Practice Free PT0-002 Exam Online Questions
A penetration tester is conducting an Nmap scan and wants to scan for ports without establishing a connection. The tester also wants to find version data information for services running on Projects.
Which of the following Nmap commands should the tester use?
- A . ..nmap -sU -sV -T4 -F target.company.com
- B . ..nmap -sS -sV -F target.company.com
- C . ..nmap -sT -v -T5 target.company.com
- D . ..nmap -sX -sC target.company.com
B
Explanation:
The Nmap command that the tester should use to scan for ports without establishing a connection and to find version data information for services running on open ports is nmap -sS -sV -F target.company.com.
This command has the following options:
-sS performs a TCP SYN scan, which is a scan technique that sends TCP packets with the SYN flag set to the target ports and analyzes the responses. A TCP SYN scan does not establish a full TCP connection, as it only completes the first step of the three-way handshake. A TCP SYN scan can stealthily scan for open ports without alerting the target system or application.
-sV performs version detection, which is a feature that probes open ports to determine the service and version information of the applications running on them. Version detection can provide useful information for identifying vulnerabilities or exploits that affect specific versions of services or applications.
-F performs a fast scan, which is a scan option that only scans the 100 most common ports according to the nmap-services file. A fast scan can speed up the scan process by avoiding scanning less likely or less interesting ports.
target.company.com specifies the domain name of the target system or network to be scanned.
The other options are not valid Nmap commands that meet the requirements of the question. Option A performs a UDP scan (-sU), which is a scan technique that sends UDP packets to the target ports and analyzes the responses. A UDP scan can scan for open ports that use UDP protocol, such as DNS, SNMP, or DHCP. However, a UDP scan does establish a connection with the target system or application, unlike a TCP SYN scan. Option C performs a TCP connect scan (-sT), which is a scan technique that sends TCP packets with the SYN flag set to the target ports and completes the three-way handshake with an ACK packet if a SYN/ACK packet is received. A TCP connect scan can scan for open ports that use TCP protocol, such as HTTP, FTP, or SSH. However, a TCP connect scan does establish a full TCP connection with the target system or application, unlike a TCP SYN scan. Option D performs an Xmas scan (-sX), which is a scan technique that sends TCP packets with the FIN, PSH, and URG flags set to the target ports and analyzes the responses. An Xmas scan can stealthily scan for open ports without alerting the target system or application, similar to a TCP SYN scan. However, option D does not perform version detection (-sV), which is one of the requirements of the question.
Which of the following should be included in scope documentation?
- A . Service accounts
- B . Tester experience
- C . Disclaimer
- D . Number of tests
C
Explanation:
A disclaimer is a statement that limits the liability of the penetration tester and the client in case of any unintended consequences or damages caused by the testing activities. It should be included in the scope documentation to clarify the roles and responsibilities of both parties and to avoid any legal disputes or misunderstandings. Service accounts, tester experience, and number of tests are not essential elements of the scope documentation, although they may be relevant for other aspects of the penetration testing process.
Reference: The Official CompTIA PenTest+ Study Guide (Exam PT0-002), Chapter 1: Planning and Scoping Penetration Tests1; The Official CompTIA PenTest+ Student Guide (Exam PT0-002), Lesson 1: Planning and Scoping Penetration Tests2; What is the Scope of a Penetration Test?3
ion tester is attempting to get more people from a target company to download and run an executable.
Which of the following would be the.. :tive way for the tester to achieve this objective?
- A . Dropping USB flash drives around the company campus with the file on it
- B . Attaching the file in a phishing SMS that warns users to execute the file or they will be locked out of their accounts
- C . Sending a pretext email from the IT department before sending the download instructions later
- D . Saving the file in a common folder with a name that encourages people to click it
C
Explanation:
The most effective way for the tester to achieve this objective is to send a pretext email from the IT department before sending the download instructions later. A pretext email is an email that uses deception or impersonation to trick users into believing that it is from a legitimate source or authority, such as the IT department. A pretext email can be used to establish trust or rapport with the users, and then persuade them to perform an action or provide information that benefits the attacker. In this case, the tester can send a pretext email from the IT department that informs users about an important update or maintenance task that requires them to download and run an executable file later. The tester can then send another email with the download instructions and attach or link to the malicious executable file. The users may be more likely to follow these instructions if they have received a prior email from the IT department that prepared them for this action. The other options are not as effective ways for the tester to achieve this objective. Dropping USB flash drives around the company campus with the file on it may not reach many users, as they may not find or pick up the USB flash drives, or they may be suspicious of their origin or content.
A penetration tester is testing input validation on a search form that was discovered on a website.
Which of the following characters is the BEST option to test the website for vulnerabilities?
- A . Comma
- B . Double dash
- C . Single quote
- D . Semicolon
A penetration tester has gained access to the Chief Executive Officer’s (CEO’s) internal, corporate email. The next objective is to gain access to the network.
Which of the following methods will MOST likely work?
- A . Try to obtain the private key used for S/MIME from the CEO’s account.
- B . Send an email from the CEO’s account, requesting a new account.
- C . Move laterally from the mail server to the domain controller.
- D . Attempt to escalate privileges on the mail server to gain root access.
A penetration tester has gained access to the Chief Executive Officer’s (CEO’s) internal, corporate email. The next objective is to gain access to the network.
Which of the following methods will MOST likely work?
- A . Try to obtain the private key used for S/MIME from the CEO’s account.
- B . Send an email from the CEO’s account, requesting a new account.
- C . Move laterally from the mail server to the domain controller.
- D . Attempt to escalate privileges on the mail server to gain root access.
A client would like to have a penetration test performed that leverages a continuously updated TTPs framework and covers a wide variety of enterprise systems and networks.
Which of the following methodologies should be used to BEST meet the client’s expectations?
- A . OWASP Top 10
- B . MITRE ATT&CK framework
- C . NIST Cybersecurity Framework
- D . The Diamond Model of Intrusion Analysis
A penetration tester fuzzes an internal server looking for hidden services and applications and obtains the following output:
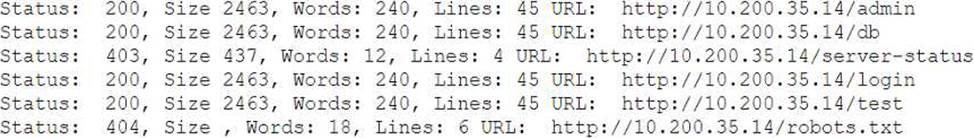
Which of the following is the most likely explanation for the output?
- A . The tester does not have credentials to access the server-status page.
- B . The admin directory cannot be fuzzed because it is forbidden.
- C . The admin, test, and db directories redirect to the log-in page.
- D . The robots.txt file has six entries in it.
A
Explanation:
The output shows that the server returned a 403 status code for the /server-status URL, which typically means "Forbidden." This often indicates that the resource exists but the server understands the request and refuses to authorize it, usually due to a lack of proper credentials or permissions to access the page.
A penetration tester has been hired to configure and conduct authenticated scans of all the servers on a software company’s network.
Which of the following accounts should the tester use to return the MOST results?
- A . Root user
- B . Local administrator
- C . Service
- D . Network administrator
A penetration tester has established an on-path position between a target host and local network services but has not been able to establish an on-path position between the target host and the Internet. Regardless, the tester would like to subtly redirect HTTP connections to a spoofed server IP.
Which of the following methods would BEST support the objective?
- A . Gain access to the target host and implant malware specially crafted for this purpose.
- B . Exploit the local DNS server and add/update the zone records with a spoofed A record.
- C . Use the Scapy utility to overwrite name resolution fields in the DNS query response.
- D . Proxy HTTP connections from the target host to that of the spoofed host.
