Practice Free MS-102 Exam Online Questions
DRAG DROP
You have a Microsoft 365 subscription.
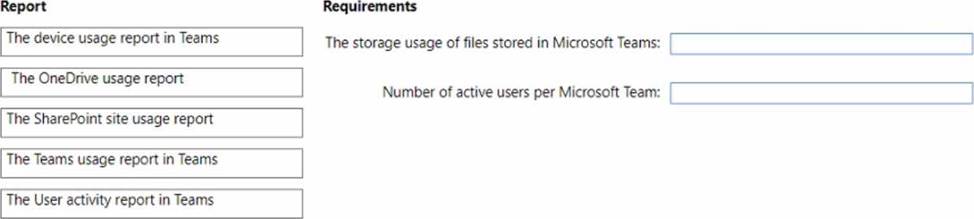
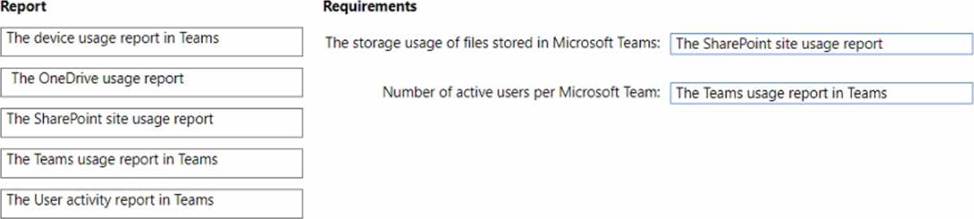
You need to review reports to identify the following:
• The storage usage of files stored in Microsoft Teams
• The number of active users per team
Which report should you review for each requirement? To answer, drag the appropriate reports to the correct requirements. Each report may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content
You have a Microsoft J65 E5 subscription.
You integrate Microsoft Defender for Endpoint with Microsoft Intune.
You need to ensure that devices automatically onboard to Defender for Endpoint when they are enrolled in Intune.
Solution: You configure a device configuration profile.
Does this meet the goal?
- A . Yes
- B . No
HOTSPOT
You have a Microsoft 365 E5 subscription.
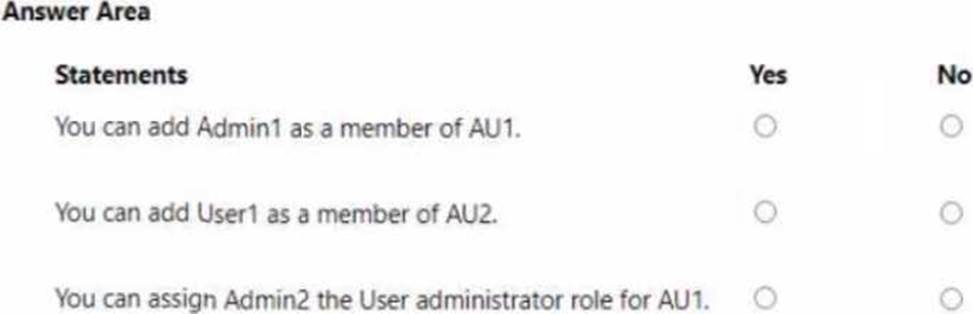
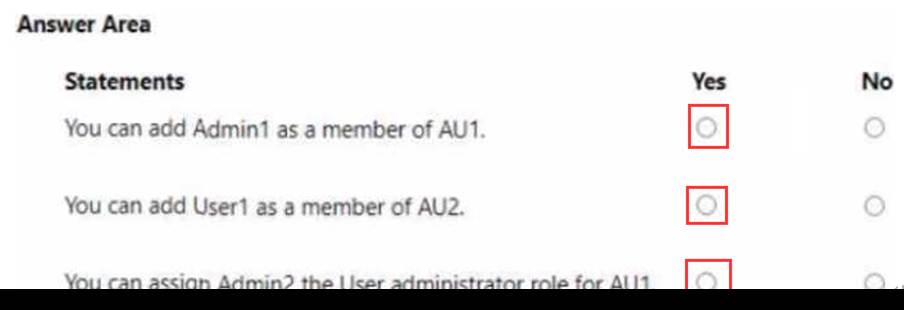
You have an Azure AD tenant named contoso.com that contains the following users:
• Admin1
• Admin2
• User1
Contoso.com contains an administrative unit named AIM that has no role assignments. User1 is a member of AU1. You create an administrative unit named AU2 that does NOT have any members or role assignments.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT
You have a Microsoft 365 E5 subscription that contains a user named User1.
Azure AD Password Protection is configured as shown in the following exhibit.
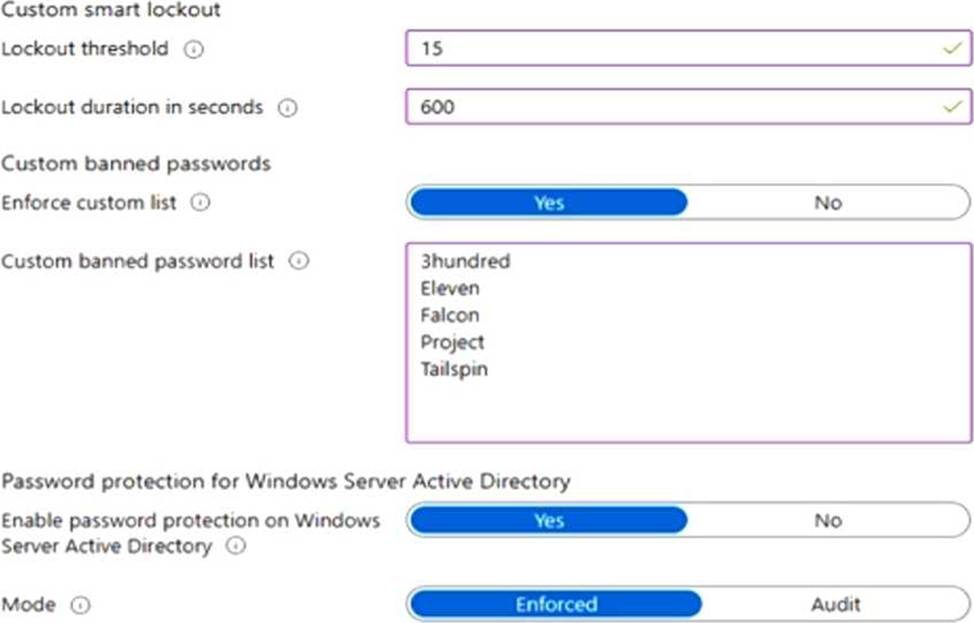
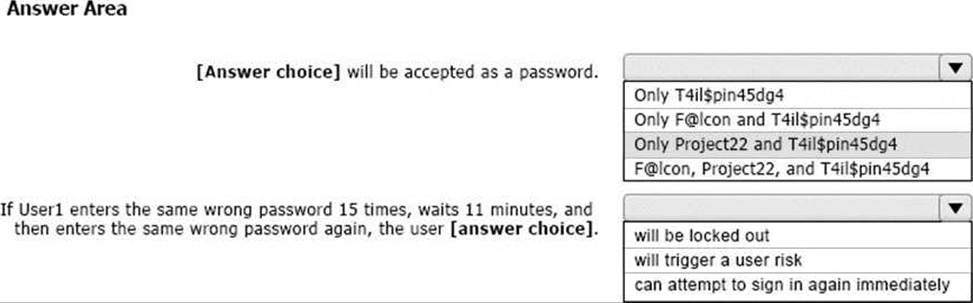
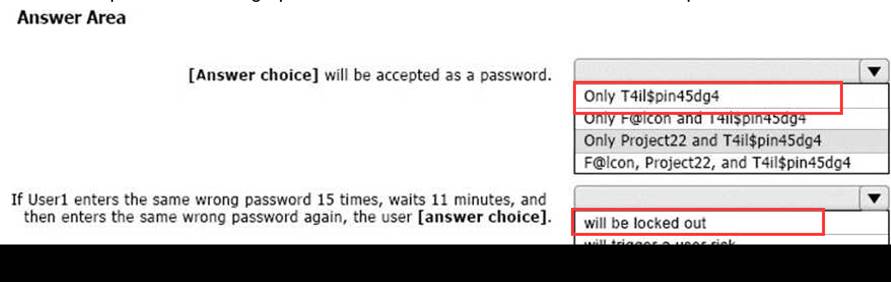
User1 attempts to update their password to the following passwords:
F@lcon
Project22
T4il$pin45dg4
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
HOTSPOT
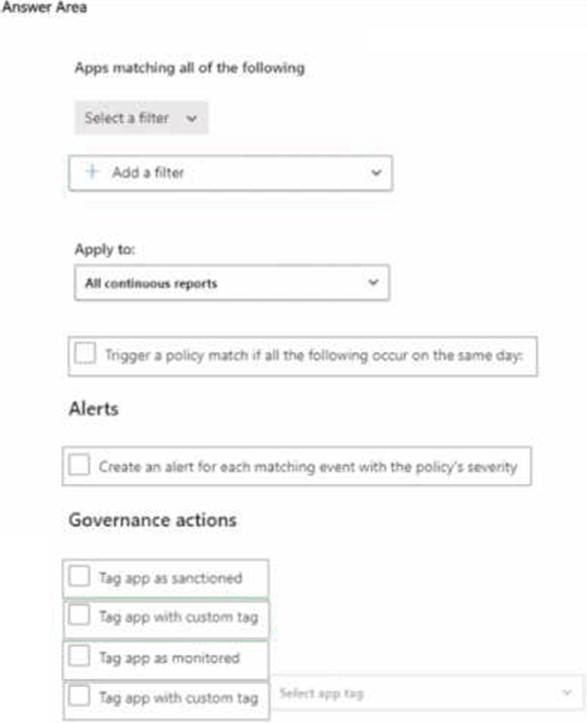
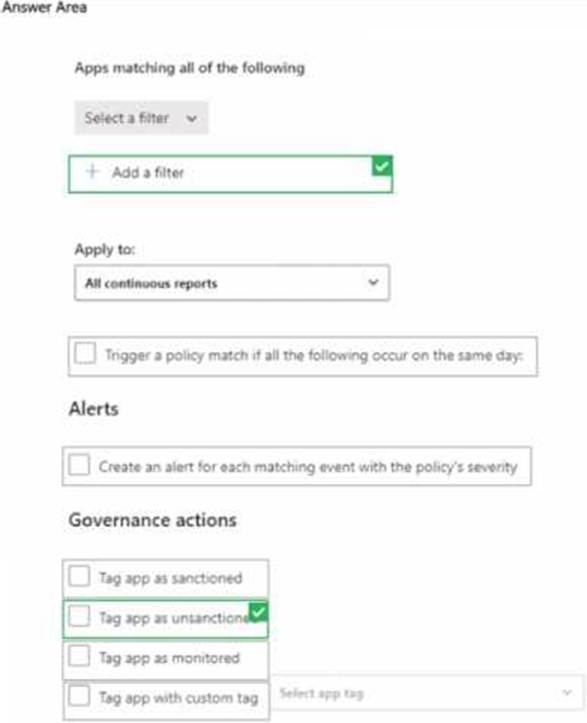
You have a Microsoft 365 subscription.
You integrate Microsoft Defender for Cloud Apps with Microsoft Defender for Endpoint.
You need to create a policy to block users from accessing discovered apps that have a risk score of 4 or lower.
Which two settings should you configure? To answer, select the appropriate settings in the answer area. NOTE: Each correct selection is worth one point.
DRAG DROP
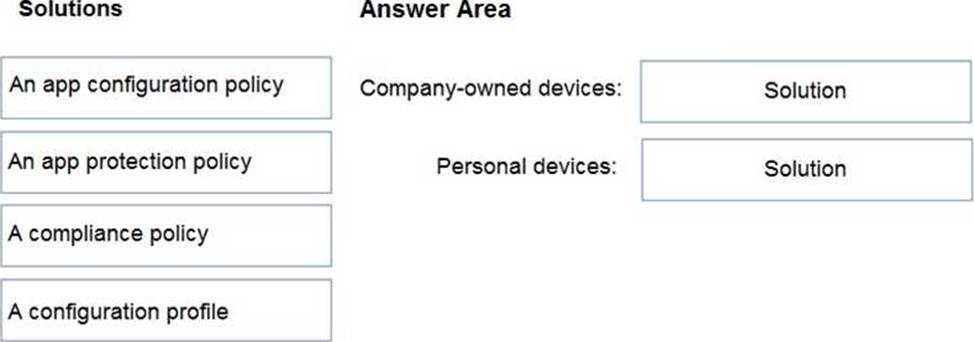
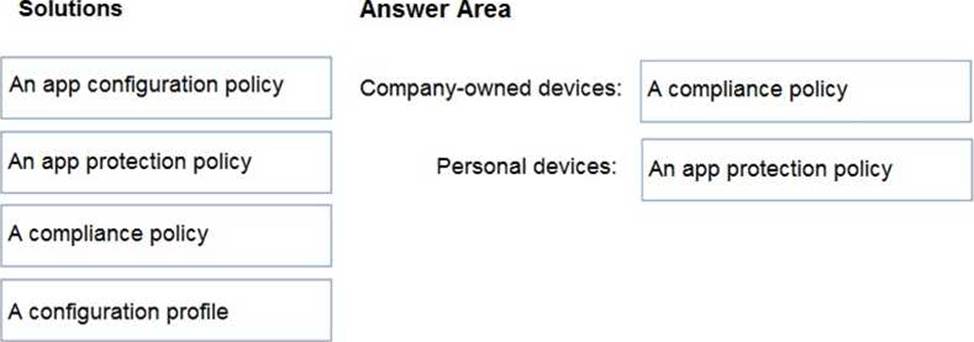
Your company has a Microsoft 365 E5 tenant.
Users access resources in the tenant by using both personal and company-owned Android devices.
Company policies requires that the devices have a threat level of medium or lower to access Microsoft Exchange Online mailboxes.
You need to recommend a solution to identify the threat level of the devices and to control access of the devices to the resources.
What should you include in the solution for each device type? To answer, drag the appropriate components to the correct devices. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
HOTSPOT
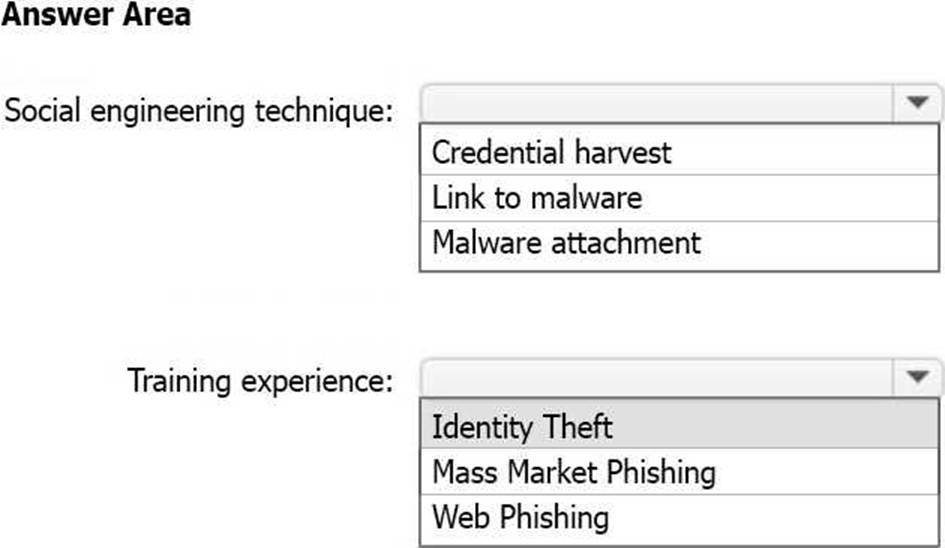
You have a Microsoft 365 E3 subscription.
You plan to launch Attack simulation training for all users.
Which social engineering technique and training experience will be available? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
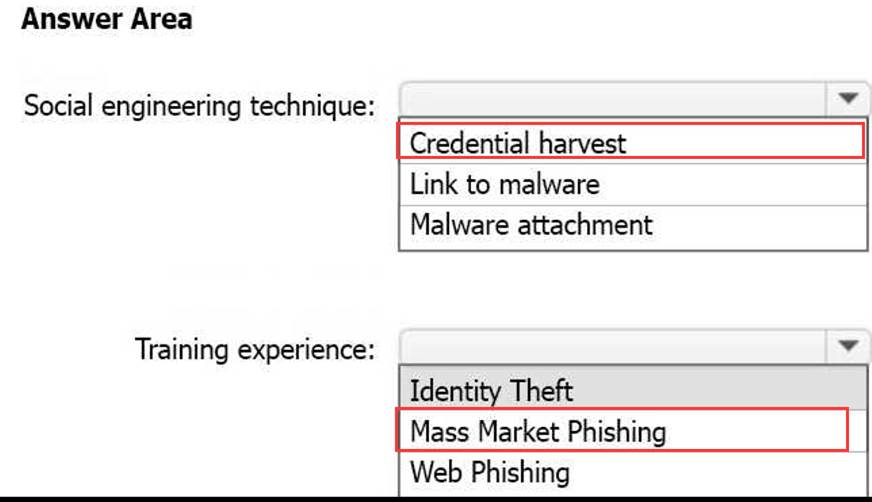
Explanation:
Box 1: Credential Harvest
Attack simulation training offers a subset of capabilities to E3 customers as a trial. The trial offering contains the ability to use a Credential Harvest payload and the ability to select ‘ISA Phishing’ or ‘Mass Market Phishing’ training experiences. No other capabilities are part of the E3 trial offering.
Note: In Attack simulation training, multiple types of social engineering techniques are available:
Credential Harvest
Malware Attachment
Link to Malware
Etc.
Box 2: Mass Market Phishing
Reference: https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/attack-simulation-training-get-started
You need to notify the manager of the human resources department when a user in the department shares a file or folder from the departments Microsoft SharePoint Online site.
What should you do?
- A . From the SharePoint Online site, create an alert.
- B . From the SharePoint Online admin center, modify the sharing settings.
- C . From the Microsoft 365 Defender portal, create an alert policy.
- D . From the Microsoft Purview compliance portal, create a data loss prevention (DLP) policy.
HOTSPOT
You have a Microsoft 365 E5 tenant that contains 100 Windows 10 devices.
You plan to attack surface reduction (ASR) rules for the Windows 10 devices.
You configure the ASR rules in audit mode and collect audit data in a Log Analytics workspace.
You need to find the ASR rules that match the activities on the devices.
How should you complete the Kusto query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
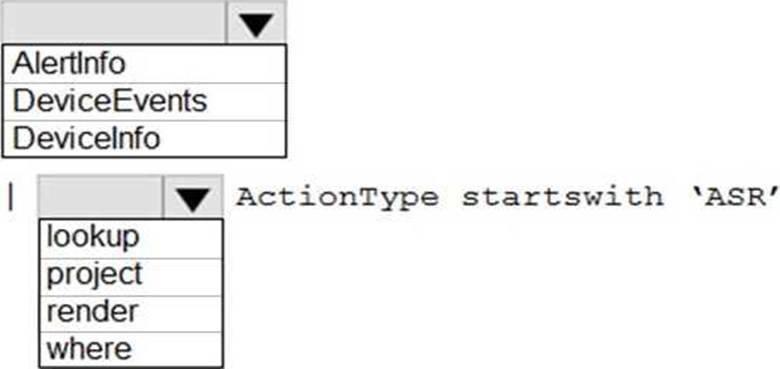
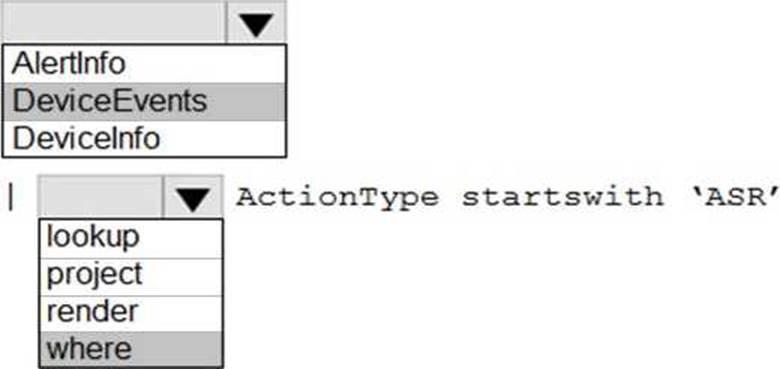
Explanation:
Reference: https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/demystifying-attack-surface-reduction-rules-part-3/ba-p/1360968
You have a Microsoft 365 E5 subscription.
Users access Microsoft 365 from both their laptop and a corporate Virtual Desktop Infrastructure (VDI) solution.
From Azure AD Identity Protection, you enable a sign-in risk policy.
Users report that when they use the VDI solution, they are regularly blocked when they attempt to access Microsoft 365.
What should you configure?
- A . the Tenant restrictions settings in Azure AD
- B . a trusted location
- C . a Conditional Access policy exclusion
- D . the Microsoft 365 network connectivity settings
B
Explanation:
There are two types of risk policies in Azure Active Directory (Azure AD) Conditional Access you can set up to automate the response to risks and allow users to self-remediate when risk is detected:
Sign-in risk policy
User risk policy
Configured trusted network locations are used by Identity Protection in some risk detections to reduce false positives.
Reference:
https://learn.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-configure-risk-policies
https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/location-condition
