Practice Free PT0-002 Exam Online Questions
Which of the following is the most important to include in the scope of a wireless security assessment?
- A . Frequencies
- B . APs
- C . SSIDs
- D . Signal strengths
B
Explanation:
Access Points (APs) are crucial in a wireless security assessment as they are the main points through which devices connect to the network. Identifying and securing APs ensures network integrity and security.
Details:
The following line-numbered Python code snippet is being used in reconnaissance:
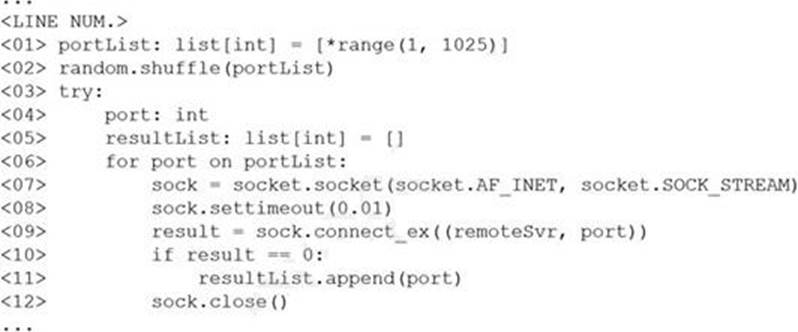
Which of the following line numbers from the script MOST likely contributed to the script triggering a “probable port scan” alert in the organization’s IDS?
- A . Line 01
- B . Line 02
- C . Line 07
- D . Line 08
A penetration tester was able to compromise a server and escalate privileges.
Which of the following should the tester perform AFTER concluding the activities on the specified target? (Choose two.)
- A . Remove the logs from the server.
- B . Restore the server backup.
- C . Disable the running services.
- D . Remove any tools or scripts that were installed.
- E . Delete any created credentials.
- F . Reboot the target server.
A penetration tester has been given an assignment to attack a series of targets in the 192.168.1.0/24 range, triggering as few alarms and countermeasures as possible.
Which of the following Nmap scan syntaxes would BEST accomplish this objective?
- A . nmap -sT -vvv -O 192.168.1.2/24 -PO
- B . nmap -sV 192.168.1.2/24 -PO
- C . nmap -sA -v -O 192.168.1.2/24
- D . nmap -sS -O 192.168.1.2/24 -T1
D
Explanation:
Reference: https://nmap.org/book/man-port-scanning-techniques.html
A penetration tester is contracted to attack an oil rig network to look for vulnerabilities. While conducting the assessment, the support organization of the rig reported issues connecting to corporate applications and upstream services for data acquisitions.
Which of the following is the MOST likely culprit?
- A . Patch installations
- B . Successful exploits
- C . Application failures
- D . Bandwidth limitations
A penetration tester completed a vulnerability scan against a web server and identified a single but severe vulnerability.
Which of the following is the BEST way to ensure this is a true positive?
- A . Run another scanner to compare.
- B . Perform a manual test on the server.
- C . Check the results on the scanner.
- D . Look for the vulnerability online.
During the reconnaissance phase, a penetration tester obtains the following output:
Reply from 192.168.1.23: bytes=32 time<54ms TTL=128
Reply from 192.168.1.23: bytes=32 time<53ms TTL=128
Reply from 192.168.1.23: bytes=32 time<60ms TTL=128
Reply from 192.168.1.23: bytes=32 time<51ms TTL=128
Which of the following operating systems is MOST likely installed on the host?
- A . Linux
- B . NetBSD
- C . Windows
- D . macOS
Which of the following would MOST likely be included in the final report of a static application-security test that was written with a team of application developers as the intended audience?
- A . Executive summary of the penetration-testing methods used
- B . Bill of materials including supplies, subcontracts, and costs incurred during assessment
- C . Quantitative impact assessments given a successful software compromise
- D . Code context for instances of unsafe type-casting operations
Which of the following would MOST likely be included in the final report of a static application-security test that was written with a team of application developers as the intended audience?
- A . Executive summary of the penetration-testing methods used
- B . Bill of materials including supplies, subcontracts, and costs incurred during assessment
- C . Quantitative impact assessments given a successful software compromise
- D . Code context for instances of unsafe type-casting operations
A penetration tester completed an assessment, removed all artifacts and accounts created during the test, and presented the findings to the client.
Which of the following happens NEXT?
- A . The penetration tester conducts a retest.
- B . The penetration tester deletes all scripts from the client machines.
- C . The client applies patches to the systems.
- D . The client clears system logs generated during the test.
