Practice Free PT0-003 Exam Online Questions
A penetration tester conducts reconnaissance for a client’s network and identifies the following system of interest:
$ nmap -A AppServer1.compita.org
Starting Nmap 7.80 (2023-01-14) on localhost (127.0.0.1) at 2023-08-04 15: 32: 27
Nmap scan report for AppServer1.compita.org (192.168.1.100)
Host is up (0.001s latency).
Not shown: 999 closed ports
Port State Service
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
873/tcp open rsync
8080/tcp open http-proxy
8443/tcp open https-alt
9090/tcp open zeus-admin
10000/tcp open snet-sensor-mgmt
The tester notices numerous open ports on the system of interest.
Which of the following best describes this system?
- A . A honeypot
- B . A Windows endpoint
- C . A Linux server
- D . An already-compromised system
A
Explanation:
A honeypot is a decoy system designed to attract attackers by exposing multiple services and vulnerabilities.
Indicators of a honeypot (Option A):
The system has an unusual combination of Windows (SMB, MSRPC) and Linux (Rsync, SSH) services.
It exposes a large number of open ports, which is uncommon for a production server.
Presence of "zeus-admin" (port 9090) suggests intentionally vulnerable services.
Reference: CompTIA PenTest+ PT0-003 Official Study Guide – "Honeypots and Decoys in Reconnaissance"
Incorrect options:
Option B (Windows endpoint): Windows would not normally run Rsync (873/tcp) or SSH (22/tcp).
Option C (Linux server): Linux servers typically don’t have NetBIOS (139/tcp) or MSRPC (135/tcp).
Option D (Already-compromised system): Although possible, honeypots mimic compromised systems to lure attackers.
A company wants to perform a BAS (Breach and Attack Simu-lation) to measure the efficiency of the corporate security controls.
Which of the following would most likely help the tester with simple command examples?
- A . Infection Monkey
- B . Exploit-DB
- C . Atomic Red Team
- D . Mimikatz
C
Explanation:
Breach and Attack Simulation (BAS) tools emulate real-world attacks to test security controls.
Atomic Red Team (Option C):
Atomic Red Team is an open-source BAS framework that provides simple commands to simulate MITRE ATT&CK® techniques.
It allows controlled adversary simulations without real exploitation.
Reference: CompTIA PenTest+ PT0-003 Official Study Guide – "Breach and Attack Simulation Tools"
Incorrect options:
Option A (Infection Monkey): Also a BAS tool but focuses on automated lateral movement, not simple commands.
Option B (Exploit-DB): A repository of exploits but not a BAS tool.
Option D (Mimikatz): Used for credential dumping, not BAS testing.
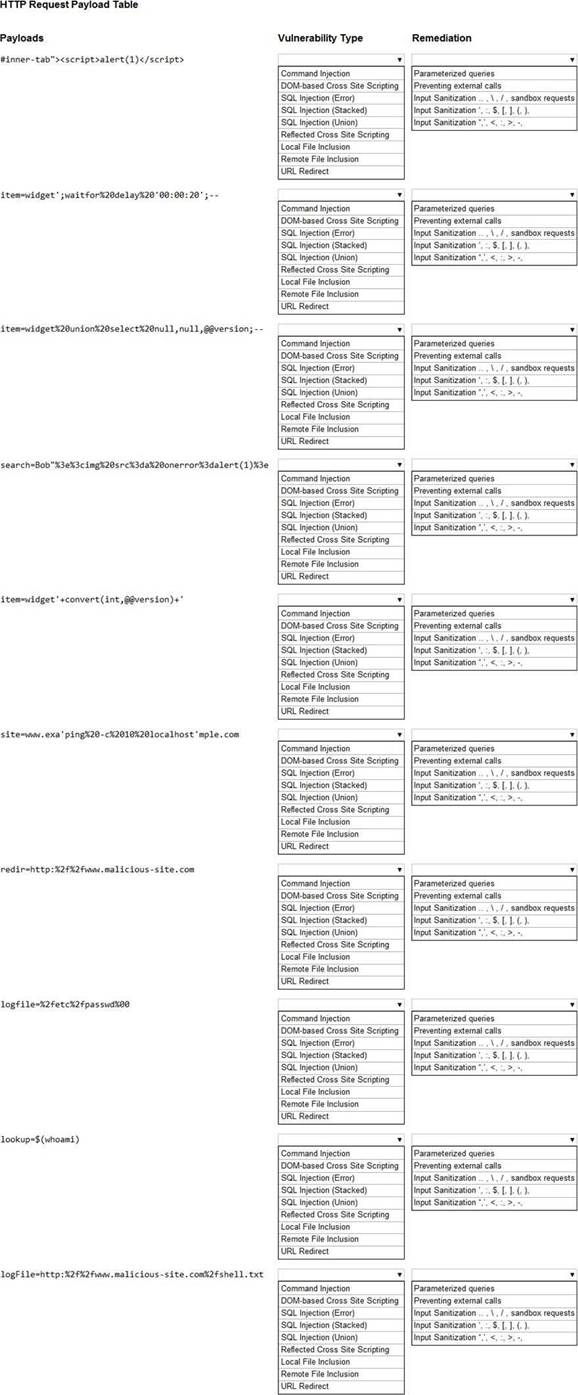
HOTSPOT
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A company that uses an insecure corporate wireless network is concerned about security.
Which of the following is the most likely tool a penetration tester could use to obtain initial access?
- A . Responder
- B . Metasploit
- C . Netcat
- D . Nmap
A
Explanation:
Comprehensive and Detailed
Given an insecure wireless network (e.g., open or poorly secured Wi-Fi), a practical initial access technique is to capture or poison name resolution/authentication requests from client systems once they are on that network. Responder is designed to perform LLMNR/NBT-NS/MDNS poisoning and capture NTLM authentication attempts and other credential material on a local network segment. On an insecure Wi-Fi network an attacker can either join the network or run a rogue AP and then run Responder to capture credentials from connected clients ― a typical and effective initial-access method in such scenarios.
Why not the others:
B. Metasploit ― a general exploitation framework; useful after finding a vulnerable service, but not specifically the most-likely initial tool on an insecure Wi-Fi.
C. Netcat ― a raw TCP/UDP utility (listeners/shells); useful post-exploitation but not for capturing broadcast name resolution requests.
D. Nmap ― a scanner to discover hosts/ports; helpful reconnaissance, but not directly used to capture credentials on a local insecure wireless segment.
CompTIA PT0-003 Mapping: Wireless/host-based attacks and network credential-capture techniques (evil twin/rogue AP and LLMNR/NetBIOS poisoning).
A penetration tester creates the following Python script that can be used to enumerate information about email accounts on a target mail server:
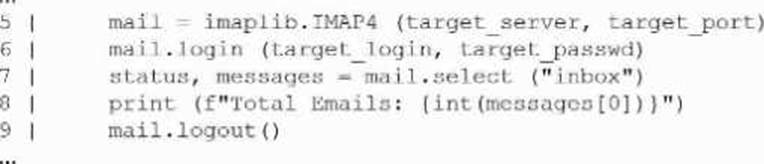
Which of the following logic constructs would permit the script to continue despite failure?
- A . Add a do/while loop.
- B . Add an iterator.
- C . Add a t.ry/except. block.
- D . Add an if/else conditional.
C
Explanation:
The correct construct for handling runtime failures (for example, login failures, network timeouts, or server errors) in Python is a try/except block (option C). Wrapping potentially failing operations in a try block and handling exceptions in except allows the script to catch the exception and continue execution (log the error, skip the target, retry, etc.) rather than crashing.
Why C is correct:
try/except is the Python mechanism to handle exceptions raised during execution. For network/email operations (IMAP login/select), IMAP libraries raise exceptions on failure ― try/except catches these and enables recovery logic.
Example corrected snippet:
import imaplib, sys
def enumerate_inbox(server, port, user, passwd):
try:
mail = imaplib.IMAP4(server, port)
mail.login(user, passwd)
status, messages = mail.select("inbox")
print(f"Total Emails: {int(messages[0])}")
except imaplib.IMAP4.error as e:
print(f"IMAP error for {user}: {e}")
# continue to next account or retry except Exception as e: print(f"Unexpected error for {user}: {e}") finally:
try:
mail.logout()
except: pass
Why the other options are not the best fit:
A penetration tester executes multiple enumeration commands to find a path to escalate privileges.
Given the following command:
find / -user root -perm -4000 -exec ls -ldb {} ; 2>/dev/null
Which of the following is the penetration tester attempting to enumerate?
- A . Attack path mapping
- B . API keys
- C . Passwords
- D . Permission
D
Explanation:
The command find / -user root -perm -4000 -exec ls -ldb {} ; 2>/dev/null is used to find files with the SUID bit set. SUID (Set User ID) permissions allow a file to be executed with the permissions of the file owner (root), rather than the permissions of the user running the file.
Understanding the Command:
find /: Search the entire filesystem.
-user root: Limit the search to files owned by the root user.
-perm -4000: Look for files with the SUID bit set.
-exec ls -ldb {} ;: Execute ls -ldb on each found file to list it in detail.
2>/dev/null: Redirect error messages to /dev/null to avoid cluttering the output.
Purpose:
Enumerating SUID Files: The command is used to identify files with elevated privileges that might be exploited for privilege escalation.
Security Risks: SUID files can pose security risks if they are vulnerable, as they can be used to execute code with root privileges.
Why Enumerate Permissions:
Identifying SUID files is a crucial step in privilege escalation as it reveals potential attack vectors that can be exploited to gain root access.
Reference from Pentesting Literature:
Enumeration of SUID files is a common practice in penetration testing, as discussed in various guides and write-ups.
HTB write-ups often detail how finding and exploiting SUID binaries can lead to root access on a target system.
Step-by-Step ExplanationReference: Penetration Testing – A Hands-on Introduction to Hacking HTB Official Writeups
A penetration tester conducts a scan on an exposed Linux web server and gathers the following data:
Host: 192.168.55.23
Open Ports:
22/tcp Open OpenSSH 7.2p2 Ubuntu 4ubuntu2.10
80/tcp Open Apache httpd 2.4.18 (Ubuntu)
111/tcp Open rpcbind 2-4 (RPC #100000)
Additional notes:
Directory listing enabled on /admin
Apache mod_cgi enabled
No authentication required to access /cgi-bin/debug.sh
X-Powered-By: PHP/5.6.40-0+deb8u12
Which of the following is the most effective action to take?
- A . Launch a payload using msfvenom and upload it to the /admin directory.
- B . Review the contents of /cgi-bin/debug.sh.
- C . Use Nikto to scan the host and port 80.
- D . Attempt a brute-force attack against OpenSSH 7.2p2.
B
Explanation:
The most effective next action is to investigate /cgi-bin/debug.sh because it is a direct, high-signal finding: a server-side script in a CGI-enabled directory that is reachable without authentication. In PenTest+ enumeration methodology, testers prioritize items that are both accessible and likely to yield immediate impact, such as unauthenticated administrative/debug endpoints, exposed scripts,
and functionality that could enable command execution or information disclosure. A debug shell script exposed through cgi-bin is a classic candidate for sensitive data leakage (paths, environment variables, credentials) or unsafe parameter handling that can lead to remote command execution― especially when mod_cgi is enabled and the file is callable over HTTP.
By comparison, uploading an msfvenom payload assumes a write primitive to /admin and an execution path, neither of which is established by the findings. Nikto can be useful, but it is redundant compared to the specific, actionable lead already identified. Brute-forcing SSH is noisy, may violate rules of engagement, and is less efficient than testing an unauthenticated web-exposed script first.
A penetration tester conducts a scan on an exposed Linux web server and gathers the following data:
Host: 192.168.55.23
Open Ports:
22/tcp Open OpenSSH 7.2p2 Ubuntu 4ubuntu2.10
80/tcp Open Apache httpd 2.4.18 (Ubuntu)
111/tcp Open rpcbind 2-4 (RPC #100000)
Additional notes:
Directory listing enabled on /admin
Apache mod_cgi enabled
No authentication required to access /cgi-bin/debug.sh
X-Powered-By: PHP/5.6.40-0+deb8u12
Which of the following is the most effective action to take?
- A . Launch a payload using msfvenom and upload it to the /admin directory.
- B . Review the contents of /cgi-bin/debug.sh.
- C . Use Nikto to scan the host and port 80.
- D . Attempt a brute-force attack against OpenSSH 7.2p2.
B
Explanation:
The most effective next action is to investigate /cgi-bin/debug.sh because it is a direct, high-signal finding: a server-side script in a CGI-enabled directory that is reachable without authentication. In PenTest+ enumeration methodology, testers prioritize items that are both accessible and likely to yield immediate impact, such as unauthenticated administrative/debug endpoints, exposed scripts,
and functionality that could enable command execution or information disclosure. A debug shell script exposed through cgi-bin is a classic candidate for sensitive data leakage (paths, environment variables, credentials) or unsafe parameter handling that can lead to remote command execution― especially when mod_cgi is enabled and the file is callable over HTTP.
By comparison, uploading an msfvenom payload assumes a write primitive to /admin and an execution path, neither of which is established by the findings. Nikto can be useful, but it is redundant compared to the specific, actionable lead already identified. Brute-forcing SSH is noisy, may violate rules of engagement, and is less efficient than testing an unauthenticated web-exposed script first.
A penetration tester successfully clones a source code repository and then runs the following command:
find . -type f -exec egrep -i "token|key|login" {} ;
Which of the following is the penetration tester conducting?
- A . Data tokenization
- B . Secrets scanning
- C . Password spraying
- D . Source code analysis
B
Explanation:
Penetration testers search for hardcoded credentials, API keys, and authentication tokens in source
code repositories to identify secrets leakage.
Secrets scanning (Option B):
The find and egrep command scans all files recursively for sensitive keywords like "token," "key," and "login".
Attackers use tools like TruffleHog and GitLeaks to automate secret discovery.
Reference: CompTIA PenTest+ PT0-003 Official Study Guide – "Source Code Review and Secret Leakage"
Incorrect options:
Option A (Data tokenization): Tokenization replaces sensitive data with unique tokens, not scanning for credentials.
Option C (Password spraying): Tries common passwords across multiple accounts, unrelated to scanning source code.
Option D (Source code analysis): Broader than secrets scanning; this question focuses specifically on credential discovery.
A penetration tester needs to exploit a vulnerability in a wireless network that has weak encryption to perform traffic analysis and decrypt sensitive information.
Which of the following techniques would best allow the penetration tester to have access to the sensitive information?
- A . Bluejacking
- B . SSID spoofing
- C . Packet sniffing
- D . ARP poisoning
C
Explanation:
If a wireless network uses weak encryption (e.g., WEP), attackers can capture and analyze packets to extract sensitive data.
Packet sniffing (Option C):
Tools like Wireshark, Aircrack-ng, and Kismet capture network packets.
Attackers analyze captured traffic to decrypt WEP encryption or extract plaintext credentials.
Reference: CompTIA PenTest+ PT0-003 Official Study Guide – "Wireless Network Attacks and Sniffing"
Incorrect options:
Option A (Bluejacking): Sends unsolicited Bluetooth messages, not for network sniffing.
Option B (SSID spoofing): Involves creating a fake access point, but does not analyze traffic.
Option D (ARP poisoning): Used for MITM attacks, but not specific to wireless traffic analysis.
