records in App1, they must view only the last four digits of the Credit Card attribute.
What should you include in the design? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains multiple network security groups (NSGs), multiple virtual machines, and an Azure Bastion host named bastion1.
Several NSGs contain rules that allow direct RDP access to the virtual machines by bypassing bastion!
You need to ensure that the virtual machines can be accessed only by using bastion! The solution must prevent the use of NSG rules to bypass bastion1.
What should you include in the solution?
- A . Azure Virtual Network Manager connectivity configurations
- B . Azure Virtual Network Manager security admin rules
- C . Azure Firewall application rules
- D . Azure Firewall network rules
Your network contains an Active Directory Domain Services (AD DS) domain.
You need to ensure that the built-in administrator account for the domain can be used only for interactive sign-ins to domain controllers.
What should you configure?
- A . the Protected Users group
- B . authentication policies
- C . the User Rights Assignment security policy settings
- D . an authentication policy silo
