Practice Free SC-100 Exam Online Questions
HOTSPOT
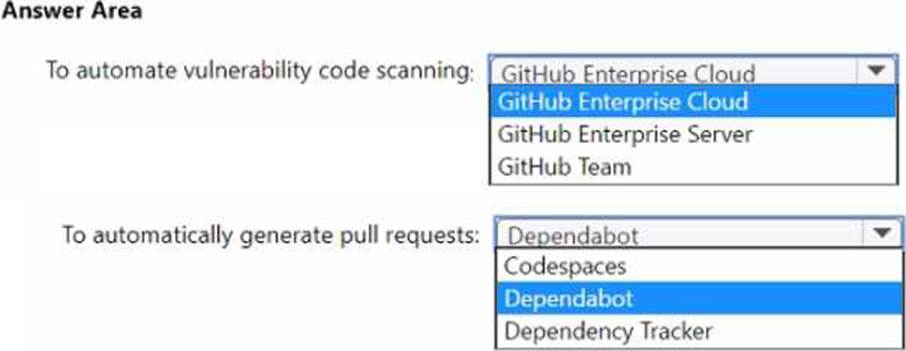
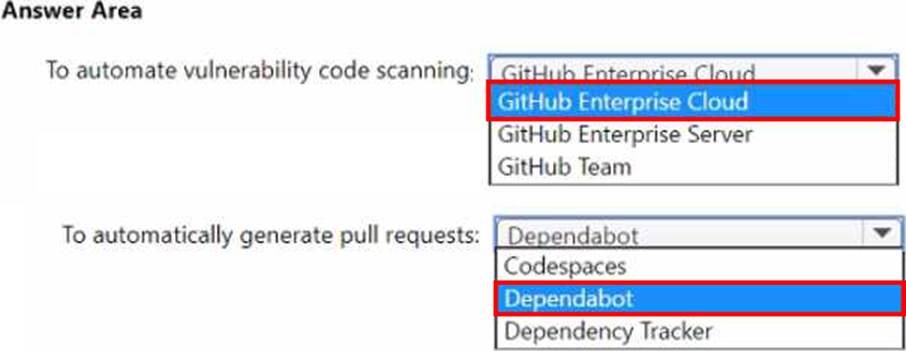
You plan to automate the development and deployment of a Nodejs-based app by using GitHub.
You need to recommend a DevSecOps solution for the app.
The solution must meet the following requirements:
• Automate the generation of pull requests that remediate identified vulnerabilities.
• Automate vulnerability code scanning for public and private repositories.
• Minimize administrative effort.
• Minimize costs.
What should you recommend using? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription and an Azure subscription. You are designing a Microsoft Sentinel deployment.
You need to recommend a solution for the security operations team. The solution must include custom views and a dashboard for analyzing security events.
What should you recommend using in Microsoft Sentinel?
- A . playbooks
- B . workbooks
- C . notebooks
- D . threat intelligence
B
Explanation:
https://docs.microsoft.com/en-us/azure/azure-monitor/visualize/workbooks-overview
You need to recommend a strategy for routing internet-bound traffic from the landing zones. The solution must meet the landing zone requirements.
What should you recommend as part of the landing zone deployment?
- A . service chaining
- B . local network gateways
- C . forced tunneling
- D . a VNet-to-VNet connection
A
Explanation:
https://docs.microsoft.com/en-us/learn/modules/configure-vnet-peering/5-determine-service-chaining-uses
You have a multicloud environment that contains an Azure subscription, an Amazon Web Services (AWS) subscription, and a Google Cloud Platform (GCP) subscription. You plan to assess data security and compliance.
You need to design a Compliance Manager solution that meets the following requirements:
• Provides recommended improvement actions that include detailed implementation guidance
• Automatically monitors regulatory compliance
• Minimizes administrative effort
What should you include in the solution?
- A . Microsoft Defender for Cloud
- B . Microsoft Defender for Cloud Apps
- C . Microsoft Sentinel
- D . Compliance Manager connectors
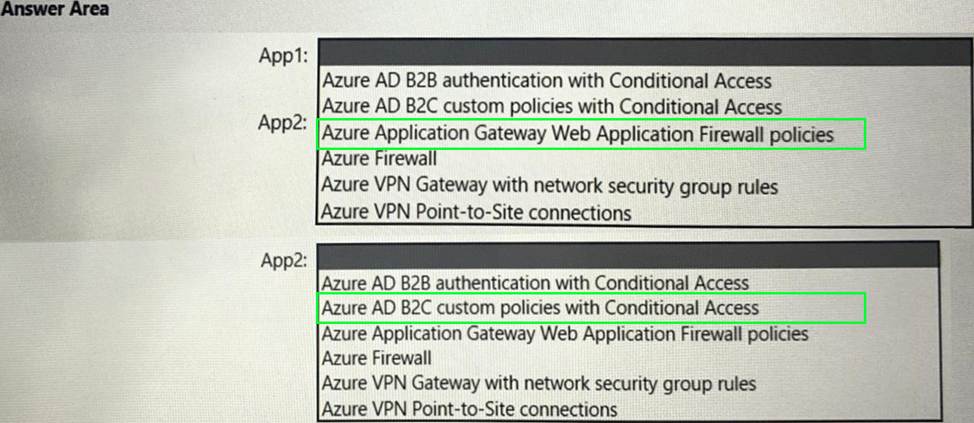
HOTSPOT
You have a hybrid cloud infrastructure.
You plan to deploy the Azure applications shown in the following table.
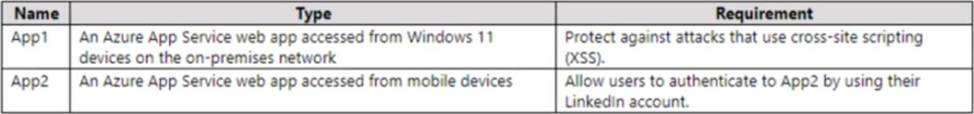
What should you use to meet the requirement of each app? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

Your company has an on-premises network, an Azure subscription, and a Microsoft 365 E5 subscription.
The company uses the following devices:
• Computers that run either Windows 10 or Windows 11
• Tablets and phones that run either Android or iOS
You need to recommend a solution to classify and encrypt sensitive Microsoft Office 365 data regardless of where the data is stored.
What should you include in the recommendation?
- A . eDiscovery
- B . retention policies
- C . Compliance Manager
- D . Microsoft Information Protection
D
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection https://docs.microsoft.com/en-us/microsoft-365/compliance/ediscovery?view=o365-worldwide
You are designing security for an Azure landing zone.
Your company identifies the following compliance and privacy requirements:
• Encrypt cardholder data by using encryption keys managed by the company.
• Encrypt insurance claim files by using encryption keys hosted on-premises.
Which two configurations meet the compliance and privacy requirements? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Store the insurance claim data in Azure Blob storage encrypted by using customer-provided keys.
- B . Store the cardholder data in an Azure SQL database that is encrypted by using keys stored in Azure Key Vault Managed HSM
- C . Store the insurance claim data in Azure Files encrypted by using Azure Key Vault Managed HSM.
- D . Store the cardholder data in an Azure SQL database that is encrypted by using Microsoft-managed Keys.
A, C
Explanation:
https://azure.microsoft.com/en-us/blog/customer-provided-keys-with-azure-storage-service-encryption/
You have an on-premises network that has several legacy applications. The applications perform LDAP queries against an existing directory service.
You are migrating the on-premises infrastructure to a cloud-only infrastructure.
You need to recommend an identity solution for the infrastructure that supports the legacy applications. The solution must minimize the administrative effort to maintain the infrastructure.
Which identity service should you include in the recommendation?
- A . Active Directory Domain Services (AD DS)
- B . Microsoft Entra ID
- C . Microsoft Entra Domain Services
- D . Microsoft Entra External ID
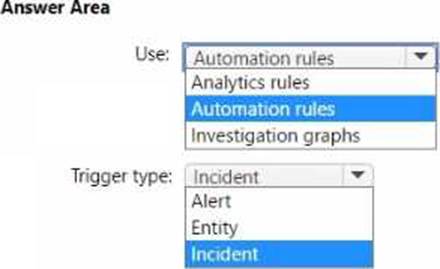
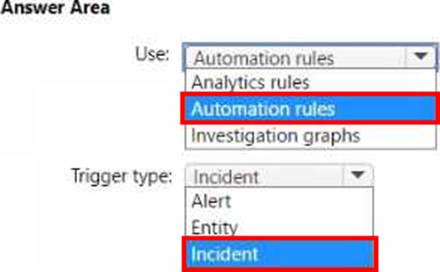
HOTSPOT
You have an Azure subscription that contains a Microsoft Sentinel workspace named MSW1. MSW1 includes 50 scheduled analytics rules.
You need to design a security orchestration automated response (SOAR) solution by using Microsoft Sentinel playbooks.
The solution must meet the following requirements:
• Ensure that expiration dates can be configured when a playbook runs.
• Minimize the administrative effort required to configure individual analytics rules.
What should you use to invoke the playbooks, and which type of Microsoft Sentinel trigger should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription. The subscription contains 50 virtual machines that run Windows Server and 50 virtual machines that run Linux. You need to perform vulnerability assessments on the virtual machines.
The solution must meet the following requirements:
• Identify missing updates and insecure configurations.
• Use the Qualys engine.
What should you use?
- A . Microsoft Defender for Servers
- B . Microsoft Defender Threat Intelligence (Defender Tl)
- C . Microsoft Defender for Endpoint
- D . Microsoft Defender External Attack Surface Management (Defender EASM)
