Practice Free SC-100 Exam Online Questions
HOTSPOT
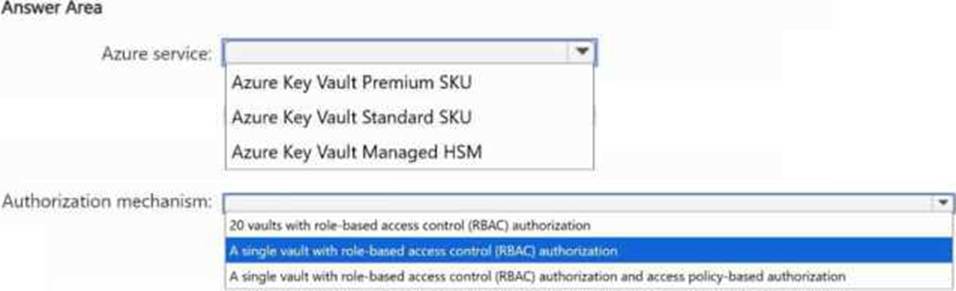
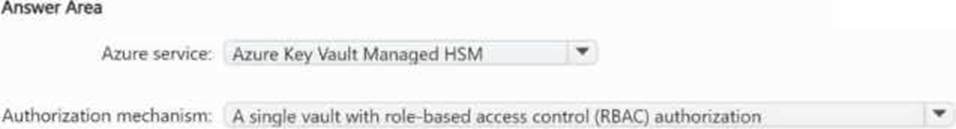
You have an Azure subscription. The subscription contains 20 App Service web apps that provide services to external customers.
Each web app has a unique certificate and key.
You need to recommend a solution to manage the keys and certificates of the web apps.
The solution must meet the follow requirements:
Provide a single tenancy to store the keys and certificates.
Maintain FIPS 140-2 Level 3 compliance.
Follow the principle of least privilege.
Topic 2, Litware, inc. Case Study 2
Overview
Litware, inc. is a financial services company that has main offices in New York and San Francisco. litware has 30 branch offices and remote employees across the United States. The remote employees connect to the main offices by using a VPN.
Litware has grown significantly during the last two years due to mergers and acquisitions.
The acquisitions include several companies based in France.
Existing Environment
Litware has an Azure Active Directory (Azure AD) tenant that syncs with an Active Directory Domain Services (AD D%) forest named Utvvare.com and is linked to 20 Azure subscriptions. Azure AD Connect is used to implement pass-through authentication. Password hash synchronization is disabled, and password writeback is enabled. All Litware users have Microsoft 365 E5 licenses.
The environment also includes several AD DS forests, Azure AD tenants, and hundreds of Azure subscriptions that belong to the subsidiaries of Litware.
Planned Changes
Litware plans to implement the following changes:
• Create a management group hierarchy for each Azure AD tenant.
• Design a landing zone strategy to refactor the existing Azure environment of Litware and deploy all future Azure workloads.
• Implement Azure AD Application Proxy to provide secure access to internal applications that are currently accessed by using the VPN.
Business Requirements
Litware identifies the following business requirements:
• Minimize any additional on-premises infrastructure.
• Minimize the operational costs associated with administrative overhead.
Hybrid Requirements
Litware identifies the following hybrid cloud requirements:
• Enable the management of on-premises resources from Azure, including the following: •Use Azure Policy for enforcement and compliance evaluation.
• Provide change tracking and asset inventory.
• Implement patch management.
• Provide centralized, cross-tenant subscription management without the overhead of maintaining guest accounts.
Microsoft Sentinel Requirements
Litware plans to leverage the security information and event management (SIEM) and security orchestration automated response (SOAK) capabilities of Microsoft Sentinel. The company wants to centralize Security Operations Center (SOQ by using Microsoft Sentinel.
Identity Requirements
Litware identifies the following identity requirements:
• Detect brute force attacks that directly target AD DS user accounts.
• Implement leaked credential detection in the Azure AD tenant of Litware.
• Prevent AD DS user accounts from being locked out by brute force attacks that target Azure AD user accounts.
• Implement delegated management of users and groups in the Azure AD tenant of Litware, including support for.
• The management of group properties, membership, and licensing « The management of user properties, passwords, and licensing
• The delegation of user management based on business units.
Regulatory Compliance Requirements
Litware identifies the following regulatory compliance requirements:
• insure data residency compliance when collecting logs, telemetry, and data owned by each United States- and France-based subsidiary.
• Leverage built-in Azure Policy definitions to evaluate regulatory compliance across the entire managed environment.
• Use the principle of least privilege.
Azure Landing Zone Requirements
Litware identifies the following landing zone requirements:
• Route all internet-bound traffic from landing zones through Azure Firewall in a dedicated Azure subscription.
• Provide a secure score scoped to the landing zone.
• Ensure that the Azure virtual machines in each landing zone communicate with Azure App Service web apps in the same zone over the Microsoft backbone network, rather than over public endpoints.
• Minimize the possibility of data exfiltration.
• Maximize network bandwidth.
The landing zone architecture will include the dedicated subscription, which will serve as the hub for internet and hybrid connectivity.
Each landing zone will have the following characteristics:
• Be created in a dedicated subscription.
• Use a DNS namespace of litware.com.
Application Security Requirements
Litware identifies the following application security requirements:
• Identify internal applications that will support single sign-on (SSO) by using Azure AD Application Proxy.
• Monitor and control access to Microsoft SharePoint Online and Exchange Online data in real time.
To meet the application security requirements, which two authentication methods must the applications support? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . Security Assertion Markup Language (SAML)
- B . NTLMv2
- C . certificate-based authentication
- D . Kerberos
AD
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-configure-single-sign-on-on-premises-apps
https://docs.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-configure-single-sign-on-with-kcd
https://docs.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-configure-custom-domain
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls.
Solution: You recommend onboarding all virtual machines to Microsoft Defender for Endpoint.
Does this meet the goal?
- A . Yes
- B . No
B
Explanation:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/secure-score-security-controls
HOTSPOT
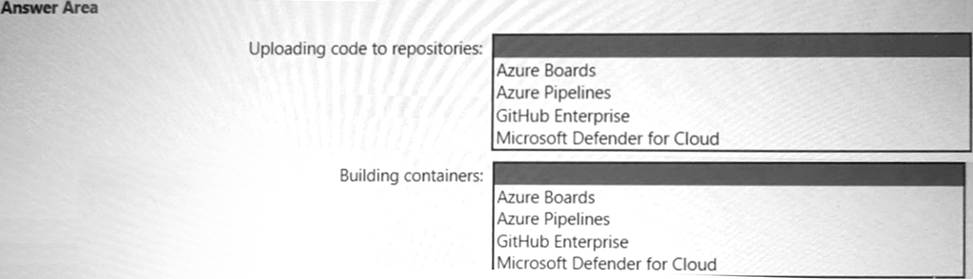
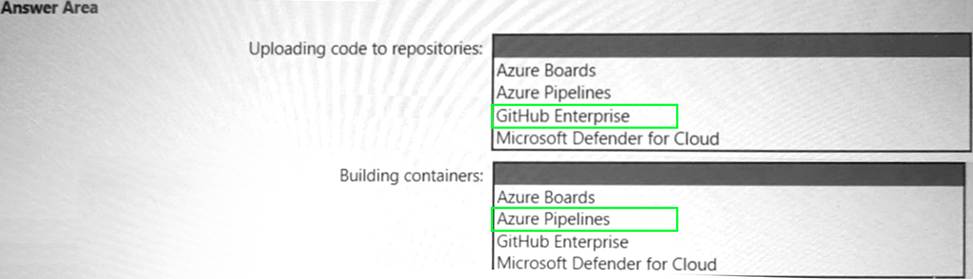
Your company has an Azure App Service plan that is used to deploy containerized web apps. You are designing a secure DevOps strategy for deploying the web apps to the App Service plan. You need to recommend a strategy to integrate code scanning tools into a secure software development lifecycle.
The code must be scanned during the following two phases:
Uploading the code to repositories Building containers
Where should you integrate code scanning for each phase? To answer, select the appropriate options
in the answer area.
Explanation:
https://docs.github.com/en/enterprise-cloud@latest/get-started/learning-about-github/about-github-advanced-security
https://microsoft.github.io/code-with-engineering-playbook/automated-testing/tech-specific-samples/azdo-container-dev-test-release/
HOTSPOT
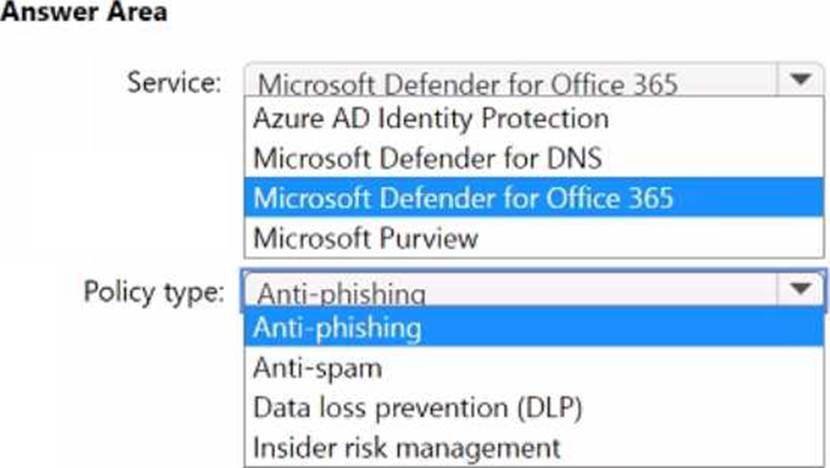
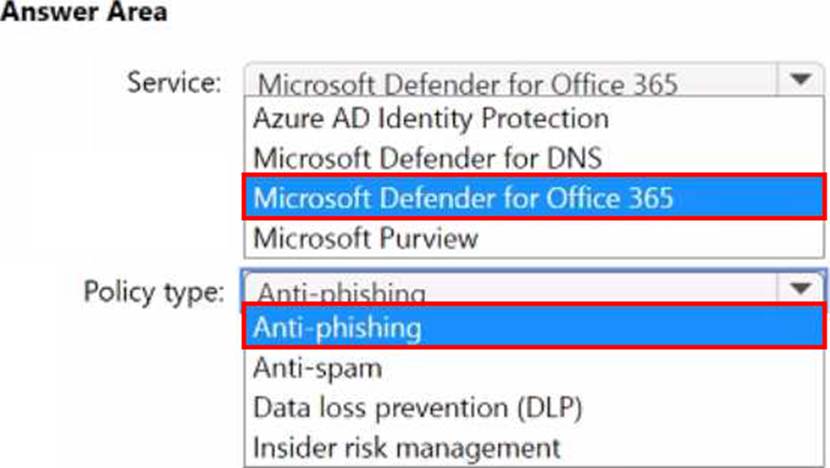
You have a Microsoft 365 E5 subscription that uses Microsoft Exchange Online.
You need to recommend a solution to prevent malicious actors from impersonating the email addresses of internal senders.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
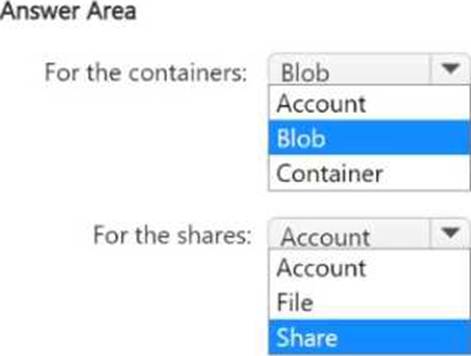
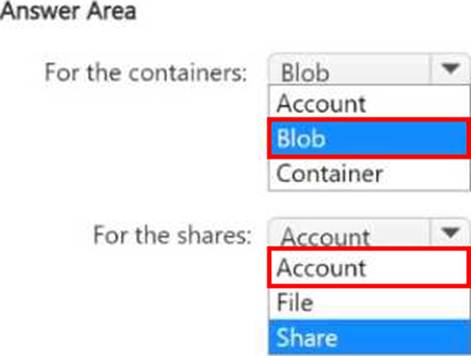
You have an Azure subscription that contains multiple storage accounts. The accounts contain Azure Files shares and Azure Blob Storage containers. The accounts have encryption scopes and infrastructure encryption enabled.
You need to implement customer-managed key-based encryption for the shares and the containers.
The solution must ensure that the encryption keys are applied at the most granular level.
At which level should you apply the encryption keys? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
You need to recommend a multi-tenant and hybrid security solution that meets to the business requirements and the hybrid requirements.
What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.


HOTSPOT
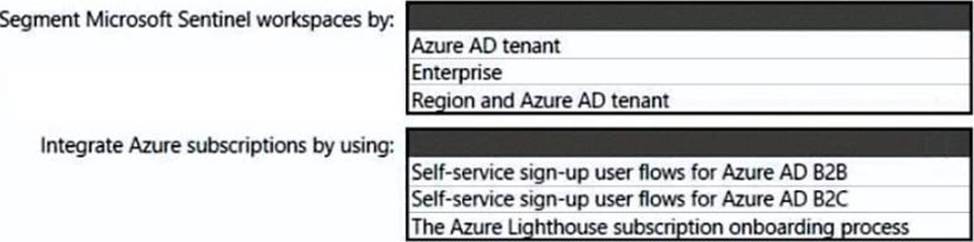
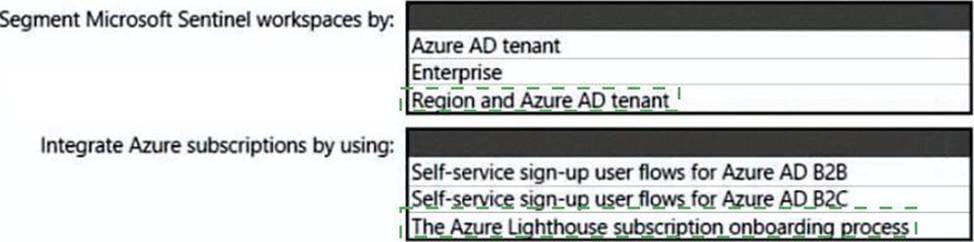
You need to recommend a SIEM and SOAR strategy that meets the hybrid requirements, the Microsoft Sentinel requirements, and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Explanation:
Segment Microsoft Sentinel workspaces by: Region and Azure AD tenant Lighthouse subscription
Your company has a Microsoft 365 E5 subscription.
The company wants to identify and classify data in Microsoft Teams, SharePoint Online, and Exchange Online.
You need to recommend a solution to identify documents that contain sensitive information.
What should you include in the recommendation?
- A . data classification content explorer
- B . data loss prevention (DLP)
- C . eDiscovery
- D . Information Governance
Note: This section contains one or more sets of questions with the same scenario and problem. Each question presents a unique solution to the problem. You must determine whether the solution meets the stated goals. More than one solution in the set might solve the problem. It is also possible that none of the solutions in the set solve the problem.
After you answer a question in this section, you will NOT be able to return. As a result, these questions do not appear on the Review Screen.
You have a Microsoft 365 subscription that uses Microsoft Defender XDR. The subscription contains 500 devices that are enrolled in Microsoft Intune. The subscription contains 500 users that connect to external software as a service (SaaS) apps by using the devices.
You need to implement a solution that meets the following requirements:
• Allows user access to SaaS apps that Microsoft has identified as low risk.
• Blocks user access to Saas apps that Microsoft has identified as high risk.
Solution: You configure app protection policies in Intune, and you create a Conditional Access policy.
Does this meet the goal?
- A . Yes
- B . No
