Practice Free NSE5_FSM-6.3 Exam Online Questions
An administrator is using SNMP and WMI credentials to discover a Windows device.
How will the WMI method handle this?
- A . WMI method will collect only traffic and IIS logs.
- B . WMI method will collect only DNS logs.
- C . WMI method will collect only DHCP logs.
- D . WMI method will collect security, application, and system events logs.
A
Explanation:
WMI Method: Windows Management Instrumentation (WMI) is a set of specifications from Microsoft for consolidating the management of devices and applications in a network.
Log Collection: WMI is used to collect various types of logs from Windows devices.
Security Logs: Contains records of security-related events such as login attempts and resource access.
Application Logs: Contains logs generated by applications running on the system.
System Logs: Contains logs related to the operating system and its components.
Comprehensive Data Collection: By using WMI, FortiSIEM can gather a wide range of event logs that are crucial for monitoring and analyzing the security and performance of Windows devices.
Reference: FortiSIEM 6.3 User Guide, Data Collection Methods section, which details the use of WMI for collecting event logs from Windows devices.
In which state can a device be moved into the CMDB to prevent monitoring log collection?
- A . Unmanaged
- B . Unapproved
- C . Pending
- D . Void
How is a subpattern for a rule defined?
- A . Filters, Aggregation, Group by definitions
- B . Filters, Group By definitions, Threshold
- C . Filters, Threshold, Time Window definitions
- D . Filters, Aggregation, Time Window definitions
In the CMDB page for a network device, the Configuration tab is unexpectedly empty.
Which is a possible reason?
- A . The SNMP credential was a read-only credential.
- B . A Telnet/SSH credential was not configured for discovery.
- C . Configuration push is not enabled on the network device.
- D . Syslog was only being sent to a worker.
Which FortiSIEM feature must you use to produce a report on which FortiGate devices in your environment are running which firmware version?
- A . Run an analytic search.
- B . Run a query using the Inventory tab.
- C . Run a baseline report.
- D . Run a CMDB report
B
Explanation:
Feature Overview: FortiSIEM provides several tools for querying and reporting on device information within an environment.
Inventory Tab: The Inventory tab is specifically designed to display detailed information about devices, including their firmware versions.
Query Functionality: Within the Inventory tab, you can run queries to filter and display devices based on specific attributes, such as the firmware version for FortiGate devices.
Report Generation: By running a query in the Inventory tab, you can produce a report that lists the FortiGate devices and their corresponding firmware versions.
Reference: FortiSIEM 6.3 User Guide, Inventory Management section, explains how to use the Inventory tab to query and report on device attributes.
IF the reported packet loss is between 50% and 98%. which status is assigned to the device in the Availability column of summary dashboard?
- A . Up status is assigned because of received packets.
- B . Critical status is assigned because of reduction in number of packets received.
- C . Degraded status is assigned because of packet loss
- D . Down status is assigned because of packet loss.
C
Explanation:
Device Status in FortiSIEM: FortiSIEM assigns different statuses to devices based on their operational state and performance metrics.
Packet Loss Impact: The reported packet loss percentage directly influences the status assigned to a device. Packet loss between 50% and 98% indicates significant network issues that affect the device’s performance.
Degraded Status: When packet loss is between 50% and 98%, FortiSIEM assigns a "Degraded" status to the device. This status indicates that the device is experiencing substantial packet loss, which impairs its performance but does not render it completely non-functional.
Reasoning: The "Degraded" status helps administrators identify devices with serious performance issues that need attention but are not entirely down.
Reference: FortiSIEM 6.3 User Guide, Device Availability and Status section, explains the criteria for assigning different statuses based on performance metrics such as packet loss.
Refer to the exhibit.
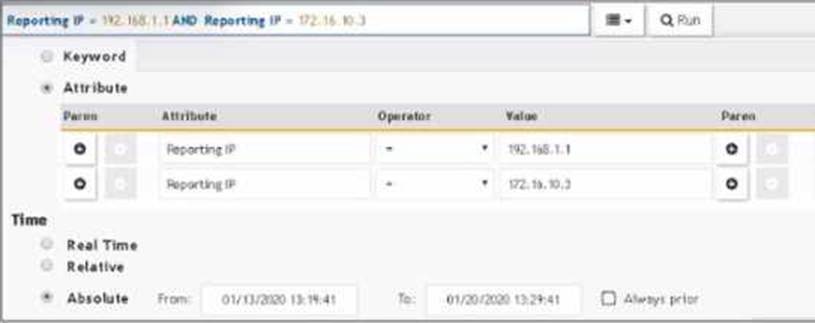
The FortiSIEM administrator is examining events for two devices to investigate an issue. However, the administrator is not getting any results from their search.
Based on the selected filters shown in the exhibit, why is the search returning no results?
- A . Parenthesis are missing.
- B . The wrong boolean operator is selected in the Next column.
- C . The wrong option is selected in the Operator column.
- D . An invalid IP subnet is typed in the Value column.
B
Explanation:
Search Filters in FortiSIEM: When searching for events, the correct use of filters and logical operators is crucial to obtain accurate results.
Issue Analysis:
Selected Filters: The exhibit shows filters for two different Reporting IP addresses.
Logical Operators: The use of "AND" between the two Reporting IP addresses implies that an event must match both IP addresses simultaneously, which is not possible for a single event.
Correct Usage: To search for events from either of the two IP addresses, parentheses should be used to group conditions logically.
Corrected Filter: (Reporting IP = 192.168.1.1 OR Reporting IP = 172.16.10.3) would return events
from either IP address.
Reference: FortiSIEM 6.3 User Guide, Search and Filters section, which explains the use of logical operators and the importance of parentheses in constructing effective search queries.
Refer to the exhibit.
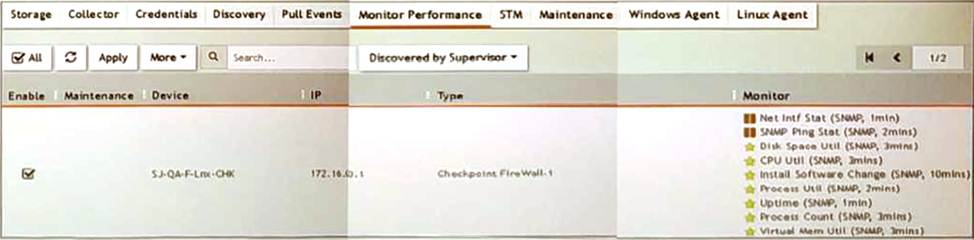
What do the yellow stars listed in the Monitor column indicate?
- A . A yellow star indicates that a metric was applied during discovery, and data has been collected successfully
- B . A yellow star indicates that a metric was applied during discovery, but data collection has not started
- C . A yellow star indicates that a metric was applied during discovery, but FortiSIEM is unable to collect data.
- D . A yellow star indicates that a metric was not applied during discovery and, therefore, FortiSEIM was unable to collect data.
B
Explanation:
Monitor Column Indicators: In FortiSIEM, the Monitor column displays the status of various metrics applied during the discovery process.
Yellow Star Meaning: A yellow star next to a metric indicates that the metric was successfully applied during discovery and data has been collected for that metric.
Successful Data Collection: This visual indicator helps administrators quickly identify which metrics are active and have data available for analysis.
Reference: FortiSIEM 6.3 User Guide, Device Monitoring section, which explains the significance of different icons and indicators in the Monitor column.
An administrator is in the process of renewing a FortiSIEM license.
Which two commands will provide the system ID? (Choose two.)
- A . phgetHWID
- B . ./phLicenseTool – support
- C . phgetUUID
- D . ./phLicenseTool-show
AC
Explanation:
License Renewal Process: When renewing a FortiSIEM license, it is essential to provide the system ID, which uniquely identifies the FortiSIEM instance.
Commands to Retrieve System ID:
phgetHWID: This command retrieves the hardware ID of the FortiSIEM appliance.
Usage: Run the command phgetHWID in the CLI to obtain the hardware ID.
phgetUUID: This command retrieves the universally unique identifier (UUID) for the FortiSIEM system.
Usage: Run the command phgetUUID in the CLI to obtain the UUID.
Verification: Both phgetHWID and phgetUUID are valid commands for retrieving the necessary system IDs required for license renewal.
Reference: FortiSIEM 6.3 Administration Guide, Licensing section details the commands and procedures for obtaining system identification information necessary for license renewal.
Refer to the exhibit.
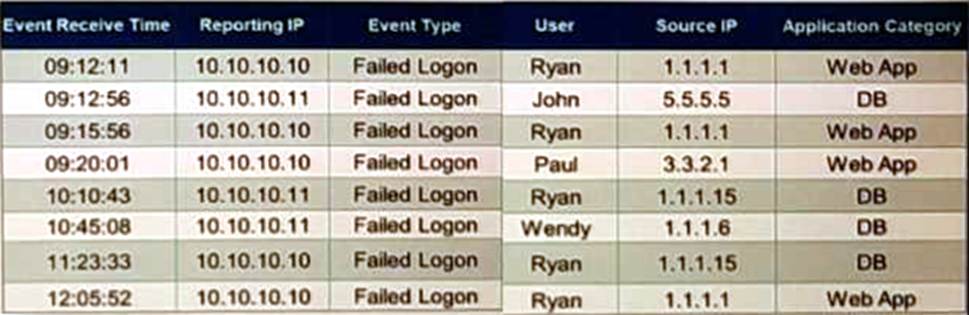
If events are grouped by Reporting IP, Event Type, and user attributes in FortiSIEM, how, many results will be displayed?
- A . Seven results will be displayed.
- B . There results will be displayed.
- C . Unique attribute cannot be grouped.
- D . Five results will be displayed.
A
Explanation:
Grouping Events: Grouping events by specific attributes allows for the aggregation of similar events.
Grouping Criteria: For this question, events are grouped by "Reporting IP," "Event Type," and "User." Unique Combinations Analysis:
