Practice Free NSE7_EFW-7.2 Exam Online Questions
Which two statements about ADVPN are true? (Choose two.)
- A . You must disable add-route in the hub.
- B . AllFortiGate devices must be in the same autonomous system (AS).
- C . The hub adds routes based on IKE negotiations.
- D . You must configure phase 2 quick mode selectors to 0.0.0.0 0.0.0.0.
CD
Explanation:
C. The hub adds routes based on IKE negotiations: This is part of the ADVPN functionality where the hub learns about the networks behind the spokes and can add routes dynamically based on the IKE negotiations with the spokes.
D. You must configure phase 2 quick mode selectors to 0.0.0.0 0.0.0.0: This wildcard setting in the phase 2 selectors allows any-to-any tunnel establishment, which is necessary for the dynamic creation of spoke-to-spoke tunnels.
These configurations are outlined in Fortinet’s documentation for setting up ADVPN, where the hub’s role in route control and the use of wildcard selectors for phase 2 are emphasized to enable dynamic tunneling between spokes.
Refer to the exhibit, which contains a partial BGP combination.
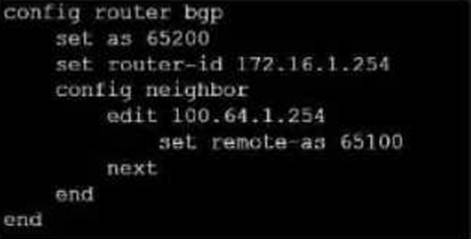
You want to configure a loopback as the OGP source.
Which two parameters must you set in the BGP configuration? (Choose two)
- A . ebgp-enforce-multihop
- B . recursive-next-hop
- C . ibgp-enfoce-multihop
- D . update-source
A, D
Explanation:
To configure a loopback as the BGP source, you need to set the “ebgp-enforce-multihop” and “update-source” parameters in the BGP configuration. The “ebgp-enforce-multihop” allows EBGP connections to neighbor routers that are not directly connected, while “update-source” specifies the IP address that should be used for the BGP session1.
Reference: BGP on loopback, Loopback interface, Technical Tip: Configuring EBGP Multihop Load-Balancing, Technical Tip: BGP routes are not installed in routing table with loopback as update source
How are bulk configuration changes made using FortiManager CLI scripts? (Choose two.)
- A . When run on the Device Database, changes are applied directly to the managed FortiGate device.
- B . When run on the Remote FortiGate directly, administrators do not have the option to review the changes prior to installation.
- C . When run on the All FortiGate in ADOM, changes are automatically installed without the creation of a new revision history.
- D . When run on the Policy Package, ADOM database, you must use the installation wizard to apply the changes to the managed FortiGate device.
You want to configure faster failure detection for BGP
Which parameter should you enable on both connected FortiGate devices?
- A . Ebgp-enforce-multihop
- B . bfd
- C . Distribute-list-in
- D . Graceful-restart
B
Explanation:
BFD (Bidirectional Forwarding Detection) is a protocol that provides fast failure detection for BGP by sending periodic messages to verify the connectivity between two peers1. BFD can be enabled on both connected FortiGate devices by using the command set bfd enable under the BGP configuration2.
Reference: = Technical Tip: FortiGate BFD implementation and examples …, Configure BGP | FortiGate / FortiOS 7.0.2 – Fortinet Documentation
Exhibit.
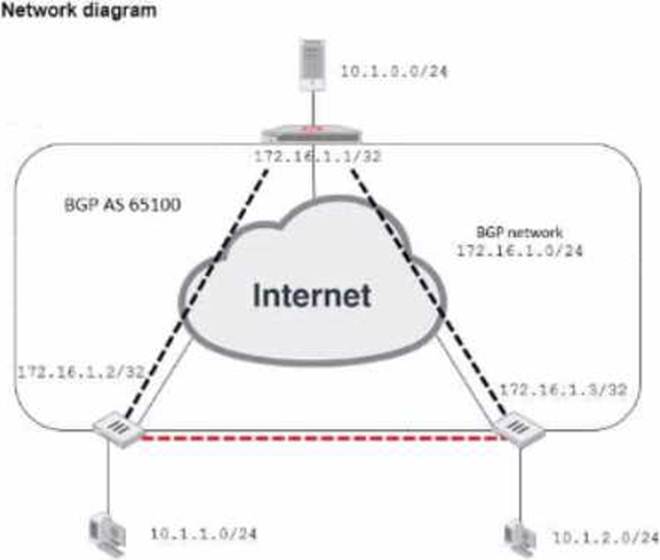
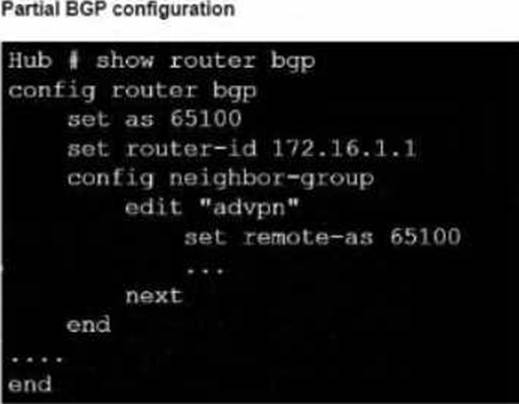
Refer to the exhibit, which contains an ADVPN network diagram and a partial BGP con figuration.
Which two parameters Should you configure in config neighbor range? (Choose two.)
- A . set prefix 172.16.1.0 255.255.255.0
- B . set route reflector-client enable
- C . set neighbor-group advpn
- D . set prefix 10.1.0 255.255.254.0
C, D
Explanation:
In the ADVPN configuration for BGP, you should specify the prefix that the neighbors can advertise. Option A is correct as you would configure the BGP network prefix that should be advertised to the neighbors, which matches the BGP network in the diagram. Option C is also correct since you should reference the neighbor group configured for the ADVPN setup within the BGP configuration.
Exhibit.
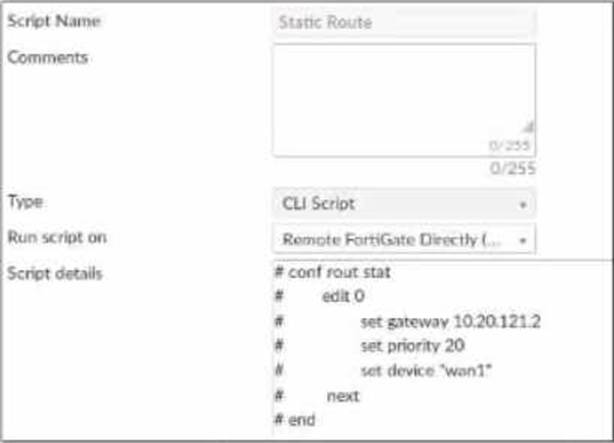
Refer to the exhibit, which contains a CLI script configuration on fortiManager. An administrator configured the CLI script on FortiManager rut the script tailed to apply any changes to the managed device after being executed.
What are two reasons why the script did not make any changes to the managed device? (Choose two)
- A . The commands that start with the # sign did not run.
- B . Incomplete commands can cause CLI scripts to fail.
- C . Static routes can be added using only TCI scripts.
- D . CLI scripts must start with #!.
AB
Explanation:
The commands that start with the # sign did not run because they are treated as comments in the CLI script. Incomplete commands can cause CLI scripts to fail because they are not recognized by the FortiGate device. The other options are incorrect because static routes can be added using CLI or GUI, and CLI scripts do not need to start with #!.
Reference: Configuring custom scripts | FortiManager 7.2.0 – Fortinet Documentation, section “CLI script syntax”.
Refer to the exhibit, which contains a partial OSPF configuration.
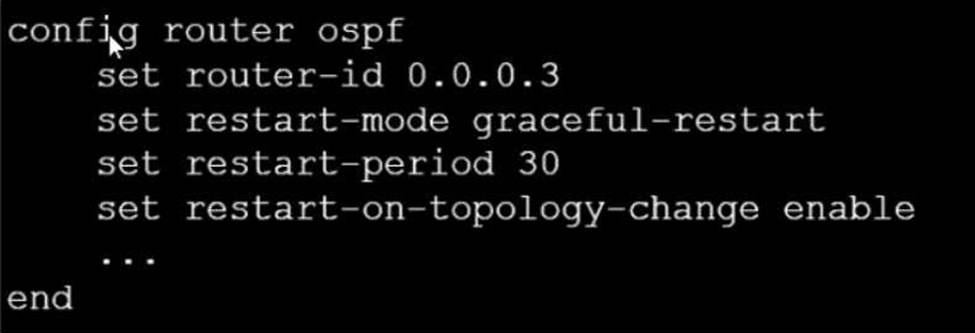
What can you conclude from this output?
- A . Neighbors maintain communication with the restarting router.
- B . The router sends grace LSAs before it restarts.
- C . FortiGate restarts if the topology changes.
- D . The restarting router sends gratuitous ARP for 30 seconds.
A
Explanation:
From the partial OSPF (Open Shortest Path First) configuration output:
B. The router sends grace LSAs before it restarts: This is implied by the command ‘set restart-mode graceful-restart’. When OSPF is configured with graceful restart, the router sends grace LSAs (Link State Advertisements) to inform its neighbors that it is restarting, allowing for a seamless transition without recalculating routes.
Fortinet documentation on OSPF configuration clearly states that enabling graceful restart mode allows the router to maintain its adjacencies and routes during a brief restart period.
Which two statements about the neighbor-group command are true? (Choose two.)
- A . You can configure it on the GUI.
- B . It applies common settings in an OSPF area.
- C . It is combined with the neighbor-range parameter.
- D . You can apply it in Internal BGP (IBGP) and External BGP (EBGP).
BD
Explanation:
The neighbor-group command in FortiOS allows for the application of common settings to a group of neighbors in OSPF, and can also be used to simplify configuration by applying common settings to both IBGP and EBGP neighbors. This grouping functionality is a part of the FortiOS CLI and is documented in the Fortinet CLI reference.
Exhibit.
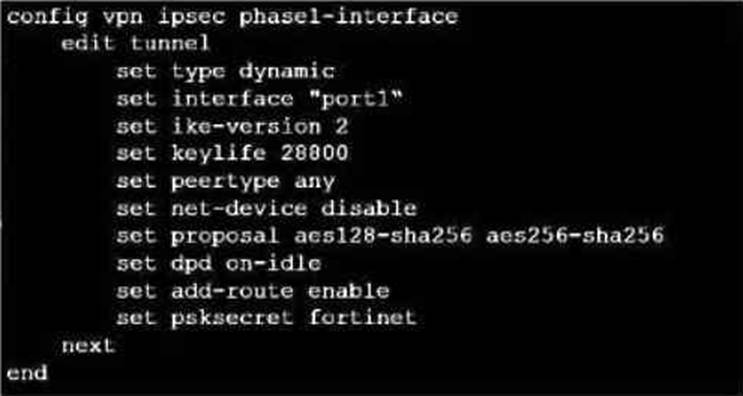
Refer to the exhibit, which contains a partial VPN configuration.
What can you conclude from this configuration1?
- A . FortiGate creates separate virtual interfaces for each dial up client.
- B . The VPN should use the dynamic routing protocol to exchange routing information Through the tunnels.
- C . Dead peer detection s disabled.
- D . The routing table shows a single IPSec virtual interface.
C
Explanation:
The configuration line “set dpd on-idle” indicates that dead peer detection (DPD) is set to trigger only when the tunnel is idle, not actively disabled1.
Reference: FortiGate IPSec VPN User Guide – Fortinet Document Library
From the given VPN configuration, dead peer detection (DPD) is set to ‘on-idle’, indicating that DPD is enabled and will be used to detect if the other end of the VPN tunnel is still alive when no traffic is detected. Hence, option C is incorrect. The configuration shows the tunnel set to type ‘dynamic’, which does not create separate virtual interfaces for each dial-up client (A), and it is not specified that dynamic routing will be used (B). Since this is a phase 1 configuration snippet, the routing table aspect (D) cannot be concluded from this alone.
You want to improve reliability over a lossy IPSec tunnel.
Which combination of IPSec phase 1 parameters should you configure?
- A . fec-ingress and fec-egress
- B . Odpd and dpd-retryinterval
- C . fragmentation and fragmentation-mtu
- D . keepalive and keylive
B
Explanation:
For improving reliability over a lossy IPSec tunnel, the fragmentation and fragmentation-mtu parameters should be configured. In scenarios where there might be issues with packet size or an unreliable network, setting the IPsec phase 1 to allow for fragmentation will enable large packets to be broken down, preventing them from being dropped due to size or poor network quality. The fragmentation-mtu specifies the size of the fragments. This is aligned with Fortinet’s recommendations for handling IPsec VPN over networks with potential packet loss or size limitations.
