Practice Free MS-102 Exam Online Questions
You have a Microsoft 365 subscription.
All users have their email stored in Microsoft Exchange Online.
In the mailbox of a user named User1. you need to preserve a copy of all the email messages that contain the word ProjectX.
What should you do first?
- A . From the Exchange admin center create a mail flow rule.
- B . From Microsoft 365 Defender, start a message trace.
- C . From Microsoft Defender for Cloud Apps, create an activity policy.
- D . From the Microsoft Purview compliance portal, create a label and a label policy.
HOTSPOT
You have a Microsoft 36S E5 subscription.
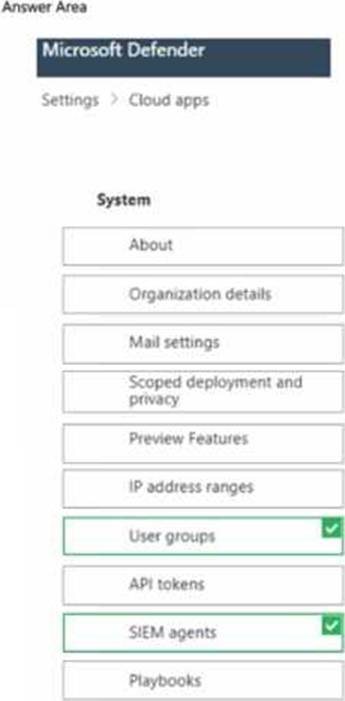
You connect a cloud app that contains a group named Group1 to Microsoft Defender tor Cloud Apps.
You need to configure the Cloud apps settings to monitor all activities performed by the members of Group 1.
Which two settings should you configure? to answer, select the appropriate settings in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 tenant.
You plan to implement Endpoint Protection device configuration profiles.
Which platform can you manage by using the profile?
- A . Android
- B . CentOS Linux
- C . iOS
- D . Window 10
D
Explanation:
Reference: https://docs.microsoft.com/en-us/mem/intune/protect/endpoint-protection-configure
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint and Microsoft Intune.
All devices run Windows 11 and are Microsoft Entra joined.
You are alerted to a zero-day attack.
You need to identify which devices were affected by the attack and send a request to Intune administrators to update the affected devices.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . From Incidents & alerts, select the latest incident.
- B . From Vulnerability management, open the security recommendation.
- C . Select the affected devices and request remediation.
- D . From Threat analytics, view the list of vulnerable devices.
HOTSPOT
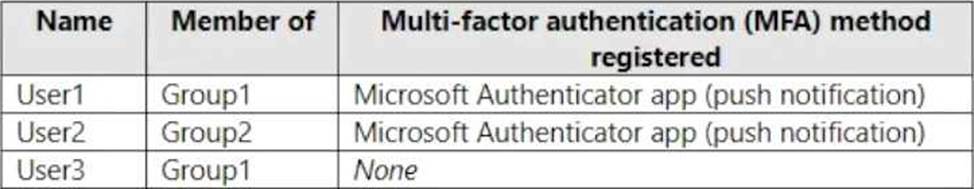
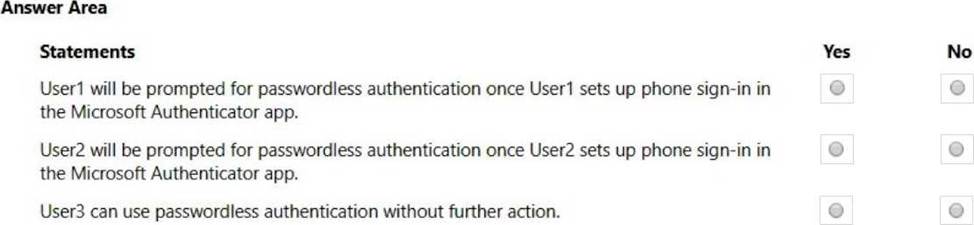
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
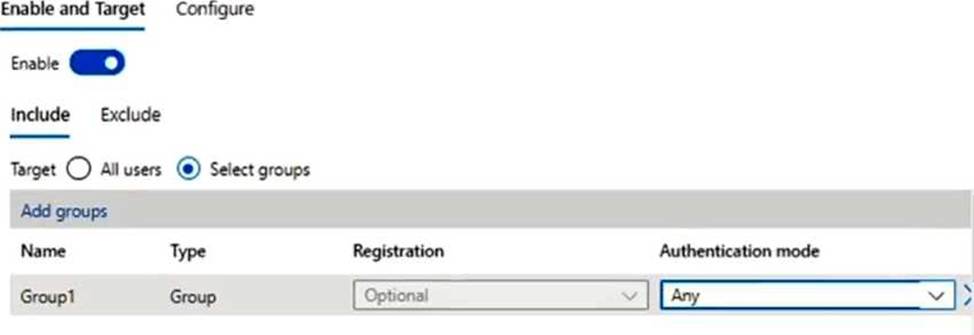
You configure the Microsoft Authenticator authentication method policy to enable password less authentication as shown in the following exhibit.
Both User1 and User2 report that they are NOT prompted for passwordless sign-in in the Microsoft Authenticator app.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Explanation:
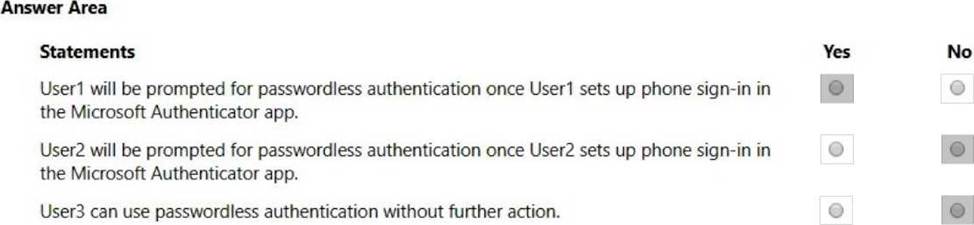
Box 1: Yes
User1 is member of Group1.
User1 has MFA registered method of Microsoft Authenticater app (push notification)
The Microsoft Authenticator authentication method policy is configured for Group1, registration is optional, authentication method is any.
Note: Microsoft Authenticator can be used to sign in to any Azure AD account without using a password. Microsoft Authenticator uses key-based authentication to enable a user credential that is tied to a device, where the device uses a PIN or biometric. Windows Hello for Business uses a similar technology.
This authentication technology can be used on any device platform, including mobile. This technology can also be used with any app or website that integrates with Microsoft Authentication Libraries.
Box 2: No
User2 is member of Group2.
The Microsoft Authenticator authentication method policy is configured for Group1, not for Group2.
Box 3: No
User3 is member of Group1.
User3 has no MFA method registered.
User3 must choose an authentication method.
Note: Enable passwordless phone sign-in authentication methods
Azure AD lets you choose which authentication methods can be used during the sign-in process.
Users then register for the methods they’d like to use.
Reference: https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-authentication-passwordless-phone
DRAG DROP
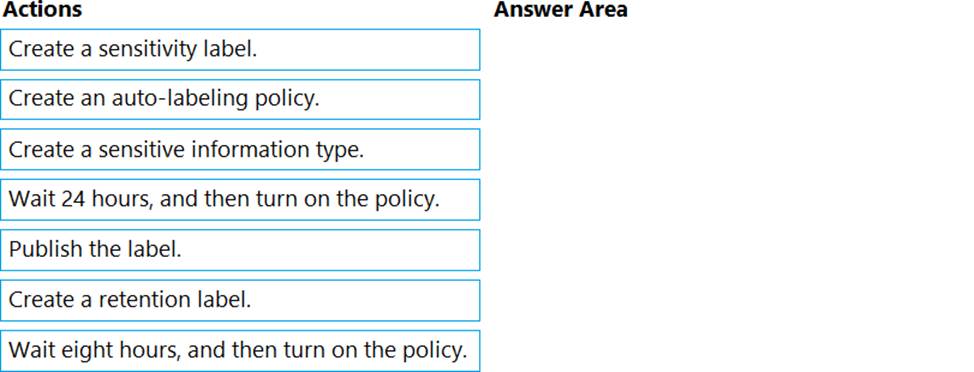
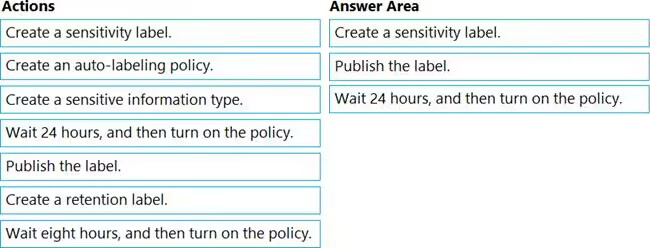
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1.
You need to automatically label the documents on Site1 that contain credit card numbers.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Which report should the New York office auditors view?
- A . DLP policy matches
- B . DLP false positives and overrides
- C . DLP incidents
- D . Top Senders and Recipients
C
Explanation:
Reference: https://docs.microsoft.com/en-us/office365/securitycompliance/data-loss-prevention-policies
This report also shows policy matches over time, like the policy matches report. However, the policy matches report shows matches at a rule level; for example, if an email matched three different rules, the policy matches report shows three different line items. By contrast, the incidents report shows matches at an item level; for example, if an email matched three different rules, the incidents report shows a single line item for that piece of content. Because the report counts are aggregated differently, the policy matches report is better for identifying matches with specific rules and fine tuning DLP policies. The incidents report is better for identifying specific pieces of content that are problematic for your DLP policies.
HOTSPOT
You have a Microsoft 365 tenant.
You plan to create a retention policy as shown in the following exhibit.
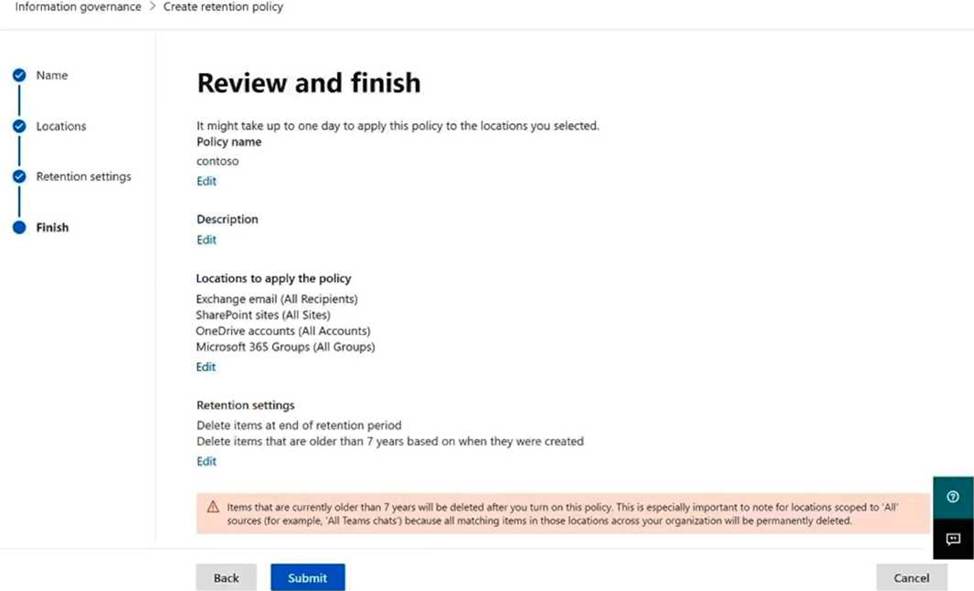
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
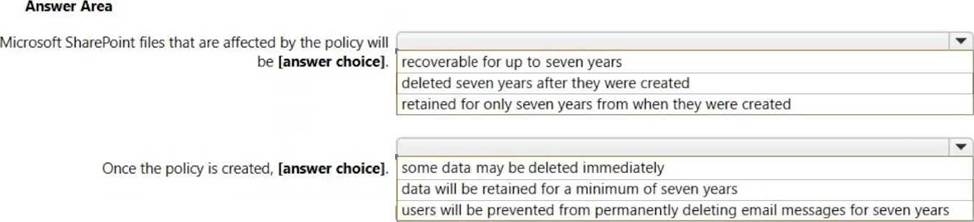
HOTSPOT
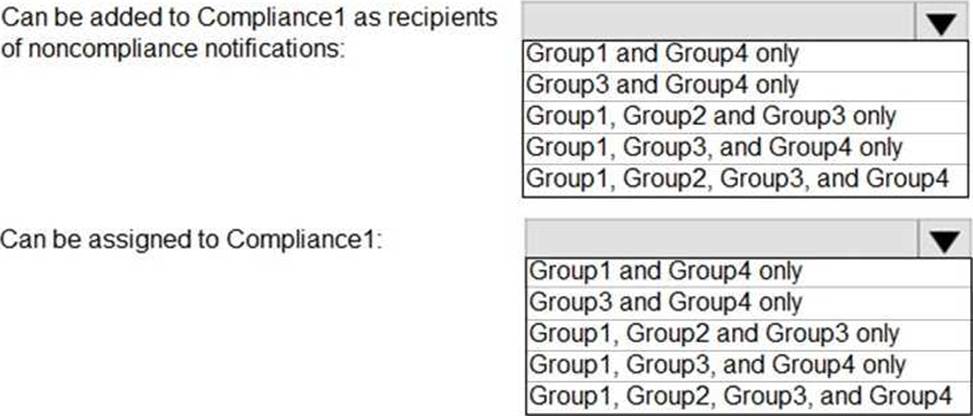
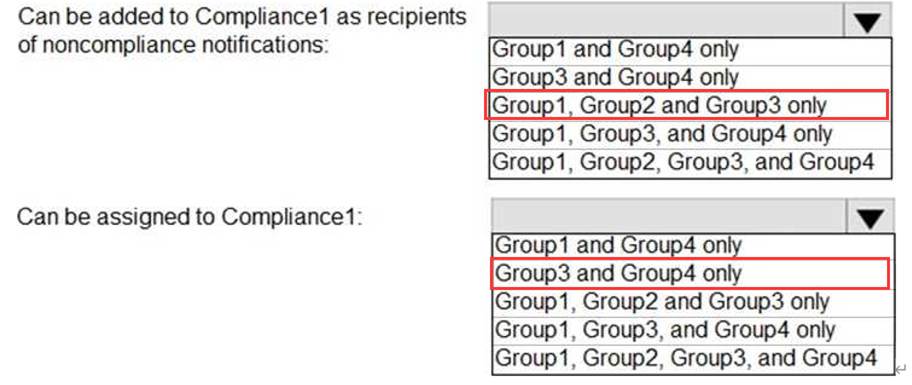
You have a Microsoft 365 tenant that contains the groups shown in the following table.
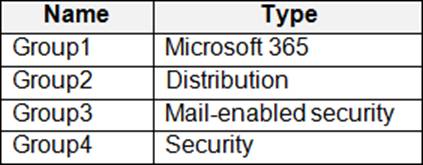
You plan to create a compliance policy named Compliance1.
You need to identify the groups that meet the following requirements:
Can be added to Compliance1 as recipients of noncompliance notifications Can be assigned to Compliance1
To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains the following user:
Name: User1
UPN: [email protected]
Email address: [email protected]
MFA enrollment status: Disabled
When User1 attempts to sign in to Outlook on the web by using the [email protected] email address, the user cannot sign in.
You need to ensure that User1 can sign in to Outlook on the web by using [email protected].
What should you do?
- A . Assign an MFA registration policy to User1.
- B . Reset the password of User1.
- C . Add an alternate email address for User1.
- D . Modify the UPN of User1.
D
Explanation:
Microsoft’s recommended best practices are to match UPN to primary SMTP address. This article addresses the small percentage of customers that cannot remediate UPN’s to match.
Note: A UPN is an Internet-style login name for a user based on the Internet standard RFC 822. The UPN is shorter than a distinguished name and easier to remember. By convention, this should map to the user’s email name. The point of the UPN is to consolidate the email and logon namespaces so that the user only needs to remember a single name.
Configure the Azure AD multifactor authentication registration policy
Azure Active Directory (Azure AD) Identity Protection helps you manage the roll-out of Azure AD multifactor authentication (MFA) registration by configuring a Conditional Access policy to require MFA registration no matter what modern authentication app you’re signing in to.
Reference: https://docs.microsoft.com/en-us/windows/win32/ad/naming-properties#userprincipalname
