Practice Free PT0-003 Exam Online Questions
A penetration testing team wants to conduct DNS lookups for a set of targets provided by the client.
The team crafts a Bash script for this task. However, they find a minor error in one line of the script:
1 #!/bin/bash
2 for i in $(cat example.txt); do
3 curl $i
4 done
Which of the following changes should the team make to line 3 of the script?
- A . resolvconf $i
- B . rndc $i
- C . systemd-resolve $i
- D . host $i
D
Explanation:
Script Analysis:
Line 1: #!/bin/bash – This line specifies the script should be executed in the Bash shell.
Line 2: for i in $(cat example.txt); do – This line starts a loop that reads each line from the file example.txt and assigns it to the variable i.
Line 3: curl $i – This line attempts to fetch the content from the URL stored in i using curl. However, for DNS lookups, curl is inappropriate.
Line 4: done – This line ends the loop.
Error Identification:
The curl command is used for transferring data from or to a server, often used for HTTP requests, which is not suitable for DNS lookups.
Correct Command:
To perform DNS lookups, the host command should be used. The host command performs DNS lookups and displays information about the given domain.
Corrected Script:
Replace curl $i with host $i to perform DNS lookups on each target specified in example.txt.
Pentest
Reference: In penetration testing, DNS enumeration is a crucial step. It involves querying DNS servers to gather
information about the target domain, which includes resolving domain names to IP addresses and vice versa.
Common tools for DNS enumeration include host, dig, and nslookup. The host command is particularly straightforward for simple DNS lookups.
By correcting the script to use host $i, the penetration testing team can effectively perform DNS lookups on the targets specified in example.txt.
During a security assessment for an internal corporate network, a penetration tester wants to gain unauthorized access to internal resources by executing an attack that uses software to disguise itself as legitimate software.
Which of the following host-based attacks should the tester use?
- A . On-path
- B . Logic bomb
- C . Rootkit
- D . Buffer overflow
C
Explanation:
A rootkit is a type of malicious software designed to provide an attacker with unauthorized access to a computer system while concealing its presence. Rootkits achieve this by modifying the host’s operating system or other software to hide their existence, allowing the attacker to maintain control over the system without detection.
Definition and Purpose:
Rootkits are primarily used to gain and maintain root access (administrative privileges) on a system.
They disguise themselves as legitimate software or integrate deeply into the operating system to avoid detection.
Mechanisms of Action:
Kernel Mode Rootkits: These operate at the kernel level, which is the core of the operating system, making them very powerful and hard to detect.
User Mode Rootkits: These run in the same space as user applications, intercepting and altering standard system API calls to hide their presence.
Bootkits: These infect the Master Boot Record (MBR) or Volume Boot Record (VBR) and load before the operating system, making them extremely difficult to detect and remove.
Detection and Prevention:
Detection Tools: Tools like RootkitRevealer, Chkrootkit, and rkhunter can help in identifying rootkits.
Prevention: Regular system updates, use of strong antivirus and anti-malware solutions, and integrity checking tools like Tripwire can help in preventing rootkit infections.
Real-World Examples:
Sony BMG Rootkit: In 2005, Sony BMG included a rootkit in their digital rights management (DRM) software on music CDs. The rootkit hid files and processes, leading to a major scandal when it was discovered.
Stuxnet: This sophisticated worm included a rootkit component to hide its presence on infected systems, making it one of the most infamous examples of rootkit use in a cyber attack.
Reference from Pentesting Literature:
In "Penetration Testing – A Hands-on Introduction to Hacking" by Georgia Weidman, rootkits are discussed in the context of post-exploitation, where maintaining access to the compromised system is crucial.
Various HTB write-ups, such as the analysis of complex attacks involving multiple stages of exploitation, often highlight the use of rootkits in maintaining persistent access.
Step-by-Step ExplanationReference: Penetration Testing – A Hands-on Introduction to Hacking HTB Official Writeups on sophisticated attacks
During an internal penetration test, the tester uses the following command:
C: Invoke-mimikatz.ps1 "kerberos: : golden /domain: test.local /sid: S-1-5-21-3234… /target:
dc01.test.local /service: CIFS /RC4: 237749d82… /user: support.test.local /ptt"
Which of the following best describes the tester’s goal when executing this command?
- A . Bypassing normal authentication
- B . Enumerating shares
- C . Obtaining current user credentials
- D . Using password spraying
A
Explanation:
This command uses Mimikatz’ kerberos: : golden module to forge a Golden Ticket, which is a fabricated Kerberos Ticket Granting Ticket (TGT) created using the domain’s Kerberos key material (commonly the KRBTGT hash, supplied here as an RC4 key). In PenTest+ post-exploitation tradecraft, a Golden Ticket allows an attacker to impersonate arbitrary users and obtain Kerberos service tickets without performing legitimate logon steps. The inclusion of /service: CIFS and /target: dc01.test.local indicates the tester intends to access the domain controller’s SMB/CIFS service using Kerberos authentication. The /ptt switch (“pass-the-ticket”) injects the forged ticket into the current session so the system will present it automatically to services.
The goal is therefore to bypass normal authentication controls by using a forged Kerberos ticket to gain authorized access to resources (like SMB shares) as a chosen identity. It is not share enumeration itself, not credential harvesting, and not password spraying.
Top of Form
A tester gains initial access to a server and needs to enumerate all corporate domain DNS records.
Which of the following commands should the tester use?
- A . dig +short A AAAA local.domain
- B . nslookup local.domain
- C . dig axfr @local.dns.server
- D . nslookup -server local.dns.server local.domain *
C
Explanation:
La opción C, dig axfr @local.dns.server, realiza una transferencia de zona DNS (Zone Transfer). Si el servidor DNS está mal configurado y permite este tipo de solicitudes, el atacante puede obtener todos los registros DNS del dominio interno.
La opción A muestra solo registros A/AAAA. La B no hace enumeración completa. La D no es válida como sintaxis.
Referencia: PT0-003 Objective 3.3 C Perform domain enumeration using dig and DNS zone transfer techniques.
A penetration tester needs to evaluate the order in which the next systems will be selected for testing.
Given the following output:
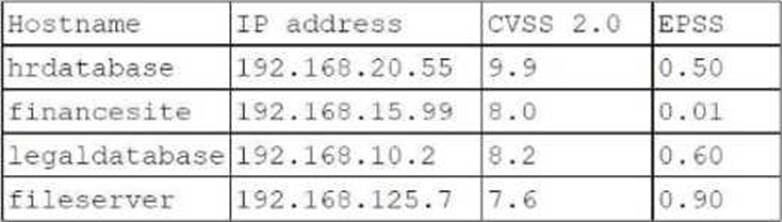
Which of the following targets should the tester select next?
- A . fileserver
- B . hrdatabase
- C . legaldatabase
- D . financesite
A
Explanation:
Evaluation Criteria:
CVSS (Common Vulnerability Scoring System): Indicates the severity of vulnerabilities, with higher scores representing more critical vulnerabilities.
EPSS (Exploit Prediction Scoring System): Estimates the likelihood of a vulnerability being exploited in the wild.
Analysis:
hrdatabase: CVSS = 9.9, EPSS = 0.50
financesite: CVSS = 8.0, EPSS = 0.01
legaldatabase: CVSS = 8.2, EPSS = 0.60
fileserver: CVSS = 7.6, EPSS = 0.90
Selection Justification:
fileserver has the highest EPSS score of 0.90, indicating a high likelihood of exploitation despite having a slightly lower CVSS score compared to other targets.
This makes it a critical target for immediate testing to mitigate potential exploitation risks.
Pentest
Reference: Risk Prioritization: Balancing between severity (CVSS) and exploitability (EPSS) is crucial for effective vulnerability management.
Risk Assessment: Evaluating both the impact and the likelihood of exploitation helps in making informed decisions about testing priorities.
By selecting the fileserver, the penetration tester focuses on a target that is highly likely to be exploited, addressing the most immediate risk based on the given scores.
Top of Form
Bottom of Form
During a security assessment of an e-commerce website, a penetration tester wants to exploit a vulnerability in the web server’s input validation that will allow unauthorized transactions on behalf of the user.
Which of the following techniques would most likely be used for that purpose?
- A . Privilege escalation
- B . DOM injection
- C . Session hijacking
- D . Cross-site scripting
D
Explanation:
Cross-site scripting (XSS) is a client-side attack where an attacker injects malicious scripts into a web page viewed by other users. When executed in a browser, it can steal session cookies, perform unauthorized transactions, or execute malicious actions on behalf of the victim.
Option D (Cross-site scripting) is correct because XSS can manipulate client-side input validation to execute unauthorized transactions.
Option A (Privilege escalation) is incorrect because it involves gaining higher privileges on a system, not attacking input validation in a web application.
Option B (DOM injection) is incorrect because DOM-based attacks manipulate browser-side JavaScript but are not necessarily used for unauthorized transactions.
Option C (Session hijacking) is incorrect because session hijacking requires capturing a valid user session, whereas XSS can steal session tokens for this purpose.
Reference: CompTIA PenTest+ PT0-003 Official Guide C Chapter 6 (Web Application Attacks).
A penetration tester downloads a JAR file that is used in an organization’s production environment. The tester evaluates the contents of the JAR file to identify potentially vulnerable components that can be targeted for exploit.
Which of the following describes the tester’s activities?
- A . SAST
- B . SBOM
- C . ICS
- D . SCA
D
Explanation:
The tester’s activity involves analyzing the contents of a JAR file to identify potentially vulnerable components. This process is known as Software Composition Analysis (SCA).
Here’s why:
Understanding SCA:
Definition: SCA involves analyzing software to identify third-party and open-source components, checking for known vulnerabilities, and ensuring license compliance.
Purpose: To detect and manage risks associated with third-party software components.
Comparison with Other Terms:
SAST (A): Static Application Security Testing involves analyzing source code for security vulnerabilities without executing the code.
SBOM (B): Software Bill of Materials is a detailed list of all components in a software product, often used in SCA but not the analysis itself.
ICS (C): Industrial Control Systems, not relevant to the context of software analysis.
The tester’s activity of examining a JAR file for vulnerable components aligns with SCA, making it the correct answer.
A penetration tester is conducting a vulnerability scan. The tester wants to see any vulnerabilities that may be visible from outside of the organization.
Which of the following scans should the penetration tester perform?
- A . SAST
- B . Sidecar
- C . Unauthenticated
- D . Host-based
C
Explanation:
To see any vulnerabilities that may be visible from outside of the organization, the penetration tester should perform an unauthenticated scan.
Unauthenticated Scan:
Definition: An unauthenticated scan is conducted without providing any credentials to the scanning tool. It simulates the perspective of an external attacker who does not have any prior access to the system.
Purpose: Identifies vulnerabilities that are exposed to the public and can be exploited without authentication. This includes open ports, outdated software, and misconfigurations visible to the
outside world.
Comparison with Other Scans:
SAST (Static Application Security Testing): Analyzes source code for vulnerabilities, typically used during the development phase and not suitable for external vulnerability scanning.
Sidecar: This term is generally associated with microservices architecture and is not relevant to the context of vulnerability scanning.
Host-based: Involves scanning from within the network and often requires authenticated access to the host to identify vulnerabilities. It is not suitable for determining external vulnerabilities.
Pentest
Reference: External Vulnerability Assessment: Conducting unauthenticated scans helps identify the attack surface exposed to external threats and prioritizes vulnerabilities that are accessible from the internet.
Tools: Common tools for unauthenticated scanning include Nessus, OpenVAS, and Nmap.
By performing an unauthenticated scan, the penetration tester can identify vulnerabilities that an external attacker could exploit without needing any credentials or internal access.
Which of the following OT protocols sends information in cleartext?
- A . TTEthernet
- B . DNP3
- C . Modbus
- D . PROFINET
C
Explanation:
Operational Technology (OT) protocols are used in industrial control systems (ICS) to manage and automate physical processes.
Here ’ s an analysis of each protocol regarding whether it sends information in cleartext:
TTEthernet (Option A):
TTEthernet (Time-Triggered Ethernet) is designed for real-time communication and safety-critical systems.
Security: It includes mechanisms for reliable and deterministic data transfer, not typically sending information in cleartext.
DNP3 (Option B):
DNP3 (Distributed Network Protocol) is used in electric and water utilities for SCADA (Supervisory Control and Data Acquisition) systems.
Security: While the original DNP3 protocol transmits data in cleartext, the DNP3 Secure Authentication extensions provide cryptographic security features.
Modbus ( Answer C):
Modbus is a communication protocol used in industrial environments for transmitting data between electronic devices.
Security: Modbus transmits data in cleartext, which makes it susceptible to interception and unauthorized access.
Reference: The lack of security features in Modbus, such as encryption, is well-documented and a known vulnerability in ICS environments.
PROFINET (Option D):
PROFINET is a standard for industrial networking in automation.
Security: PROFINET includes several security features, including support for encryption, which means it doesn’t necessarily send information in cleartext.
Conclusion: Modbus is the protocol that most commonly sends information in cleartext, making it vulnerable to eavesdropping and interception.
During an assessment, a penetration tester sends the following request:
POST /services/v1/users/create HTTP/1.1
Host: target-application.com
Content-Type: application/json
Content-Length: [dynamic]
Authorization: Bearer (FUZZ)
Which of the following attacks is the penetration tester performing?
- A . Directory traversal
- B . API abuse
- C . Server-side request forgery
- D . Privilege escalation
B
Explanation:
This attack attempts to manipulate the API by fuzzing the authorization token (Authorization: Bearer (FUZZ)). This suggests an attempt to bypass authentication or escalate privileges by using an invalid, stolen, or guessed token―a form of API abuse.
Option A (Directory traversal) ❌ :
Involves manipulating file paths (e.g., ../../../etc/passwd), but this attack targets API authentication.
Option B (API abuse) ✅ :
Correct. Fuzzing the authorization token suggests an attempt to bypass authentication or test for weak API security.
Option C (Server-side request forgery – SSRF) ❌ :
SSRF manipulates backend requests to make unauthorized HTTP calls, which is not evident here.
Option D (Privilege escalation) ❌ :
While API abuse may lead to privilege escalation, fuzzing the token alone does not directly escalate privileges.
Reference: CompTIA PenTest+ PT0-003 Official Guide C API Security Testing & Authentication Bypasses
