Practice Free PK0-005 Exam Online Questions
As a result of an approved change, the project manager updates the project plan with the newest project end date.
Which of the following change control processes should the project manager complete NEXT?
- A . Document the request in the change control log.
- B . Communicate the change deployment.
- C . Conduct an impact assessment.
- D . Implement the change.
B
Explanation:
The project manager should communicate the change deployment next after updating the project plan with the newest project end date as a result of an approved change. Communicating the change deployment involves informing all relevant parties about when and how the change will be implemented and what are the expected outcomes and benefits. Communicating the change deployment can help to ensure alignment, readiness, and support for the change and avoid any confusion or resistance.
How does data discovery assist with data classification’?
- A . It shows where specific data is stored
- B . It automatically classifies data by keywords
- C . It helps to identify the data owner
- D . It provides assurance of data integrity
A
Explanation:
Data discovery is the process of finding and analyzing data across an organization’s data sources, such as databases, files, cloud services, and applications12. Data discovery can assist with data classification, which is the process of assigning labels and categories to data based on its sensitivity, value, and risk34.
By showing where specific data is stored, data discovery can help to:
Identify the location and scope of sensitive data, such as personal, financial, or health information, that may require special protection or compliance measures56.
Evaluate the data quality, accuracy, and relevance for different purposes and users78.
Optimize the data storage, access, and governance policies and practices910.
Reference = CompTIA Project+ Certification Study Guide, CompTIA Project+ Certification Exam Objectives, What is Data Discovery and Classification?1, Data Discovery and Classification: Working Hand in Hand2, Why Data Discovery and Classification are Important3, Data Discovery & Classification4, Data Discovery and Classification: The First Step to Data Security5, Data Discovery and Classification: A Key Component of Data Protection6, Data Discovery and Classification: The Foundation of Data Quality7, Data Discovery and Classification: The Key to Data Governance8, Data Discovery and Classification: The Essential Step to Data Optimization9, Data Discovery and Classification: The Best Practice for Data Management10
Which of the following would be MOST beneficial to do before a call to ensure all meeting items are addressed and the correct participants attend?
- A . Assign action items to attendees.
- B . Distribute an agenda.
- C . Email the minutes from the previous meeting.
- D . Schedule a convenient time.
B
Explanation:
The project manager should distribute an agenda before a call to ensure all meeting items are addressed and the correct participants attend. An agenda is a document that outlines the purpose, topics, and objectives of a meeting. It also includes information such as date, time, duration, location, attendees, and roles. Distributing an agenda can help to prepare the participants for the meeting, set clear expectations, and facilitate a productive and focused discussion12
Which of the following items must be protected as Pll? (Select TWO).
- A . Job title
- B . Home address
- C . Work phone number
- D . Time zone
- E . Date of birth
- F . Blood type
B,E
Explanation:
Home address and date of birth must be protected as personally identifiable information (PII). PII is any information that can be used to identify, contact, or locate an individual person, either alone or in combination with other sources. PII can include information such as name, email address, phone number, social security number, passport number, driver’s license number, bank account number, credit card number, biometric data, medical records, etc. PII must be protected from unauthorized access, use, disclosure, modification, or destruction to prevent identity theft, fraud, or other malicious activities that may harm the individual’s privacy or security.
A company asks some vendors to provide a solution for its specific needs.
Which of the following documents should the company provide?
- A . RFP
- B . RFQ
- C . RFB
- D . RFI
A
Explanation:
A Request for Proposal (RFP) is a document issued by an organization to solicit proposals from potential vendors for a specific solution or service. It outlines the organization’s requirements and criteria for evaluation, allowing vendors to propose how they would meet those needs. An RFP is appropriate when the company seeks detailed proposals for a solution to its specific needs.
According to the CompTIA Project+ PK0-005 exam objectives, under Domain 3.4: Explain important project procurement and vendor selection concepts, understanding the use of RFPs is essential for effective procurement management.
Which of the following cloud models is designed to provide compute, storage, and networking resources on demand?
- A . Software as a service
- B . Infrastructure as a service
- C . Data as a service
- D . Platform as a service
B
Explanation:
Infrastructure as a service (IaaS) is a cloud model that provides on-demand access to cloud-hosted physical and virtual servers, storage, and networking resources. IaaS customers can provision, configure, and use these resources as they would use on-premises hardware, but without the hassle of purchasing, installing, managing, and maintaining them. The cloud service provider owns, manages, and maintains the hardware and computing resources in its own data centers, and charges the customers based on their usage. IaaS is suitable for customers who need flexibility, scalability, and control over their IT infrastructure, and who want to avoid the high costs and complexity of owning and operating their own hardware.
The other options are not correct because:
Software as a service (SaaS) is a cloud model that provides on-demand access to ready-to-use, cloud-hosted application software. SaaS customers do not need to install, update, or maintain the software, as the cloud service provider handles all the technical aspects. SaaS is suitable for customers who need to access common applications, such as email, office productivity, or customer relationship management, without worrying about the underlying infrastructure or platform.
Data as a service (DaaS) is a cloud model that provides on-demand access to cloud-hosted data sources, such as databases, data warehouses, or data lakes. DaaS customers can query, analyze, and visualize the data, as well as integrate it with other applications or services, using APIs or web interfaces. DaaS is suitable for customers who need to leverage data from various sources, such as social media, IoT devices, or third-party providers, without having to store, manage, or process the data themselves.
Platform as a service (PaaS) is a cloud model that provides on-demand access to a complete, ready-to-use, cloud-hosted platform for developing, running, maintaining, and managing applications. PaaS customers can use the platform’s tools, frameworks, libraries, and services to create and deploy applications, without having to worry about the underlying infrastructure or software. PaaS is suitable for customers who need to develop, test, and deploy applications quickly and efficiently, and who want to take advantage of the cloud’s scalability, reliability, and security
features.
Reference = IaaS vs. PaaS vs. SaaS; AWS Fundamentals: Understanding Compute, Storage, Database, Networking & Security; What are the different types of cloud computing?; What is Cloud Storage and How to Use It
A project team was instructed to refurbish old desktops.
The following provides the details of the issues observed:
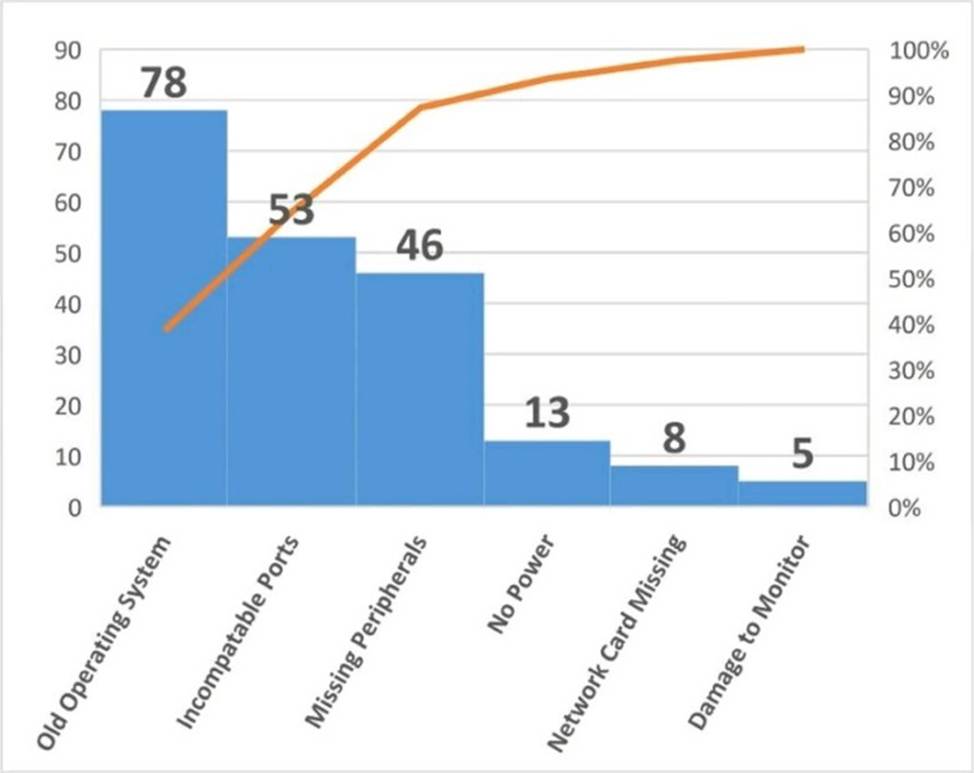
Which of the following issues should be addressed FIRST?
- A . Replace missing peripherals because this process can be easy and less costly.
- B . An old operating system issue has the most amount of occurrences.
- C . Damage to the monitor has the highest percentage.
- D . Address each issue as discovered to avoid rework.
C
Explanation:
The project manager should address the issue of damage to the monitor first because it has the highest percentage (40%) among the issues observed. This means that it is the most frequent and severe issue that affects the quality and functionality of the refurbished desktops. Addressing this issue first can help to improve customer satisfaction, reduce rework, and avoid waste1
A project team evaluated the performance of a new reporting system and the quantity of queries to be processed during predetermined time stamps.
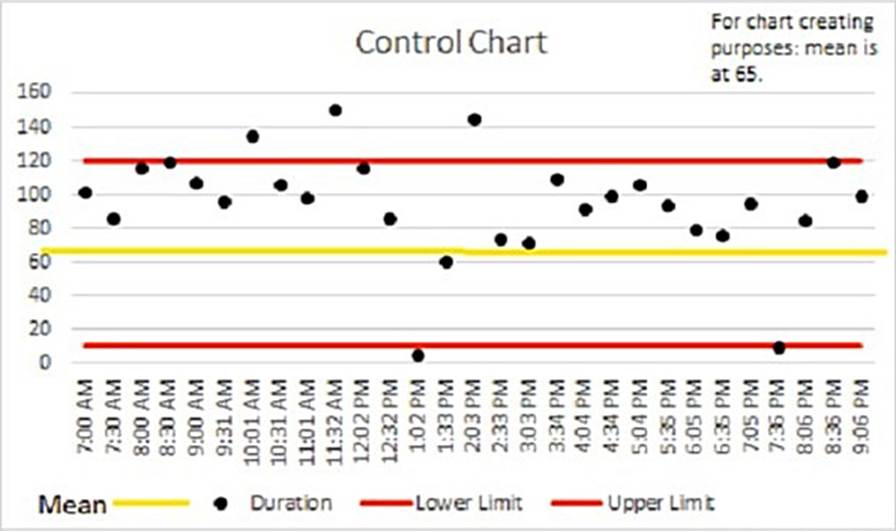
Which of the following is the current status of the process?
- A . Based on the rule of seven, the process is under control
- B . The amount of data is insufficient to determine if quality is low.
- C . The process is out of control and should be revised.
- D . The goal should be adjusted since most of the data points are close to the lower limit.
C
Explanation:
The process is out of control and should be revised. The project manager can use the rule of seven to determine the status of the process based on the control chart. The rule of seven states that if seven or more consecutive measurements fall on one side of the mean that there’s an assignable cause that needs investigation. In this case, the last seven data points are all below the mean, which indicates that the process is out of control and in need of adjustment12
A company is creating a new technology. The company is concerned that the project details could be compromised if a cloud service is used, and another company could launch the technology before the current projected delivery.
Which of the following can the company do to minimize this risk?
- A . Use an on-premises project management scheduling tool.
- B . Limit access to members of the project team.
- C . Mandate overtime to get the project completed sooner.
- D . Ensure all team members have signed a non-disclosure agreement.
B
Explanation:
Limiting access to members of the project team is a way to minimize the risk of compromising the project details if a cloud service is used. This means that only authorized and trusted individuals can access, view, modify, or share the project information stored in the cloud. Limiting access can prevent unauthorized access, data leakage, cyberattacks, or espionage from external parties who might want to steal or sabotage the new technology. Limiting access can also reduce the risk of human error, negligence, or misconduct from internal parties who might accidentally or intentionally expose or misuse the project information123.
Reference = CompTIA Project+ Study Guide: Exam PK0-005, 3rd Edition, Chapter 4: Project Communications, p. 143; Cloud Security Risks and How to Mitigate Them | Cloud Academy; Cloud Security: How to Secure Your Data in the Cloud |
Kaspersky; Cloud Security: Best Practices for Securing Cloud Computing | Cloud Security Alliance
A company is creating a new technology. The company is concerned that the project details could be compromised if a cloud service is used, and another company could launch the technology before the current projected delivery.
Which of the following can the company do to minimize this risk?
- A . Use an on-premises project management scheduling tool.
- B . Limit access to members of the project team.
- C . Mandate overtime to get the project completed sooner.
- D . Ensure all team members have signed a non-disclosure agreement.
B
Explanation:
Limiting access to members of the project team is a way to minimize the risk of compromising the project details if a cloud service is used. This means that only authorized and trusted individuals can access, view, modify, or share the project information stored in the cloud. Limiting access can prevent unauthorized access, data leakage, cyberattacks, or espionage from external parties who might want to steal or sabotage the new technology. Limiting access can also reduce the risk of human error, negligence, or misconduct from internal parties who might accidentally or intentionally expose or misuse the project information123.
Reference = CompTIA Project+ Study Guide: Exam PK0-005, 3rd Edition, Chapter 4: Project Communications, p. 143; Cloud Security Risks and How to Mitigate Them | Cloud Academy; Cloud Security: How to Secure Your Data in the Cloud |
Kaspersky; Cloud Security: Best Practices for Securing Cloud Computing | Cloud Security Alliance
