Practice Free PK0-005 Exam Online Questions
As part of a global project, the project manager wants to ensure there is no disruption in the day-to-day performance among project team members around the world.
Which of the following should the project manager consider doing as part of the project planning?
- A . Monitoring the project team
- B . Creating a handoff process
- C . Colocating the project team
- D . Creating a separate statement of work
During a brainstorming session, a project team is elaborating on what caused the unexpected crash of the website that the team was developing.
Given the following:
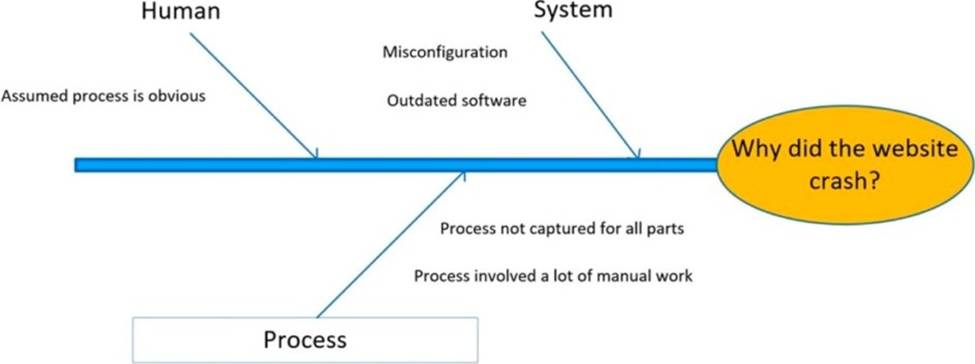
Which of the following was the initial cause of the issue?
- A . Inadequate memory
- B . Incorrect configuration
- C . Lack of infrastructure
- D . Inadequate instructions
B
Explanation:
Incorrect configuration was the initial cause of the issue that caused the unexpected crash of the website that the team was developing. The diagram given is an example of a fishbone diagram or a cause-and-effect diagram that shows the possible causes of a problem or effect. The diagram has four main categories: people, process, technology, and environment. Each category has subcategories that list specific factors that may contribute to the problem or effect. The diagram shows that incorrect configuration under technology was marked as an initial cause of website crash.
A project manager has been very diligent in maintaining the version control for the documentation of requirements.
Which of the following tools is the project manager using?
- A . Multiauthoring software
- B . Word processor
- C . Real-time polling
- D . Conferencing platforms
A
Explanation:
The project manager is using multiauthoring software to maintain the version control for the documentation of requirements. Multiauthoring software is a type of software that allows multiple users to create, edit, and collaborate on documents simultaneously. It also provides features such as tracking changes, commenting, reviewing, and merging versions. Multiauthoring software can help to improve the quality, accuracy, and consistency of documents and facilitate communication and feedback among stakeholders. Examples of multiauthoring software include Google Docs, Microsoft Word Online, and Confluence34
A project manager buys an extended warranty for a set of servers.
Which of the following risk management strategies is the manager using?
- A . Transfer
- B . Avoid
- C . Accept
- D . Mitigate
A
Explanation:
Transfer is a risk management strategy that involves shifting the responsibility or impact of a risk to a third party, such as an insurance company, a vendor, or a contractor1. By buying an extended warranty for a set of servers, the project manager is transferring the risk of server failure or malfunction to the warranty provider, who will cover the cost of repair or replacement in case of a risk event. This way, the project manager reduces the exposure and liability of the project to the risk, while still retaining some level of accountability and oversight2.
Reference = CompTIA Project+ PK0-005 Certification Study Guide, Chapter 8: Planning Projects Part 4, page 245; 4 Risk Management Strategies for Successful Project Execution, Risk transferring section; How to Manage Project Risk: A 5-Step Guide, Risk treatment section.
Which of the following BEST identifies the intent and purpose of a project closeout report?
- A . To provide documentation of lessons learned
- B . To document variances from the initial project baseline
- C . To validate that a project has been successfully completed
- D . To release resources and terminate all access rights
C
Explanation:
To validate that a project has been successfully completed. The intent and purpose of a project closeout report is to validate that a project has been successfully completed and to summarize the goals, objectives, and outcomes of the project, as well as the lessons learned and the feedback from stakeholders. A project closeout report is a document that is submitted at the end of a project to officially conclude it and release the resources and contracts involved. It is useful for evaluating the project’s success and improving the performance of future projects12
A project team is reviewing the project plan and related documents and identifies tasks that could be spread into smaller deliverables.
Which of the following documents should the team edit first?
- A . Risk assessment
- B . Preliminary scope statement
- C . Work breakdown structure
- D . Milestone chart
C
Explanation:
The Work Breakdown Structure (WBS) is a hierarchical decomposition of the total scope of work to accomplish project objectives. If tasks can be broken into smaller deliverables, the WBS should be updated first to reflect these changes.
According to the CompTIA Project+ PK0-005 exam objectives, under Domain 2.2: Given a scenario, determine the appropriate scope management activities, maintaining an accurate WBS is crucial for effective scope management.
A project sponsor is struggling to provide the latest project status information on a weekly executive call.
Which of the following should be reviewed?
- A . Meeting cadence
- B . Gap analysis
- C . Dashboard
- D . Adoption training
C
Explanation:
A dashboard is a visual tool that displays key project metrics and indicators in a single view12. A dashboard can help a project sponsor to provide the latest project status information on a weekly executive call by showing the project progress, budget, schedule, risks, issues, and milestones in a clear and concise way34. A dashboard can also facilitate communication, collaboration, and decision making among project stakeholders56. A dashboard should be reviewed and updated regularly to reflect the current state of the project7.
Reference = CompTIA Project+ Certification Study Guide8, CompTIA Project+ Certification Exam Objectives9, Write a Project Status Report in 8 Steps + Template [2023] • Asana6, Project Status Reports: 9 Easy Steps & Examples [+ Template]7, How To Write a Project Status Report (Definition and Steps)8, How to Write a Project Status Report [Template Included] – Toggl9, What Is a Project Status? Definition and Key Terms – Indeed10
During the testing process, testers have found multiple bugs that could jeopardize the project commitment date.
Which of the following tools should the project manager use first to update the findings?
- A . Defect log
- B . Change log
- C . Issue log
- D . Risk log
A project scheduler updates the project status with the following information: SPI = 1.25 and CPI = 0.85.
Which of the following can the project manager infer about the current project status?
- A . The project is ahead of schedule and under budget.
- B . The project is behind schedule and over budget
- C . The project is ahead of schedule and over budget.
- D . The project is behind schedule and under budget
Which of the following statements best describes a content management system?
- A . A system to manage electronic signatures and document workflow
- B . A system to manage database integration and provide messaging services
- C . A system to manage shared data on the web, allowing multiple contributors to create, edit, and publish
- D . A system to manage documents archival, such as emails, spreadsheets, and support tickets
C
Explanation:
A content management system (CMS) is a software application that allows users to create, manage, and deliver content via digital channels, such as websites, blogs, or social media12. A CMS enables multiple contributors to access, edit, and publish content without requiring technical knowledge or coding skills34. A CMS also provides features such as templates, workflows, media libraries, and analytics to help users design, organize, and optimize their content56.
Reference = CompTIA Project+ Certification Study Guide7, CompTIA Project+ Certification Exam Objectives8, What Is a Content Management System (CMS)?1, What is a Content Management System (CMS) | Oracle2, What is a Content Management System (CMS)? | Adobe Basics3, What is a CMS?4, What is a Content Management System?5, Content Management System (CMS) – Definition from Techopedia6
