Practice Free MS-102 Exam Online Questions
You have a Microsoft 365 IS subscription and use Microsoft Defender for Cloud Apps.
From Policy management you open Information protection as shown in the following exhibit.
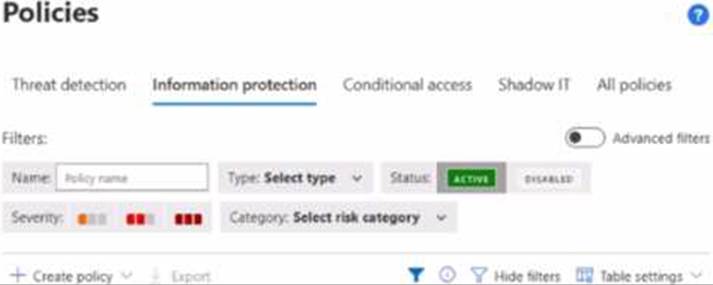
Which type of policy can you create?
- A . file policy
- B . access policy
- C . activity policy
- D . OAuth app policy
- E . session policy
HOTSPOT
You have a Microsoft 365 E5 subscription that contains the security groups shown in the following table.
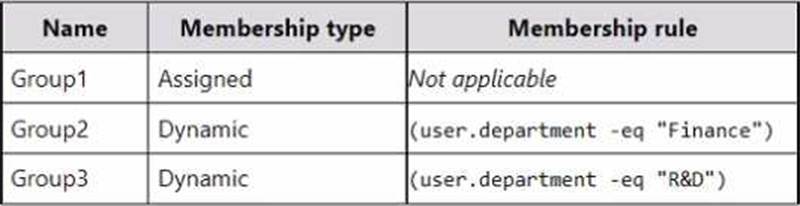
The subscription contains the users shown in the following table.
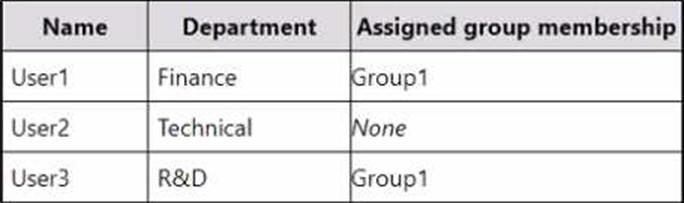
You have a Conditional Access policy that has the following settings:
• Assignments o Users
• Include: Group1
• Exclude: Group2. Group3 o Target resources
• Cloud apps
• App1
• Access controls
• Grant
• Block access
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT
You have a Microsoft 365 E5 subscription.
You plan to create the data loss prevention (DLP) policies shown in the following table.
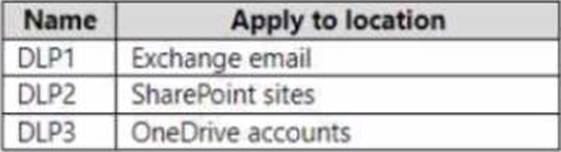
You need to create DLP rules for each policy.
Which policies support the sender is condition and the file extension is condition? To answer select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
You have a Microsoft 365 E5 subscription.
You need to configure threat protection tor Microsoft 365 to meet the following requirements:
• Limit a user named User 1 from sending more than 30 email messages per day.
• Prevent the delivery of a specific file based on the file hash.
Which two threat policies should you configure in Microsoft Defender for Office 365? To answer, select the appropriate threat policies in the answer area. NOTE: Each correct selection is worth one point.
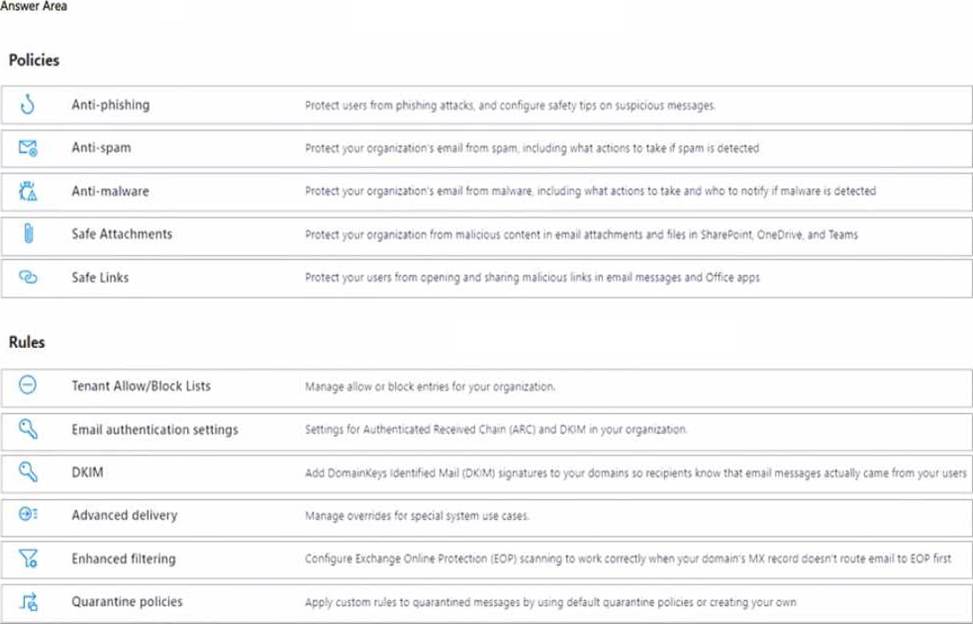
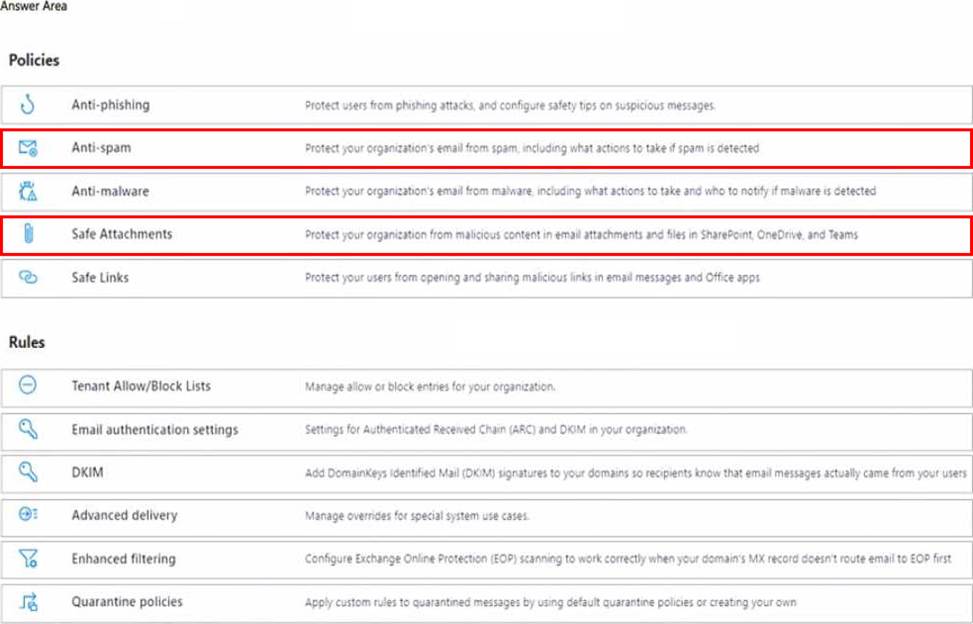
Explanation:
Limit a user named User 1 from sending more than 30 email messages per day: Anti-spam policy
The anti-spam policy in Microsoft Defender for Office 365 allows you to configure outbound spam settings, including limiting the number of email messages a user can send per day. This helps prevent spam and potential email abuse within the organization.
Prevent the delivery of a specific file based on the file hash: Safe Attachments policy
The Safe Attachments policy in Microsoft Defender for Office 365 can be configured to block or quarantine emails with attachments that match specific file hashes. This ensures that potentially malicious files are not delivered to users’ inboxes.
You have a Microsoft 365 tenant.
You plan to manage incidents in the tenant by using the Microsoft 365 security center.
Which Microsoft service source will appear on the Incidents page of the Microsoft 365 security center?
- A . Microsoft Cloud App Security
- B . Azure Sentinel
- C . Azure Web Application Firewall
- D . Azure Defender
A
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender/investigate-alerts?view=o365-worldwide
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goats. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain.
You deploy a Microsoft Entra tenant.
Another administrator configures the domain to synchronize to the Microsoft Entra tenant.
You discover that 10 user accounts in an organizational unit (OU) are NOT synchronized to the Microsoft Entra tenant. All the other user accounts synchronized successfully.
You review Microsoft Entra Connect Health and discover that all the user account synchronizations completed successfully.
You need to ensure that the 10 user accounts are synchronized to the Microsoft Entra tenant.
Solution: From Microsoft Entra Connect, you modify the filtering settings.
Does this meet the goal?
- A . Yes
- B . No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goats. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain.
You deploy a Microsoft Entra tenant.
Another administrator configures the domain to synchronize to the Microsoft Entra tenant.
You discover that 10 user accounts in an organizational unit (OU) are NOT synchronized to the Microsoft Entra tenant. All the other user accounts synchronized successfully.
You review Microsoft Entra Connect Health and discover that all the user account synchronizations completed successfully.
You need to ensure that the 10 user accounts are synchronized to the Microsoft Entra tenant.
Solution: From Microsoft Entra Connect, you modify the filtering settings.
Does this meet the goal?
- A . Yes
- B . No
HOTSPOT
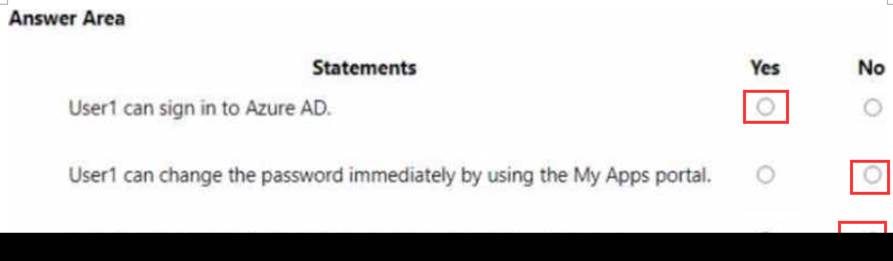
Your network contains an on-premises Active Directory domain named adatum.com that syncs to Azure AD by using the Azure AD Connect Express Settings. Password write back is disabled.
You create a user named User1 and enter Pass in the Password field as shown in the following exhibit.
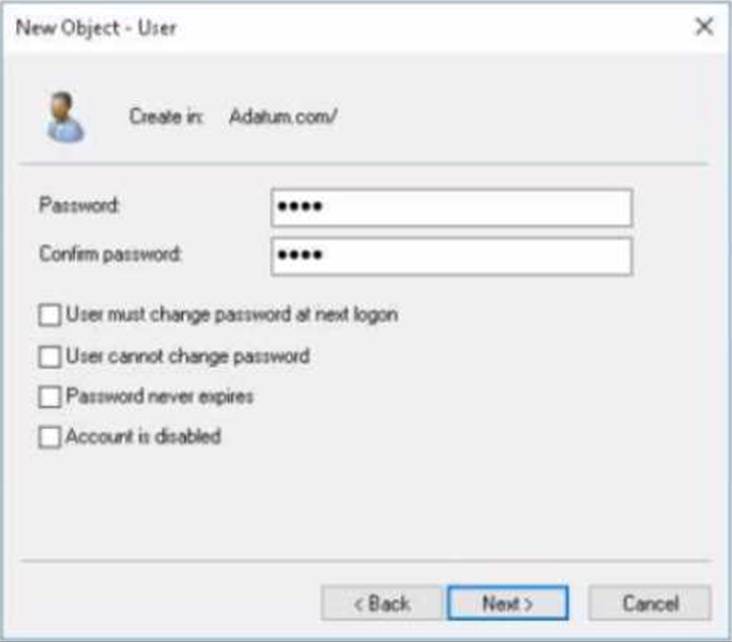
The Azure AD password policy is configured as shown in the following exhibit.
Password policy
Set the password policy for all users in your organization.
You confirm that User1 is synced to Azure AD.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
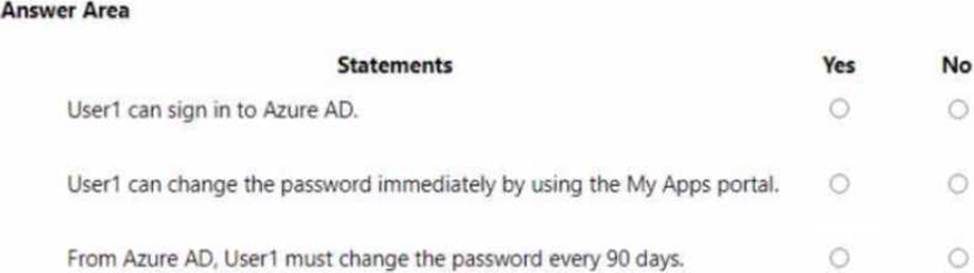
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an on-premises Active Directory domain. The domain contains domain controllers that run Windows Server 2019. The functional level of the forest and the domain is Windows Server 2012 R2.
The domain contains 100 computers that run Windows 10 and a member server named Server1 that runs Windows Server 2012 R2.
You plan to use Server1 to manage the domain and to configure Windows 10 Group Policy settings.
You install the Group Policy Management Console (GPMC) on Server1.
You need to configure the Windows Update for Business Group Policy settings on Server1.
Solution: You upgrade Server1 to Windows Server 2019.
Does this meet the goal?
- A . yes
- B . No
You have a Microsoft 365 subscription that contains a user named User1.
User1 requires admin access to perform the following tasks:
Manage Microsoft Exchange Online settings.
Create Microsoft 365 groups.
You need to ensure that User1 only has admin access for eight hours and requires approval before the role assignment takes place.
What should you use?
- A . zure AD Identity Protection
- B . Microsoft Entra Verified ID
- C . Conditional Access
- D . Azure AD Privileged Identity Management (PJM)
D
Explanation:
Privileged Identity Management provides time-based and approval-based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions on resources that you care about.
Here are some of the key features of Privileged Identity Management:
Provide just-in-time privileged access to Azure AD and Azure resources
Assign time-bound access to resources using start and end dates
Require approval to activate privileged roles
Enforce multi-factor authentication to activate any role
Use justification to understand why users activate
Get notifications when privileged roles are activated
Conduct access reviews to ensure users still need roles
Download audit history for internal or external audit
Prevents removal of the last active Global Administrator and Privileged Role Administrator role assignments.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
