Practice Free PL-600 Exam Online Questions
A bank is transforming its operations by using Microsoft Power Platform.
You lead a requirements workshop for the bank. Several users request Microsoft Teams dialing capabilities in a canvas app so that they can call clients and record and transcribe client conversations.
You need to determine the feasibility of this requirement.
- A . technical
- B . regulatory
- C . priority
- D . usage of the feature
- E . level of effort
HOTSPOT
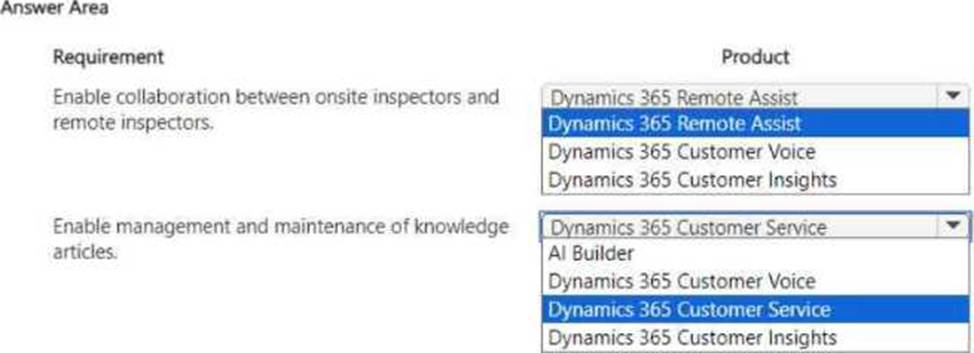
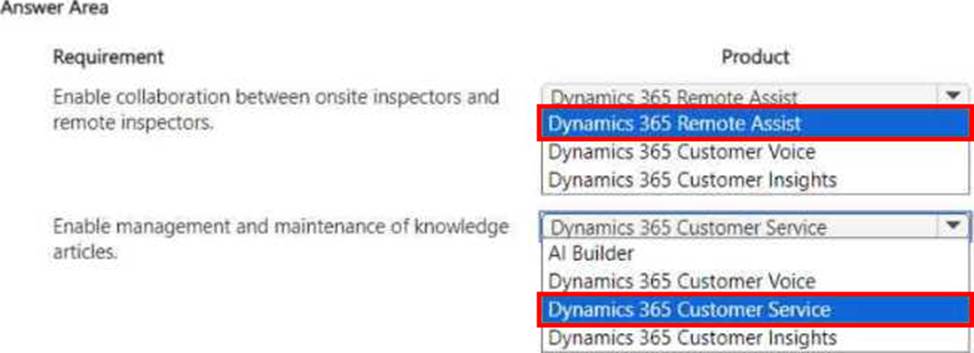
A company uses Dynamics 365 Field Service to manage onsite services provided by frontline workers.
The company has the following requirements:
• Onsite inspectors must be able to collaborate with remote inspectors to carry out inspections.
• Customer support teams must be able to easily manage and maintain knowledge articles based on customer questions and feedback.
You need to recommend a product that can be implemented for each requirement.
Which products should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point
HOTSPOT
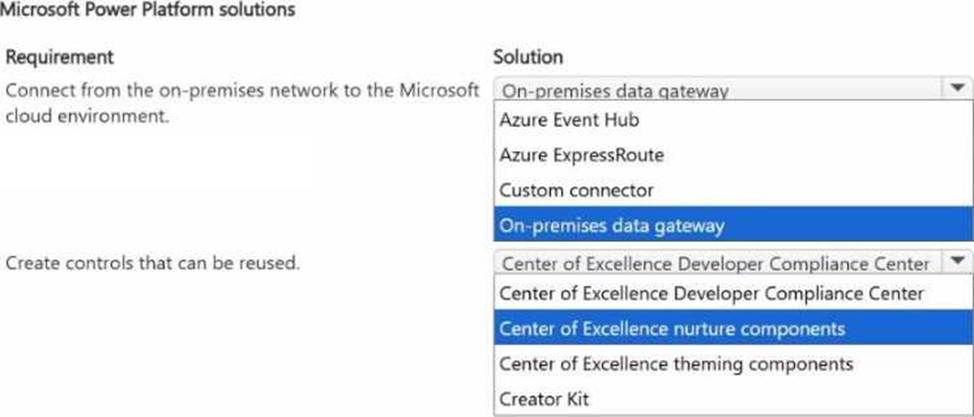
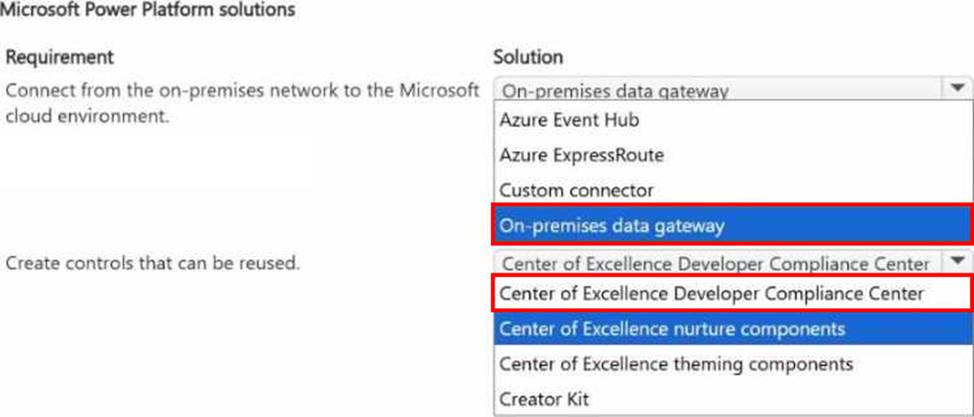
You are implementing a Microsoft Power Platform project for a company.
The company has the following requirements for the project:
• Employees must be able to connect to the Microsoft cloud environment from their on-premises network by using a private connection.
• Employees must be able to create controls for applications that can be reused in applications and projects
You need to implement the appropriate solutions.
What should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
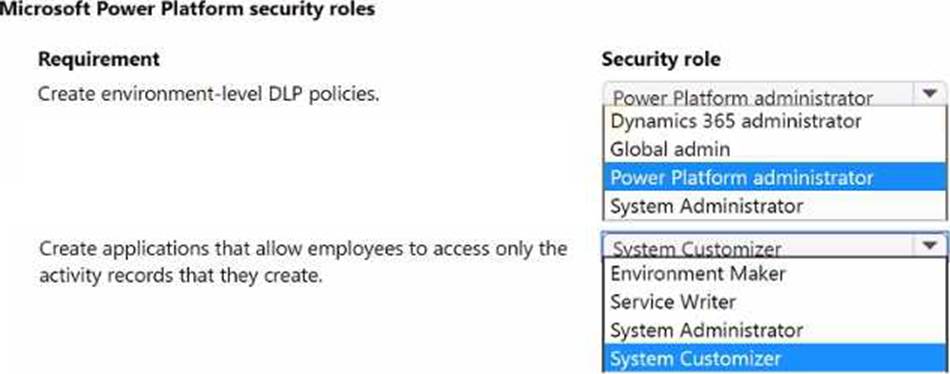
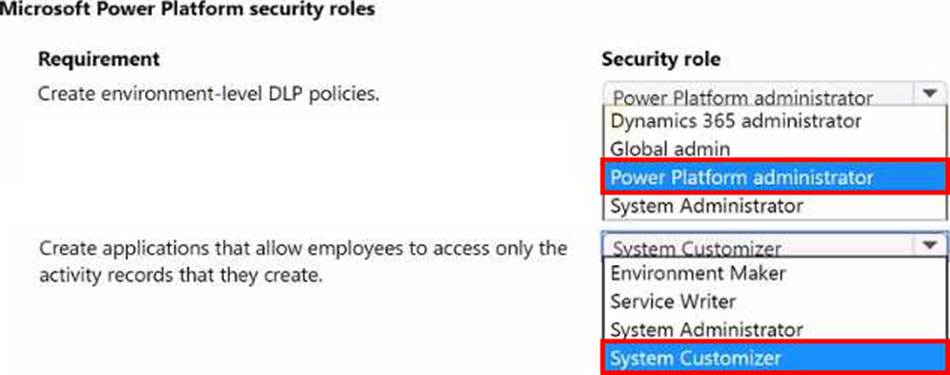
A company has a Power Apps app and uses Microsoft Dataverse for data storage.
The company plans to provide employees the ability to create the following:
• Data loss prevention (DLP) policies that are at the environment level.
• Applications that allow employees to access only the activity records that they create.
You need to identify the security roles that the employees require.
Which security roles should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
DRAG DROP
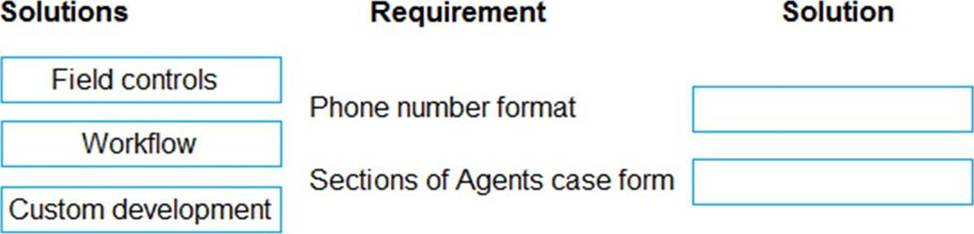
You need to propose a solution for form requirements.
What should you recommend? To answer, drag the appropriate solutions to the correct requirements. Each solution may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
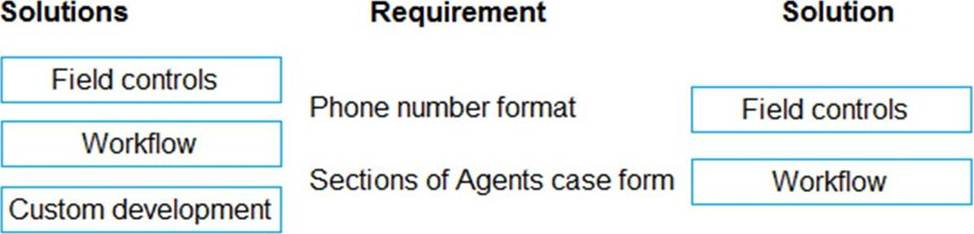
Explanation:
Box 1: Field controls
You must standardize the format used by agents to enter customer phone numbers.
Box 2: Workflow
Log issues as cases. The case form must show variable sections based on the case type.
You are designing an integration between an Azure SQL database and a model-driven app.
You have the following requirements:
• Audit updates to the data.
• Assign security role access to tables at the user level.
• Assign security role access to tables at the organization level.
• Enable change tracking.
• Add and update data.
You need to implement virtual tables.
Which two requirements can you meet by using virtual tables? Each correct answer presents a complete solution. NOTE Each correct selection is worth one point.
- A . Enable change tracking.
- B . Assign security role access to tables at the user level.
- C . Add and update data.
- D . Assign security role access to tables at the organization level.
- E . Audit updates to the data.
You are evaluating company data.
The data must be migrated to Microsoft Dataverse.
You need to recommend the process to ensure clean data for the migration.
Solution: Eliminate duplicate records.
Does the solution meet the goal?
- A . Yes
- B . No
A company uses Microsoft Power Platform and Microsoft Dataverse. The company enables auditing in the environment, tables, and at column level for all eligible tables and columns. You need to ensure audit history is available for all users.
What should you do?
- A . Add the View audit history privilege to the user’s security role.
- B . Enable log access in the Microsoft Power Platform admin center.
- C . Remove auditing from the required tables, and then re-enable it.
- D . Add the View audit partitions privilege to the user’s security role.
DRAG DROP
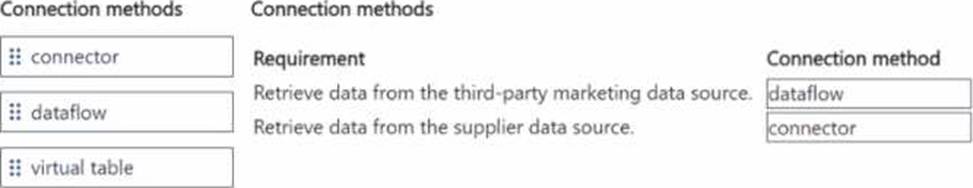
You need to configure Microsoft Dataverse to retrieve external data for the sales and construction departments.
Which connection methods should you use? To answer, move the appropriate connection methods to the correct requirements. You may use each connection method once, more than once, or not at all. You may need to move the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
A company uses a third-party cloud-based app to make real-time business decisions. The app has a RESTful API.
You must design a Microsoft Power Platform solution that interacts with the third-party app. Changes made in the Microsoft Power Platform solution must be reflected in the cloud app.
You need to recommend technologies to integrate the Microsoft Power Platform solution with the cloud app.
Which two technologies should you recommend? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Scheduled Power Automate cloud flow with a custom connector to the cloud app
- B . Power Virtual Agents
- C . Custom plug-on registered with Microsoft Dataverse
- D . Model-driven app
C, D
Explanation:
A: To enable Logic Apps, Power Automate, or Power Apps to communicate with the REST or SOAP API, use a custom connector, which is a wrapper around a REST API (Logic Apps also supports SOAP APIs).
C: Custom APIs are a powerful way to connect to any existing API, hosted anywhere, from PowerApps. You do not need a PowerApps Enterprise subscription to register or use a Custom API.
Custom APIs are RESTful endpoints that you can connect to and use from PowerApps. All you’ll need is a Swagger definition file for your endpoint.
Reference:
https://docs.microsoft.com/en-us/power-platform/guidance/architecture/real-world-examples/custom-connector-canvas
https://powerapps.microsoft.com/hr-hr/blog/register-and-use-custom-apis-in-powerapps/
